Hacking Drones … Overview of the Main Threats
Introduction
The Unmanned Aerial Vehicles (UAVs), also known as drones, represent a revolution in the security context; these powerful systems could be used in various contexts such as military and also civil sector.
Drones use most advanced technological equipment and the research on these vehicles is providing continuous improvements, the scope is the definition of a new generation of UAVs characterized by high performance, high autonomy, extreme versatility which makes their use suitable for many uses.
Drones are sensibly transforming military operations. Every day it is possible to read about strikes conducted by Unmanned Aerial Vehicles in critical areas of the planet. Drones are remotely controlled airborne systems that make large use of sensors and positional systems to operate.

What should you learn next?
Their use was initially conceived for reconnaissance and surveillance operation, but with each passing month governments, such as the US and Israel, have started to use the drones for offensive purposes, initially against member Al-Qaeda members and affiliates.
By 2020, the Federal Aviation Administration (FAA) expects to have as many as 30,000 drones flying over the United States. Of course, the large diffusion of the vehicles must be sustained by meticulous attention to matters related to the security and privacy of the population.
The use of these vehicles raises a series of discussions about their security. These systems are complex environments that theoretically could be hacked becoming a weapon in the hand of attackers. Other serious questions are related to their use in the civil sector and privacy issue related to the improper management of data collected by the drone during the missions.
Why use a drone? The US case
The drones are remotely controlled vehicles considered by principal governments a secure and efficient weapon. UAVs are able to infiltrate the territory of adversaries in stealthy mode conducting intelligence-gathering mission. They can be deployed to monitor inaccessible areas and could be also used to attack specific targets with high precision thanks to the use of sophisticated pointing devices, all minimizing collateral damages.
The US Government has deployed military installations for the launch of drones in critical areas such as the Strait of Hormuz and on the African territories such as Djibouti, Ethiopia Niger to mitigate possible offensives of extremist groups. In the last decade the number of drones has increased exponentially, the US Government has more than 8,000 vehicles and new ones have been already ordered to principal manufactures for the next future, the use of UAVs has made possible the surveillance of critical tribal areas of countries such as Iraq, Afghanistan, Yemen, and Pakistan.
The adoption of drones for "targeted killings" is seriously debated. A growing number of controversial issues are raised, representatives of various governments are critics of the use of Drone of strikes in foreign areas, US are accused of violating other states' sovereignty if their governments do not authorize the US to operate in their territory, and the case of Pakistan is emblematic and caused serious frictions between the states.
On March 25th, 2013 Ben Emmerson, the UN Special Rapporteur on Counterterrorism and Human Rights, confirmed that no consent by Pakistan had been given for drone use on national territory and US attacks are considered a manifest breach of customary international law.
Statistics
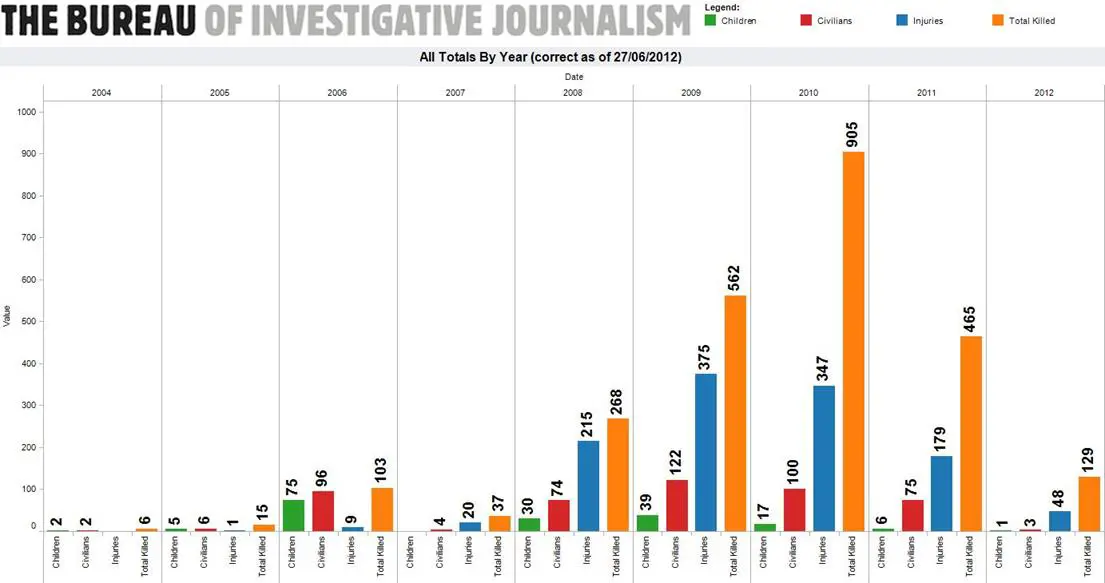
Unofficial estimates reports that since 2004 the US has launched around 360 drone strikes in Pakistan and around 100 offensives in Yemen. Unfortunately, during the attacks, thousands of people have lost their lives, what is concerning is that according independent organizations like the London-based Bureau of Investigative Journalism, around 20% of victims were innocent civilians and only 2% were high-level targets.
Figure 1 - Pakistan drone strikes: illustrating minimum total casualties - London-based Bureau of Investigative Journalism
Despite these concerning figures, Unmanned Aerial Vehicles (UAVs) are considered by governments an indispensable option in the modern warfare, the International Institute for Strategic Studies provided an interesting data on the distribution of 56 different models of drones worldwide. The data include 56 different types of UAVs used in 11 different countries counting around 807 vehicles in active service around the world, not considering the information related to China, Turkey and Russia that is not available.
But the use of these UAVs raises many thorny issues:
- Unmanned Aerial Vehicles are used in military reprisals conducted secretly. Its legality is much debated, US military has launched several lethal attacks on terrorist targets all over the world, but according specialists on government secrecy issues, the congressional oversight of these operations appears to be cursory and insufficient. The specialist Steven Aftergood declared :
"It is Congress' responsibility to declare war under the Constitution, but instead it appears to have adopted a largely passive role while the executive takes the initiative in war fighting."
Another concern about the use of drones is the real capacity of Western industry in protecting its projects and technological solutions. Foreign governments such as China are persistent collectors of military secrets and intellectual property. Cyber espionage is a common practice and various data breaches were denounced in the last year that could have a great impact also on the security of these complex machines. Cyber-attacks, network exploits, malware based attacks are all methods to steal industrial secrets on special projects, and Unmanned Aerial Vehicle technologies are among the most targeted.
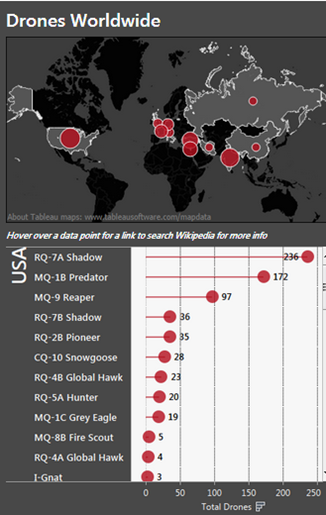
Figure 2 - Drone Worldwide Distribution (IISS)
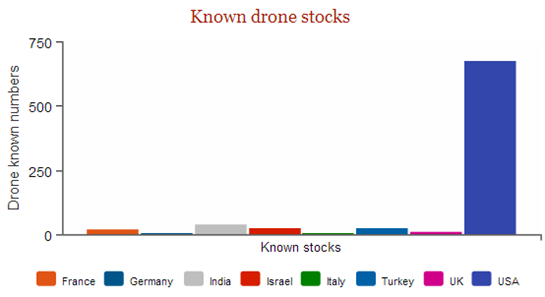
Figure 3 - Drone Stocks (IISS)
Hacking drones
The large diffusion of UAVs imposes a serious analysis under the security perspective. The vehicles are equipped with high technology components, each system could be potentially subject to cyber-attack with serious repercussions. The nightmare of military security experts is the hijacking of the vehicle by remote attacker that could gain the access to the vehicle using it against the forces that manage it.
But we said the drones manage a huge quantity of information during a mission. They acquire information from the field using various sensors, GPS systems and cameras, they execute specific flight plans and manage data related to asset located on the territory, for example in military context they have the exact location of troops on the battlefield including the basics of landing. A possible violation of the control system of a drone could represent a drama because the militias that launched it, they could lose the control of the vehicle and the attacker silently could have access to sensitive information for the evolution of conflict.
On December 4th 2012 Iranian government captured near the Iran-Afghanistan border an Unmanned Aerial Vehicle model Lockheed Martin RQ-170 used by US force for reconnaissance missions, the event was exploited by Iran forces to make propaganda on its technological capabilities but it was mainly an opportunity to study the components that equipped the drone including the data managed for its missions. The public was surprised by the perfect condition of the vehicle captured by Iranian forces, the status of the vehicle was visible in the images broadcasted by Teheran inducing security experts to think that the Iranian cyber units were able to hack the aircraft or in any case to force him to a secure landing causing a system failure.
The Iranian experts have had the opportunity to study the drone and analyzing the maintenance logs discovered for example that it had been sent back to Palmdale from Afghanistan for maintenance. Such information is strategic, they could provide exact data on the history of the vehicles including sensitive information on the ongoing missions.
Todd Humphrey, assistant professor at the University of Texas at Austin's Radio navigation Laboratory, has demonstrated with his research that hacking a civilian drone in not so complicated. The professor did it in front of the Department of Homeland Security, in various interviews and presentation the researcher revealed that using a limited budget and with a small group of individuals, he is able to send signals to an Unmanned Aerial Vehicle's GPS receiver, hijack the aircraft in mid-air, and control its route.
Humphrey demonstrated to Homeland Security agents that spending around $1,000 on equipment and designing an application able to send signals to the drone's GPS receiver he is able to gain complete control of the vehicle.
"The navigation systems of these drones have a variety of sensors," "…but at the very bottom is a GPS unit — and most of these drones that will be used in the civilian airspace have a civilian GPS unit which is wide open and vulnerable to this kind of attack. So if you can commander the GPS unit, then you can basically spoon feed false navigation information in the navigation center of these drones." explained Humphreys.
Commenting the results of its research Humphrey demonstrated a great concern related to the rapid diffusion of UAVs especially for civil use because lack of security could enlarge the attack surface of the Nation representing an Achilles heel for homeland security.
"In 5 or 10 years you have 30,000 drones in the airspace," "Each one of these could be a potential missile used against us." "I'm a big proponent of bringing in drones to the national airspace. They are going to come and we might as well expect it. The question is, how can we bring them in reliably?" he asks. "And right now the dangers of bringing them in, before addressing this problem, is that someone on the ground could hack the drones and turn them into their own device, making them go to a different place or along a different path. So it could cause loss of life, it could cause collisions. But I hope that we can address the problem long before that happens."
Humphreys explained to RT that he went into the experiment expecting a real challenge by hacking the drone's GPS with a homemade spoofer device, but along with some students, he says he "worked hard to demonstrate that it was indeed possible, and perhaps within the capability of other hackers."
Government and private businesses are fascinated by the use of UAVs, but there is a lack of understanding of the inner workings of the technology and of the cyber threat related.
Humphreys and his team of researchers of the University of Texas at Austin have led a successful attack accepting the challenge of the Department of Homeland Security. The event is really dangerous; an attacker can take control of the UAV to use it as a weapon.
GPS Spoofing attack
The principle behind the GPS spoofing attack is that sending to control system of the drone fake geographic coordinates it is possible to deceive the on board system hijacking the vehicle in a different place for which it is commanded.
A similar attack is possible due the leak of use of encrypted GPS signal, common occurrence for civilian aviation according Noel Sharkey, co-founder of the International Committee for Robot Arms Control.
"It's easy to spoof an unencrypted drone. Anybody technically skilled could do this - it would cost them some £700 for the equipment and that's it," Last year he declared to the BBC News.
An UAV could be directed somewhere using its GPS, a spoofer can make drone think it's somewhere else and make it crash into a specific target, contrary to what we can thing it wouldn't be too hard for a very skilled attacker to manipulate an unencrypted signal sent to a drone and spoof them.

Figure 4 – Drones and GPS
The first report in which it has been discussed of possible attacks against GPS technology is the "Volpe Report" that describes the main reasons to consider the GPS system as an attractive target in the civil and military sectors.
"GPS spoofing" is the principal threat to GPS receivers that are fooled into tracking counterfeit GPS signals, unlike in case of jamming of GPS signals in the case of spoofing the targeted receivers are deceived.
GPS "spoofers" are devices that create false GPS signals to fool receivers into thinking that they are at a different location or different times, this type of attacks can be really useful in a multitude of scenarios.
Let's consider that these attacks aren't simple to detect and can be conducted in aviation like in financial environments.
The Volpe report recommends studies to characterize the spoofing threat:
"Information on the capabilities, limitations, and operational procedures [of spoofers] would help identify vulnerable areas and detection strategies."
A the GPS receiver installed on the UAVs works exactly as any other GPS devices, observing the signals from a set of satellites and using the relative delays of the signals [si(t)] to solve the equations which determine the position of the vehicle and the time offset Δ of the receiver V.
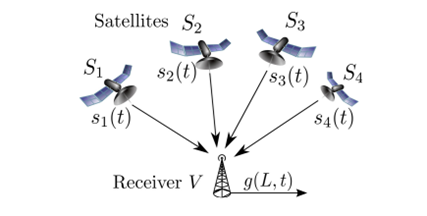
Figure 5 - GPS Satellites
In the attack scenario, the victim uses a GPS-based localization system and is synchronized to the legitimate satellites. The attacker starts sending own spoofing and jamming signals forcing the victim to synchronize to the attacker's signals.
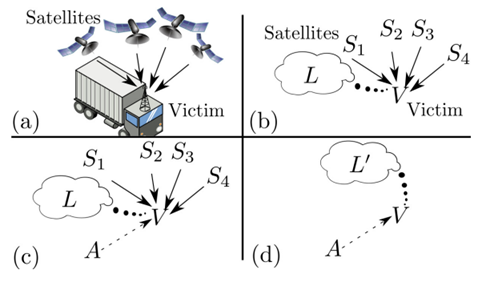
Figure 6 - GPS Spoofing attack
During the attack, the GPS signals can be spoofed by a hacker that could gain complete control of wireless traffic by intercepting, injecting, modifying, replaying, delaying, and blocking messages without temporal constraints for individual receivers. As explained in the paper "On the Requirements for Successful GPS Spoofing Attacks", "If the attacker has full control over the input to each individual receiver antenna, he can send the signals as they would be received at any location L0 j. This would, however, require the attacker to either be very close to each receiver or to use directional antennas with narrow beam widths and shielding to prevent that the signals intended for one victim are also received by another victim; in both cases, the number of required attacker antennas would be linear in the number of victims."
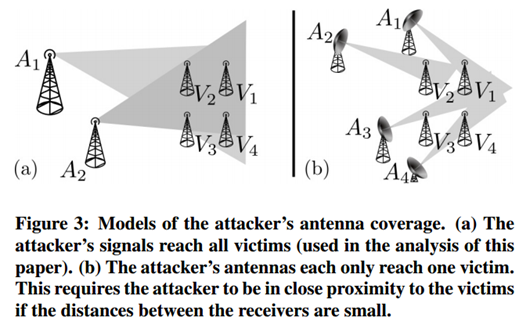
Figure 7 - Figure 6 - Model of GPS Spoofing attack
In the above paper, the researchers demonstrated in which condition attackers can establish the correct parameters to launch a successful spoofing attack on one or more victims. The attack against multiple targets is until now only theorized. The study revealed the inaccuracies in these parameters influence the lock takeover during the attack distinguishing the spoofing from the case of signal loss at the GPS receivers. The results proposed are very interesting especially for the implementation of effective countermeasures at receiver side, which are not implemented yet in current standard GPS receivers.
As described, there are meaningful differences between attacks against civil and military GPS systems.
Attacks on civilian (unauthenticated) GPS
The attacker can delay signals or send them prematurely, due the absence of authentication mechanisms he can modify the content of received GPS signals or arbitrarily generate the spoofing signals using the public GPS parameters. On standard GPS receivers plausibility or consistency of the data content in the received GPS signals is not verified, the hacker could use for the purpose a GPS signal generator to create specifically crafted GPS messages to send to the target, also modifying the claimed locations of the satellites.
Attacks on military (authenticated) GPS
The attacks against the military system present a greater difficulty due to the implementation of authentication mechanisms, the attacker could not generate valid GPS signals, but he can capture and relay existing ones (e. g. By separating signals from different satellites using high-gain directional antennas and broadband transceivers (called Selective-Delay in).
Note that neither the spreading codes nor the data content of the signal need to be known to the attacker for a successful selective-delay attack. The hackers can operate on a delay time of signals and amplify or attenuate them.
The spoofing generation methods could be divided into three main categories
GPS Signal Simulator - GPS signal simulator concatenated with an RF front-end generates authentic GPS signals. The GPS signals generated by the attacker do not essentially synchronize to the real signals. Despite the techniques appears very noisily it could be efficient against commercial GPS receivers especially if the spoofing signal power is higher than the authentic signals. The GPS signal simulator is easily detectable by antispoofing techniques such as amplitude monitoring and consistency checks among different measurements.
Receiver-Based Spoofers - GPS receiver concatenated with a spoofing transmitter. This system first synchronizes to the current GPS signals and extracts the position, time, and satellite ephemeris, and then it generates the spoofing signal. This technique is hard to detect but it is complex to realize due to the high correlation with victim receiver.
The technique appears impossible to realize in the case of military system such as the control system of UAVs.
Sophisticated Receiver-Based Spoofers – Spoofer know exactly the level position of the target receiver antenna phase center to synchronize perfectly the spoofing signal code and carrier phase to those of authentic signals at the receiver. This type of spoofer can take advantage of several transmit antennas in order to defeat direction of arrival anti-spoofing techniques. This is most complex technique, the realization of this type of spoofers is very difficult, and the attack is considered impossible to realize in majority of cases due to the geometry and movement of the target receiver antenna(s).

Figure 8 - UAV
Spoofing attacks countermeasures
Spoofing and anti-spoofing mechanisms are considered in modern GPS applications as critical aspects, as we have seen the spoofing is a deliberate interference that aims to force GNSS receivers into generating false position/navigation solutions.
The attacker attempts to mimic authentic GPS signals in order to mislead the target receiver, recently the implementation of sophisticated spoofers has become more feasible, flexible. The evolution of less costly in software-defined radio (SDR) technology is increasing the risk of occurrence of these types of attacks.
Countermeasures implemented in software on GPS receivers could be grouped in the following categories:
- Amplitude discrimination
- Time-of-arrival discrimination
The most sophisticated techniques are:
- Consistency of navigation inertial measurement unit (IMU) cross-check
- Polarization discrimination
- Angle-of-arrival discrimination
- Cryptographic authentication
The principal prevention against these attacks is the use of cryptographic techniques, receiver and transmitter use mutual authentication processes avoiding interferences of external sources. Unfortunately, these techniques are used only in the military sector and not in civil ones.
Evidence of GPS attacks has been collected in several countries monitoring jamming and spoofing activities principally against civil systems. It is necessary to take into serious consideration this kind of threat due their sensible impact on our ordinary activities.
Referring to the specific attacks against drones, the researcher Humphrey's team suggests that one not implement a countermeasure against GPS spoofing attacks that does rely on the signal analysis or on the lock loss of signal. The researchers proposed a method based on the use of several GPS receivers that can exchange their individual GPS locations implementing a mutual check on calculating locations. Of course, a possible attack is observed in the case that the calculated GPS locations are different from the known formation.
If only two GPS receivers are used, the countermeasure method is able to detect any attacker that is only using a single antenna; in this case both GPS receivers would report the same location (with small time offsets).
GPS signal jamming
Using jamming techniques against drones, it is possible interrupt the GPS receiving transmitted to the UAVs. In this scenario the aircraft could potentially lose the capability to monitor its route and to calculate its location, altitude, and the direction in which it is traveling.
Due large diffusion of low cost GPS jammer according principal industry experts, GPS jamming would become a serious problem, that's way security industry is also searching for alternative methods for navigating a UAS that not rely on GPS and that could integrate modern control systems.
GPS signals result very vulnerable to jamming attacks that differently from spoofing attacks have the unique intent block reception of information at receiver side, incidents related to GPS jamming are have occurred several times in the past. During 2009, GPS receivers at Newark Airport have been discovered that a driver had installed in his truck a GPS jammer to avoid the control of his employer. In 2001, a boat's television antenna preamplifier took out GPS over the entire harbor town of Moss Landing for weeks.
Figure 9 - GPS Jamming
GPS jamming is also used electronic warfare efforts, the North Korea has used in different occasions jamming equipment to interfere with global positioning system signals of South Korea's two largest airports near Seoul and across the center of the Korean peninsula. Fortunately, no accident was registered but it demonstrates that North Korea is also adopting this technique of attack to hit the South Korea.
In 2010, South Korean Defense Minister Kim Tae-young declared that North Korea had imported truck-based jamming systems from Russia that is able to interfere with GPS signals in a radius of 100 kilometers, since there various GPS-jamming incidents were observed in the area.
Jamming the communication, then the operator becomes blind and the UAV will fly until it crashes or it will land due an emergency procedure or the fuel is finished.
To prevent jamming attacks, the Department of Homeland Security and Overlook have been working since 2009 on a program called Patriot Watch, to develop and install a network of sensors that would be able to detect and localize any interference to GPS systems, unfortunately the program is undefined due the high cost of realization for the coverage of the entire country.
Last year DARPA sponsored a new research to help drones navigate without GPS. Called "All Source Positioning and Navigation (ASPN)," it's trying to "enable low-cost, robust, and seamless navigation solutions … with or without GPS." This demonstrates the high interest in the matter and the great concern of US authorities.
A solution to the attacks is production of equipment having spoofing or jamming detectors and used encrypting GPS signals, like the military does.
Another countermeasure against jamming is the possibility to use backup chips like the one proposed by DARPA that designed a tiny chip about one third the size of a penny that contains gyroscopes, accelerometers and a master clock. The chip has been dubbed Time and Inertial Measurement Unit or "TIMU.", it is able to produce an airtight record of vehicle movements, maintaining coordinates accurate until GPS connection is established again. It could be precious for the bombs, missiles, and UAVs that rely on the system.
Cyber-attacks malware based against UAVs
A drone, more in detail the software that equips its component could be hit by malicious code able to infect civil of military environments. The menace is concrete and it probably already happened in US military networks. In October 2011, Wired Magazine reported a virus infected drone remote control system, in particular the malware captured strokes on a keyboard in drones' cockpits at Creech Air Force Base in Nevada, made it tricky for the pilots who remotely fly assault drones like the Predator and Reaper.
The malware used did not appear sophisticated but security experts spent a couple weeks before to completely immunize the system.
"We keep wiping it off, and it keeps coming back," a source told Wired.
The US military has shared no information on the incident and on the way, the virus infected the systems, it was reported no news of data breach but there is no certainty that no sensitive data was stole.
"We generally do not discuss specific vulnerabilities, threats, or responses to our computer networks, since that helps people looking to exploit or attack our systems to refine their approach," says Lt. Col. Tadd Sholtis, a spokesman for Air Combat Command, which oversees the drones and all other Air Force tactical aircraft. "We invest a lot in protecting and monitoring our systems to counter threats and ensure security, which includes a comprehensive response to viruses, worms, and other malware we discover."
In that case Sergey Novikov, the head of Kaspersky's EEMEA research center, refused the hypothesis that the malware was part of a targeted attack on US military.
"This is definitely not a targeted attack. It's a simple Trojan, which infected the network of this military [base] in the US," "Any person, any employee of this huge network – it can be military or anybody else – comes with a USB stick or removable hard-drive and [connects] this device [to their] computer, and if that hard-drive was infected by any kind of Trojan or a worm, or any other malware, this malware starts distributing inside the network."
The menace of malware is serious, in recent cyber-attacks various sophisticated malicious code hit also high confidential environment, a malicious code could exploit zero-day vulnerability to elude security controls and hit the complex vehicle. Another serious aspect that must be considered is that UAVs are composed of various components provided by different subcontractors; potentially an attacker could try to exploit a vulnerability in one of these systems to compromise the overall security of a drone.
Drones, terrorism and cyber espionage
The use of UAVs on global scale in continuously menaced also by other factors, cyber terrorism and foreign governments are demonstrating an increasing interest in the powerful vehicles. Recently a new magazine titled "Azan" set up by Islamist radicals in Afghanistan and Pakistan is appealing to Muslims militants to develope new methods disturb US drone operations.
The magazine include a dedicated to calls for assistance against drones as a "sacred duty" of the Ummah, or the Muslim community.
"These drones can be hacked and manipulated as evidenced by the efforts of the Iraq Mujahideen. Furthermore, they can be destroyed using various technologies that the Mujahideen are working on. But the Muslims of the world must question themselves as to what role they are playing in helping these innocent Muslims with the abilities that Allah Has Given them. This is a call to anyone in the Islamic Ummah with knowledge, expertise and theories regarding anti-drone technology."
The attacks referred in the magazine occurred in 2009 when Iraqi insurgents deployed commercial software SkyGrabber to tap into live video feeds provided by US Predator drones in Iraqi airspace.
"Any opinions, thoughts, ideas and practical implementations to defeat this drone technology must be communicated to us as early as possible because these would aid the Ummah greatly in its war against the Crusader-Zionist enemy," reads the entreaty by the magazine's editors.Azan depicts Pakistan's Army and government as collaborators with the US in the continuing American drone campaign, though the US is shown to be the "main culprit."
The development of new malware able to target civil and military UAVs and in particular its component is a concrete risk. It must be considered that in the next couple of years the use of the drone will increase in a meaningful way, my concern is related to those environments in more exposed to hacker attacks, such as services by private companies. In these sectors, the probability that certain security measures are not adopted is not negligible.
Governments, principal manufacturers of UAVs and private companies must collaborate to define a minimum set of security requirements to defend from external attacks the drones and their components.
Cyber espionage
The cyber espionage is considerably one of the primary menaces to UAVs development; various cyber espionage campaigns have been conducted in the last months to steal technological intellectual property of the defense manufactures.
Unmanned Aerial Vehicles are considered primary targets in cyber-espionage, the technique adopted is consolidated, attacker conduct spear-phishing attacks that aim to steal information relating to technology such as Unmanned Aerial Vehicles (UAVs).
Early 2013 security Firm FireEye revealed to have discovered an APT campaign targeting companies in the defense and aerospace sector and that has been originated from China to steal intellectual property and industrial secrets from US companies.
"The set of targets covers all aspects of unmanned vehicles, land, air, and sea, from research to design to manufacturing of the vehicles and their various subsystems," said James T. Bennett, a senior threat research engineer at FireEye, in a blog post.
FireEye named the cyber espionage campaign 'Operation Beebus' from the name of an initial sample in this campaign (MD5: 7ed557921ac60dfcb295ebabfd972301), which was originally submitted to VirusTotal on April 12, 2011
The schema adopted for the attack is a basic spear phishing, the hackers in fact uses both email and drive-by downloads to targeted victims exploiting common vulnerabilities in PDF and DOC files to install a Trojan backdoor.
Security company FireEye registered suspicious activities against its clients operating in aerospace and defense sector, continuous waves of attacks that are repeated over time.
FireEye specialists collected various evidences that behind the operation there were Chinese hackers, known as most active persistent collectors of western technology, the security firm recorded 261 separate attacks on its clients in 2012, 123 of which were on UAV or UAS (Unmanned Aerial Systems) vendors.
In total, the C&C had reached 214 servers with 60 unique IP addresses, a large investment in time and effort.
Acquiring information on technology used for the construction of drones is essential for a reason:
- Bridging the technology gap
- Use the information gained to discover vulnerabilities that can be exploited in successive attacks.
Dealing with the phenomenon of cyber espionage requires a structured approach, the threat has grown in complexity in recent years, and in many cases, the attackers were able to evade the main security mechanisms for long periods.
On the one hand, therefore be thought of a new model of dynamic defense, which however cannot be separated by a major level of awareness of the users, in majority of cases the exposure is caused by wrong human behavior.
Conclusions
The various types of attacks described and the intense activities of foreign governments and cyber terrorists must set a maximum level of alert for UAV manufacturers. In future years these technological marvels will crowd the skies, security must be first requirement and a multilevel approach is necessary to prevent incidents caused by the different cyber threats. The mission is not simply due to the evolution of methods of attack and the sophistication level of the agents used, it is absolutely necessary a joint effort of defense manufacturers, industry, government and private companies.
References
http://securityaffairs.co/wordpress/2845/hacking/gps-spoofing-old-threat-and-new-problems.html
http://en.rt.com/news/jihadi-publication-appeals-drone-hacking-907/
http://www.bbc.co.uk/news/technology-18643134
http://www.caasd.org/library/presentations/navigation_workshop/FAA_Responses.pdf
http://www.syssec.ethz.ch/research/ccs139-tippenhauer.pdf
http://www.hindawi.com/journals/ijno/2012/127072/
http://www.guardian.co.uk/news/datablog/2012/aug/03/drone-stocks-by-country
http://online.wsj.com/article/SB126102247889095011.html
http://www.syssec.ethz.ch/research/ccs139-tippenhauer.pdf
http://diydrones.com/profiles/blogs/how-to-spoof-gps-to-potentially-take-over-a-drone
http://www.infosecisland.com/blogview/18912-The-RQ170-Affair-Spoofing-Jamming-and-The-GBAS.html
http://rt.com/news/virus-cyber-attack-drones-401/
http://www.cio.com/article/728292/Chinese_Malware_Targeted_U.S._Drone_Secrets_Security_Firm_Alleges
http://online.wsj.com/article/SB126102247889095011.html
http://www.wired.com/dangerroom/2012/07/drone-hijacking
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.