How do I go about hacking file transfer protocol? Part I
Usually, I write about human resource management, risk assessment and project estimation almost every day, but from time to time, I get an e-mail from InfoSec asking for purely technological articles. So I start to look for topics that interest me and have fun, and sometimes, if I'm lucky, I can find something really nice.
I've always wondered what the risks are when transferring files between machines using FTP, so I decided to look at the matter closely. With the few items that I'll discuss below, you will learn how to take over an FTP connection and what you can do with it. It will definitely be interesting, I promise.

What should you learn next?
Foreword
Sometimes, there's a very high activity on TCP port 21. Most of this is related to nothing other than the search for anonymous FTP servers. Most of the servers allow for completely anonymous writing and reading of data. That is why servers of this type are very attractive to the hundreds of people who are looking for places to store illegal software. In addition, as we all know, FTP is not secure and you can still find very serious gaps in its implementations. Mostly, this is a buffer overflow, but not always. Sometimes this unusually strong activity on port 21 is an attempt to scan and identify potential holes of the web server.
Unfortunately, it's not easy to unlearn things. Most business users and private FTP account holders believe that despite all evidence, the protocol is secure. Users are not really very careful when saving files on FTP servers. They send there practically everything, such as personal photos or confidential documents that should never see the light of day, which by their activity, can be very easy to find. In fact, every file thrown in to the FTP server is generally available to the public and I really would not have too much bother to get it.
FTP, or File Transfer Protocol, is one of the most popular file transfer protocols on the network. After reading its specifications, it appears that this protocol has been purged of a lot of errors related to data security. Have you thought about what they may really consist of? The fact is that there are so many possible security flaws in FTP that can be a real threat to its users? If the threat is really there, how do we, as administrators and users, defend ourselves? This article is really my attempt to answer these and many other questions related to FTP. So get ready to have fun with File Transfer Protocol.
Anyway what is FTP really?
A lot of times I wondered what it was really that File Transfer Protocol was designed for. After reading the technical specifications, several options occurred to me. First, it's to promote the common use of files and software. In addition, at the beginning of the existence of the network, this protocol was made primarily to encourage the remote use of computers. But the truth is, today, FTP is used mainly for very accurate and efficient file transmission in computer networks.
Do you know what really demonstrates the success of this protocol? First of all, FTP can be used both by users on a terminal and by other programs, though it was really designed primarily for the latter. There is also another feature of this protocol, which earned its popularity. Read the specifications for FTP and draw conclusions. I suggest the following. Now, the entire specification of the FTP protocol actually puts its main focus on meeting all the needs of its users, those that are related to transferring files between computers, and at the same time preserving some very important features.
How does FTP really work?
I always find myself needing to know in depth how it all really works and whether the algorithm of the program has any defects. So let's look at how FTP works. Basically, to be able to start using FTP, a client runs a client program that connects to port 21 of the server computer and the software that is used to share files. This type of connection to the server is called a control connection. It allows the client to transmit commands to the server, which then responds to them. Most commonly used FTP commands are shown below:
- ABOR - stops the any running command or data transfer
- LIST - displays a list of files and directories
- PASS - sends the password you used to log on
- QUIT - allows you to log out from the server
- RETR - allows you to download the file
- STOR - allows you to place your files
- SYST - the server returns all kinds of information about the type of system
- TYPE - allows you to specify the type of the file
- USER - allows you to get or send the user name
Of course, all of these commands are also in the FTP specification, so there should be no problem with them, but how does FTP really work? The easiest way to understand the protocol in practice is by observing the communication between the client and the server. This session presents an anonymous call to the server to download any http://ftp.stratus.com/ file:
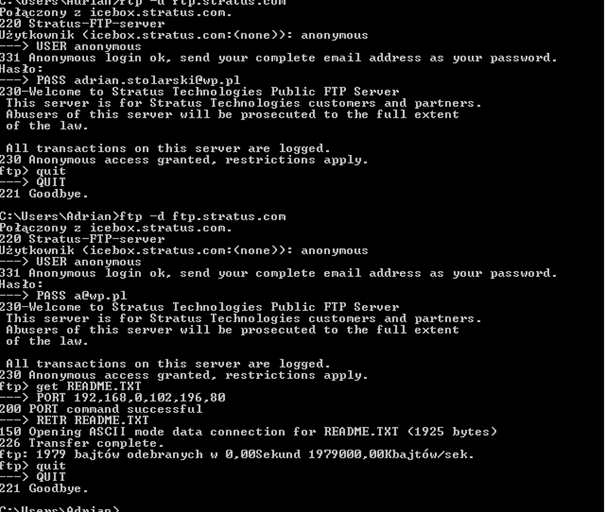
This example demonstrates the README.TXT file download. The client has been started with the -d command so that we see onscreen commands, which are entered and all server responses, which are replaced by a combination of steering. All lines of what the client sends to the file server start with -> have been sent from the client to the file server. However, in our example, all the lines that begin with a three-digit number are the file server responses. Also, the interactive command line is actually ftp>.
As you can see in the attached picture, an FTP session really is nothing big or anything complicated. But we must note one thing. In addition to a control connection, which, as already mentioned, is when commands are sent between client and server, FTP actually uses another type of connection, called the data connection. This connection is used to transfer specific files and is actually compiled only in situations where there is really a need to send data between computers. In our case it is compiled only when the README.TXT file was grabbed. As we can see, the control connection exists throughout the FTP session, that is, from the moment you log on as any user, download files, and even change the directory from you're on until the user logs off. However, the data connection is actually established and terminated several times during a single FTP session. So, as you can see, it really is a combination of connections during each downloading of a single file, while sending each file and displaying the contents of a directory.
A little bit about the types of FTP connections
One of the most frequently asked questions directly related to the firewall and the thousands of other issues about communication is, what really is the difference between active and passive mode FTP and how to handle them. So I decided to write briefly about this, despite the fact that the subject will develop later in the rest of this article.
Compiling an FTP connection can be done in two modes: active mode and passive mode. How do they actually look like in practice? When using the active mode, the client actually opens one of its ports, and then asks the server to be connected to this port. However, sometimes the situation is you are behind a firewall that has blocked incoming calls to unusual ports. How does it look then? In this situation, the client uses the passive mode. This mode differs from the active mode in that it's not the client but the server who opens one of its ports, and then the client initiates the connection with the selected port. To compile a data connection, the PORT command is used. It is a means for two applications to exchange information on the selected ports, which will be performed on route.
Why do I get tired so much about compiling a data connection?
The answer is simple. In this cycle, you want to really bring an FTP error that occurs during the compilation of a data connection. So in this section tell the merger of data. Have you ever wondered to what tasks it is used? Well, it is, as I mentioned three main tasks:
- Transferring files from the client to the server
- Transferring files from the server to the client
- Send a list of files from the server to the client
As we said earlier, something that is called the lead connection is active all the time during the session. However, in the case of a data connection, it is established at that time and closed in accordance with user needs. How is this done? Or is this just a special mode? But of course it is. This mode really exists and is commonly used when transferring data. It is called stream mode. In this case, the connection is closed at the end of the download. How does it look? For each file and list of files in a directory, a new data connection is created. However, when it comes to the way in which they are actually selected port numbers and the information that the page is in active mode, and that the passive, it really only differs depending on the selected mode. (sorry, this is so bad)
Summary
In this article, we started only on the basics, which should make it easier to use FTP and understand how it really works. Despite the fact that this knowledge should be publicly available and communicated to everyone, it isn't so. Amazingly in universities, where everyone should talk about it, it's only discussed very briefly.
I understand that these are the absolute basics of File Transfer Protocol and some of you may seem bored with them, but in the case where we want to thoroughly understand a subject, we need the basic knowledge of the how it works. And then the trouble begins, because I do not know how to go about conducting an audit or a controlled break.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
On the next part of this series about FTP hacking, we return a bit to the active and passive mode and look at them in practice before we describe the preparations needed for an attack. Then, on part three, we consider the various ways to attack FTP, followed by how to carry out a full attack on part four, which I hope will be successful. Stay tuned for the next articles in this series and I promise it will be worth it.










