Understanding Session Fixation
1. Introduction
Session ID is used to identify the user of web application. It can be sent with the GET method. An attacker can send a link to the user with predefined session ID. When the user logs in, the attacker can impersonate him, because the user uses the predefined session ID, which is known to the attacker. This is how session fixation works. As we can see, there is no need to guess the session ID because the attacker just chooses the session ID that will be used by the victim.
2. Environment
Let's analyze session fixation step by step in one of the lessons available in WebGoat [1].
WebGoat is a web application that is intentionally vulnerable. It can be useful for those who want to play with web application security stuff. The goal of WebGoat is to teach web application security lessons. WebGoat is part of the Samurai Web Testing Framework [2].
The Samurai Web Testing Framework is a Linux-based environment for web penetration testing.
This aforementioned lesson is entitled "Session Fixation" (part of "Security Management Flaws"). It was created by Reto Lippuner and Marcel Wirth.
3. Session Fixation Lesson from WebGoat
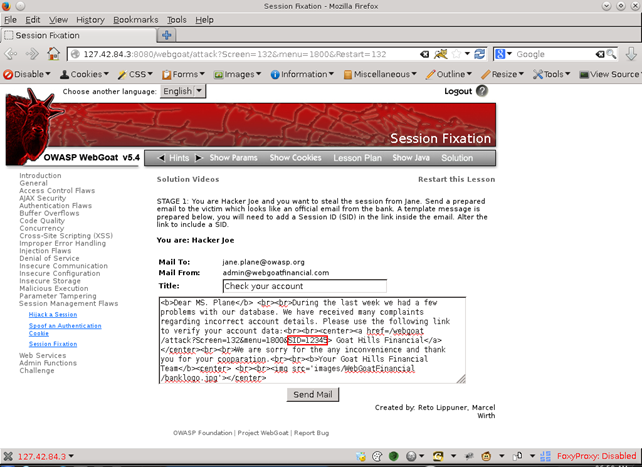
The attacker first sends a mail to a victim with a predefined session ID (SID). It has the value 12345 for the purpose of demonstration. The attacker has to convince the user to click the link.
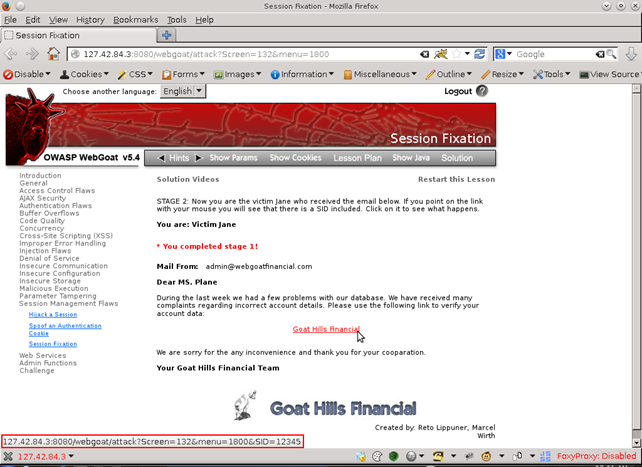
The victim gets the mail and is going to click the link to log in. As we can see, the link has a predefined session ID.
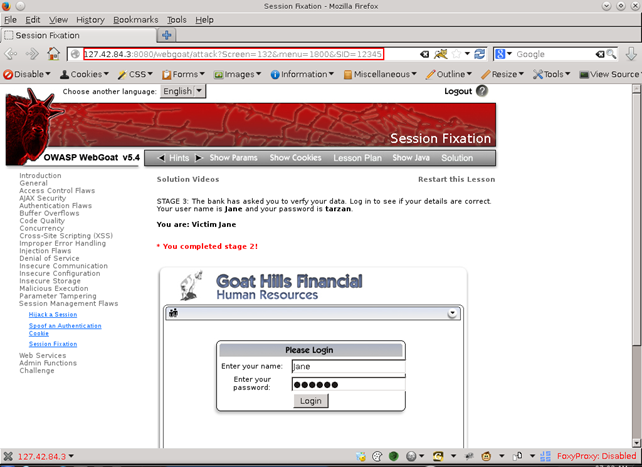
The victim logs into the web application and is recognized by the attacker's predefined session ID.
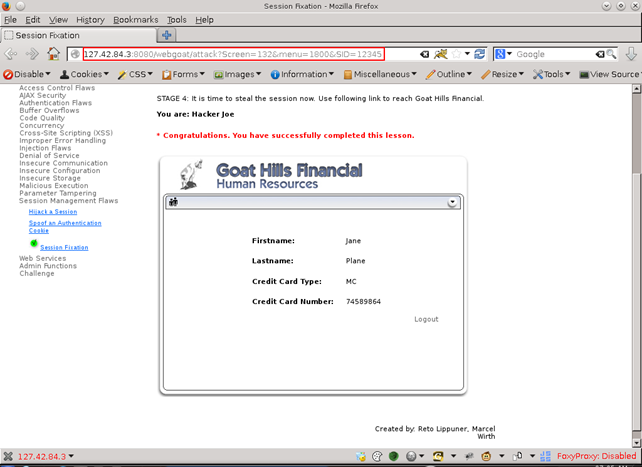
The attacker knows the predefined session ID and is able to impersonate the user.
4. Summary
Users can be impersonated when they use links with predefined session ID values chosen by the attacker. Session fixation was described and the lesson from WebGoat ("Session Fixation" from "Session Management Flaws" created by Reto Lippuner and Marcel Wirth) was presented to analyze session fixation step by step.
The mitigation for session fixation would be session ID regeneration after successful log in of the user. Then the predefined session ID wouldn't be helpful any longer to the attacker.
References:
[1] WebGoat https://www.owasp.org/index.php/Category:OWASP_WebGoat_Project (access date: 22 October 2013)
[2] Samurai Web Testing Framework http://samurai.inguardians.com/ (access date: 22 October 2013)









