4 tips for phishing field employees [Updated 2020]
Phishing is easy. Let’s just get that out of the way. It’s easy for an attacker, and, if you have the right tools (such as InfoSec Institute’s PhishSim), it is easy for a cybersecurity professional who wants to test the company employees using simulated phishing campaigns. With an average of 90 messages being delivered to a business email address per day [1], phishing is like, well, shooting fish in a barrel. 60% of work email accounts get checked at least once a day [2]. But what about the other 40%? What about employees whose responsibilities do not include a lot of, or any, email communication? Most organizations have employees working in the field. From drivers to technicians, to visiting nurses and field engineers, there is a significant percentage of workers that never set a foot in your main office and, while having a company email address, never have to use it to perform their duties. Add to that number your custodial crew, cafeteria and on-premises daycare employees, and all of a sudden you have a small army of email “non-users”. Even if they use their company email only to receive their paycheck deposit notifications, just by having an active account their present a possible attack avenue for cybercriminals. From ransomware to establishing foothold via a compromised internal account, attackers can use phishing in any number of ways against any business email account, regardless of its usage frequency or the owner’s role. Remember, all is needed for a successful compromise is one click.
An additional risk here is in that field employees are often not subjected to the same amount of security awareness training as the rest of the staff. The logistics of delivering the training materials to employees who hardly ever set foot in the main building are sometimes too hard to figure out for security administrators. InfoSec Institute’s AwareEd takes care of that problem by offering a 100% browser-based awareness courses with a lot of flexibility for creating, scheduling, running, and tracking effective awareness education campaigns.

Strengthen security awareness with human risk management
Infosec HRM, powered by Right-Hand Cybersecurity, provides alert-based training nudges to minimize human risk at your organization.
Below are some tips for running effective simulated phishing campaigns targeted at your field employees. Something that we did not include as a separate recommendation, because it applies universally: think like an attacker. Malicious hackers will try to find and exploit the weakest links in your system, including careless email users, so you have to beat them to it with effective simulated phishing campaigns followed by targeted awareness education efforts.
-
Use their infrequent email usage against them
Ironically, the very fact that field workers don’t use their company email much is their Achilles heel. A rare email delivered to their company mailbox for them fits into two possible scenarios. First is that this is something completely normal and, therefore, safe. This applies best to situations when there is some sort of scheduled/automated communication already in place, in other words, if getting an email from a certain recipient and/or within a specific timeframe is part of the employee’s routine. Examples would include a paycheck notification, a recurring conference call invite, etc. Password reset/renewal would be expected by most of the infrequent account users at some point. On the other hand, if the message is not expected, it looks like something completely out of the ordinary, and, therefore, requiring immediate attention. Which brings us to the next point:
-
Crank up the urgency
Urgency is important in any phishing email. Attackers want to get results fast, before their malicious server got taken down, before malware definitions get updated, etc. But it’s even more important when targeting field employees. Many of them may not see the email until the end of the day, when they get back to the office. Many will see the notification pop up on their device and just ignore it if this is something that does not seem to require any immediate action on their side. So, you have to make sure to grab their attention right when they lay their eyes on the New Email notification. If you are simulating internal communication, use the appropriate language and naming convention for file attachments. “Health insurance cancellation notice” will give at least a click, if not a download, in most cases. Here, email not being a regular method of communication for the employee plays to your advantage as well: they may not be aware that such notification is not appropriate for the organization. Make sure to throw in some power words into the subject line: now (urgent, immediate), removal (cancellation), required (requested, needed), etc.
-
Target mobile users
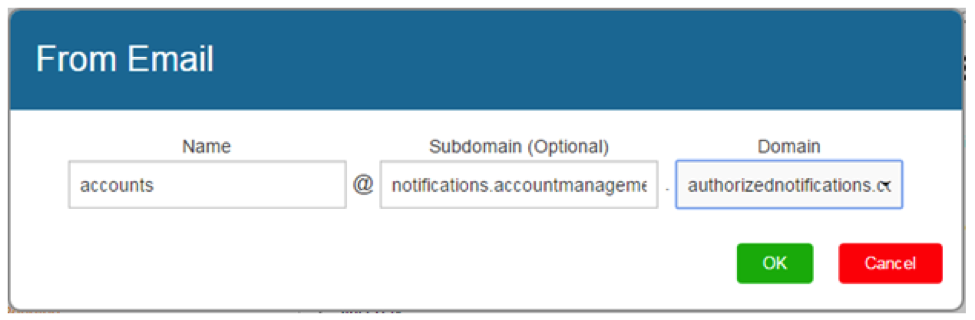
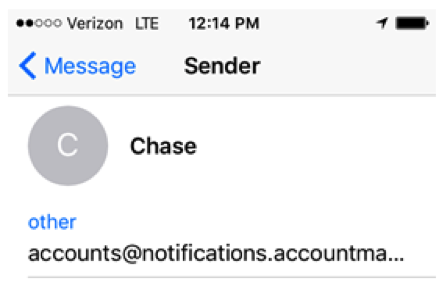
It’s probably a safe bet that most of your filed employees will receive your simulated phishing emails on their mobile devices. There are various way that this can be used to your advantage. First thing to consider is the small screen size. SecurityIQ PhishSim template editor lets you add one or several subdomains to your From email address. Below is what the address looks like in the editor and when opened on an iPhone.
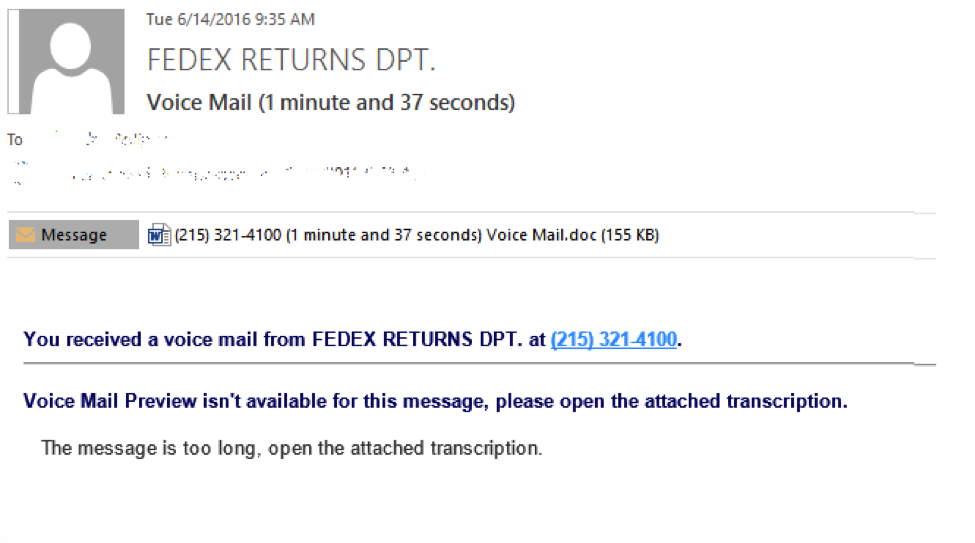
Another way to exploit the technology aspect is to refer to the device’s functionality. Assuming that this is a phone, you can send Missed Call notifications with attachments containing “message transcriptions”. Below is an example of such email created with and sent from SecurityIQ PhishSim.
You can send out notifications about mobile malware detected on the device or bogus “confirmation codes”, requiring to use them on the landing page because “account was accessed from a mobile device”. Creating new templates is a matter of a few clicks in SecurityIQ PhishSim, so let your imagination run wild.
-
Deliver education
As we mentioned earlier, one of the issues with educating field employees is in finding an effective and efficient mechanism for the actual delivery of awareness training materials. Without any kind of educational component to follow a successful simulated phishing event, your campaign is just that: a phishing campaign, not a truly valuable component of your organizational security awareness program. SecurityIQ PhishSim customizable landing page includes a high-quality interactive phishing awareness module, complete with several exercises. This module is:
- Presented immediately after the employee falls for a simulated phishing attack, or can be accessed later via unique URL.
- Is platform-independent and scalable to be comfortably viewed on any device with a web browser.
- Trackable, so you can see exactly which employees completed the training and when.
With phishing attack methods evolving, and new threats (like self-propagating ransomware) emerging, compromise of even a single email account, even if it is not being used as primary communication method, is a great risk that most organizations have to face. Think like a sophisticated attacker and arm yourself with sophisticated tools, such as InfoSec Institute’s SecurityIQ, to be help your employees, regardless of their role within the company, develop safe information technology habits.
See Infosec IQ in action
Check out our top 9 free phishing simulators article.