Hacking Microsoft teams vulnerabilities: A step-by-step guide
We are living in an era where technology is part of our lives and a primary valuable resource for personal and professional tasks. The use of online videoconference platforms such as Zoom and Microsoft Teams has exploded in recent months, due in large part to the COVID-19 pandemic situation.
This article provides a detailed step-by-step guide on how to hack Microsoft Teams with a simple GIF image. The vulnerability published in April-mid 2020 could be exploited by a remote agent, and Microsoft promptly patched the flaw a few days after the disclosure. However, this scenario should be understood as an actual threat facing not only Microsoft Teams but all applications that maintain the same modus operandi.

What should you learn next?
How to hack Microsoft teams
The disclosed flaw is a worm-like vulnerability that allows criminals to take over an organization’s entire roster of Teams accounts just by sending victims a malicious link to an innocent-looking GIF image.
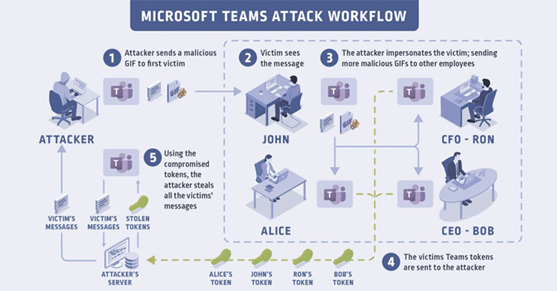
Even if a criminal doesn’t have sensitive information from a Team’s account, the flaw can be used to perform a spread attack over the organization’s accounts just like a worm, getting the account’s tokens and then accessing all the chat sessions of the target users. Figure 1 below demonstrates how this attack can be executed against a large company.
Figure 1: Microsoft Teams attack workflow
In detail, the attack can be exploited following the next steps:
- A malicious GIF image is prepared and created by criminals and sent to a first victim during a videoconference via chat.
- The victim opens and sees the message with the GIF image embedded. At this point, the criminal impersonates the victim and spreads the GIF image with the payload in the organization’s Teams accounts like a worm, infecting a large group of employees.
- The message is disseminated and other victims are affected.
- The victims’ Teams tokens are sent to the criminal’s side.
- Criminals can use the exfiltrated tokens to access the victim’s information, contacts, messages and so on.
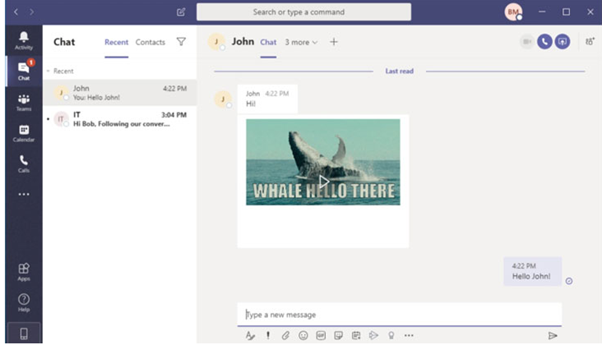
As described above, the vulnerability resides on a simple GIF image and in the way how Teams handles authentication to image resources. Below, the initial payload is presented.

Figure 2: GIF image sent to the first victim.
In detail, when the application is opened (both mobile and desktop), a JSON Web Token (JWT) — the access token — is created during that process. This token allows a user to view images shared by the individual or others in a conversation/meeting.
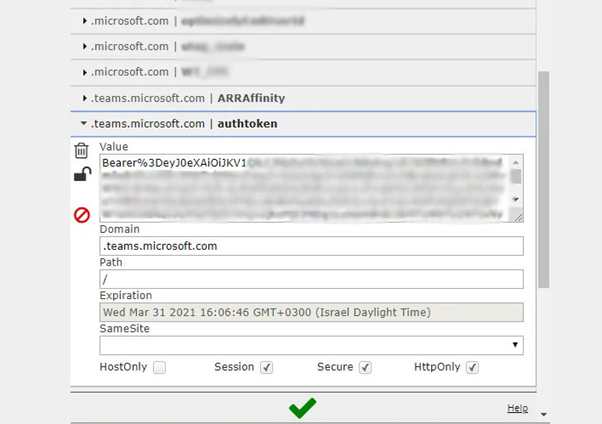
Because of this, a cookie called “authtoken” that grants access to a resource server “api.spaces.skype.com” can be abused to create the “skype token”, giving access to send messages, create groups, add new users or remove users from groups, change permissions in groups via the Teams API and so on.
Figure 3: JWT token exfiltrated by using this vulnerability.
Next step: The takeover attack
After getting this privileged token, it can be abused to interact with other internal systems of the Microsoft ecosystem. In order to perform a well-succeeded attack, two subdomains were identified as vulnerable to takeover attacks:
- aadsync-test.teams.microsoft.com
- data-dev.teams.microsoft.com
Obtaining this point, a criminal can force a user to access the subdomains that have been taken over. After that, the victim’s browser will send the cookie authtoken to the criminals’ remote server. Now the Skype token can be created and all the victim’s Team’s account data can be accessed.
Details including confidential information, meetings and calendar information, competitive data, secrets, passwords, private information, business strategy, plans and procedures can be now used to perform other kinds of attack vectors.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Final thoughts
From here, unauthorized accesses via remote services such as VPN and email can give the possibility of an internal access. A set of pre-deployed tasks can be executed by criminals to take advantage of this initial foothold. Because of this, monitoring should be seen as a surgical tool to prevent scenarios of this nature.
Since videoconference software has been used to maintain straight communication between employees, clients and even family, maintaining the software updated in order to prevent the exploration of the most recent attack vectors is a mandatory procedure for everyone.
The usage of endpoint security solutions such as antivirus on host-IDS agents should be taken in account as a way of preventing the success of the emergent threats and tricks used by criminals.
Sources
Beware of the GIF: Account Takeover Vulnerability in Microsoft Teams, CyberArk
Como comprometer o Microsoft Teams apenas com uma imagem GIF, Segurança Informática