Android hacking and security, part 2: Content provider leakage
In the previous article, we discussed how an attacker exploits vulnerable Activity Components and ways to secure them. In this article, we will discuss "Content Provider Leakage."

FREE role-guided training plans
What are content providers?
As per Google's inbuilt security model, application data is private to an application, hence it is not possible for an application to access another application's data by default. When applications want to share their data with other applications, Content Provider is a way which acts as an interface for sharing data between applications. Content providers use standard insert(), query(), update(), and delete() methods to access application data. A special form of URI which starts with "content://" is assigned to each content provider. Any app which knows this URI can insert, update, delete, and query data from the database of the provider app.
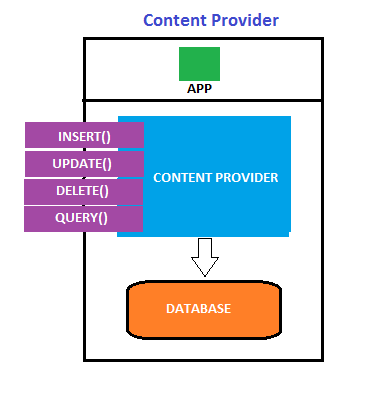
There may be some cases where content providers might not be implemented for sharing data with other apps, or the developer may want to give access only to those apps which have proper permissions. In such cases, if proper security controls are not enforced in the app, that leads to leakage of information.
The inbuilt SMS application in Android devices is a classic example of content providers. Any app can query the inbox from the device using its URI
content://sms/inbox. But, READ_SMS permission must be declared in the app's AndroidManifest.xml file in order to access the SMS app's data.
You can download the sample application used in this article.
Prerequisites to follow the steps
- Computer with Android SDK installed
- A non-rooted mobile device to install the app
Testing the application's functionality
After downloading the test application, install it in the non-rooted android device in order to test and exploit it.
It can be installed with adb using the following command:
adb install <name of the apk>.apk
It has a feature to store data inside the application. When we launch it, it appears as shown in the figure.
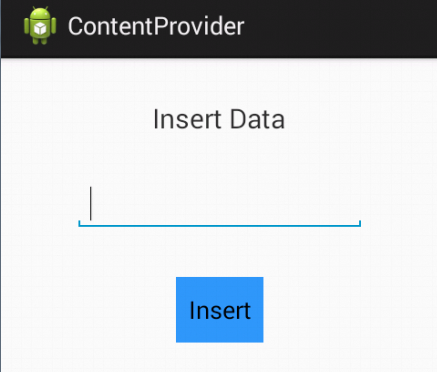
The goal is to find out if there are any content providers implemented in this app and if YES, we need to check and exploit if they are vulnerable to data leakage.
Topics Involved
- Information gathering
- Attacking vulnerable content providers
- Securing the applications
Information gathering
Like any other pentest, let's start with information gathering. We assume that we have the APK file with us. So, decompile the downloaded APK file as shown in Part 1 and check AndroidManifest.xml file for any registered content providers. We should also check the smali files for all the URIs used in the app.
Content Providers are generally registered in the AndroidManifest.xml file in the following format.
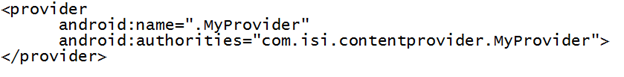
So let's go ahead and examine the manifest file.
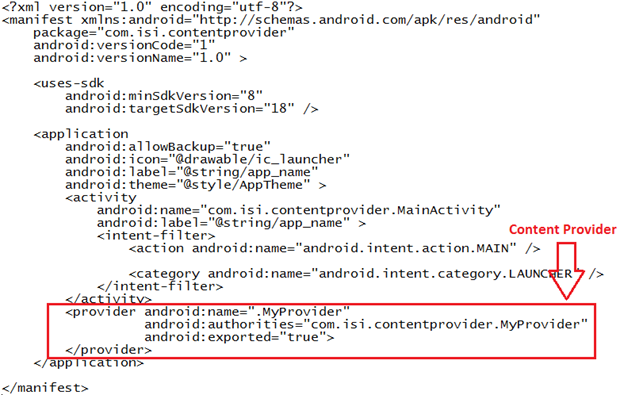
We have one content provider registered in the AndroidManifest.xml file and the good news is, it is exported to be accessed by all other apps.
Attacking vulnerable content providers
This is the most interesting part. Let's now try to query the content provider we found. If it returns any data, then it is vulnerable. This can be done in multiple ways.
- Using adb shell
- Using a malicious app to query
- Using Mercury Framework
Using adb
To query the content provider from adb, the app should be installed on the device.
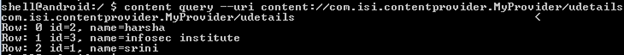
Get an adb shell on the device and type the following command to query the content provider. In my case, I am going to query the URI I found in MyProvider.smali file which is extracted by the APK tool.
Content –query –uri content://com.isi.contentprovider.MyProvider/udetails
We should now see all the details stored into the app's db as show in the figure below.
Using a malicious app to query
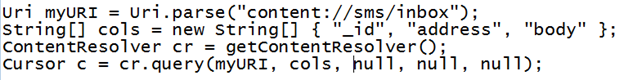
We can even write a malicious app to query the data from its content provider. Following is the code snippet to query the inbox from a mobile device.
Using Mercury Framework
The entire process can be carried out using Mercury Framework in even more efficient and simple way.
Securing the applications
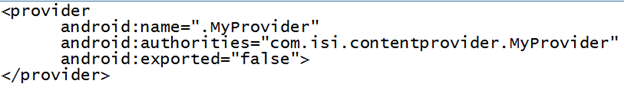
- Setting android:exported attribute's value to false:
In the AndroidManifest.xml file of our application, we should add the following attribute to the content provider to be secured. In our case, com.isi.contentprovider.MyProvider is the content provider.
If we try to query the content provider whose android:exported value is set to false, it will throw an exception as shown below.
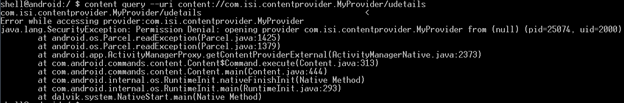
Note: The Default value of android:exported is true for all the applications using an API level lower than 17.
- Limiting access with custom permissions
We can also impose permission-based restrictions by defining custom permissions for an activity. This is helpful if the developer wants to limit the access to his app's components to those apps which have permissions.
Other issues with content providers
SQL Injection: If security controls are not properly implemented, content providers can lead to client side attacks like SQL injection. This works similarly to traditional SQL injection attacks.

FREE role-guided training plans
Path Traversal: This is one more attack which can be carried out if a content provider is not properly implemented. This is similar to the path traversal attacks on web applications. It allows an attacker to traverse and view the local file system. Sensitive files can be transferred from the device to the local machine using an app vulnerable to Path Traversal attack.










