Phishing Techniques: Similarities, Differences and Trends - Part II: Targeted Phishing
For Part I, which discusses Mass Phishing and sets the objects of examination in this paper, please check /phishing-techniques-similarities-differences-and-trends-part-i-mass-phishing/.
Introduction

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
Spear-phishing is a technique by which a cyber-criminal falsely presents himself in an electronic communication as a CEO, director, manager or a subordinate (an insider) of a particular firm or department of government where his victim works to earn their trust, or he impersonates an entity which is either trusted by the targeted firm/government or the latter has relations or obligations towards it.
To illustrate, a fake FBI subpoena was sent by a cyber-criminal to deceive his targets into installing an add-on in order to "view" it, which resulted in a malware being installed on the victim's computer. The goal of this masquerade is to infiltrate the entity's computer system through the victim's access to it and steal confidential information such as trade secrets, military information, personnel information, corporate intellectual property, etc. The intruder steals data that can either be sold for material gain when the information is sold on the black market or used for non-material gain. The collected information can then later be used to the cyber-criminal's benefit and most likely to the detriment of the targeted entity.
Targeted phishing could as well merely aim at making the victim divulge personal information such as credit card details like mass phishing, but in the disguise of an electronic communication coming from an insider of the victim's workplace or in another manner target the victim. The difference between mass phishing and spear-phishing is that in spear-phishing, only the employees of a particular entity are targeted, whereas in mass phishing, the targets are random and the perpetrators only desire to extract personal information from the victims.
Furthermore, in spear-phishing, perpetrators often disguise their messages as coming from within the entity they wish to penetrate which is also where the target works, whereas in mass-phishing, they impersonate a global and/or popular brand to which the victim may or may not be a customer and such cyber-criminals do not wish to infiltrate the brand they impersonate.
Whaling is a type of spear-phishing in which the targets are high-profile individuals only such as CEOs, managing directors and high-ranking governmental officials.
Spear-phishing and Whaling
File extension in attachment and file format exploits
Spear-phishing is referred to as "the main email attachment threat". A common manner of tricking targets in spear-phishing is to disguise a malicious attachment in a file extension that the victim will not open as a corporate document in a popular file extension used for various documents(1). The fake file extension could also imitate a legitimate image format. The other manner is to use trusted file extensions but take advantage of program vulnerabilities to gain access to the victim's machine when he opens the attachment (2). Such file format exploits that enable the perpetrator to access the information stored on the victim's device are gaining popularity and usage, and are, in general, a more successful means of tricking the target than disguising the file extension.
(1) The first manner requires little technical knowledge. A file extension can be concealed or disguised as benevolent by utilizing numerous tricks.
To con the potential victim, the spear-phisher makes the file extension look and feel like an innocent document such as "Business plan, amended 2013_2014.pdf" .or it could be any popular file extension or document name.
First, the phisher might take advantage of the option "Hide extensions for known file types" in Windows which is checked by default. Using this method, an .exe file extension will not be shown and a file.pdf.exe would appear as file.pdf. To further the scam, the phisher would use an Adobe symbol as an icon. Any icon can appear with the file, so .jpg and a myriad others could also be imitated. This method of hiding extensions is easily stopped as all you have to do is uncheck this option.
Second, the phisher might attach a file which is a shortcut, enabling this shortcut to have a masked real file extension but appearing with any name and extension he desires. In this way, the shortcut can be set to execute a command and serve the function of an .exe file.
Third, RTLO or RLO (Right-to-Left Override unicode) can be used to disguise the file extension by reversing the direction of reading of the file names and their extension while retaining the same type of execution for the extension. For instance, a file named "Business plan, 2013_2014ann[RTLO]fdp.exe" would appear as "Business plan, 2013_2014 annexe.pdf".
Lastly, the debugger of a legitimate application provided in the attachment can be changed to initialize a malicious executable every time you run the particular legitimate application.
The ways of concealing or disguising a malicious attachment are not exhausted in this discussion.
(2) The fact that exploits of file format bugs and vulnerabilities are being preferred by phishers as a method to infiltrate the targeted entity is not random.
Firstly, such exploits can provide access not only over the process and application which is exploited but over the entire PC's operating system and machine. File format vulnerabilities are not only a security threat for Windows but also for other operating systems as well, such as Android and Linux. For instance, there is a vulnerability of Adobe Reader v8.x and v9.x which allows an executable file to be launched along with opening the .pdf file if you are using Windows XP SP3. Of course, vulnerabilities are plentiful which gives phishers a lot of discretion.
Thus, malware can easily be installed without your consent and knowledge when you open the file.
Secondly, as such exploited files appear to be legitimate, you can open them and see that the file is what it is supposed to be (text, image, etc.). This will further reduce the chance of you even figuring out that you have been phished which will decrease the chance of you reporting the scam to the appropriate person, taking measures to quickly remove the threat, or taking future precautions.
If nothing is done, the phisher will have unlimited access in terms of duration.
Thus, instead of the common manner and trend of creating fake web sites or pages used in mass phishing to get concrete information such as username and password or credit/debit card details, in spear-phishing and whaling, perpetrators often attempt to gain access to the machine so they can browse through all the corporate or governmental information available there and decide on their own which confidential information would be profitable enough to collect. Moreover, by gaining access to a single machine in the particular work place, they may further attempt to infiltrate its entire computer system.
File format vulnerabilities are most frequently exploited by malicious software. The three file types that were used the most in the previous year for spear-phishing emails were .rtf (38%), .xls (15%) and .zip (13%). It has to be said that the most regularly attached file types accounted for 70% of all such malicious attachments.
Executable files are not used that much, as it has been noted above that file format exploits and not malware in plain sight is preferred for targeted cyber-attacks as it is harder to notice the threat in the file. The chance of the phishing email to be filtered by your email provider will be small and it is difficult to react to the threat as it appears to be a legitimate file.
However, the (1) first manner of concealing a malicious attachment is still used by phishers with very low technical knowledge and in simple phishing attacks (mass phishing).
I have discussed file extension and file format vulnerabilities as a means of infecting the victim in spear-phishing and whaling, as it is estimated that 94% of targeted emails are trying to scam the potential victims through malicious attachments while only 6% use links to trick them.
Customizations in spear-phishing emails (as a result of email spoofing)
Trend Micro has estimated that around 91% of all cyber-attacks start with an email of spear-phishing origin. All it takes for a phisher is to trick one employee of a company into compromising his PC or divulging sensitive information to enable this cyber-criminal to masquerade as the scammed employee and use advanced social engineering techniques to gain further access and obtain more and more confidential/sensitive information. Thus, phishers would try to customize the emails to their targets as much as possible to make these emails seem legitimate and successfully gain access to the recipient's machine and/or work place.
The first strategy and customization that you will see in a spear-phishing email is email spoofing, which aims to establish trust between you and the scammer. The phisher would mask the From, Return-Path and Reply-To fields in his email to appear as sent from within the company, governmental department or from an entity or authority with which the previous two had dealings with. Note that email spoofing is not limited to spear-phishing and is frequently employed in all phishing techniques, but in spear-phishing and whaling, the sender will be someone you definitely know.
One must be aware that the given email address in these three fields mentioned above can be fake and different from the email address of the actual sender. However, there are numerous ways to spoof an email.
First, phishers can use the network protocol Telnet to connect to the SMTP or ESMTP (Extended Simple Mail Transfer Protocol) of a website, company, organization, etc. and send an e-mail that could be masked as coming from any desired email address. This method is not widely used nowadays, as this legitimate practice has become a victim to anti-spam techniques and because it is a bit sluggish. Most email service providers would warn you that the email might not be coming from the stated email address, or the email might go to the spam folder, etc.
However, customized and spoofed emails "sent" from an email address with which you have communicated before are less likely to go to the spam folder.
Below is an illustration that shows how a spoofed email can be sent to a victim using the above mentioned method:
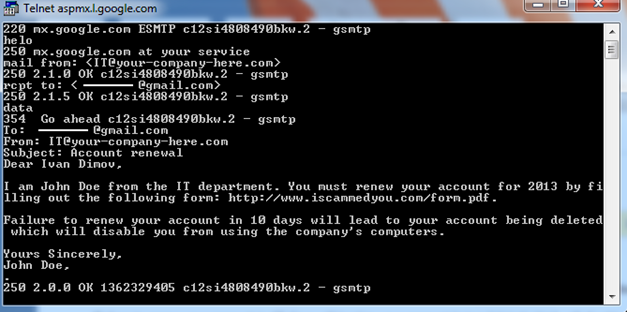
Fig.1: Screenshot of Command Prompt which shows relaying a spoofed email via Telnet with an ESMTP.
It is quite simple but somewhat ineffective. Here is how the email looks like when you open it:
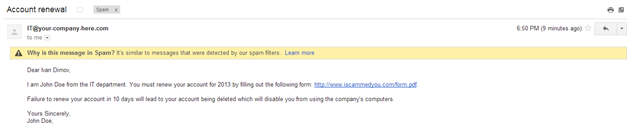
Fig.2: Screenshot demonstrating how a spoofed email can look like in your inbox.
You can see that this method definitely does not provide good results for phishers anymore. However, if the spoofed email address appears to come from someone with whom you communicate, regularly or not, the email might not go to spam.
To relay an email via telnet, one has to enable Telnet Client on his Windows as it is turned off by default. To do so, you should first go to Control Panel -> Programs and Features -> Turn Windows features on or off -> Telnet Client. Then, you need to open the Command Prompt (Windows Tab, enter in search "command"). Afterwards, you would have to choose the SMTP server by performing nslookup in the Command Prompt to find out the SMTP server address of the website whose server address you are going to use.
The image below shows what you ought to do to get the SMTP server address:
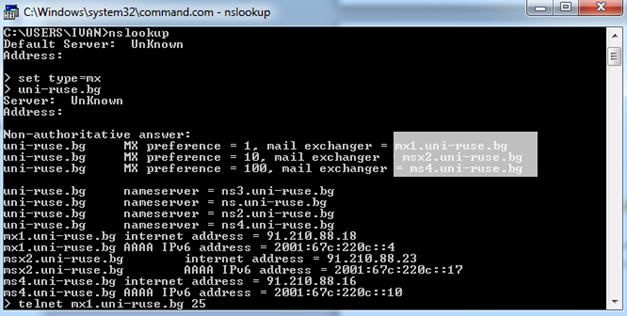
Fig.3: Screenshot of Command Prompt; nslookup
The SMTP server addresses for the website uni-ruse.bg are highlighted. After you have retrieved this information, all you have to do is write "telnet SMTP.server.address 25" (25 stands for the port number and 25 is almost always used for (E)SMTPs) and follow the procedure from the first figure.
Nevertheless, most ISPs SMTP servers require authentication, which could be manually achieved, and they would, generally, send a message only if it has To and From fields as its own domain name, for instance, the domain in the illustration above. You can relay emails that can have any To and From fields and require no authentication by connecting to aspmx.l.google.com, among other ESMTPs.
Furthermore, this method can not only be ineffective but it could also be risky as your IP address will be stored during the virtual terminal connection. Thus, you can easily get caught and brought to justice. That is why a phisher would have to mask his IP address and whatever links his machine and ISP to the crime scene. Plus, he can get graylisted, which will bar him from using the services of the SMTP for a period of time if he abuses this function in some way.
An easy and somewhat secure method of email spoofing is via a "legitimate" email spoofing provider. Such providers are widely available and are a paradise for phishers, spammers and similar cyber-criminals. In this manner, the email spoofing requires no technical knowledge. A phisher can use the services of Zmail or the former Pseudo Mailer, which was later known as hoaxMail and is now known as Fogmo, among others.
The illustration below shows how Fogmo's website interface looks like:
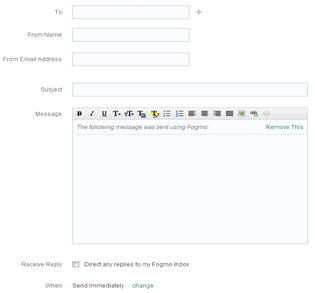
Fig.4: Screenshot of http://www.Fogmo.com showing partial interface (after login)
You have to pay a small amount of money to remove "The following message was sent using Fogmo" in the message body which, if not removed, would almost certainly ruin the phishing attempt.
The list of methods phishers use for email spoofing described in this article covers only a fragment of the techniques available.
Customizations in spear-phishing emails (as a result of information gathering)
Most of the information used by phishers to customize their emails comes from the public domain.
The phisher would visit the company's website, gather your name and email address from there along with any additional information available. After he has collected such basic information about you and the person that he is going to impersonate from the company's website, the phisher can choose to gather further information from the public domain, for instance, by using OSINT tool such as Maltego.
If the spear-phishing attempt is meant to be more complicated and important like whaling, he can use all this information collected from the public domain to conduct deeper information gathering to collect information not located in the public domain. He can learn what your schedule is, where you are supposed to travel, what documents you are working on, what your tasks and duties are, and include bits of this data in his email which will make you open the attachments or click the links there without any hesitation as to the reliability or the authenticity of the email.
For instance, the phisher might employ dumpster diving to get to the company's papers and get ahold of projects, plans, decisions, minutes of meetings and other company documents. Afterwards, he may send you a spoofed email from a colleague of yours claiming that he is sending an "amended" version of the document, that he wants you to skim through it, review it, etc., when in fact the document would have file format vulnerabilities which the phisher will have exploited, or the file would be malicious in nature, or be a form of malware in the wild. Thus, it should be a company policy to always shred documents with a shredder before throwing them in the trash.
Thus, so far we have said information gathering occurs firstly through the public domain. This is done through: 1, the company's website, to collect your name and email address and anything else readily available such as publicly available corporate documents and the phisher can also gain initial information via corporate directories and telephone conversations; 2, open source intelligence and other tools, and also through pictures, social media, forums, blogs, news articles, leaks etc.; and 3, the private sphere, with techniques such as dumpster-diving, social engineering and, rarely, whistleblowers, or by giving the job to a third-party.
An example of the second method of obtaining information would be images. By using tools such as exifdata.com one can not only see the date when the image was created and the camera's platform, but he can also see the GPS geo-localization of the image if the creator of the photo did it from a device with GPS turned on in its settings, like iPhones are by default. Hence, the phisher might conclude that you have been in a particular place on a particular date and time just by looking at one of your pictures uploaded somewhere in the Internet. To see more about information gathering through pictures, visit /reconnaissance-with-images/.
An instance of the third method is social engineering. The phisher might have gained access to another employee's computer, data, accounts, etc., which will enable the cyber-criminal to employ more sophisticated social engineering techniques, based on already collected information from the first victim, than would otherwise be available to him to entice other employees into opening the provided attachment or link and, thus, gain further access to the workplace and obtain pricey data.
The scammer can also call support and ask questions or impersonate a trusted entity, for example, to gain initial information about the target.
Furthermore, by adding him to your friends in Facebook or by making this information public, the phisher can freely view your email address, phone number, tastes and preferences, family, and friends which can be used as part of the social engineering technique.
To conclude, always expect your name and job position to be mentioned in the email, along with a familiar email in the From field. Moreover, familiar work-related or personal things may be mentioned along with an attachment that's seemingly work-related or personal and coming, often, from a colleague of yours.
An example of how effective spear-phishing and whaling can be
In 2011, Google shut down Chinese spear-phishers who targeted senior U.S government officials and officials in different Asian countries, among others. They used spoofed emails to mask the sender as being an acquaintance or a coworker, and some of the emails even had hand-crafted text inserted in the body of the message. Of course, every email was customized to lure the particular target. The cyber-criminals did not only use attachments but inserted "View Download" links that, when opened, would falsely require the victims to authenticate themselves in Gmail. After being scammed, the phishers changed the settings of their mail to forward incoming messages to them.
These attacks might have been aimed at collecting initial information for more quality social engineering techniques. The phishing is claimed to have originated from Jinan, China and the region is a source of other cyber-attacks which might be related as they were "similar".
Further Trends
Spear-phishing cons 2 people for every 1000 targeted ones but this can vary enormously depending on the methods and customizations employed. For instance, Aaron Ferguson, wanting to prove the colonel effect and the effectiveness of spear-phishing, masked a message as coming from a Colonel Robert Melville of West Point, targeted and sent emails to 500 cadets prompting them to open a link to verify their grades, which around 80% of the cadets clicked. This illustration should show the subjectivity of spear-phishing's success rate.
Furthermore, the criminal can expect $150,000 in profit from such a campaign while he can only get $14,000 from mass phishing, on average.
Findings from a survey of more than 330 IT professionals last year show that spear-phishing attacks are frequently the root cause of security breaches. 51% of the IT professionals said that they believe their organization was targeted by spear-phishers in the past year. The survey findings also include that larger organizations are more likely to get targeted. This is evident as such organizations not only provide more targets but have more information in terms of quantity and value.
See Infosec IQ in action
References:
- IT Law Wiki, 'Spear-phishing'. Available at: http://itlaw.wikia.com/wiki/Spear-phishing (Accessed 2/23/2013)
- Paul Gil, 'What is "Whaling"? Is Whaling Like "Spear Phishing"', Available at: http://netforbeginners.about.com/od/scamsandidentitytheft/f/What-Is-Whaling-Spear-Phishing.htm (Accessed 3/3/2013)
- Antony Savvas, '"Spear phishing" the main email attachment threat', November 29 2012. Available at: http://news.idg.no/cw/art.cfm?id=F04FD271-AB0F-DB8A-31F4EB29297930D5 (Accessed 2/24/2013)
- LoredanaBotezatu, 'Six tricks scammers use to con you into clicking a malicious .exe file', October 20 2011. Available at: http://www.hotforsecurity.com/blog/six-tricks-scammers-use-to-con-you-into-clicking-a-malicious-exe-file-1184.html (Accessed 2/24/2013)
- How-To Geek, 'How Hackers Can Disguise Malicious Programs With Fake File Extensions'. Available at: http://www.howtogeek.com/127154/how-hackers-can-disguise-malicious-programs-with-fake-file-extensions/ (Accessed 2/24/2013)
- Wikipedia, 'Email spoofing'. Available at: http://en.wikipedia.org/wiki/Email_spoofing (Accessed 3/3/2013)
- wikiHow, 'How to Forge Email'. Available at: http://www.wikihow.com/Forge-Email (Accessed 3/3/2013)
- Shathabheesha, 'Reconnaisance with images', June 28 2012. Available at: /reconnaissance-with-images/ (Accessed 3/3/2013)
- Ravi Miranda, 'Playing mindgames', July 17 2012. Available at: http://ravimiranda.wordpress.com/tag/colonel-effect/ (Accessed 3/3/2013)
- Kevin Poulsen, 'Google Disrupts Chinese Spear-Phishing Attack on Senior U.S Officials', 06.01.2011. Available at: http://www.wired.com/threatlevel/2011/06/gmail-hack/ (Accessed 3/3/2013)
- SearchSecurity.TechTarget, 'spear phishing'. Available at: http://searchsecurity.techtarget.com/definition/spear-phishing (Accessed 3/3/2013)
- Keith R. Crosley, 'Spear Phishing Statistics: 2012 Findings from Microsoft TechEd, RSA Security Conference Surveys', July 18 2012. Available at: http://blog.proofpoint.com/2012/07/spear-phishing-statistics-2012-findings-from-teched-rsa-security-conference-surveys.html (Accessed 3/3/2013)










