Hacking ZigBee networks
What is ZigBee?
Internet of Things (IoT) is what most experts consider as the next step of the Internet revolution where physical objects are invariably linked to the real and virtual world at the same time. Connected devices now have the ability to communicate with one another through wireless channels, and ZigBee is the leading standard for wireless communication applicable to IoT devices.
Hence, ZigBee is an open global wireless standard designed to address the unique needs of intelligent device-to-device communication. It allows a great diversity of smart home applications to connect to the Internet (e.g., cloud service) and be controlled/monitored through ZigBee-enabled remote control. Compared to other wireless standards, ZigBee seems to be the best option for smart home:

What should you learn next?
By way of illustration: "ZigBee transmissions require 1/1,000th or less of the power required to transmit Wi-Fi (What Smart Home and IoT Devices Makers Need to Know about ZigBee 3.0 by Cees Links)."
Advantages of preferring ZigBee to the other standards: low power usage/long battery lifetime, the support of a considerable number of nodes in a single network (up –to 65,000), the simplified deployment, the low costs and worldwide usage.
The ZigBee standard operates on top of the IEEE 802.15.4 physical radio specification. The complete ZigBee protocol stack:
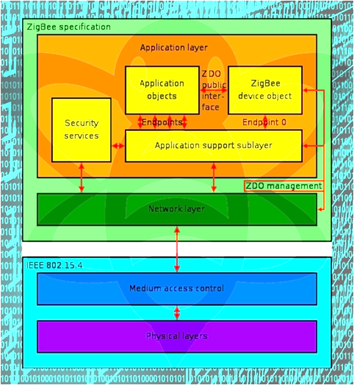
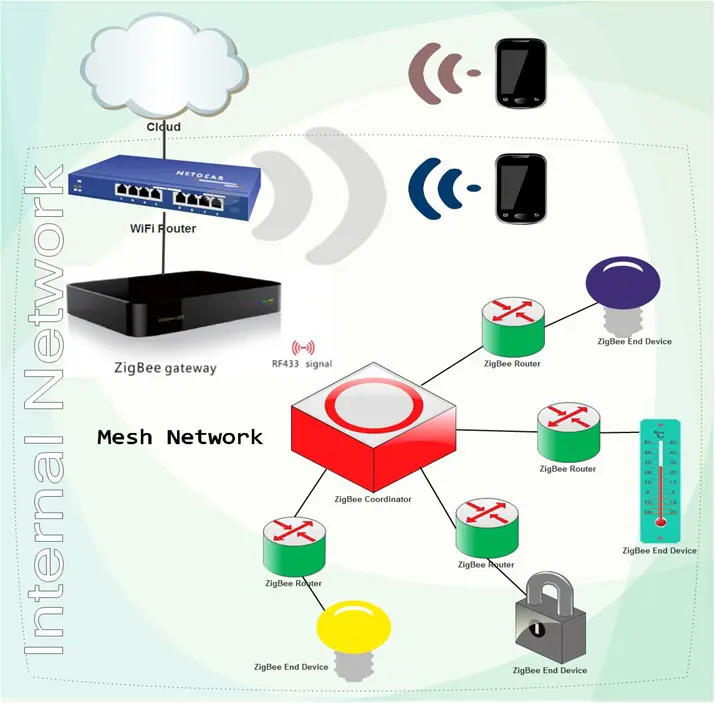
ZigBee is based on either a star or a mesh topology. The mesh topology expands the reach of networks and eliminates single points of failure. Some experts deem that its reliability increases with its growth – the more devices are connected, the better.
Overall, the creators of ZigBee made it secure, but there is enough evidence pointing to the contrary. Factors like low-cost units, usability and compatibility take precedence over implementing security, at least that is the opinion of several security researchers. This article presents some of the breakthrough findings concerning the security of ZigBee networks.
Security issues in ZigBee
Making ZigBee standard hack-proof is necessary to ensure secure networks, frame security, key transport and establishment. Security is implemented at the Network and the Application Support Sublayer (APS), which is a sub layer of the Application Layer. Cryptographic protection is on when different devices in the ZigBee network communicate with each other. Therefore, it is imperative encryption keys to be properly secured at all times. There are two types of security keys:
- Network key is a 128-bit key distributed and shared among every device in the network to secure broadcast communication.
- Link key, also 128-bits, serves as a means to secure unicast communication on Application layer, and it is shared only between two devices.
The security of ZigBee networks hinges on the presupposition that keys are securely stored and devices have the symmetric keys pre-installed so that they will not be transmitted in an unencrypted form. Nevertheless, making an exception to the general rule is how strongholds are seized – in this case, when a new and non-preconfigured device enters the network, then a single, unprotected key will likely be sent to allow for encrypted communication. Thus safekeeping the encryption keys, which is critical, will put the security of the entire network at risk. Despite that, the timeframe for such a security compromise is seemingly narrow; a hacker could utilize various techniques to take advantage of this vulnerability (See the "Empirical Evidence of ZigBee Vulnerabilities" part).
Another way to penetrate ZigBee networks is physically accessing some types of smart home devices such as temperature sensors and light switches. Due to their low cost and limited capabilities, it is assumed that their hardware is not tamper-resistant, which in turn might be just enough for the attacker to lay his hands on privileged information.
Types of theoretical attacks against ZigBee
ZigBee and the 802.15.4 protocol were designed with security in mind, but security is occasionally not well implemented by developers. The possible attacks can generally be classified into three categories: physical, key and replay/injection.
Physical attacks
A direct physical interaction may prove detrimental to the integrity of the targeted ZigBee network. In fact, many radios residing on this network employ a hard-coded encryption key loaded in the RAM memory once the device is powered. Being distributed, flashed, on all of the devices in a ZigBee network, the probability of replacing the keys is very low. Armed with this knowledge, hackers can resort to setting up special serial interfaces on the ZigBee device in order to intercept the encryption keys moved from flash to RAM during power up. This exploit can be executed with the help of various low-cost and open source tools, for example, GoodFet and Bus
Pirate: "Once physically connected to a ZigBee device through a simple serial interface such as a Bus Pirate, an attacker can unravel the security of an entire ZigBee network and potentially intercept and alter data."
Key attacks
Remote attacks aiming to snatch encryption keys are possible due to methodologies known as Over the Air (OTA) key delivery and pre-shared keying immanent to ZigBee. OTA is typically applied to more sophisticated ZigBee networks to ensure better security and updating. Its security protection can be circumvented with a device that mimics a ZigBee node and picks the transmissions exchanged among internal devices; these packets can be analyzed or decrypted later on. An attack of this kind will be almost impossible to detect. KillerBee is a toolset, combining hardware and software, which will effectively intercept and analyze 802.15.4 packets. Remote attacks also distinguish themselves with high stealthiness, and the intruder can even extend the range of coverage by creating high-powered transmitters or special Yagi antennas.
Replay and injection attacks
It is a key-based attack combined with packet replay and/or injection whose goal is to dupe ZigBee devices into executing unauthorized actions. ZigBee units are particularly vulnerable to these attacks, since they are equipped with a lightweight design of the protocol with weak replay protection. Hence, captured packets from ZigBee nodes are sent back in a replay attack scenario to make it look that they come from the originating node. The minimal session checking by the ZigBee units will not suffice to uncover the ruse, and the network will treat the traffic as if it arrives from a valid node (More on replay attacks on ZigBee networks here).
Empirical evidence of ZigBee vulnerabilities
The Austrian security researchers Tobias Zillner and Sebastian Strobl from Cognosec disclosed details on principle security weaknesses in ZigBee networks at the Black Hat USA 2015 in Las Vegas.
Application profiles is a unified functionality of ZigBee devices manufactured by different vendors that enables all these various devices to communicate. An example of an application profile would be the ZigBee Home Automation Public Application Profile (HAPAP) designed for exchanging control messages among wireless home automation applications – for instance, commands to turn a smart lamp on/off or sending an alert signal if the occupancy sensor detects movements.
All certified devices from each manufacturer should be able to use the standard interface and operability of this profile, but the key moment here is when an unconfigured device joins the ZigBee network for a first time. According to the Austrian experts, the way the default TC link key works poses a security threat to the secrecy of the network key. This fallback mechanism is activated "in the case where the joining device is unknown or has no specific authorization associated with it." The moment a device joins the ZigBee network via the default TC link key is therefore critical as it could lead to compromising the network key and from there the confidentiality of the whole network communication.
The Austrian researchers promoted in their report SecBee – a new ZigBee security testing tool based on killerbee and scapy-radio. They put it into use in order to assess the security of real life devices such as a home automation system, a ZigBee enabled door lock and a smart lighting solution. Characteristically to all three of them were the simplified setup and usage, but also the fact that the pairing procedure between configured and unconfigured devices lacks security robustness. Although the timeframe to sniff the exchanged network key is very limited, directing the hacking manoeuvre through the user level, i.e. attacking the user directly, can overcome this obstacle. The whole hack attack unfolds as follows:
- Signal jamming – ZigBee is designed for energy saving and low power communication, and targeting ZigBee channel with noise will easily obstruct communication;
- Re-pairing to restore connectivity
- Reconfiguration – a typical unaware user upon noticing a loss of connection will attempt to reconnect, usually by pressing a button on a remote control unit, for instance;
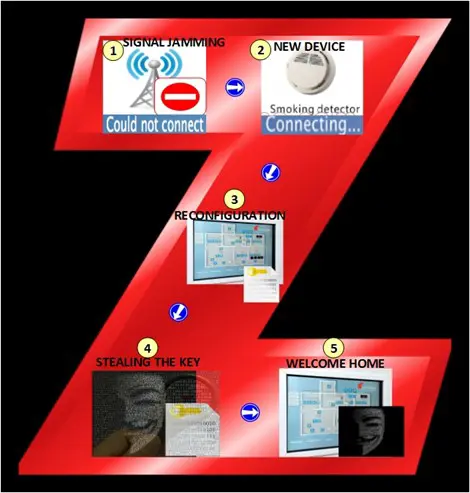
4. Acquiring the transmitted network key – as mentioned above, if the user is targeted successfully, the hacker will leverage the re-paring to his advantage and sniff the key;
5. The attacker will assume control over the system because the entire security hinges on the secrecy of the key.
The bad news does not end here. The tested home automation system has no setting that can reset or change the applied network key; hence, the average user cannot lock the intruder out.
The smart lighting solution is susceptible to a malicious attack as well. Unlike the previous case, hijacking smart light bulbs and linking them to a fake network do not necessitate knowing the active secret keys. Light bulbs are always sending  beacon requests in effort to find a new network to join. By sending a "reset to factory default" command, a hacker will make the bulb seek for ZigBee networks, which will join the first network available automatically, without even interacting with the user.
beacon requests in effort to find a new network to join. By sending a "reset to factory default" command, a hacker will make the bulb seek for ZigBee networks, which will join the first network available automatically, without even interacting with the user.
***
In addition, this ZigBee-specific quality of the network can be used for location purposes. A security expert from Praetorian, Paul West Jauregui, explains: "When [IoT devices] communicated over a wireless protocol called ZigBee, the protocol is open at a network level. Therefore, when the devices start connecting, they send out beacon requests. We capture data based on this."
can be used for location purposes. A security expert from Praetorian, Paul West Jauregui, explains: "When [IoT devices] communicated over a wireless protocol called ZigBee, the protocol is open at a network level. Therefore, when the devices start connecting, they send out beacon requests. We capture data based on this."

Under the so-called "Internet of Things Map Project," this Texas-based IT security firm successfully created a searchable database—Shodan— the first search engine for Internet-connected appliances. Perhaps it would be interesting to mention that information for Shodan is gathered via a Flying Drone with a custom-made tracking system capable of sniffing out data emitted by IoT devices. To illustrate its efficacy, researchers state that the drone managed to find almost 1,600 Internet-enabled devices throughout an 18-minute flight (see Austin, TX map here).
Other cases:
Not long before the publication of the research by Cognosec – less than a month or so – Tripwire reported security defects in smart home hubs. Smart hubs function as links to home networks for controlling lightning, locks and cameras.
Work by Nitesh Dhanjani back in 2013 displayed how Philips Hue light bulbs are "highly hackable" because of their control portal referred to as "the bridge," which relies on a feeble authentication system to exchange wireless communications with other devices. The MAC address of the bridge in its communications was easily discovered by Dhanjani when he injected malware into that bridge via a malicious website. With that being done, the targeted Hue bulb's takeover was completed – Dhanjani was able to switch on and off the smart bulb, regardless of the actual position of the switch, whenever he wanted.
One valuable presentation on hacking ZigBee, "I'm A Newbie Yet I Can Hack ZigBee – Take Unauthorized Control Over ZigBee Devices," carried out by Li Jun and Yang Qing of Qihoo360's Unicorn team, narrates how ZigBee-enabled appliance fell victim to hackers with the assistance of encryption keys founded in firmware.
Conclusion
It is predicted that there will be more than 500 smart devices per household by 2022. There are serious privacy concerns arising from home automation since it generates immense amounts of data that is linkable to a person. Vendors need to address security and privacy issues as soon as possible in order to mitigate the threats.
ZigBee is a reliable standard when it is applied properly. However, this article showed that for some reason or other the reality is different at times. With this regard, Tobias Zillner from Cognosec concludes:
"The shortfalls and limitations […] discovered in ZigBee have been created by the manufacturers. Companies want to create the latest and greatest products, which today means they are likely to be internet connected. Simple units such as light switches have to be compatible with a whole host of other devices and, unsurprisingly, little consideration is made to security requirements – most likely to keep costs down. Unfortunately, the security risk in this last-tier wireless communication standard can therefore be considered as very high."
Ms. Smith summarized very well what security measures need to be taken on the implementation side, according to Zillner:

Sizeable deals between market players are already shaping the niche of smart home products, which is expected to reach $71 billion by 2018. ZigBee is the platform they run on, so all potential customers will value implementation performed without trade-offs between security and convenience, even if it would mean that the IoT products would have to arrive at market with a small delay. After all:
A smart home is safe home.
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Sources
- Bowers, B. (2012). ZigBee Wireless Security: A New Age Penetration Tester's Toolkit.
- Condliffe, J. (2013). Philips Hue Light Bulbs Are Highly Hackable.
- Dhanjani, N. (2013). Hacking Lightbulbs.
- Hayes, J. (2015). Zigbee's wireless security flaws threatens IoT devices.
- Kumar, M. (2015). How Drones Can Find and Hack Internet-of-Things Devices From the Sky.
- Leyden, J. (2015). Cyber poltergeist threat discovered in Internet of Stuff hubs.
- Links, C. (2015). What Smart Home and IoT Devices Makers Need to Know about ZigBee 3.0.
- Meyer, R. (2012). Security Issues and Vulnerability Assessment of ZigBee Enabled Home Area Network Implementations.
- Ms. Smith (2015). Researchers exploit ZigBee security flaws that compromise security of smart homes.
- Pullen, J.P. (2015). Everything You Need to Know About Smart Home Networking.
- The Register (2015). Researchers make SHODAN of the skies to probe internet-of-things.
- Zillner, T. (2015). ZigBee Exploited: The good, the bad and the ugly. Available at(10/15/2015)
- The table in this article is based on "Table 3 Wireless technology comparison" that can be found on p. 15 of "Security Issues and Vulnerability Assessment of ZigBee Enabled Home Area Network Implementations" by Roger Meyer
- In the drone image is used "Darstellung der von Taifun Haiyan betroffenen Gebäude"










