Hacking the Tor network: Follow up [updated 2020]
In a previous post, I presented the main techniques used to hack Tor networks and de-anonymize Tor users. Law enforcement and intelligence agencies consider "de-anonymization" of Tor users a primary goal.
Authorities can try to implement techniques to break the encryption used to anonymize the traffic or to exploit vulnerabilities in one of the software modules that allows anonymizing the user's online experience.

What should you learn next?
There is also another option for authorities: to try secretly to destroy the overall Tor architecture or attack the hidden services to interfere with the traffic that flows to them.
Operation Onymous
Since the publication of the last post, a blow was dealt by the authorities to the cybercriminals that use the Tor network for illegal purposes. Police and intelligence agencies in a joint effort conducted the takedown of several illegal marketplaces as part of Operation Onymous. Coordinated by Europol's European Cybercrime Centre (EC3), Operation Onymous hit the criminal organization that exploited the Tor network to manage black markets. The operation is considered an important success in the fight agaisnst cybercrime, but many experts have begun to question how law enforcement was able to locate the servers hosting hidden services and operators who ran the illegal activities. The developers of the Tor Project published an interesting blog post titled "Thoughts and Concerns about Operation Onymous", in which they have explained the possible techniques adopted by authorities to locate the hidden services and de-anonymize the operators that managed the most popular black markets, including Silk Road 2.0.
"Over the last few days, we received and read reports saying that several Tor relays were seized by government officials. We do not know why the systems were seized, nor do we know anything about the methods of investigation which were used," states the post.
The principal assumptions that law enforcement has made on the possible attack scenarios implemented by the law enforcement are:
- Lack of operational security of hidden services
- Exploitation of bugs in the web application
- Bitcoin de-anonymization
- Attacks on the Tor network
The members of the Tor Project highlighted that the police has compromised the anonymity of the location of the servers behind the hidden services due to the lack of one of the following conditions:
- The hidden service must be properly configured.
- The web server should be not vulnerable: this means that it must be not affected by any flaw and must be properly configured.
- The web application should have no flaws.
An attacker that is able to exploit a vulnerability in the web server or in the web application (e.g. the e-commerce system exposed by the operators to propose the illegal products) could easily hack the targeted hidden service.
Resuming, to de-anonymize Tor users it is possible to compromise a poorly configured server or the web application it exposes, and there is no need to search and exploit an alleged vulnerability in Tor architecture.
By exploiting a vulnerability in a third-party application used by a dark marketplace, it is possible to install a backdoor on the server, revealing its location and the identities of its operators.
Another possibility for law enforcement is to infect the machine of one of the alleged administrators with a spyware. The computer could be localized through ordinary investigations.
Traffic analysis attack based on NetFlow
Exactly one week after the disclosure of Operation Onymous, a group of researchers presented the findings of a study conducted between 2008 and 2014 on the de-anonymization of the Tor users. The researchers analyzed the possibility to identify Tor users and reveal their originating IP addresses; they claimed to have obtained a 100 percent 'decloaking' success rate under laboratory conditions. The group led by professor Sambuddho Chakravarty, now researching Network Anonymity and Privacy at the Indraprastha Institute of Information Technology in Delhi, has published several papers on the topic over the last few years.
NetFlow
The study revealed that more than 81 percent of Tor clients can be de-anonymized by exploiting the NetFlow technology designed by Cisco for its network appliances.
NetFlow was introduced by the IT giant into its routers to implement an instrument to collect IP network traffic as it enters or exits an interface. It is a precious instrument to analyze the network traffic managed by the router and identify the causes of congestion. The protocol is widespread, and many experts consider it as a standard de facto. It actually runs by default in the hardware of many other network device manufacturers.
The technique proposed by Chakravarty and his team implements an active traffic analysis based on the introduction of specific traffic perturbations on server side. The researchers are able to de-anonymize Tor users by evaluating the effect of a similar perturbation on the client side through statistical correlation.
In a previous study, Chakravarty demonstrated that an attacker can monitor a significant percentage of the network paths from Tor nodes to destination servers by having access to a few Internet exchange points. The control of a few Internet exchange points allows the monitoring of a significant percentage of the network paths from Tor nodes to destination servers. This means that a powerful and persistent attacker can run traffic analysis attacks by observing similar traffic patterns at various points of the network.
The last study conducted by the team of researchers has revealed how to run an effective traffic analysis attack with less traffic monitoring capabilities, such as Cisco's NetFlow, and run a traffic analysis attack on a large scale.
Previous research, in fact, suggested a significant effort to de-anonymize users on a large scale. The experts consider that previous techniques required an effort sustainable only by a government or by an intelligence agency. The researcher explained that a single AS (Autonomous System) could monitor more than 39 percent of randomly-generated Tor circuits.
A traffic analysis attack elaborated in the last study doesn't request the enormous infrastructural effort as the previous techniques do, but it exploits one or more high-bandwidth and high-performance Tor relays. The team used a modified public Tor server, hosted at the time at Columbia University, running on Linux for its tests.
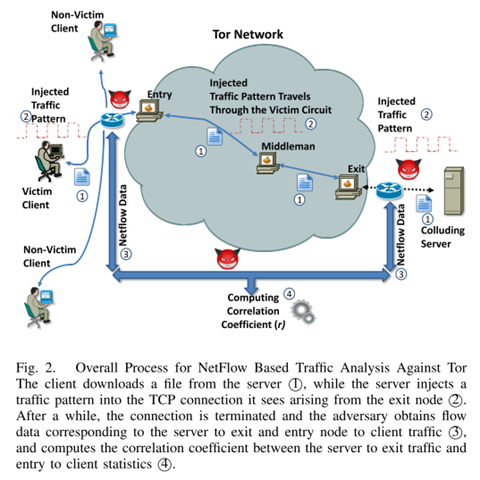
Figure 1 - Traffic Analysis based on NetFlow
The group of experts simulated the Internet activity of a typical Tor user: they injected a repeating traffic pattern (i.e. HTML files) into the TCP connection that they saw originating in the target exit node, and then analyzed the traffic at the exit node, as derived from the router's flow records, to improve client identification.
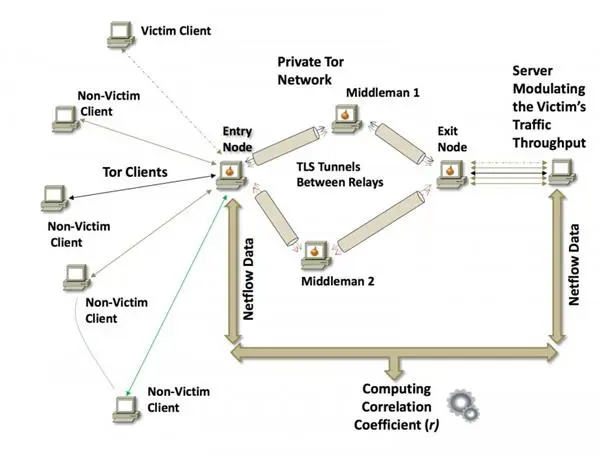
Figure 2 - Traffic Analysis attack
In the first phase, the researchers conducted specific tests in a lab environment with surprising results. In the second phase, the team started the live sessions using real Tor traffic. The team analyzed the traffic obtained from its public Tor relay that served hundreds of Tor circuits simultaneously.
The targeted victims were hosted on three different locations in the Planetlab, the global research network that supports the development of new network services. The chosen locations were Texas (US), Leuven (Belgium) and Corfu (Greece).
The victim clients downloaded a large file from the server that deliberately introduced perturbations in the arriving TCP connection's traffic, thereby deliberately injecting a traffic pattern in the stream between the server and the exit node.
"The process was terminated after a short while and we computed the correlation between the bytes transferred between the server and the recently terminated connection from the exit node and the entry node and the several clients that used it, during this interval," states the paper.
The test sessions were organized in two phases based on the source of data analyzed: a first session to evaluate the effectiveness when retrieving data from open-source NetFlow packages, and a second part based on sparse data obtained from an institutional Cisco router accessed by the group of researchers.
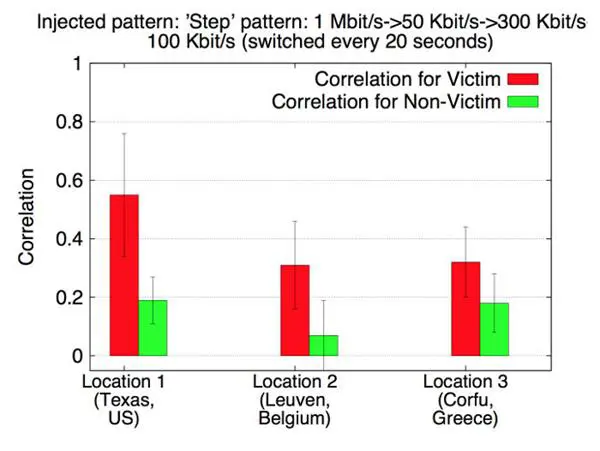
Figure 3 - Test results for Traffic Analysis based on NetFlow
"We present an active traffic analysis method based on deliberately perturbing the characteristics of user traffic at the server side, and observing a similar perturbation at the client side through statistical correlation. We evaluate the accuracy of our method using both in-lab testing, as well as data gathered from a public Tor relay serving hundreds of users. Our method revealed the actual sources of anonymous traffic with 100% accuracy for the in-lab tests, and achieved an overall accuracy of about 81.4% for the real-world experiments, with an average false positive rate of 6.4," states the paper.
The method elaborated by the researchers obtained excellent results: the researchers were able to de-anonymize traffic with 100% accuracy with in-lab tests and achieved an accuracy of about 81 percent for live sessions.
Many experts speculate that the recent Operation Onymous, which allowed the seizure of several dark market places, may have exploited a traffic analysis attack against the Tor network to identify the operators of the black markets.
De-anonymize Tor users from their Bitcoin transactions
While the majority of Bitcoin users considers Bitcoin one of the most secure systems to pay online without being tracked by law enforcement, the members of Tor Project warned of the possibility that the recent Operation Onymous exploited the Bitcoin to identify the operators behind the seized black markets.
In effect, it is possible to de-anonymize clients in a Bitcoin P2P network, as demonstrated by a team of researchers working at the University of Luxembourg.
The researchers Alex Biryukov, Dmitry Khovratovich, and Ivan Pustogarov published a paper titled "Deanonymisation of clients in Bitcoin P2P network" to explain how to exploit a built-in flaw in the Bitcoin architecture to reveal the IP address of a client who makes a payment with the virtual currency.
The attack consists in generating a 'malformed message', faking that it had been sent by the user through the Bitcoin peer-to-peer network. These malformed messages cause the increase for the penalty score of the IP address, and if fake messages exceed 100, the IP could be banned for 24 hours.
The mechanism is implemented as a DoS protection and could be abused to separate Tor from Bitcoin.
The attackers force Bitcoin servers to refuse connections via Tor and other anonymity services. This results in clients using their actual IP addresses when connecting to other peers and thus being exposed to the main phase of the attack, which correlates pseudonyms with IP addresses. At this point, every time a user's client makes a connection to the Bitcoin server, its address will be revealed.
Resuming, if a Bitcoin client is proxying its connection over a Tor relay and sends malformed messages, the IP address of this relay will be banned after a specific number of messages, and the Bitcoin client will continue to work with its original IP address.
This technique allows the isolating of any target client from the entire Tor network, if the attacker is able to force the separation of Bitcoin clients from the entire Tor network by sending malformed messages to every Tor sever.
"For the time of writing there were 1008 Tor exit nodes. Thus the attack requires establishing 1008 connections and sending a few MBytes in data. This can be repeated for all Bitcoin servers, thus prohibiting all Tor connections for 24 hours at the cost of a million connections and less than 1 GByte of traffic. In case an IP address of a specific Bitcoin node can be spoofed, it can be banned as well," states the paper.
"Once the hacker knows this address, he can trick the Bitcoin server into revealing the IP address of the user," states the post.
The researchers described their technique with the following statements:
"The crucial idea of our attack is to identify each client by an octet of outgoing connections it establishes. This octet of Bitcoin peers [entry nodes] serves as a unique identifier of a client for the whole duration of a user session and will differentiate even those users who share the same NAT IP address.
"As soon as the attacker receives the transaction from just two to three entry nodes he can with very high probability link the transaction to a specific client."
The researchers explained in the paper that the anonymity in the Bitcoin virtual currency scheme is weak. Many features could be exploited to run a cyber attack on the crypto currency and reveal a user's identity.
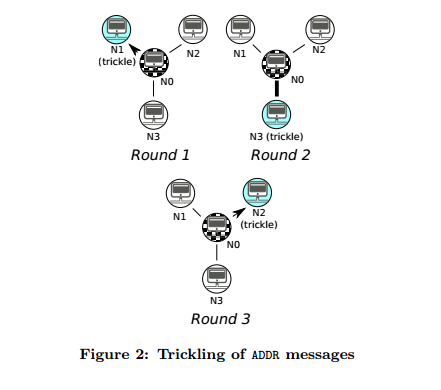
Figure 4 - Trickling of ADDR messages
The usage of Tor could increase the level of anonymity, but a hacker can always track users from their Bitcoin payments.
"We demonstrate that the use of Tor does not rule out the attack as Tor connections can be prohibited for the entire network. It shows that the level of network anonymity provided by Bitcoin is quite low. Several features of the Bitcoin protocol makes the attack possible. In particular, we emphasize that the stable set of only eight entry nodes is too small, as the majority of these nodes' connections can be captured by an attacker," states the paper.
Another problem related to the anonymity of Bitcoin is that the virtual currency's lack of a robust authentication system makes it easy for an attacker to cause nodes to blacklist the IP addresses of seemingly misbehaving connections.
"We figured out that very short messages may cause a day IP ban, which can be used to separate a given node or the entire network from anonymity services such as proxy servers or Tor. If the Bitcoin community wishes to use Tor, this part of the protocol must be reconsidered."
Experts at Tor Project speculated that a similar technique could have been exploited by law enforcement in the recent Operation Onymous against black markets in the Tor Network, allowing authorities to persecute their operators.
Mary-Ann Russon on the International Business Times reports that, as explained by researchers, a hacker could de-anonymize a Bitcoin user from its transactions through Tor for €1,500.
Not only de-anonymization … the seizure of the directory authorities
So far we have discussed the possibility of revealing the IP addresses of Tor users, however there is also the possibility of compromising the entire architecture, targeting critical components such as the directory authorities.
The Tor network relies on nine directory authorities located in the Europe and United States, which provide a signed list of all the relays of the Tor network. Experts at Tor Project highlighted that an attack to these servers can "incapacitate" the overall architecture of Tor.
"The Tor Project has learned that there may be an attempt to incapacitate our network in the next few days through the seizure of specialized servers in the network called directory authorities," Tor Project leader Roger Dingledine explained in a blog post.
"We are taking steps now to ensure the safety of our users, and our system is already built to be redundant so that users maintain anonymity even if the network is attacked. Tor remains safe to use … We hope that this attack doesn't occur; Tor is used by many good people."
The seizure of the directory authorities could have the primary target to sabotage the entire Tor network, but it would not be effective to reveal the identities of its users. An attacker, by seizing at least five of the directory authorities belonging to the Tor network, could force Tor clients to connect other relays.
This kind of attack could be conducted only by an actor that is interested in dismantling the Tor network. Experts speculate that law enforcement could run covert operations to block the infrastructure and hinder criminal crews that exploit the anonymizing system.
This could be a serious problem. Do not forget that the Tor network provides a safe network from surveillance and censorship for millions of people who live in repressive regimes.
"Every person has the right to privacy. This right is a foundation of a democratic society."

What should you learn next?
Sources
- Hacking Tor online anonymity
- Tor traffic analysis
- Law enforcement operation onymous
- Possible upcoming attempts disable Tor network
- Tor traffic analysis - Security affairs
- Operation onymous vs dark markets
- Techreport Columbia
- Bitcoin anonymity
- bitcoin anonymity there's way hackers find out your IP address










