Exploiting corporate printers
Printer exploitation and vulnerability in printers are serious problems, similar to those faced with computers and other hard drive devices, since they are connected to the network like other devices. Nowadays, most corporate offices or organizations have a large number of printers within their building, which print sensitive information's that can be hacked and exploited. In earlier times, printers just had the function to print the requested data. As technology developed, new printers were used with inbuilt memory and various security features.
Printer exploitation or vulnerability has resulted in increase of corporate espionage and gathering of highly sensitive information. The latest survey shows that more than two-thirds of the leading companies use 3D printing applications. Technology advancement has led to great improvement in printers, which has many advantages but also has various dark sides. Corporate organizations use printers ranging from various offset or digital printers to 3D printers. These printers installed in company networks have no security by default. Worst case is that most MFPs provide full administrative access until the network administrator reconfigures the network once in a while. This results in serious threats and misuse of data, creating a platform for attacking all the systems connected to the network. Therefore, unsecured multi-functional printers create a threat that can be utilized by spies or hackers.

What should you learn next?
Multi-function printers
An MFP is a device that can provide the functions of multiple devices. It is used in home for small footprint, in a small-scale business setting, or in a large-scale corporate company. A typical MFP is a mixture of various devices such as a fax, email, photocopier, scanner and printer.
MFPs are divided into two types: inkjet and laser. Inkjets are exceptional in creating high-quality color graphics while laser printers excel in printing large amounts of documents. MFPs are also divided into various segments. Depending on the features offered, there are four types: (i) All-in-one for a small office; (ii) SOHO MFP for a large desktop in small office; (iii) office MFP for a central office system; (iv) production, which is a printing MFP- reprographic department device.
MFPs contain many features, such as SDK, advanced LCD panels with optical mouse and keyboard attachments, wireless data capability, IPv6 support, storage capacity (HDD), active directory, SNMP support, editing capabilities, finishing capabilities, fax sending and receiving capability, forwarding to email (via SMTP), color fax capability, resolution DPI, direct CD/DVD label printing, automatic document feeder (ADF), security of scanned documents, cordless phone, TCP/IP fax methods, answering machine, and many more.
Internal architecture
Hardware: RAM, Processor, Digital Photocopier, storage memory- Flash memory or hard drive.
Software: They run on a set of platforms like PC operating system: Linux, VxWorks, Windows (NT 4.0 embedded, and XP embedded). MFP's provide various functions along with firmware. These softwares manage functions such as network service clients and servers, user input by MFP panel control, processing and conversion of images, remote management functions by Web server, raster image processing functions, internal hosting of third-party applications by Bytecode interpreters or virtual machines, configuration and administration of device, document imaging and management, input mode selection, monitoring of resources, etc.
Connection of printers to a network
Normal connections:
- Use of printers having built-in network capabilities:
As you know, printers can be installed very easily. The connection provided will be either cable-based or wireless. The setup process differs for each network printer. Network printers can be accessed either by DHCP (dynamic host configuration protocol) server or static network addressing. Static addressing is mainly used in small offices, while dynamic helps to automatically address each network in large corporate offices. After connecting from workstations, direct connections can be made. For example: In Windows OS, select Control Panel>Devices and Printers>Add Printer then wizard starts the search for printers.
Some printers having network enabled infrastructure are:
Inkjets: Epson B-510DN, HP OfficeJet Pro 8000 Wireless, etc.
Laser: Dell 5130cdn, HP CP4025dn, etc.
- Attach printer to exclusively allocated print server or network end point:
These processes include printers that don't have network-enabled capability. Non-network printers can be accessed through USB ports on the server and also through a parallel port that is connected to the network at another port. The server setup depends on the features included by manufactures and the device's complexity. The advantage of this type of printers is that after setup it seems similar to that of the network printers to the workstation. Some of the printers in this are low-end and high-end types, depending on their functional states:
Low-end: Netgear WGPPS606, Dlink DPR-1260, etc.
High-end: HP JetDirect EW2500, EdiMax PS-3103P, etc.
- Connect to workstation of computer to share with other users:
Another way to connect printers to a computer workstation is by connecting to a network of computers for sharing. Its advantage is that it can be easily accessed by the existing device and its disadvantage is that, even if the main workstation is turned off, others will have connectivity to the printers, which may be considered as vulnerability in some cases.
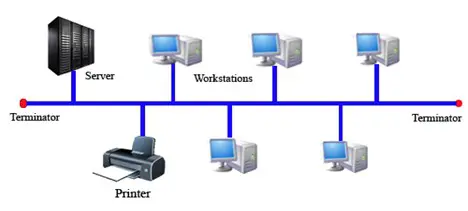
1: Printer connected to workstation
How do attacks happen in printers?
Printers are more vulnerable to attacks nowadays because most of the companies give importance to the security of the PC's in their offices. But the truth is, most of the highly sensitive data stored in PCs when printed are stored in printers that can be exploited from internal to reproduce the prints. Attacks can be done in different ways. Some of them are listed below:
- Authentication processes being bypassed:
Many of the MFP's in corporate settings have authentication mechanisms for controlling the users who are going to access the device. Thus each company can keep a log of employees using the printer. They have to log in with their credentials to unlock the MFP to use it, i.e., with an RFID key, fingerprint, swipe card, lightweight directory accessory protocol (LDAP). But most of these can be skipped by the MFP network access, allowing hackers to bypass the security and print the information.
- Work assigned to system users
A hacker can take advantage of the vulnerabilities in the printer and can modify the data pre-defined in the printer. The permissions assigned to different users may be different. Once bypassed, this information could be edited, depending on the hacker's requirement.
- Personal devices with OS
The mixture of mobile apps, cloud printing technology, and the continuous penetration of OS-based personal devices in companies has made it is easy for every attacker. An attacker could develop a malware for such device, which could be used to gain access to the printers connected in the network. After gaining access, the entire network can be bypassed easily.
- SQL injection
It's a type of attack in which the SQL function spyware is installed into the firmware by the attacker. The continued use of many web-based features or applications may lead to a phishing attack, through which the attacker deploys malware to the desired location. The threat level of the printer is same as that of a PC. Any person can access a MFP physically or electronically if they aren't securely controlled or protected, which leads to leakage of information from MFP tray or by maliciously accessing printed data from network.
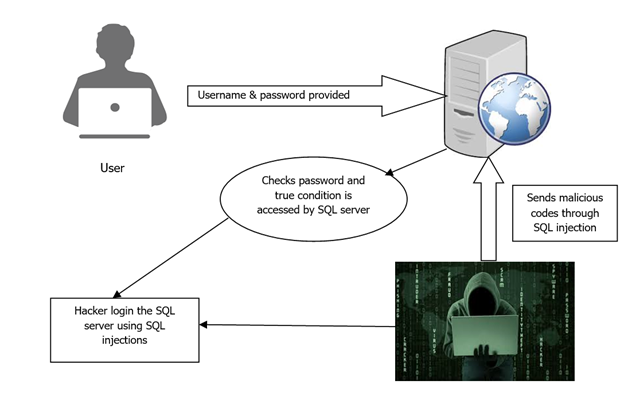
2: Steps carried out For SQL injection attack
- Denial of service
The amount of data to be printed varies according to the request made by the user. Since these all are processed through networks in MNC's, by increasing the traffic in such networks an attacker could bring down the device. The large number of request made by intruder might be a bit difficult to handle. This could result in the malfunction of the printer.
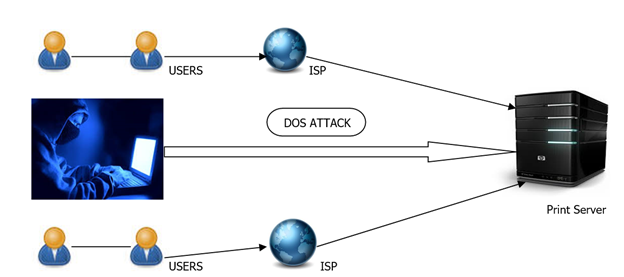
3: Denial of Service attack
- Device commissioning
Most of the corporate companies MFPs handle a large amount of information and disk drives integration. Access from unauthorized personnel gives sensitive information that is revealed by scanning. E.g.: The NYPD sold their MFPs, exposing details of an ongoing investigation during 2010.
- Network sniffer device
A chip can be replaced on printer's circuit board and also by firmware modification. It can be plugged into network's port of MFPs, which can be used to store or forward data packet information.
- HTTP attack
These management services have highly documented security problems. Cross-site scripting fools the user into connecting to web server of printer but actually is communicating to attacker.
- PJL attack
Printer job language sends printers status information to a program application. It controls file system along with printer's settings. It can be hacked easily by brute force attack. Many hacker tools are also available to grant full system access by changing the settings.
- FTP bounce attack
Anonymous FTP servers are used to drop print jobs into MFPs. Passive mode FTP provides passive FTP forwarding, making it vulnerable. This helps us to use it as a proxy server, which allow the hiding of IP address of the attacker, making it untraceable and redirecting without discovering of network attacks.
- SNMP attack
Most of the MFPs have backdoor administrator access. Attackers can access through a default password by SNMP (simple network management protocol), since it is stored in the SNMP variable from where anyone can access if they know location of variable or address of the MFP. Structure of the network can be obtained through just sniffing the SNMP traffic.
Some threats hackers cause while they exploit printers are:
Security and protection measures
Printer configuration varies according to different models along with its manufactures but security steps are almost similar for all. Many steps can be taken to strengthen the security of the MFPs. These could be mainly divided into three:
Steps to secure the printer:
- Configure according to default deny policy and secure password reset.
- Protect the network with efficient firewall hardware.
- Allow communications only with secured or trusted networks and hosts.
- Updating of printer firmware by administrator regularly.
- Available tools, such as digital management tools, should be used to secure sensitive data and information from loss or theft.
- Including MFPs in standard policies and regulations.
- Unused protocols (e.g.. AppleTalk) or services (e.g., telnet, web, ftp, and SNMP) are to be turned off. Also use secure options for printing if available.
- Utilization of access control list (ACL) in the product can restrict usage of MFP to a pre-defined set of clients.
- Change of network printer password and transmission of it in clear text over the network.
- Access control at the MFP and also level of functioning to individuals, groups, activities etc.
- MFP having direct software integrated device operating with whitelisting method. This means allowing of approved files and embedded system protection, thus providing tracking of time with the origin of the attack.
- Allow any enabled remote access services to create strong passwords.
- Enabling of SSL state for network management in the case of https for the encrypted network data transport.
- Configuration of syslog, which supports remote logging by connecting to network security's server or departmental monitoring server.
- Change of default community string.
- Allowing to send logs having genuine authentication.
- Use of services with remote control like FTP.
- Use of corporate-only network address so that MFP is not available to Internet or Web.
- Audit logging integrates real-time tracking by intrusion detection system obtaining potential risks.
- Usage of only digitally signed firmware by vendors.
- SNMPv3 for data encryption components with extensive secure capabilities for remote management.
- Separation of fax/network from each other.
- Use of NTP Protocol for clock synchronization.
- TCP connection and port filtering.
- Controlling network traffic by encryption and authentication.
- TLS to secure LDAP and having security templates.
- Auto insertion of email addresses, causing eradication of anonymous emails.
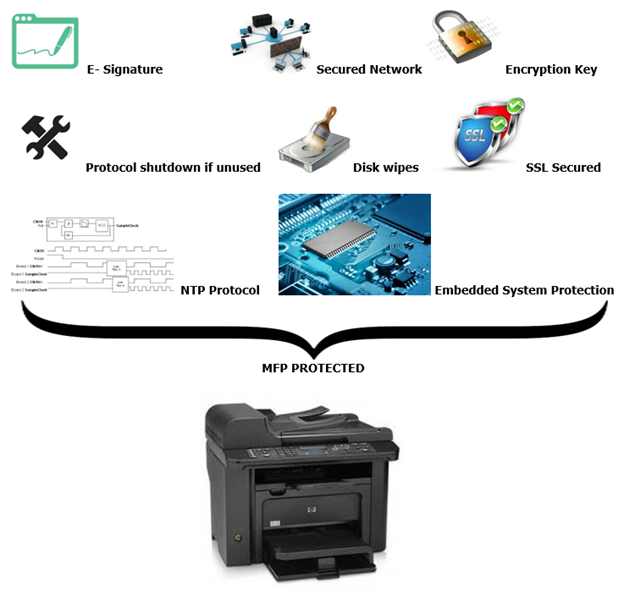
4: Functions used for MFP protection
- Confidential print will help remove print jobs in RAM after an elapsed time set.
- Encryption of hard disk with AES key and physical lock support.
- Both automatic disk and out-of-service disk wipe should be configured.
- Non-volatile memory wipe helps to clean forms of flash memory.
-
Check security of the data transmission across the workflow.
Normal steps for hacking network printers
MFPs can be hacked by concentrating on security problems from most of the brands. Mainly used protocols are Appstock/RAW, PCL, PJL, PS, IPX, etc. In most printers, when we search the address (not technical) http://your-printers-ip:9100, it will not lead to any location but it reads a print job. It gives a request for root document by https. This gives access to the LCD display, through which the attacker enters. This proves no need of any tools or code for access. For accessing through telnet: telnet 192.169.1.2 9100. NetCat accessing: e.g., echo @PJL RDYMSG DISP='Text' netcat –q 0 192.168.1.2 9100.
Next step is to obtain the password, since both telnet and the device password used are similar for software along with Web interface. All the passwords entered are registered into the registry when you use it, so sniffing tools and a brute force attack help to obtain the password from the printer's registry. SNMP vulnerability also allows getting the password just by interfering the community name of the network.
Many of the printers in a network could be found out by Nmap and SNMP tools along with an UDP scan. Printers can be also obtained from the Internet, since most administrators store data in an intranet, e.g., inurl:brand/device/this.LCDispatcher. Spam can be used to iterate the data by accessing tool in Windows and Linux. Network printers are easily exploitable to gain unauthorized access to data and Wi-Fi pin settings.
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Conclusion
The subject of network printer security is indeed a developing problem in corporate offices or organizations. Many numbers of vulnerabilities or threats or risks can happen to multi-functioning printers, but only some number of security measures. The efficient method is to provide assess or analyze the critical threats of the each corporate organizations and tackle them according to the risk occurring. So it is as necessary to consider the security of printer as that of PC, since both have large amounts of sensitive data and information.
Sources
- Security flaws leave networked printers open to attack
- Network printers an overlooked security threat
- Hidden IT security threat multifunction printers
- Chicago
- Hacking HP printers vulnerability wifi password
- Tens of millions of hp laserjet printers vulnerable to hacking
- Exploit cloud literally allow hackers to set HP printers
- Vulnerabilities and threats










