QR Code: USSD attack
The QR code or Quick Response code was originally designed for industrial applications, and has quickly gained popularity in the advertising industry. With the huge popularity and sales in smartphone and tablets every year, these QR codes are beloved by marketers.
What a typical QR contains

What should you learn next?
- A QR code can contain an electronic version of the contact information.
- A QR code can contain event information. Scan the code on a poster and the app automatically adds its name and location to the agenda on your smartphone.
- A QR code can contain WIFI configuration data.
In my previous article: https://resources.infosecinstitute.com/what-is-behind-that-qr-code/ , I mentioned how attackers depend on human curiosity and the innate obfuscation of the QR codes to craft an attack. Various protocols invoking service set commands on the mobile devices are misused by exploiting vulnerabilities on mobile platform. QR codes are used as an attack vector to harm mobile users.

https://resources.infosecinstitute.com/what-is-behind-that-qr-code/
In this article, I shall demonstrate how QR codes can be misused to execute a remote attack on an Android device. There are tons of service list commands, also known as USSD (Unstructured Supplementary Service Data), which can be executed using this attack starting from displaying IMEI number to factory reset service command. But as far as this article is concerned, I will be limiting it to executing a USSD command to display IMEI number, since I do not want our readers to execute a factory reset command and wipe off their important data and settings on their own smart devices.
Here is a list of things we will require to perform a USSD attack. First of all we need an android smartphone. The one I will be using is an Android device with Froyo (2.2) platform. You can test it on the newer versions like 2.x, 3.x or 4.x series. There are plenty of vulnerable devices out there; you just need to find one which is susceptible to this attack.
Secondly, you need a QR code generator. There are plenty of generators available as Android apps, desktop applications, and online generators. Make sure whichever you use, it supports embedding a phone number in the QR code.
Third, you need a barcode scanner for your smart device. We will use this to scan QR code and to test if our device is susceptible to USSD attack. Select your favorite 2D/QR barcode scanner from the Android play store.
Finally, you will need the USSD code to display the IMEI number. The USSD service command is *#06#.
Let's get started with our experiment. Install you favorite QR code generator and fire it up. Click on the option which says "CALL" or "TELEPHONE NUMBER" and enter the USSD service command: *#06#. Finally, click on "Generate QR code".
Personally, I found http://goqr.me easy to use. This is an online QR code generator and does not require end users to download anything.
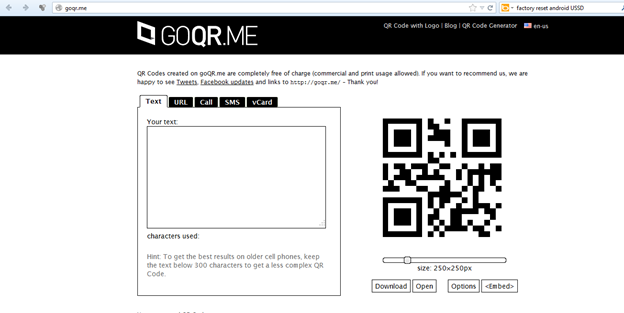
Head over to the above mentioned website, and click on the "Call" tab. Click on the text field stating "Telephone number:" and enter the USSD service command: *#06#. Automatically, a QR code will be generated on the right hand side of the browser screen. Click on the "Download" button.
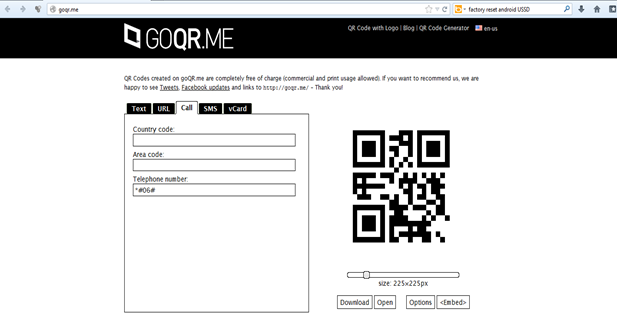
You will have a downloaded QR code that looks like this:

Now you require some social engineering skills to distribute this QR code to as many people as possible and make them scan it. One possible way is to tell them that this QR code is for free Android games or this QR code is my contact number. Try posting it on some public places; I am quite sure people out of sheer curiosity will scan the QR code. This is the biggest risk —that people cannot control their curiosity and you can use this to your own advantage and evil intent. You can find out 'n' number of ways to make people scan your malicious QR code; you just need to figure out the best one.
Fire up your QR code scanner on your smart android device and scan the QR code that you just downloaded. You will probably see a pop-up box showing a title named: "IMEI" followed by your 15 digit IMEI number.
See below:
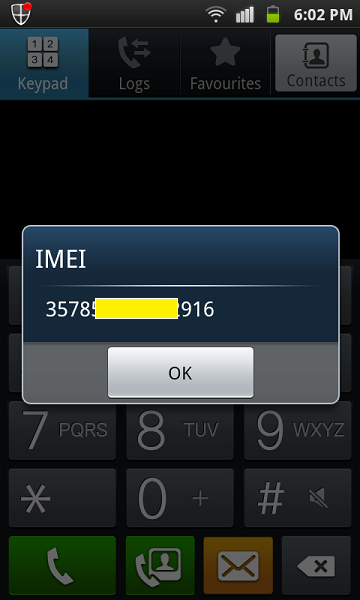
If you do not see the IMEI number like the above picture, consider yourself lucky. What does it mean? Well, in your case, your Android device is not susceptible to the USSD attack and your device is secure from such attacks. Cheers!
What if you do see the above screen and the IMEI number?
In this case, you need to update your Android device to the latest firmware. If there are no latest updates available for your device currently, download and install a dialer other than the default one, thus stopping the auto execution of any malicious USSD code.
After installing the new dialer, head over to http://mobtest.indianhans.org from your mobile's default browser or re-scan the QR code which you have generated and see if the problem still persists.
So what is happening?
We are trying to make the Android user execute the "tel" protocol which is available on mobile platform followed by the USSD code *#06# to display the pop-up box containing the mobile's IMEI number.
You can try various USSD service commands by embedding it in the QR code using the above procedure and see for yourself if they get executed.
The most harmful USSD code would be the Factory Reset command code. As soon as the victim scans the QR code, the tel protocol will get invoked followed by factory reset code and thus your all of your settings and data will be wiped out in matter of seconds.
Note:
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
- Only some devices or versions will be vulnerable to this attack. Some devices only execute the tel protocol and display a " *
" on the dialer screen.
- Don't try the factory reset code by embedding it in the QR code; you may lose your valuable information.
- The author is not liable to any harm done to whomsoever and to whatsoever. This article is intended only for educational purposes.
References:










