Overview of phishing techniques: Fake invoice/bills
Introduction
Invoices can be a costly matter — and not always in the usual sense. Phishers believe that you would have a hard time spotting fake bills, which is why they’re increasingly using them as part of their mass mailings.
These scams happen when adversaries trick individuals into transferring funds by acting as legitimate companies. Paying just a single fraudulent bill can set you up for being a victim of a bigger fraud down the line.

Two year's worth of NIST-aligned training
Deliver a comprehensive security awareness program using this series' 1- or 2-year program plans.
Phishers can send fake invoices/bills to both individuals and companies. Last year, a Lithuanian man pleaded guilty for sending bogus invoices for computer gear to Facebook and Google. The scam allowed the fraudster to bilk the tech giants out of $123 million over the course of two years.
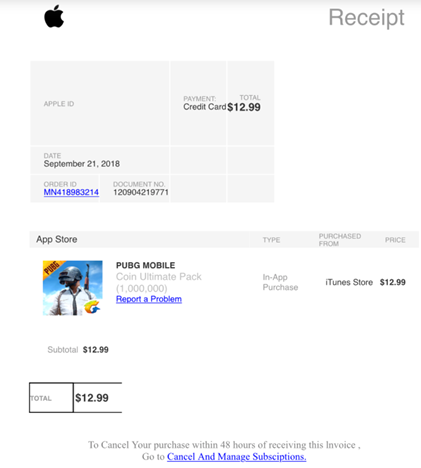
On an individual level, many Apple users received fake iTunes bills for purchases they didn’t make. Phishers duplicated an authentic Apple email and also placed the company’s logo on the invoice, making it difficult to determine whether it was legitimate or fake. Below is an example:
In this article, we take a closer look at how fake invoice and bill phishing scams work. You’ll learn about common attack techniques, how to identify the potential red flags and what defensive measures are available to you.
How do fake invoice/bill scams work?
Typically, these scams work in three steps:
- Phishers attempt to find contracts and names of suppliers providing goods to a particular company
- They impersonate a legitimate supplier and send bills to subordinate personnel
- They try to solidify their efforts by sending fake letters that claim to come from the actual supplier’s designated bank
Fake invoice scams take advantage of the fact that the average email user or someone handling administrative tasks for a business may not know whether any product or service has actually been purchased. Strapped for time, recipients either quickly make decisions about due payments or delegate duty for cutting checks to a lower-level employee who doesn’t have the means to cross-check with the vendor.
Why are fake bills scams so successful?
These scams are often so successful because they feature common items. Products such as computer supplies are mentioned on the bill, a product so ubiquitous in many people’s budgets that it causes the recipient to automatically proceed with the payment. Also, fraudsters conduct thorough research to make sure they’re sending the fake invoice to the right person — that is, someone who has the authority to pay but who’s unlikely to verify the purchases.
Finally, the sender of the fake invoice may create an impressive website and list names of respected companies, as if those companies are clients of the company that sent the invoice.
Common attack techniques
Fraudsters leverage various techniques to trick people into sharing sensitive information or transferring money into their bank. Below are some methods:
- Imitate a legitimate vendor: Fake invoices are often mocked up in a format that matches a particular vendor’s invoice, with only the payment account number modified. This helps them appear legitimate on first glance. Adversaries may even copy an actual invoice so that reference details like dates, purchase order number, customer numbers and invoice number are all accurate.
- List a particular value: Fake bills are often deliberately valued so that they meet the standard authority thresholds for mid-tier managers and AP (Accounts Payable) staff to sign off. When a busy approver gets an invoice with a value that’s within range of normal expectations, he or she will clear it and move on.
Red flags
How do you know if the invoice attached in an email is legitimate or fake? Here are some red flags:
- Have you ever received an invoice where you weren’t given a lot of time to make payment? Adopt caution, as it might be a sign of a fraudulent bill. Phishers often send time-sensitive invoices to make sure they’re able to succeed before anyone discovers their intent.
- Another red flag is the incorporation date of the company. If the company was recently established and those running it say they had issues with previous business operations, there’s a good chance that the invoice they sent is fake.
- You may get an invoice with an email address that is very close to your actual supplier’s address, but with a few symbols or letters off (for example, @as0s.com rather than @asos.com).
- To prevent verification, phishers exclude contact information or claim that they have limited phone coverage.
- Fake invoice scams often fail to clearly state what the bill is for.
Preventive measures
There are several ways you can avoid becoming a victim of fake invoice schemes. The next time someone sends you a bill, make sure to take the following measures.
- Create effective communication channels so payment requests can be verified. For example, ensure personnel can ascertain any invoice from the issuing company by feeding contact data (email, phone number, etc.) into a CRM.
- Review every email address carefully, especially those dealing with invoice-related matters.
- Keep an eye out for frequent billing reminders. Fraudsters will send more reminders than a legitimate vendor.
- Prevent invoice buildup to make it easy for authorizers to spot discrepancies. If the person in charge of payments has to clear 200 invoices instead of 20, the authorization will likely be done in a rush. Try your best to clear the backlog so your employees can spend more time determining whether a bill is authentic or fake.
- If the sender claims that there has been a change in business practice, check how previous invoices were issued. Were previous bills posted via regular mail, while this one is emailed? Were previous payments done via credit card, but now they want you to make a bank transfer?
- Don’t be pressured into clearing payment. Adversaries may try to inject FOMO (fear of missing out) — for instance, by saying you won’t get a discount or free shipping. Don’t be a victim. Genuine suppliers will understand that it can take a while for a company to clear an invoice.
- Consider combining employee IT training with phishing simulation programs where you teach staff how to identify and prevent fake invoice schemes.
Conclusion
Invoices/bills should be carefully analyzed before they’re cleared or approved for payment. Oversight on your part may result in you losing your hard-earned money or damaging the reputation of your company. Fortunately, fake invoices can be avoided if you take some proactive measures such as reviewing invoice details carefully, checking the issuer’s history, and providing robust training.
Phishing simulations & training
Sources
- Man Pleads Guilty To Phishing Scheme That Fleeced Facebook, Google Of $100 Million, NPR
- iTunes Billing Scam, Scam Detector
- Fake Invoice Scams: Is Your Business at Risk?, Universal Funding Corporation