8 phishing simulation tips to promote more secure behavior
The benefits of testing and preparing your employees with simulated phishing emails in the same environment that real attacks persist (the inbox) are undeniable. There’s a reason phishing simulations are recommended by NIST as a staple in any security awareness and training program.
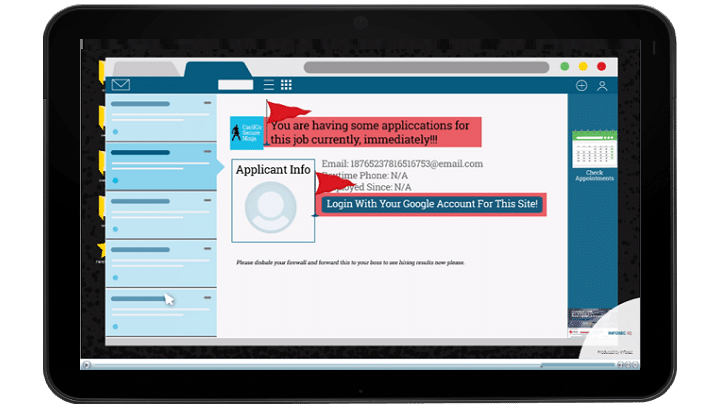
With the right phishing simulator, it’s easy to craft the perfect simulated phishing email using the same tricks and techniques used by real scammers to prepare your workforce for the most dangerous attacks. But just because you can craft a perfectly disguised simulated phishing email that will bait most of your employees to click, doesn’t mean you should. And even though you could send the most obvious Nigerian Prince emails to ensure your organization’s phish rate drops lower than ever before, doesn’t mean it's a good idea.
See Infosec IQ in action
The goal of simulated phishing is to both prepare employees to spot real attacks while also encouraging them to report suspicious emails to your security team. Meanwhile it’s important to ensure employees and management maintain a positive association with your security awareness and training efforts, not be turned away by your phishing simulations. To help you strike this delicate balance, we put together our top eight phishing simulation tips perfect for anyone trying to refine their strategy or even launch their very first simulated phishing program.
Is your organization susceptible to phishing attacks? Find out today with a free Phishing Risk Test!
1. Start with a moderate baseline phish
Before launching your simulated phishing program, it's important to send an unannounced (to employees) baseline phishing simulation. The resulting phish rate and email reporting percentage serve as your baseline metrics to measure against future simulations. The goal of your baseline phish is to get the most accurate representation of your organization’s phishing susceptibility. For this reason, don’t start with spearphishing emails that will trip up most of your workforce or the simplest email that the whole organization can spot. Select or build a phishing template you would consider moderate difficulty for your most accurate measurement.
2. Educate, but keep it brief
Education is one of the most important parts of your simulated phishing program. Not only does education help employees identify their mistakes and encourage more secure behavior in the future, but it can be served to phished employees immediately, in the most teachable moment. To keep this technique effective, it's important to deliver bite-sized, actionable tips to inspire behavior change without distracting the employee with minutes of training. We recommend using engaging, microlearning modules or education pages that take less than a minute to consume.
3. Use at least two clues per phishing email
Give your employees a chance. Especially when you first launch your program, it's more important to encourage secure behavior than it is to trick more employees into clicking your simulated phishing email. Adding two clues — red flags employees should recognize — per phishing email will help encourage behavior change without constantly phishing employees and barraging them with training. As your security awareness program matures and as employees get better at spotting your phish, you can increase the difficulty and sophistication of your simulated emails.
4. Be realistic, not destructive
 Modern phishing attacks use the dirtiest tricks in the book to evoke emotional responses in victims. While scams such as sextortion attacks exist in the wild, they can do more harm than good in your simulated phishing program. Before sending a simulated phishing email, ask yourself, “Could this scare someone, upset a relationship or keep an employee up at night?” If so, don’t send it. Your awareness and training program can still train on these topics, but using vulgar or aggressive simulated phishing emails is more likely to make employees resent your training program and undermine your efforts than encourage lasting behavior change.
Modern phishing attacks use the dirtiest tricks in the book to evoke emotional responses in victims. While scams such as sextortion attacks exist in the wild, they can do more harm than good in your simulated phishing program. Before sending a simulated phishing email, ask yourself, “Could this scare someone, upset a relationship or keep an employee up at night?” If so, don’t send it. Your awareness and training program can still train on these topics, but using vulgar or aggressive simulated phishing emails is more likely to make employees resent your training program and undermine your efforts than encourage lasting behavior change.
5. If you’re impersonating a department, let them know first
It’s important to simulate the most common, targeted phishing attacks your organization faces. This often includes internal or BEC attacks impersonating departments such as HR, finance and accounting. Before sending a simulated phish impersonating one of your departments, let a department manager know. This will help avoid confusion and disruptions in employees’ workdays and will even bring a member outside of the security department into the fold of your awareness and training program.
6. Spearphish based on highest risk — not at random
Employees with access to financial information, personal records or other sensitive information are the most vulnerable to spearphishing attacks. Instead of building hyper-targeted phishing emails for everyone, pinpoint the highest risk employees at your organization and focus your simulated spearphishing efforts there.
7. Give special attention to the C-suite
Your C-suite and upper management are unique. Not only are they top targets in phishing attacks, but they play by different rules than the rest of your workforce. If you plan to send simulated phishing emails to them, be sure to agree on a plan that keeps leadership on your side. Personalized, in-person training for the C-suite and upper management might be better received at your organization, and may be more effective than the same phishing simulation and training regimen used for the rest of your workforce.
8. Don’t rely on phish rate as your sole metric
Your organization’s phish rate is a great metric to estimate your phishing risk and track progress over time. However, this metric can easily be manipulated or misinterpreted based on the difficulty and execution of your simulated phishing program. Sending painfully obvious phishing simulations to your most cyber-aware staff members will surely drop your phish rate, but is it truly reflecting your organization’s phishing susceptibility? Along with your phish rate, track your phishing report rate. Tracking the number and percentage of emails reported by your employees is a much more accurate representation of not only employee recognition of phishing attacks, but also behavior change.
These eight phishing simulation tips are meant to help you prepare your employees for phishing attacks and encourage behavior change at your organization while ensuring employees and leadership alike maintain a positive association with your security awareness and training efforts. If you’re ready to take a closer look at exactly how you can pull these strategies together and build your own simulated phishing program, we’d love to help.
See Infosec IQ in action
Request a demo of Infosec IQ security awareness and phishing simulation platform to see for yourself









