Windows exploit suggester – An easy way to find and exploit windows vulnerabilities
During our penetration testing engagements, we often come across the situations where we need to find the right exploits to escalate the privileges on a compromised host. Though there are multiple techniques to escalate the privileges, finding out missing patches could be an easy way if an exploit is publicly available. Blindly trying various exploits could be time-consuming process if most of them are failing. "Windows Exploit Suggester" is a tool developed in python to find out the missing patches and show us relevant exploits on windows platform. This tool can be useful for penetration testers, administrators as well as end users.
This article explains the following.

What should you learn next?
- How "Windows Exploit Suggester" tool can be leveraged to see if the host is exploitable
- Using the results to exploit a local privilege escalation vulnerability
- Patching the vulnerability
- Rechecking the vulnerability using "Windows exploit Suggester"
Getting ready with the setup
Following is the set up I have for this article.
- Kali v2.0 for running "Windows Exploit Suggester"
- An unpatched "Windows server 2003 R2"
Download "Windows Exploit Suggester" tool in Kali Linux here:
[download]
I am copying the zip file to my root directory to save some space on the terminal.
Once done, unzip the compressed file. You should see the python script inside the extracted folder. This looks as shown below.
This tool uses security bulletin database from Microsoft and checks against the hotfixes installed on the host. For this reason, we need to have the security bulletin database with us to use this tool. This tool makes our life easy by automatically downloading and saving the results into an excel spreadsheet using "—update" flag. This is shown below.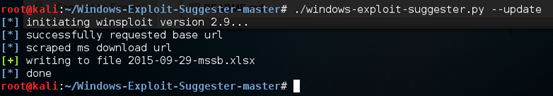
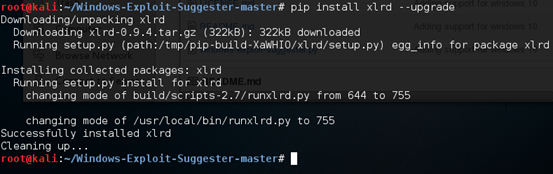
Then install the required dependencies using the command below.
pip install xlrd --upgrade
This completes the setup.
Checking for privilege escalation
Though this tool reports both remote and local exploits available, I am specifically looking for local privilege escalation exploits on the target machine.
This tool requires the output of "systeminfo" command to look for the installed hotfix data. So, let's get the output of "systeminfo" command from the target host as shown below.
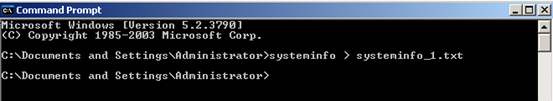
Place it in the folder where we have the python script. Now, we have the following files in the local machine.
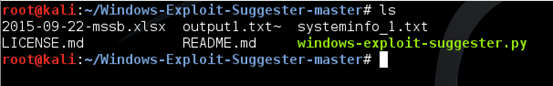
Run the following command, to get the information about the missing patches.
./windows-exploit-suggester.py --database 2015-09-22-mssb.xlsx --systeminfo systeminfo_1.txt
root@kali:~/Windows-Exploit-Suggester-master# ls
2015-09-22-mssb.xlsx LICENSE.md README.md systeminfo_1.txt windows-exploit-suggester.py
root@kali:~/Windows-Exploit-Suggester-master# ./windows-exploit-suggester.py --database 2015-09-22-mssb.xlsx --systeminfo systeminfo_1.txt
[*] initiating winsploit version 2.9...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (ascii)
[*] querying database file for potential vulnerabilities
[*] comparing the 1 hotfix(es) against the 473 potential bulletins(s) with a database of 115 known exploits
[*] there are now 473 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2003 SP2 32-bit'
[*]
[M] MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
[E] MS15-010: Vulnerabilities in Windows Kernel-Mode Driver Could Allow Remote Code Execution (3036220) - Critical
[E] MS14-070: Vulnerability in TCP/IP Could Allow Elevation of Privilege (2989935) - Important
[E] MS14-068: Vulnerability in Kerberos Could Allow Elevation of Privilege (3011780) - Critical
[M] MS14-064: Vulnerabilities in Windows OLE Could Allow Remote Code Execution (3011443) - Critical
[M] MS14-062: Vulnerability in Message Queuing Service Could Allow Elevation of Privilege (2993254) - Important
[M] MS14-058: Vulnerabilities in Kernel-Mode Driver Could Allow Remote Code Execution (3000061) - Critical
[E] MS14-035: Cumulative Security Update for Internet Explorer (2969262) - Critical
[E] MS14-029: Security Update for Internet Explorer (2962482) - Critical
[E] MS14-026: Vulnerability in .NET Framework Could Allow Elevation of Privilege (2958732) - Important
[M] MS14-012: Cumulative Security Update for Internet Explorer (2925418) - Critical
[M] MS14-009: Vulnerabilities in .NET Framework Could Allow Elevation of Privilege (2916607) - Important
[E] MS14-002: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (2914368) - Important
[E] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
[M] MS13-097: Cumulative Security Update for Internet Explorer (2898785) - Critical
[M] MS13-090: Cumulative Security Update of ActiveX Kill Bits (2900986) - Critical
[M] MS13-080: Cumulative Security Update for Internet Explorer (2879017) - Critical
[M] MS13-071: Vulnerability in Windows Theme File Could Allow Remote Code Execution (2864063) - Important
[M] MS13-069: Cumulative Security Update for Internet Explorer (2870699) - Critical
[M] MS13-059: Cumulative Security Update for Internet Explorer (2862772) - Critical
[M] MS13-055: Cumulative Security Update for Internet Explorer (2846071) - Critical
[M] MS13-053: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2850851) - Critical
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[M] MS11-080: Vulnerability in Ancillary Function Driver Could Allow Elevation of Privilege (2592799) - Important
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[M] MS10-015: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (977165) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[M] MS09-065: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (969947) - Critical
[M] MS09-053: Vulnerabilities in FTP Service for Internet Information Services Could Allow Remote Code Execution (975254) - Important
[M] MS09-020: Vulnerabilities in Internet Information Services (IIS) Could Allow Elevation of Privilege (970483) - Important
[M] MS09-004: Vulnerability in Microsoft SQL Server Could Allow Remote Code Execution (959420) - Important
[M] MS09-002: Cumulative Security Update for Internet Explorer (961260) (961260) - Critical
[M] MS09-001: Vulnerabilities in SMB Could Allow Remote Code Execution (958687) - Critical
[M] MS08-078: Security Update for Internet Explorer (960714) - Critical
[M] MS08-067: Vulnerability in Server Service Could Allow Remote Code Execution (958644) - Critical
[M] MS08-053: Vulnerability in Windows Media Encoder 9 Could Allow Remote Code Execution (954156) - Critical
[M] MS08-041: Vulnerability in the ActiveX Control for the Snapshot Viewer for Microsoft Access Could Allow Remote Code Execution (955617) - Critical
[E] MS08-025: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (941693) - Important
[M] MS07-064: Vulnerabilities in DirectX Could Allow Remote Code Execution (941568) - Critical
[M] MS07-029: Vulnerability in Windows DNS RPC Interface Could Allow Remote Code Execution (935966) - Critical
[M] MS07-017: Vulnerabilities in GDI Could Allow Remote Code Execution (925902) - Critical
[M] MS06-019: Vulnerability in Microsoft Exchange Could Allow Remote Code Execution (916803) - Critical
[*] done
root@kali:~/Windows-Exploit-Suggester-master#
As we can see in the above table, we have got various remote as well as local exploits found for this machine. This machine appears to be extremely vulnerable. Good News!
In the output, [M] suggests that there is a Metasploit module available for that bulletin. If it is [E], it has an exploit-db POC.
Among the list of vulnerabilities, I have highlighted one vulnerability ms10-015, which is one of the most popular privilege escalation exploits. You should have heard about it if you know what meterpreter "getsystem" does.
You can also see the popular ms08-067, which I am not going to touch here.
We can use "grep" command to filter out the output and thus we can have only local privilege escalation exploit list.
./windows-exploit-suggester.py --database 2015-09-22-mssb.xlsx --systeminfo systeminfo_1.txt | grep 'Elevation'
root@kali:~/Windows-Exploit-Suggester-master# ./windows-exploit-suggester.py --database 2015-09-22-mssb.xlsx --systeminfo systeminfo_1.txt | grep 'Elevation'
[M] MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
[E] MS14-070: Vulnerability in TCP/IP Could Allow Elevation of Privilege (2989935) - Important
[E] MS14-068: Vulnerability in Kerberos Could Allow Elevation of Privilege (3011780) - Critical
[M] MS14-062: Vulnerability in Message Queuing Service Could Allow Elevation of Privilege (2993254) - Important
[E] MS14-026: Vulnerability in .NET Framework Could Allow Elevation of Privilege (2958732) - Important
[M] MS14-009: Vulnerabilities in .NET Framework Could Allow Elevation of Privilege (2916607) - Important
[E] MS14-002: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (2914368) - Important
[E] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
[M] MS11-080: Vulnerability in Ancillary Function Driver Could Allow Elevation of Privilege (2592799) - Important
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-015: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (977165) - Important
[M] MS09-020: Vulnerabilities in Internet Information Services (IIS) Could Allow Elevation of Privilege (970483) - Important
[E] MS08-025: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (941693) - Important
root@kali:~/Windows-Exploit-Suggester-master#
The above code shows the list of local privilege escalation exploits.
Though the highlighted vulnerability is an old vulnerability, the idea here is to show the usage of Windows Exploit Suggester rather than focusing on which exploit we are working with. If you feel, this is a very old exploit, try ms15-051 that is very latest and it works like charm.
So, let's see MS10-015 in action.
KitrapOd exploit is available to exploit this vulnerability. KitrapOd can be downloaded from the Internet with little Google search.
First, let see the privileges of the currently logged in user using "whoami".
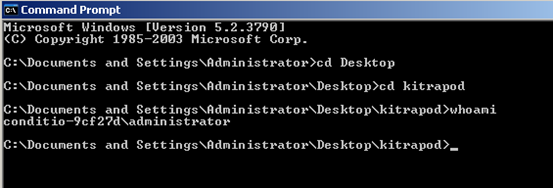
It is "Administrator"
Well, let's run kitrapOd and check the privileges.
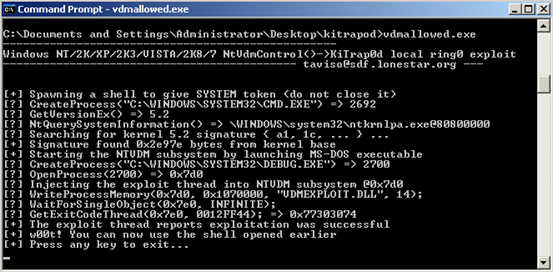
As we can see in the figure above, kitrapOd has successfully executed and launched a new shell with SYSTEM level privileges as shown below.
Let's check the privileges.
Woot! We got a shell with SYSTEM level privileges.
I just wanted to add another section to this article to show the accuracy of this tool when right information is provided to it. Among all those reported vulnerabilities, I left everything as is and applied a patch to fix MS10-015.
The hotfix is available at the following link.
http://www.microsoft.com/en-us/download/details.aspx?id=4324
Let's download and install the patch. I just added the screenshots with steps showing "PATCHING" vulnerabilities. This is for those who have never seen how difficult it is to apply a patch. Rest of the readers can skip this section.
- Download the hotfix
- Run the downloaded file
- Click next
- Check "I Agree" and click next
- Wait for a while J
- Click Finish and let the machine restart to apply changes.
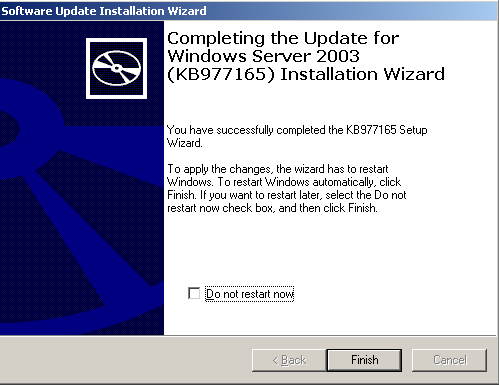
Difficult enough? ;)
That's it. We fixed the vulnerability.
Let's crosscheck the exploit once again to see if the vulnerability is fixed.
First, check the privileges of currently logged in user.
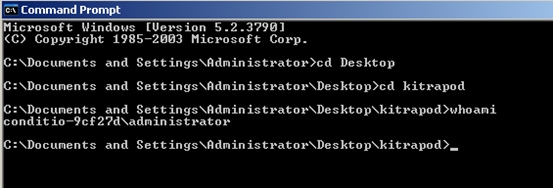
Run kitrapOd once again and check the privileges.
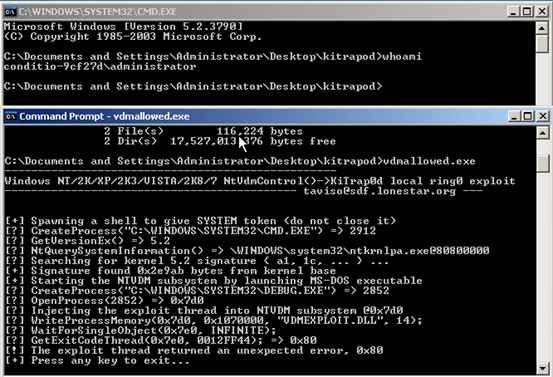
Exploit failed and no SYSTEM privileges. This is what is expected.
Let's re run the Windows Exploit Suggester tool to see if MS10-015 is missing from the output.
Get "systeminfo" output once again
Place it in the current directory.
Run the following command and check the output.
./windows-exploit-suggester.py --database 2015-09-29-mssb.xlsx --systeminfo systeminfo_2.txt | grep 'Elevation'
root@kali:~/Windows-Exploit-Suggester-master# ./windows-exploit-suggester.py --database 2015-09-29-mssb.xlsx --systeminfo systeminfo_2.txt | grep 'Elevation'
[M] MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
[E] MS14-070: Vulnerability in TCP/IP Could Allow Elevation of Privilege (2989935) - Important
[E] MS14-068: Vulnerability in Kerberos Could Allow Elevation of Privilege (3011780) - Critical
[M] MS14-062: Vulnerability in Message Queuing Service Could Allow Elevation of Privilege (2993254) - Important
[E] MS14-026: Vulnerability in .NET Framework Could Allow Elevation of Privilege (2958732) - Important
[M] MS14-009: Vulnerabilities in .NET Framework Could Allow Elevation of Privilege (2916607) - Important
[E] MS14-002: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (2914368) - Important
[E] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
[M] MS11-080: Vulnerability in Ancillary Function Driver Could Allow Elevation of Privilege (2592799) - Important
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS09-020: Vulnerabilities in Internet Information Services (IIS) Could Allow Elevation of Privilege (970483) - Important
[E] MS08-025: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (941693) - Important
root@kali:~/Windows-Exploit-Suggester-master#
As we can see in the output, this time ms10-15 is not reported.

FREE role-guided training plans
Limitations
Just like any other tool, it has its own limitations. One such limitation is false positives. Another limitation is not being able to automate the whole process in certain situations. According to its documentation, "if the "systeminfo" command reveals "File 1" as the output for hot fixes, this tool will not be able to determine which are installed on the target". In that case, we need to manually extract the hotfix information and feed it to this tool.










