Covering Tracks of Attacks
In this article, we will learn about the most frequent ways used by attackers to cover their tracks. This will include covering tracks in networks, Windows, Linux, etc. So let's start by seeing how tracks can be covered over networks. Please note that I will cover only ways and a little bit about how the attacker uses them, but this article is not meant to dig deep into technical aspects of each type of attack.
Covering Tracks on Network
In this section we will learn about how tracks can be covered on the network. This section has further use cases as below:

What should you learn next?
-
Using Reverse Http Shells:
In this type of attack, the attacker typically installs reverse HTTP shell on the victim computer. This reverse HTTP shell is programmed to ask the commands from an external moderator who controls this reverse shell at regular intervals. This seems like a normal traffic to an organization network perimeter security device like a firewall, as port 80 is usually opened.
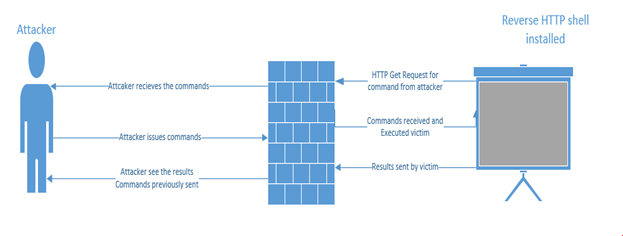
Once the attacker receives the request from the reverse HTTP shell, commands will be issued back that will be executed locally by the victim. This all is seen as HTTP request /response to the network devices. Once the commands get executed, results will be sent out in the next web request. These HTTP reverse shells can also be programmed to bypass any static authentication required by perimeter devices, like a firewall.
-
Using ICMP Tunnels
Because HTTP reverse shells are so famous, some organizations keep a check on what is leaving their network in response to the client's GET request. Some also check what comes as a reply to a GET request and most probably the attacker commands can be detected there. In lieu of this, some carry traffic via covert channels using ICMP packets. This is usually successful because organizations block only incoming ICMP packets and forgot about outgoing ICMP packets. Because of this configuration, an attacker uses ICMP packets to transfer TCP payloads.
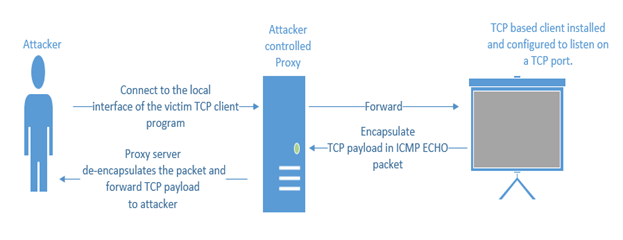
First the attacker configures the local client to connect with the victim client. The victim in turn encapsulates the TCP payload in an ICMP ECHO packet and forwards it to the proxy server. The proxy server in turn de-encapsulates the packet and extracts the TCP payload and send to attacker. To the network devices, it seems like a simple ICMP packet.
-
Various tools are available to do this. Some of them are given below:
- Ptunnel
- Loki
- ICMPShell
- PingChat
- ICMPCmd
Using TCP Parameters
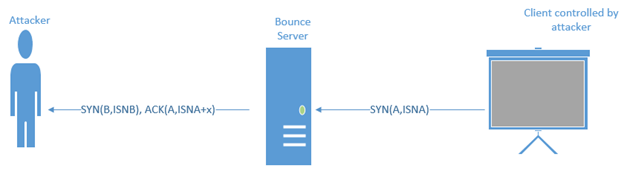
How about distributing the attacker's payload via the normal TCP packet instead of the encapsulating protocol? This method is well known and even today can be used to bypass IDS/IPS. The attacker can distribute the payload via the unset parameters of the TCP packet. Some of the interesting fields in TCP packet that can be used to transfer the content are:
-
Client generates a TCP SYN packet with a spoofed source address of the receiving server and destination address of the bounce server. Let's say the initial sequence number is ISNA, which holds the character to be transmitted.
Covering Tracks on OS
-
Windows
Hiding Files in NTFS
A file on an NTFS partition acts a drawer with various shelves, with name of the file as the name of the shelf. There can be any number of data streams associated with a data stream. It should be noted that file streaming applies on the NTFS and not in AT. An attacker can use this property of streaming to hide their files behind normal files on the system. For this we can normally use:

Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
-
Windows "type" command, which it has following syntax:
- type file_to_hide > normal_file:stream1
-
To view the stream use "more" with the syntax below:
- more < path to stream (for this you need to know the name of the stream)
-
-
Unix
- Files can be hidden in UNIX by appending a dot(.) in front of them. Each directory in nix contains at least two directories, which are the current directory(.) and parent directory(..). The attacker gives their files similar names like ".. " (there is a space after the dots). Usually files are hidden in /dev, /tmp, /etc .
- Sometimes the attacker edits the log files to cover their tracks. However, sometimes the attacker leave their trail that they edited the log file behind because, when the file is being opened to be edited, the shell will be placed to record that someone edited it. This will keep on happening. Smart attackers overcome this problem by using "kill" to kill the shell and setting the variable HISTSIZE to zero.
That covers the basics of it. In this article, we have seen how nefarious tracks can be covered on the network and OS.










