OSINT and pre-game show for a on-site WLAN Penetration Test
Wireless Penetration Testing in my opinion is one of the most fun parts of Ethical Hacking. It incorporates application exploits once you are on the WLAN/LAN, web application hacking to attack router web interfaces and a lot of networking trade craft. Needless to say gaining complete control of a WLAN is a daunting task. Luckily there are ways to prepare for our attacks before we even arrive on site and most importantly many of these preparatory measures are impossible or very difficult to detect. The reason these measures are so hard for a company or person to detect is the information we gain does not need to come from the target, and when it does the target gave that information to anyone who knows where to look. The focus of this article will be on how to use Open Sources of intelligence to give us an edge in the field.
Now for those who do not know Open Source intelligence or OSINT is the art and science of using publicly available sources to collect intelligence valuable to an attacker or competitor. Now OSINT can be applied to almost any form of penetration testing and hacking in general but this article is devoted to OSINT sources that can benefit a Wireless hacker. This article will also cover a list of suggested items and tools to bring when you arrive on site.

What should you learn next?

What should you learn next?
The First source of intelligence we will cover and by far one of the most effective is SHODAN. While Google is a search engine for web sites SHODAN is a search engine for the actual computers. SHODAN works by scanning ranges of IP addresses and domains for specific services and then storing the results in a publicly available website. While it is possible to use SHODAN for free doing so limits the number of results and what services it reveals to you. How ever at the time of this article's writing full access to SHODAN and a unlocked API key costs only 19 dollars and is well worth the cash. Now to make SHODAN work we need to give it a query, a query can be something as simple as "router" which will only show machines that SHODAN identified as a router or we can give it a HTTP(s),telnet,SSH or SIP banner and it will only show machines with that banner. Now like google there are advanced operators or "dorks" as some hackers call them. The ones most useful to a penetration tester are "net:" which when followed by an IP range will only display machines in that IP range that meet the parameters of the rest of the query and domain: which when followed by a domain name


there is a community of SHODAN users who submit dorks they have found for specific Internet connected technologies, on of the things that SHODAN advertises is its ability to locate nuclear power plants and other SCADA systems that are connected to the Internet. Using these dorks under the Search Directory category is straight forward, click the link and then append the target's IP range or domain to the query and if SHODAN has found machines that match that dork on that IP range or domain then relevant information on those machines will be displayed. By clicking the details link under the name of the country the machine is located in you can get a list of all services SHODAN has a record of being on that machine. Now this is all very useful for a penetration tester because it allows us to check if the target has critical network infrastructure facing the Internet. In some cases routers' telnet and web interfaces are facing the Internet allowing for remote administration. Some times it is even possible to extract the encryption key for a network from miles away!

Now Shodan can reveal other things that are useful for a wireless penetration test as well, the Shodan search directory is stocked with a wide array of dorks to locate various IP security Cameras, many of these Cameras have web interfaces with little to no security allowing a hacker to scout a location from the comfort of their own home (although this would not be OSINT).
What is probably the most ubiquitous source of OSINT for a pen test is google's very popular satellite image viewer Google Earth. Google earth gives us an bird's eye view of the Physical Layout of the target's location as well as any security measures that may be in place such as guard booths,checkpoints etc. What really makes Google Earth effective is its ability to go into street view where we can see any given location as if we where physically standing there
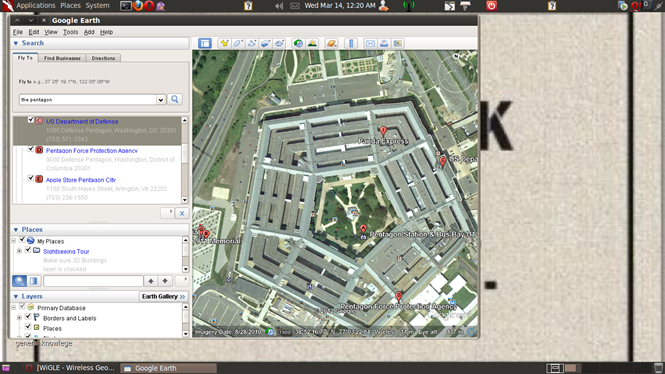

what makes Google earth especially useful for Wireless penetration testers is GPS coordinates in the form of a KML file can be turned into a marker on Google Earth's map.
There exists another geographic intelligence that is by far one of the most useful for wireless exploitation: Wiggle, Wiggle is a service that allows war drivers, or people who drive around areas looking for wireless networks and recording their details to upload their findings to a central database and map which allows searching via street address, MAC address or ESSID. Wiggle is extremely useful for a Wireless penetration tester because it not only records the ESSID, or network name but its physical address and its encryption and authentication types as well. An attacker armed with this data could generate a rainbow table to crack WPA personal encryption with out having to set foot on site. Wiggle has a web interface to view its worldwide database of wifi,GSM and CDMA networks but windows and Java clients are available but require map packs of the target area to be downloaded. It should be noted that while Wiggle is free it requires registration with the site to access data.

While technically not a Open Source of intelligence DNS records can provide a wealth of data useful to a Wireless hacker. DNS brute forcing, or looking up possible sub domains on a network from a list of common names is the most effective way of locating servers on a particular domain. One of the most efficient and simple tools to do DNS brute force enumeration is reverseraider in the backtrack toolkit under information gathering and DNS analysis , it can quickly and efficiently carry out a DNS brute force or a Reverse DNS brute force where it checks every address in a IP range for a DNS record. Both are effective methods of locating services on a network and getting an idea of how the network is set up. Using reveseraider is simple and the screen shots below show both a DNS brute force and a brute force in reverse:


as we can see reverseraider is a simple tool, you tell it what wordlist to use with -w and the wordlist's directory and -d and the domain you wish to enumerate or -r with the IP range you wish to scan. While many DNS servers block certain records from being accessed outside of their network many networks still leak records they should not. This is extremely useful for a wireless hacker because we can know what kind of servers they have by their name. For example if we see a server named radius.target.com we can assume they have a net logon system and possibly make use of PEAP or some other form of EAP for wireless security if they have a machine names ids.target.com or wids.target.com then we can assume they have a Intrusion Detection System and we best be on our guard when attacking this network. While some DNS enumeration tools make use of DNS Zone transfers to access DNS records that normally would not be accessable I do not recommend this for a penetration test because many IDS solutions are capable of detecting Zone transfers and alert administrators when they occur.
The Target's website can also give us insight into how their network works. For example if we see the website is made up entirely of ASP.NET web pages and uses IIS as a web server then we can assume that it is most likely a windows shop. Also when doing reconnaissance on the Target's web page look for information on partnerships and contracts with IT companies and security best practices. Another thing to look for is instructions on remote access and default passwords for employees as this will be useful when we actually attack the target.
Social Networking sites such as Facebook and Linkedin can offer insight into what kind of people the target hires as well as what companies they do business with. But what may be even more useful is that many IT professionals post their resume and credentials on Linkedin. This is very useful because it gives us insight into what kind of training their IT staff has and what vendors they prefer or use frequently as well as how much effort they will put into securing and monitoring their WLAN and LAN. Social networking sites such as Twitter and FourSquare can also reveal their working habits which can be used to determine an optimal time to attack. Also metadata on the images and other files they post on Social Networking sites can be used to ascertain what programs and Operating Systems they use. Social Networking sites often are a place where IT professionals vent about technical issues they have at work which can reveal information about the Target's IT setup. Finally Social Media is a great source of email addresses and other login names and credentials as well as information that can be used to generate a wordlist.
Another source of documents pertaining to technical or organizational procedures targets may use is a website called http://www.docstoc.com/ docstoc is a repository of documents ranging from IT stratigies to legal and business practices. This is very useful especially if the pen tester is attacking a company in an industry he or she is not familiar with so he or she could "bone up" to fit in the enviornment better or to Social Engineer them better.
Earlier in the article I mentioned that metadata can be extracted from documents the target's employees post on Social Networks there exists a tool called FOCA that not only extracts metadata from a target's website but it makes use of many of the tools and techniques we mentioned such as shodan, the target's website,DNS etc. how ever the goal of FOCA is not just a tool to enumerate these services but to extract and fingerprint metadata from documents on these servers.

One of the most revealing documents a target can put on the web is a Microsoft Word .doc file, these files can contain information on the machine that they where made on such as the version of the software used to make it, Operating System version and type and even user names and sometimes passwords of the user logged on at the documents creation.

All of which can be very useful to a wireless attacker. For example knowing what Operating system and word processor the target uses can be helpful when preparing a client side attack. And knowing the target's windows login information is always useful. While tools like FOCA and Maltego are advertised as all-in-one tools and many penetration testers use them as such I personally have found that all-in-one tools often generate false positives, miss things or are ineffective. In my opinion dedicated tools tend to be more accurate and offer related functionality that tools like Maltego can not. How ever Maltego does have it's uses, it is a great tool to visualize and organize data gained from other tools.

While not a source of intelligence on 802.11 networks it is still a highly comprehensive source of intelligence on wireless frequencies registered to a organization or physical location it is called radioreference.com this website is a source of FCC registered frequencies as well as those submitted and used by HAM radio operators not only does it keep records of the frequencies and related information but allows through a web interface to listen to those frequencies. This is useful if a target's security personnel use unencrypted radios letting an attacker monitor the target to determine when is the best time to attack the network.
To use Radioreference.com click the database button on the main page then click on the state on the map that your target is in and then the county, at this point you can scroll through all the registered frequencies in that area or click on the type of organization the target is and relevant information will be displayed. If you want to check if the target has unencrypted walkie-talkies that you can listen to on the top of that page is a tab saying Live Audio where you can see if your target is listed if it is click on the speaker icon next to its entry and a new tab will be opened where the audio on that frequency will be displayed.




Obviously the ability to listen to a target's security force operate can reveal not only security practices but lingo which can be useful in a social engineering attack.
The last source of OSINT I will cover in this article is EDGAR, EDGAR or the Electronic Data-Gathering, Analysis, and Retrieval system is a service provided by the United States Government's Securities and Exchange commission that makes many documents companies and governments operating in the United States publicly available. These documents can range from tax filings to quarterly reports. And can make understanding the scope of a target and the relationships it has with other companies and governments easier to understand. For a wireless attacker this is useful because he or she can infer from these documents what kind of technologies are used by the target. For example, if a company made a purchase of a large amount of surveillance equipment from a foreign company chances are they have extensive camera coverage. While EDGAR does not always help a wireless attacker it can help to give a target a quick query.

Now that we have enumerated services on the Target's network, did remote reconnaissance on the technical setup of the wireless network and it's physical location and have an idea of how the target is organized and how it's security staff operates. It is almost time to head out and conduct the penetration test. But first we must allocate the resources we may need for the attack. One thing we may need is a server running a metasploit listener on a pre determined port as well as a netcat listener also on a pre determined port. We also may need on that server a backdoor to download onto target machine or to inject via Man In the Middle attacks on the wireless network. We may want to download up to date exploits for various routers, this can be targeted based on information we gained from our OSINT sources. We obviously will need wifi adapters that support monitor mode and packet injection. We also may need access points for honeypot attacks. We may need GPS adapters to log key areas on site. We definitely will need a white list of ESSIDs and MAC addresses of the target's infrastructure as well as a document giving us permission to conduct the penetration test preferably signed by the target's chief security and information technology officers. We also may need a car with a full tank of gas assuming our reconnaissance with Google earth tells us it can be useful. We also may need prepaid cell phones and SIM cards to keep in contact with the rest of the team as well as for Social Engineering attacks.
But all of these things depend on the scope of the penetration test as well as the enviornment we are attacking. As you probably can tell our OSINT sources can help us weed out what preparatory work we need to do and what resources we need to allocate. At this point you are ready to go into the field and carry out a wireless penetration test with greater efficiency then if you where to go in blind. Bellow are links to all the tools used in this article although many of them can be found in backtrack 5 R2:
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
- reverseraider: http://complemento.sourceforge.net/
- SHODAN: http://www.shodanhq.com/
- Maltego:http://www.paterva.com/web5/
- http://www.informatica64.com/foca.aspx
- Wiggle: http://wigle.net/gps/gps/main
- Google earth: http://www.google.com/earth/index.html
- Radioreference: http://www.radioreference.com/
- docstoc: www.docstoc.com
- EDGAR: http://www.sec.gov/edgar/searchedgar/companysearch.html
Work cited
- "Company Search." U.S. Securities and Exchange Commission (Home Page). Web. 14 Mar. 2012. <http://www.sec.gov/edgar/searchedgar/companysearch.html>.
- "Plotting Wifi on Maps." Wiggle Wireless Geographic Logging Engine. Web. 14 Mar. 2012. <http://wigle.net/gps/gps/main>.
- "RadioReference.com - Scanner Frequencies and Radio Frequency Reference." RadioReference.com. Web. 14 Mar. 2012. <http://www.radioreference.com/>.
- "SHODAN - Computer Search Engine." SHODAN. Web. 14 Mar. 2012. <http://www.shodanhq.com/>.










