Ethical hacking: Passive information gathering with Maltego
In this article, we’ll discuss passive information gathering. We’ll first look at how we can use Maltego, a common information-gathering tool, to perform this form of reconnaissance. Using a hands-on walkthrough of Maltego, we’ll see how you can acquire IP addresses, sub-domains and perform different levels of reconnaissance to inform your information gathering exercise.
What is information gathering?
During penetration testing (the hacking process), you will have to adhere to a methodology that will direct your hacking. Intelligence gathering is usually the first step. It is the process of acquiring intelligence on a target before we can begin attacking it.

What should you learn next?
There are two main types of information gathering that hackers can employ:
- Passive information gathering: Here, you acquire as much information as you can about the target without establishing any contact between yourself and the target. The chances of getting discovered here are extremely low, since you will be mostly leveraging information that is publicly available. There are numerous tools that can help you do this
- Active information gathering: Here, you acquire as much information as possible, yet establishing contact with the target. The chances of getting discovered here are much higher than when conducting passive information gathering. While using tools here, you need to be careful not to cause too much noise on the network in order to avoid detection by Intrusion Detection Systems and SIEMs
The importance of information gathering is that it informs your attack. You need to have as much information as possible in order to begin attacking your target. This is by far the most time-intensive step when performing penetration testing, as you will want to be aware of all the attack vectors that can be leveraged on before the pentesting can begin.
According to Christopher Truncer, a Red Teamer with Mandiant, “the chief difficulty is in identifying relevant, reliable sources from… publicly available info.” This step is time-consuming, but the rewards are very much worth it.
How can one perform information gathering?
Information gathering can discover a great deal of useful information, based on what type of information gathering is being conducted. You should aim to obtain as much information on a target as possible. According to Mark Czumak, “… just because you’re interested in www.target.gov, doesn’t mean you should restrict your passive recon activities to that address. If you do, you’re likely to miss some valuable information and/or vulnerabilities. WHOIS, Google, Maltego, Intercepting Proxies, Web Spiders, Netcraft, and sites such as Pastebin.com can all be useful resources.”
The types of information that can be discovered through passive information gathering include:
- Subdomains and public IP addresses
- Usernames and passwords
- Directory listing (directory indexes)
- Publicly available sensitive documents and files
- Leaked credentials
The types of information that can be discovered through active information gathering include:
- Drive shares
- Open ports on applications
- Application versions and platforms
- API keys
- Technologies used
- Infrastructure details
- IP address ranges
Now that we understand what intelligence gathering is, let’s discuss how we can use Maltego to achieve this.
What is Maltego?
Maltego is an application software used for open-source intelligence and forensics and is developed by Paterva. It focuses on providing a library of transforms for the discovery of data from open sources and visualizing that information in a graph format suitable for link analysis and data mining.
Imagine all the information one can acquire from whois lookup servers, or the information a DNS lookup tool can get from public DNS servers, or even emails and hostnames one can acquire from TheHarvester (using Google and Bing). Maltego does all that plus more, using the same open sources by help of transforms, then represents it all in one application and in an easy-to-visualize graphical way.
Paterva provides two licenses that can be used, a commercial version and a free version. We’ll focus on the free version, otherwise referred to as the “Community Edition.” This version comes pre-installed within Kali Linux
What features does Maltego provide?
Maltego CE, which is what we will be discussing to keep things as universally applicable as possible, comes with some limited features. These features include:
- The ability to share graphs in real time with multiple analysts in a single session
- The capability to return up to a maximum of 12 entities per transform for CE
- The provision of collection nodes which group together common features
- The ability to export in multiple formats including jpeg, PDF and GraphML
Note that the paid version will offer much more features than these listed above. Once you’ve worked with the free version for a while, you’ll have a better sense of whether you need the additional features in the commercial version.
How can I launch and run Maltego for information gathering?
To launch Maltego on the Kali Linux terminal, type maltego and press “enter” as shown below: [CLICK IMAGES TO ENLARGE]
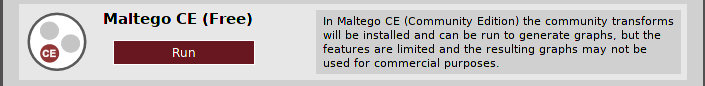
Once you have done that, choose “Maltego CE (Free)” as shown below, then click “Run”:
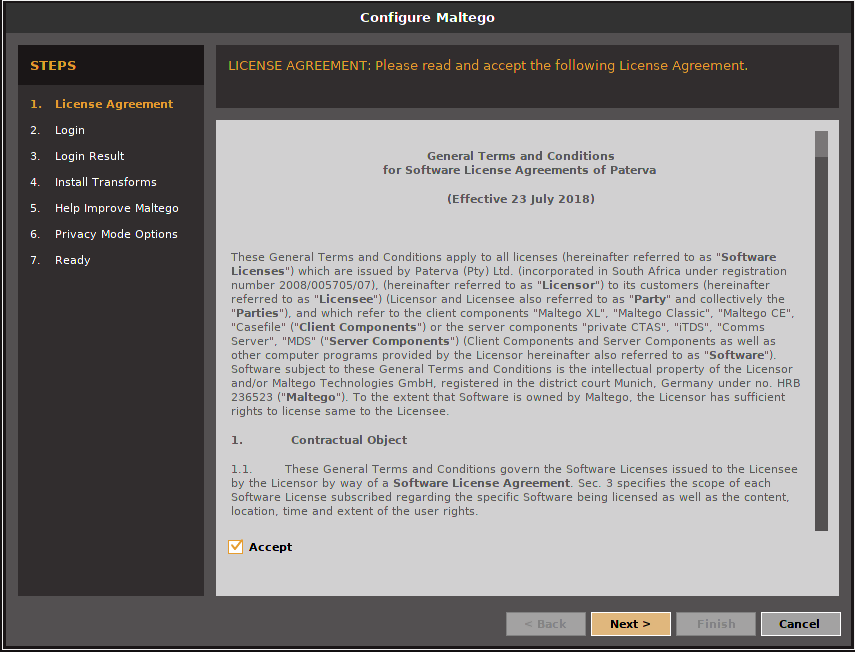
You will then be required to accept the license agreement. You can do this as shown below:
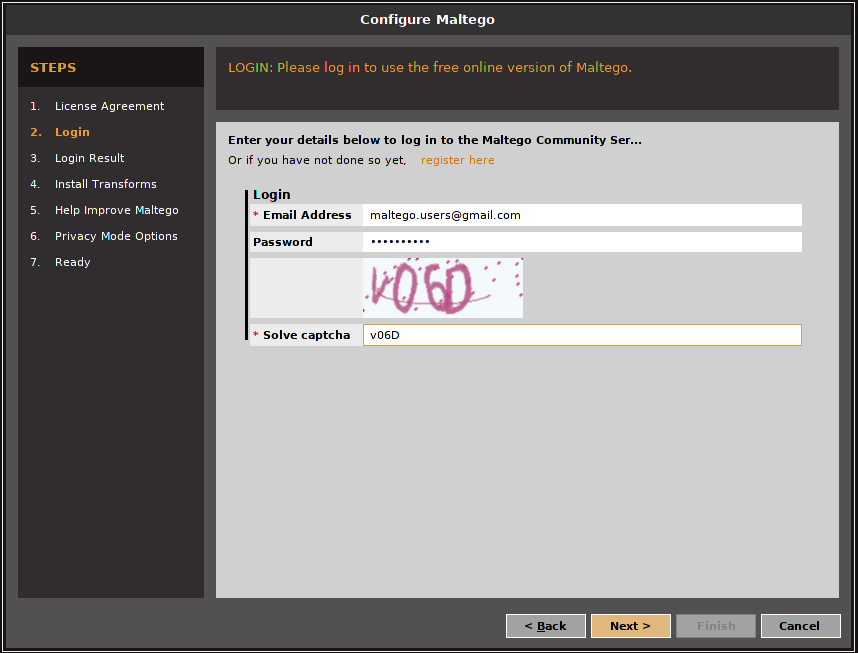
Press “Next,” then perform your login using the provided credentials below:
Username: maltego.users@gmail.com Password: Maltego210
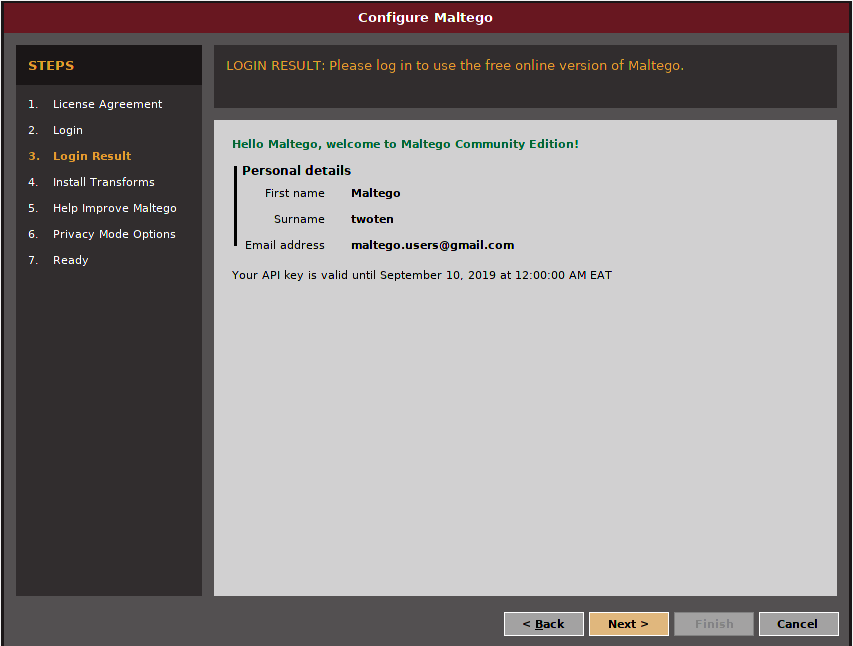
This can be seen below:
After the login is successful, you will see the screen below:
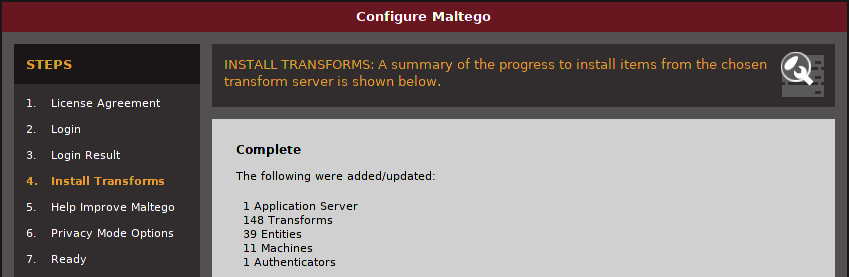
Once you are done, the transforms will get updated and you will have a result similar to the one below:
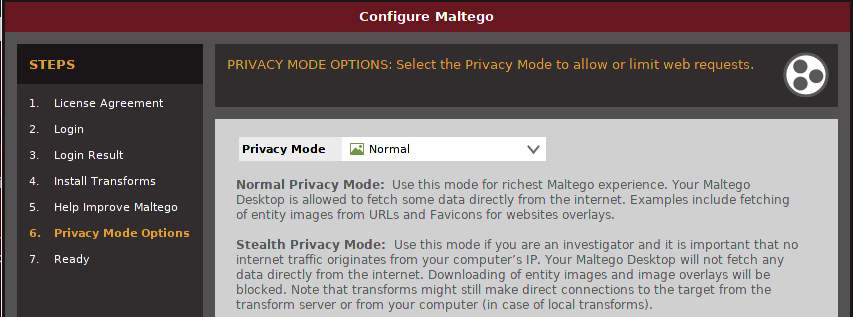
Press “Next” and you will have a screen asking you to help Maltego by sending error reports. Press “Next” again and select your privacy mode. We selected “Normal” in order to have the richest Maltego experience. See the screenshot below:
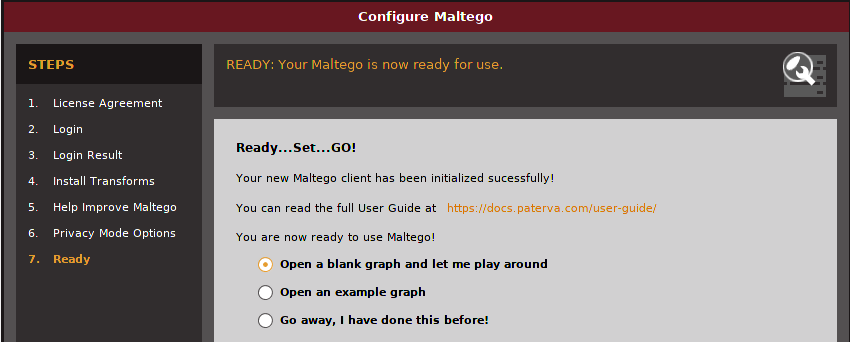
You will then be presented with the screen below. You can either choose to open a blank graph, open an example graph or ignore the two and proceed.
What are transforms and how can I run them within Maltego?
Transforms are pieces of code that fetch related information for given input. The fetched input is then formatted and returned as entities to Maltego. Transforms are extensible. This means that other transforms can run of their output.
In order to run a transform, one simply needs to drag and drop an item from the palette on the far left to the new launched Maltego tab. The item can be either of the many subcategories on the left, e.g., infrastructure, personal, location and so on.
Once an item has been dropped into the workspace, you can simply change the value/name by double-clicking on it and typing the desired value — say, by changing the domain to your target domain.
Under “Infrastructure,” we choose “Domain” and feed in infosecinstitute.com, replacing paterva.com. See the screenshot below:
To run a transform, simply right-click anywhere inside the current workspace and pick a transform of your choice. Maltego will do that and reply with a graphical display on the findings as well as the relationships. We right-clicked on our domain and selected “all transforms.” This is shown below:
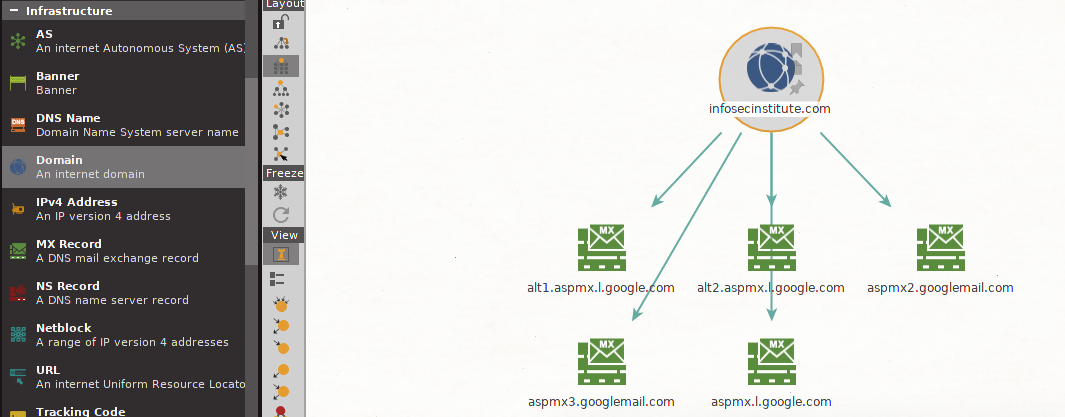
The screenshot below shows us selecting “To DNS Name - MX”. This transform returns all the mail servers as discovered by Maltego.
As can be seen below, Maltego returns all the discovered mail servers.
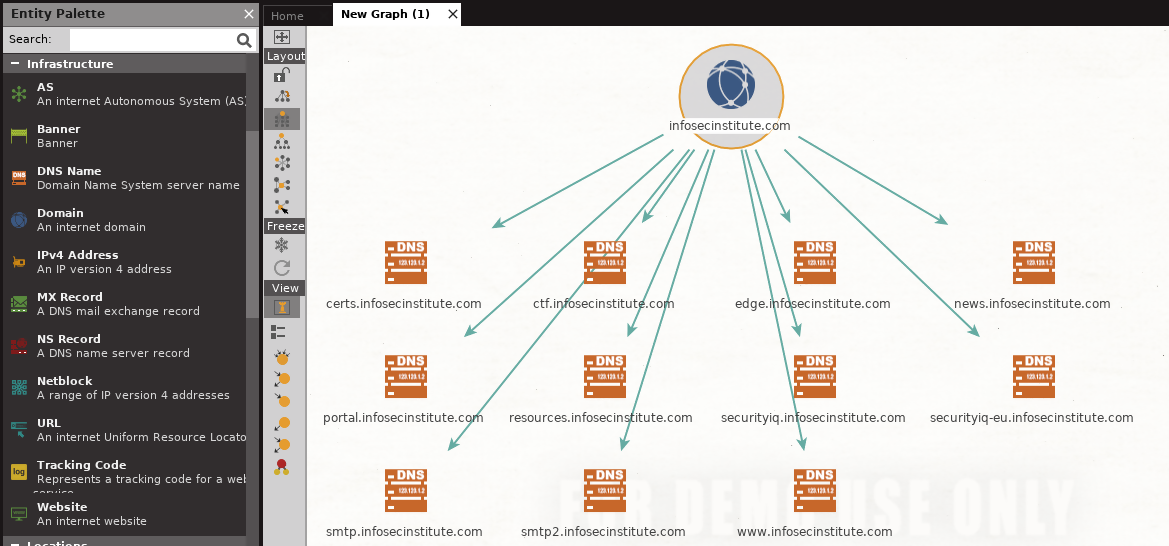
We can determine sub-domains belonging to infosecinstitute.com by using the “Robtex” database. We do this by selecting the “To DNS Name [Robtex]”. The following shows the discovered sub-domains:
We can also enumerate IP addresses using the “Shodan” transform. Shodan is an Open Source intelligence-gathering website where one can obtain information on people and devices (such as cameras, servers and printers). We can acquire this transform from the “Home” tab and “Transform Hub” tab. We need to include our Shodan API Key before we can use this transform.
Once we have done this, we can go to “All Transforms” after we have added our domain, then go to “ToDNSName [Shodan]”. From here, we can obtain DNS names that we did not previously enumerate. We can also go to “ToIPV4Address with hostname [Shodan]”. Here we can obtain IP addresses using Shodan, but through Maltego.
The screenshot below shows the discovered IP addresses and a new sub-domain which was not previously discovered above.
What are machines and how can I run them within Maltego?
Machines are scripts (or macros) which run multiple transforms with different filters. Machines are able to complete tasks such as forwarding footprints of domains. It is possible for you to create custom scripts using a custom scripting language. This is covered in Paterva’s developer portal. The available machines that you can run include:
- Company stalker: This machine will attempt to obtain email addresses from the given domain, check social networks for any relations and extract metadata, then document them
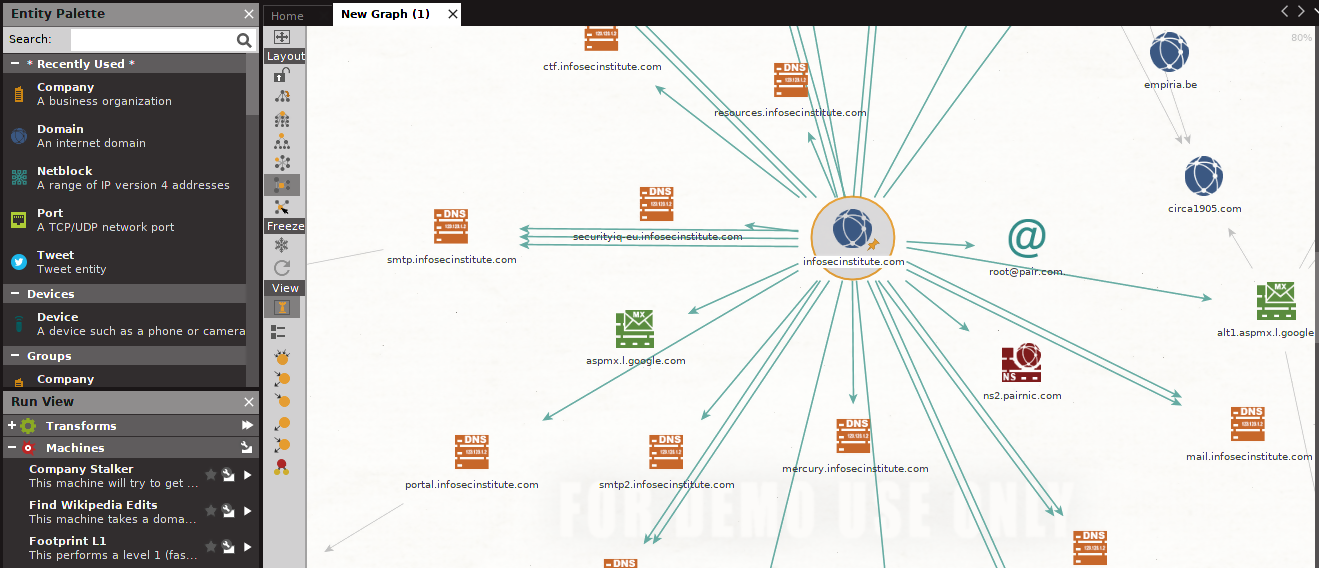
- Wikipedia edits: This machine will search Wikipedia for any available edits on a given domain. We ran the machine against our domain and were able to get the following graph output. Note that even though there were no Wikipedia edits, Maltego still enumerates a lot of similar information, as seen at the company stalker level
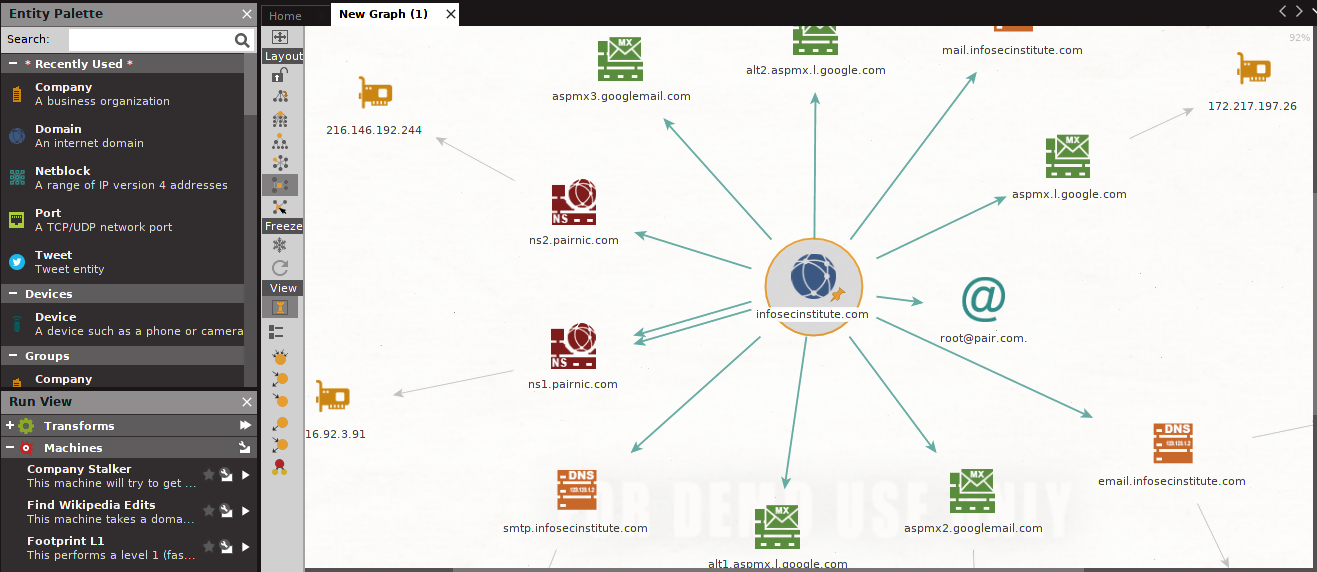
- Machine footprints: Footprints can be done as from L1 to L2 and L3. L1 footprinting is rather basic and quite fast, with L3 being the most resource-intensive level of foot printing. The screenshot below shows the graph we were able to obtain when we ran an L3 machine against the domain infosecinstitute.com
Notice that at this level, we are able to obtain much more information than at any other level above.
What are some other applications of Maltego?
We have now looked at the basic and most common use of Maltego. However, it can also be used to perform reconnaissance on:
- Provided infrastructure such as IPv4 addresses, DNS names, banners, NS records, network blocks and websites
- Provided locations such as circular areas and GPS coordinates
- Provided malware information such as hashes
- Provided network ports within a network (sometimes combined with banners)
- Provided personal information such as photos, email addresses, phone numbers and aliases
- Provided tweets, revealing as much information concerning them
It is possible to get very deep information when using Maltego. However, you should bear in mind that some transforms and machines are very resource-intensive and could cause your system to freeze.
Conclusion
In this article, we have looked at how Maltego can be used to perform information gathering on domains as targets. From a single domain, we have seen that it is possible to acquire more subdomains that can be used in an attack or pentest. We have also discussed the different machines that Maltego comes with. We have also seen that you can purchase transforms or install free ones.
Maltego is one of the most popular yet powerful passive intelligence-gathering tools available today. We encourage you to put the other features it provides to the test in order to appreciate its power. Have fun doing this and happy hacking!

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
Sources
- A Guide to Open Source Intelligence Gathering (OSINT), Medium
- Machines Tab, Maltego
- What is a transform?, Maltego
- What are the features of Maltego CE?, Maltego
- Passive Intelligence Gathering and Analytics - It’s all Just Metadata!, Troopers
- Passive Reconnaissance, Security Sift