How to acquire a user’s facebook credentials, using the credential harvester attack
In this article you will see how you can obtain a user's Facebook credentials without him suspecting a thing. There are going to be provided two versions of this attack, one being locally in a private network and one being public, using port forwarding for the latter.
Before devoting yourself to the main body of this article, I would like to mention two things right from the very beginning. Firstly, DO NOT, UNDER NO CIRCUMSTANCE, try what you are about to see, to cause harm, assault, threat or have a leverage over a person (illegal, you get it). The purpose of this article is to show how it's done in regard to academic purposes (pass the knowledge on to everyone) and for testing purposes. Should you be given strict consent, act accordingly. Secondly, you must have Kali Linux installed or booted from a live CD or USB Flash before doing anything. So, check this article here explaining what Kali Linux is, if you haven't already.

What should you learn next?
A few more definitions so everything will be clear before witnessing some awesomeness. So, what's Social Engineering, SET, Site Cloner, Man-in-the-middle Attack, Phishing and Credential Harvester Attack?
SET (Social-Engineer Toolkit)
It is an open-source tool written in Python. It's a framework that offers a variety of tools regarding phishing, spoofing, etc. in Social Engineering environment, as the name suggests. It was created by TrustedSec and according to them, Social Engineering is one of the hardest attacks to protect against and nowadays one of the most prevalent.
Site Cloner, as the name suggests, is a tool that gives you the option to clone a website, locally. This means that your localhost, 127.0.0.1 will be running the desired website, provided that you enable the Apache service. You can find many details regarding Apache and running a website locally in the DVWA article, here (link).
Two very basic things before starting following the guide. Write down your private and your public IP. You can type "ifconfig" in a terminal window to display your private IP and as for the public IP, simply type on Google "what's my ip". If you know both IPs, skip this step. Also, you need to know how to use port forwarding on your router if you want to clone Facebook and target users outside your network, but more of that later on in the guide.
Local network
Without further ado, launch Kali, open a terminal window and type "service start apache" in order to start the Apache service and run the cloned website locally and then "setoolkit" in order to launch SET.
Next, type 1 for Social-Engineering Attacks and press Enter, then 2 for Website Attack Vectors and press Enter, then 3 for Credential Harvester Attack Method and press Enter, then 2 for Site Cloner and press Enter.
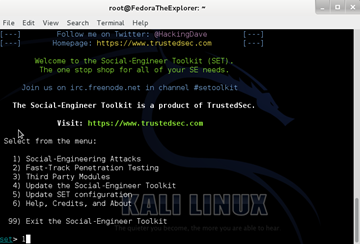
Type 1 for Social-Engineering Attacks and press Enter
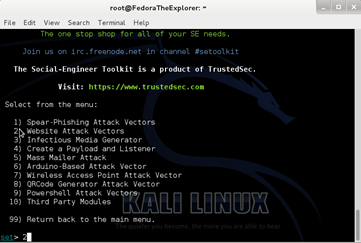
Then, type 2 for Website Attack Vectors and press Enter
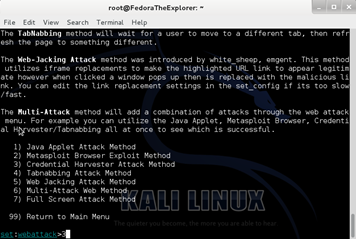
Then, type 3 for Credential Harvester Attack Method and press Enter
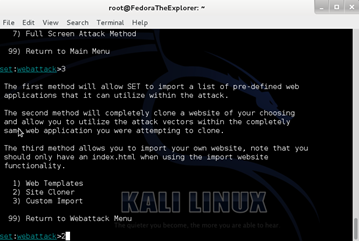
Then, type 2 for Site Cloner and press Enter
Now you are prompted to type the IP address. Both Private and Public IP methods will be presented, starting with Private IP. Go ahead and type your Private IP address and then press Enter. Next, type the desired website to be cloned, in our case, www.facebook.com and press Enter.
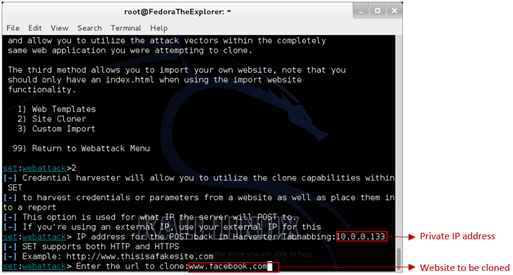
Type Private IP then press Enter, then type www.facebook.com and press Enter
Let's hold on for a second and review the procedure so far. By now, you have the option to access Facebook, by opening a Web browser and type www.facebook.com or if you are mad enough by typing one of its Public IP addresses, 173.252.120.6. Yet, you and everyone else in your local network can now access Facebook through you and by that I mean through your local Private IP address.
By now a cunning smile should be starting forming on your face as you realize that, if only everyone could access Facebook through you, by typing your Private IP address in the URL field, instead of the typical www.facebook.com. Yes, that would be awesome, because in that way you would be gathering/getting/harvesting all the credentials from the users that try to access Facebook through you. But, now you ask yourself why and how would people want to access Facebook through your Private IP and not with the original link. Fact is, they won't. Imagine yourself trying to persuade another person why he must access Facebook through your Private IP and not by typing the original link. With what lie would you come up with in order to persuade him/her? "Here, use this IP address to access Facebook, because insert imagination here". You could use some link shorteners like Bitly or Google URL Shortener, to transform that suspicious Private IP address of yours into a link that looks like every other shortened link. So yeah, now you got a not so suspicious link to access Facebook. However, the shortened link alone would have no effect to above average users.
If you combine that though, with yourself acting as a confident person in a library for example, letting everyone know around you that if everyone wants to join Facebook must use your shortened link for "security reasons". You could promote your link as "very secure", "encrypted", "insert epic lies here". And that's what Social Engineering is! Everyone will be using your link, users will type their credentials, you will be harvesting them and users will eventually access their Facebook profiles, because the network traffic will be automatically redirected from your computer (cloned Facebook) to the original Facebook. You and your computer will be acting as a man-in-the-middle. Think for a minute the above scenario. You won't persuade everyone, but a respectful amount of average users will fall for your story. That's why Social Engineering is the biggest vulnerability in almost every information system. You can't eliminate human error, can you?
Now that your cunny smile has grown bigger and you think of yourself as a master of the arts and crafts in roleplaying, let's proceed with the guide. The next screen you will be facing, after having typed www.facebook.com as the desired website to be cloned and pressed Enter, is the one below.
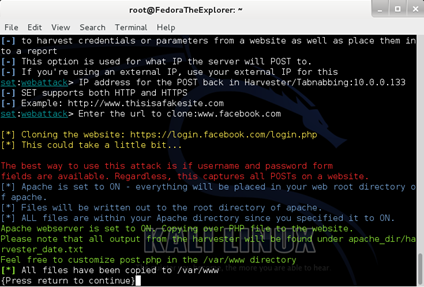
Waiting for credentials harvesting
You can find the text file in which the credentials are being saved, in /var/www directory. The name of the file should be something like "harvester_day time.txt".
A dummy demonstration will take place below, by clicking on the malicious link. Facebook pops up, so some fake credentials are typed.
Malicious shortened link
Fake credentials are typed
Afterwards, head over to /var/www through a terminal and type "ls" to verify that indeed there is a text file with the harvested information. Finally, open the text document with a text editor, like leafpad.
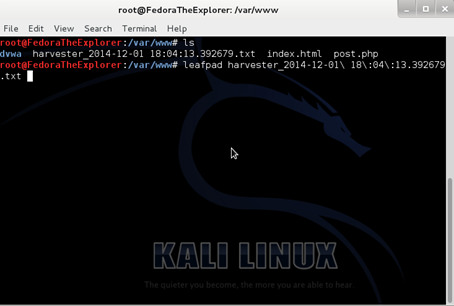
Verifying the created text document containing the harvested credentials
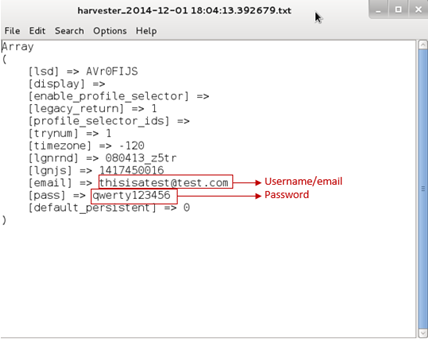
Harvested credentials
That's it ladies and gentlemen. You just got yourselves some nice credentials over there. And if you're very satisfied with what you just accomplished (you should feel satisfied and awesome) you can stop reading this guide at this point. By now, you have managed to harvest credentials from an unsuspected Facebook user in a local network.
Public network
If you want to take this a bit further and try to harvest credentials outside your local network and lure unsuspicious users towards you (your cloned website), two more things need to be taken into account. First, instead of typing your Private IP address when prompted in order to create the cloned website, you will now type your Public IP address. Secondly, you need to access your router, enable port forwarding and make a specific rule linking your Private IP address to your Public IP address.
So, go ahead and create that rule in your router. Due to the plethora of routers available, there's a variety of ways to create the port forwarding rule. It should look more or less like the screenshot below.
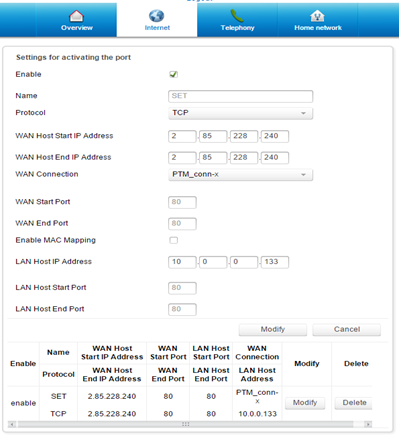
Port forwarding rule
Now you can follow all of the previous steps of this guide and when prompted to type the IP address, type your Public IP.
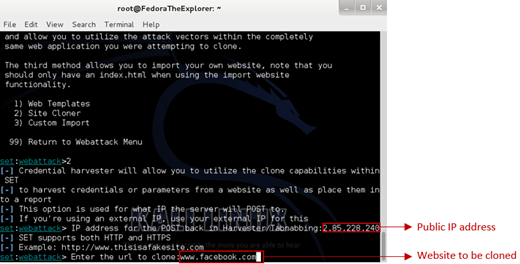
Type your Public IP address this time
Literally, the whole process is the same as doing it for a private network. Just don't forget to type your Public IP address and make a port forwarding rule in your router.
Give yourselves a round of applause, for you have reached the end of this guide. Cheers for making it until the end, after this long pile of text. Truth be told, this guide is quite thorough and extensive, but hey, think of all the new terms you learned and the euphoria you felt when you saw that you could actually get someone's Facebook credentials. Should your acting skills support you in the act of Social Engineering, you might get yourself some critical information over other users. Remember, credential harvesting could apply to even more crucial information, such as credit card numbers.
You just learned how to use a tool in Kali, now go practice your acting skills in order to be persuasive. Thank you very much for spending your time reading this guide. I hope you'll find it useful, easy to read and understand. Should any questions occur, don't hesitate to contact me.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
Check out this follow up article on DNS Spoofing/ARP poisoning for advanced SEToolkit attacks here: http://centralgeekhub.com/dns-spoofingarp-poisoning/










