NPK: Free tool to crack password hashes with AWS
The NPK tool is an open-source password cracking tool developed by the Coalfire Labs Research and Development team. The initials NPK are inspired by the atomic elements contained within farm fertilizers — nitrogen, phosphorus and potassium. The inspiration comes from the fact that just as farm fertilizers increase crop yields, this tool can increase the password cracking yields in a penetration testing engagement for hackers, yet at a lower cost than other alternatives.

FREE role-guided training plans
Benefits of NPK
NPK succeeds over conventional password-cracking techniques due to a couple of strong benefits:
1. It allows for easy installation
Compared to conventional password cracking tools, NPK allows for very easy installation. All it takes is running one configuration file for the installation process, and you can begin to crack passwords.
2. It allows for an intuitive campaign builder
NPK allows the penetration tester to run through a campaign builder wizard that makes a campaign configuration easy. This would otherwise be complex with other alternatives and tools, but NPK allows for a streamlined configuration process.
3. It has very straightforward pricing
NPK allows the penetration tester to perform a cost analysis before the commencement of a campaign. This makes it possible to know how much it would cost to run a campaign. This can be quite useful and prevents situations where unexpected billing can be made without your knowledge.
Installation
Before running NPK, you need to clone the repository locally, then install the prerequisites. The required ones are only two — jsonnet and jq. I have included the installation process below to see and follow along while you set up your own instance.
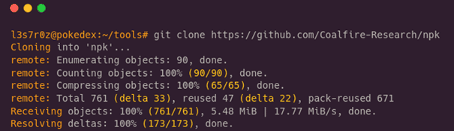
Step 1: Cloning the repository locally
I have cloned the repository to my local device to install the prerequisites in this first step. I am cloning from the NPK Github repository. During this step, the NPK code will be locally downloaded into a directory named NPK.
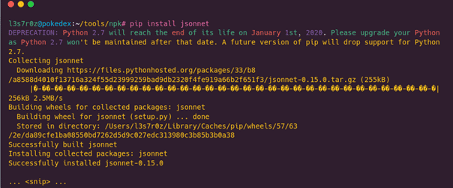
Step 2: Installing jsonnet
In this step, I have used pip to install jsonnet. The importance of jsonnet is to allow NPK to define data templates and to transform these into JSON objects.
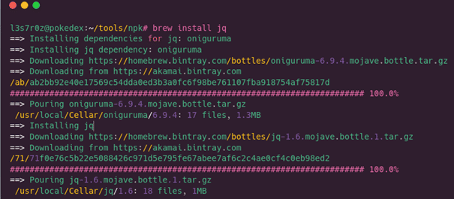
Step 3: Installing jq
This is the last step in installing the prerequisites, installing jq. This is a lightweight and command-line JSON processor. It is like sed (on Linux) but for JSON data.
Finally, I also had to install AWS CLI and Terraform, which was pretty straightforward. The reason for these two tools was to allow me to interact with the AWS instance on which NPK would Bruteforce from.
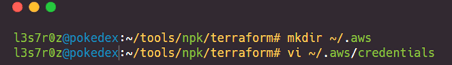
Step 4: Configuring NPK
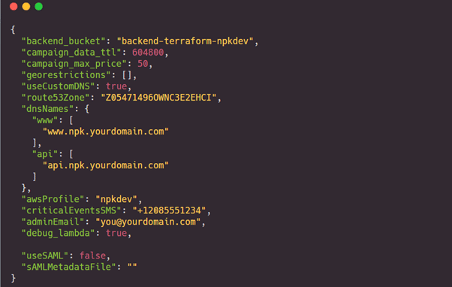
It was now time to configure the local NPK settings on my machine. I copied the sample npk-settings.json.sample file to a working npk-settings.json file, then edited my AWS credentials into it. You can access and verify these as shown in the screenshot below: also, note that the named credential profile that AWS CLI and Terraform use while deploying NPK must be the same.
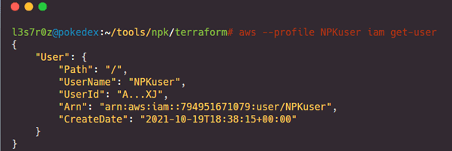
Once I had done that, I verified my credentials with the 'iam get-user' AWS CLI command. Please remember that you should use a fresh AWS account to keep things clean and well organized. It is recommended that you do this via the organization's console in AWS. This is shown below:
I have also included a sample config file below to see how a completed one would look.
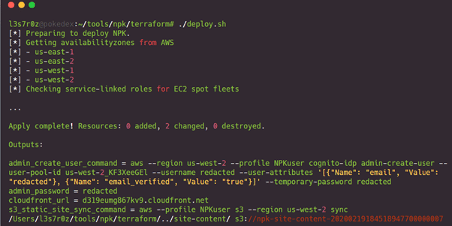
I then ran the deploy script as shown below, and it was completed successfully. I was now able to begin cracking passwords. You will, too, once the deploy step is completed successfully.
Password cracking
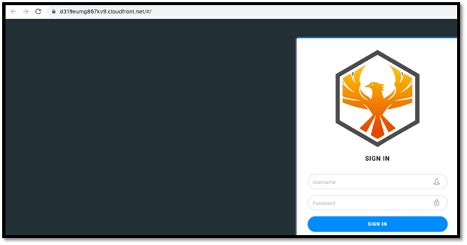
Once I was done with the installation, it was time for some password cracking. As shown below, I logged into Cloudfront with the temporary password for the first cracking attempt.
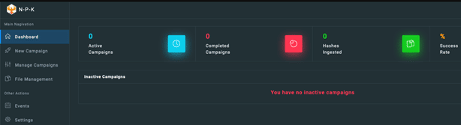
As shown below, I logged in and presented a dashboard that allowed me to start and manage campaigns.
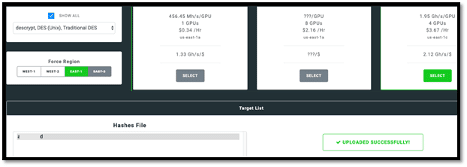
I started a new campaign and started cracking passwords, as shown below. There are different subscription plans as per your needs.
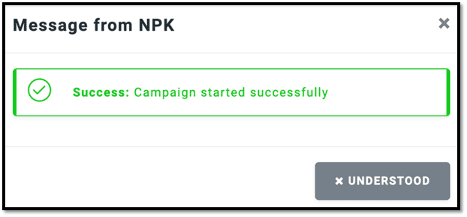
Once you have successfully set up your campaign, you should see the screen below. Click on "Understood" to proceed. The campaign configuration is straightforward and does not require too much effort.
The screenshot below shows the progress of NPK as it cracks the provided hashes.
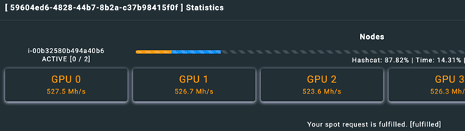
I could access some statistics as NPK was running, as shown below. These provide information on the rate of password cracking, GPU usage, and the active nodes.
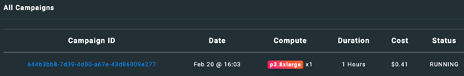
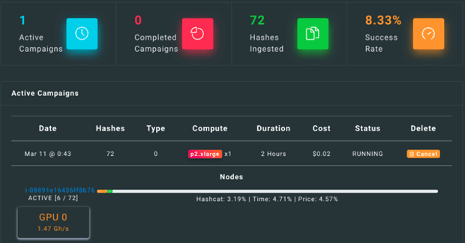
I also saw the active campaigns, completed campaigns, ingested hashes, and success rate. The history of all campaigns is also provided, and as is shown below, I had a running campaign.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
The benefits of using NPK
NPK is quite fast and reliable for password cracking. However, one disadvantage is that it is too simple and does not offer granular configuration as some other tools such as hashcat, which comes preinstalled in Kali Linux. The granularity of a tool like hashcat allows you to finetune your password cracking to a much deeper level, configuring options that can easily be issued on a Linux terminal via multiple switches. This is something that NPK lacks. What you are getting with NPK is the raw password cracking power, meaning that what would have otherwise taken you quite a long time can be done in a few hours, if not in minutes.
Sources
- Coalfire Labs Develops Open Source Password Cracking Tool (prnewswire.com), PRNewswire
- Detailed NPK Settings, Coalfire
- Detailed NPK Usage Instructions, Coalfire