Phishing attachment hides malicious macros from security tools
A clever new wave of phishing attacks prove malicious, macro-enabled attachments can still bypass security tools and pack a serious punch under the right conditions.
The attacks, recently spotted by researchers at FireEye, targeted financial services organizations in the United States, tricking them to download and deploy a backdoor giving attackers full control of the victim’s environment.
See Infosec IQ in action
Is your organization susceptible to phishing attacks? Find out today with a free Phishing Risk Test!
How does this attachment attack work?
At first glance, this attack looks similar to many phishing attachment attacks.
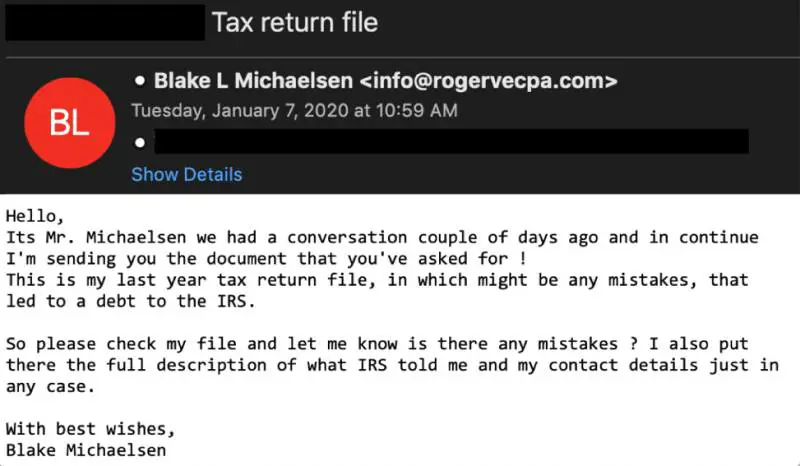
Image courtesy of FireEye
Although the grammar is an obvious red flag, the attacker uses an email address and domain including “CPA” in an attempt to legitimize the tax-themed email and encourage the victim to download the attachment.
This attack’s greatest disguise comes with the attachment itself.
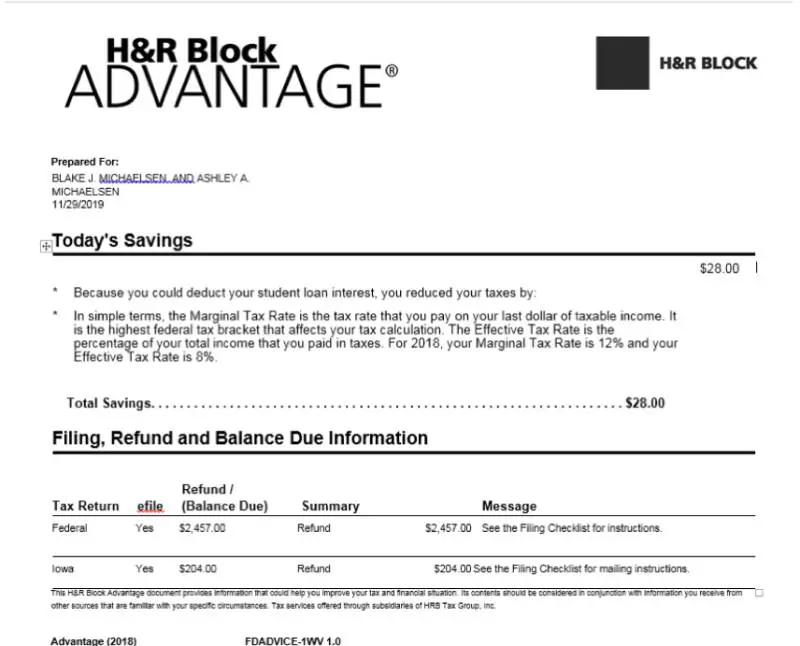
Image courtsey of FireEye
The attachment is well formatted and takes advantage of legitimate H&R Block branding.
While the visual elements of the attachment lend credibility to the email, the real danger of this attachment phishing attack is the hidden macros. With this attachment, attackers used a technique called VBA stomping to hide the macros used to download and deploy the malicious code. Under the right conditions, this allows the email and attachment to pass antivirus checks which normally flag macro-enabled files.
What is VBA stomping?
VBA stomping is a technique attackers use to manipulate VBA source code in Microsoft Office files and hide malicious code in the file’s pseudo-code (or p-code). Security tools that only check the VBA code of the file may not recognize the macro-enabled functionality and may fail to flag a malicious file. In this scenario, the email above could land in an employee’s inbox or be opened without an antivirus warning.
Although VBA stomping can be an extremely effective technique, there are several limitations that may stop the attack in its tracks. For example, the malicious p-code must be compiled for the same version of Office with which the victim opens the file or the macro will not execute as intended. This requires the attacker to uncover the Office version used by their target organizations or victims before launching an attack.
What does this mean for your organization?
The above attack isn’t perfect or undetectable by any stretch. It is possible that your antivirus software will catch a VBA-stomped file or that your most cyber-aware employees will notice the red flags if the phishing email manages to reach their inbox. However, this attack serves as a reminder that cybercriminals operate on the playing field set up by your business technology and security tools. In this case, exploitable elements in Office files and a way to coax a benign antivirus assessment provide hackers with a roadmap to exploit an unsuspecting employee.
It’s impossible to know where future attacks will come from and if your existing infrastructure can protect against them all. That’s what makes training and empowering each employee to recognize and report the security threats that reach them so important.
Prepare your workforce with awareness, training & phishing simulations
Security awareness and training platforms like Infosec IQ give you the tools and training content to educate your workforce and inspire them to adopt habits that will keep your organization secure. Infosec IQ also includes phishing templates like the attack above to help you prepare your workforce for real, active attacks.
See Infosec IQ in action
Want to test phishing susceptibility at your organization? Run a free Phishing Risk Test and learn your organization’s phish rate in 24 hours.









