Phishing Attacks in the Not-For-Profit Industry
Introduction
Although the non-profit sector is not in the top phished industries of 2017, it is not as safe as one may think. The statistics from Privacy Rights Clearing House (PRC) show that between 2005 and 2014, over 100 security breaches in the sector have been detected, exposing over 2 million records to serious threats. In fact, this ended up with 250,000 records subject to hacking or malware, especially in the education and healthcare fields. Of course, not all the security breaches involve phishing, but these numbers are food for thought about information security of Not-For-Profit Organizations (NPOs).
Why Phish the Not-for-Profit Sector?
The motivation cybercriminals have behind launching phishing campaigns against NPO depends not only on what kind of data it collects from its members and other stakeholders, but often on its mission and activities.
Phishing simulations & training
A typical type of attack, with the purpose of identity theft through the collection of sensitive information such as financial information and social security numbers, is the “sophisticated cyber-attack” which was conducted against the Los Angeles Gay & Lesbian Center. This attack was suspected to compromise 59,000 personal information accounts between September 17 and November 8, 2013. It is typical because it could happen in any other sector as well.
Nevertheless, organizations in the non-profit field are often involved in activities whose details are of high value for any third parties potentially interested in hacking their systems. An example of that is the security breach in the web server of the Veterans of Foreign Wars (VFW) in April 2014, led by a hacker presumably based in China, and whose supposed motivation was to collect information on military plans or military contracts. Even if it is unclear whether he reached this goal or not, he could have collected 55,000 members’ personal information!
Human rights and democracy organizations are another example, especially since their activism might be disturbing and annoying for a third party. An unnamed organization reported being a victim of a cyber-attack in 2013 and 2014 aimed at collecting information about its activities and the people who were involved in it. The end-purpose of this operation wasn’t money or sensitive data, but to stop its work and even harm the persons involved in the organization, and hacking the organization’s systems was only the first step. More recently, in 2016 and 2017, a big phishing campaign known as “Nile Phish” targeted a specific portion of the Egyptian civil society. The victims included lawyers, journalists and activists, and were involved in the 2011 “foreign funding” Court Case 173. In it, the government prosecuted Non-Governmental Organizations’ (NGO) workers for using funds from a foreign origin against the governing system. The phishing campaign has been reported to add pressure on the civil society in Egypt. Another example is the post-Trump election phishing five wave campaigns, led by the famous Cozy Bear that targeted NGOs, political think tanks and even the US government.
In other cases, NGOs have simply taken weak information security measures and procedures. These attacks are costly, and NGOs may not be able to afford them, making their entities vulnerable to security breaches, especially if they are interacting with other big organizations. Yet in other situations, NPOs collect sensitive information which is not necessarily needed for their activities, making themselves attractive for hackers.
How Are NPOs Phished?
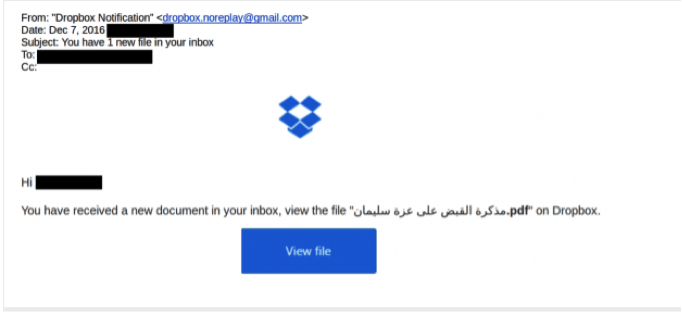
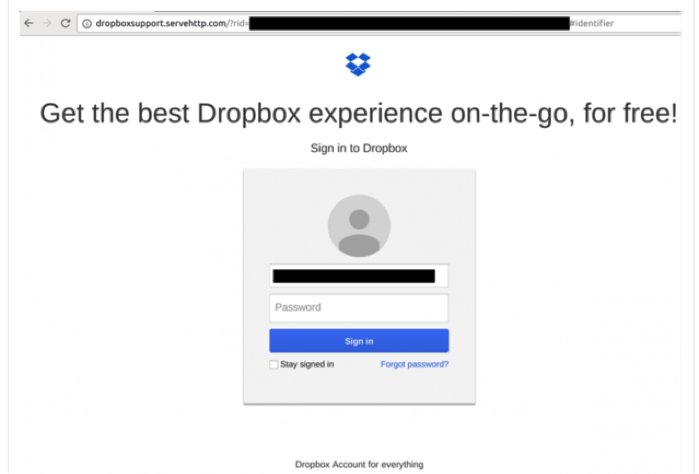
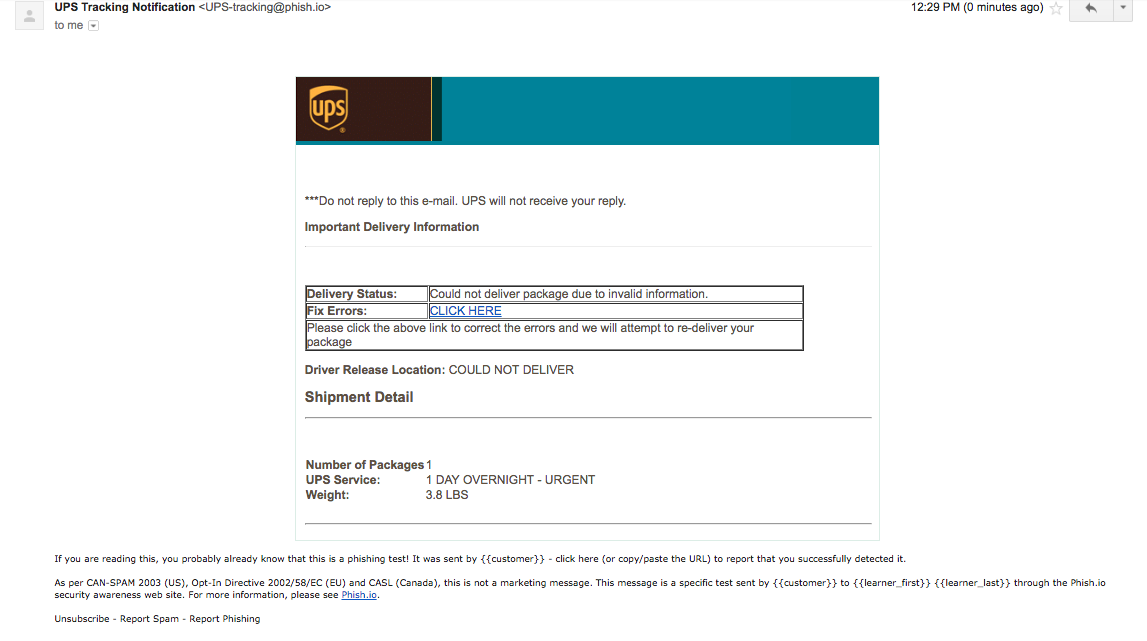
Back to the Nile Phish campaign. It consisted of two phases where 92 phishing emails have been recorded. In the first phase (November 2016-December 2016), emails were sent to organizational and personal email addresses of targeted activists. They embedded Google-like and Dropbox-like malicious links, supposedly leading to highly important data related to Case 173. The phishing emails included travel ban lists, invitations to discuss the case, or a letter from the civil society to the country’s president about the matter. The most advanced email was an invitation to download the arrest warrant of a lawyer arrested the same day of the attack (Figure 1), which in its turn led to a sign-in Dropbox platform where the person’s email was already pre-filled (Figure 2).
Figure 1. Phishing email with a fake Dropbox link
Figure 2. Fake Dropbox registration platform
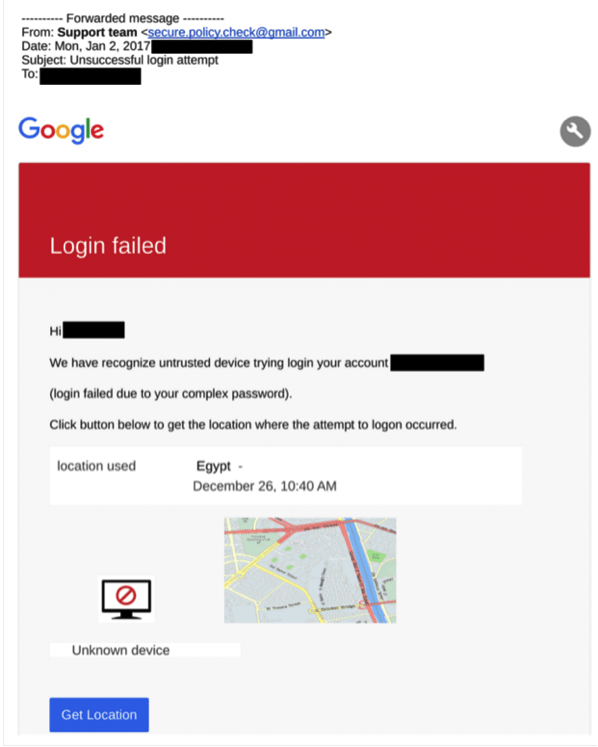
In the second phase of the campaign (December 2016- February 2017), failed login and insecure connection malicious and personalized emails were sent to similar target NGOs (Figure 3).
Figure 3. Fake Gmail security alert
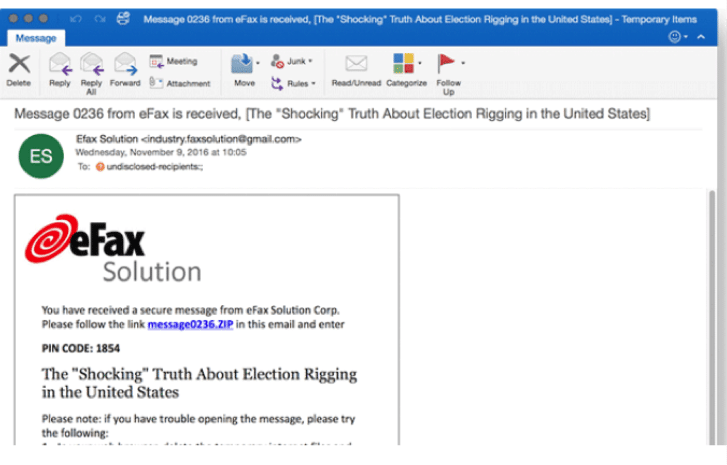
Similarly, the Cozy Bear phishing attack used Gmail accounts and in addition used a Clinton Foundation’s email address and even the hacked account of a Harvard professor to send emails where malicious programs were embedded in a Zip attachment and a PNG file (Figure 4).
Figure 4. Fake Zip file link in a phishing email
Three Strategies for Preventing non-profit organization Phishing
Educate your employees
The key actors who may fall for the phishing trick are the employees, and as a famous French quote says: “A wise man is worth two”. Therefore, communicating with employees is the most effective way to prevent sensitive data from being stolen by a third party. This helps make them aware of the risks and how to avoid them. Communication starts first by educating the employees on the matter, and the InfoSec Institute, through its SecurityIQ program, has designed AwareEd, which is a strong security awareness program that will not only help you communicate with your personnel, but it will most importantly make your employees active participants in it through videos and interactive components. AwareEd can be personalized to a specific audience (i.e top management, officers) and with company-specific content for premium users. AwareEd makes learning fast and fun for your employees and does not require a lot of effort from them in the process. In addition, the program allows you to follow the progress of the course participants and generates reports about the course. This in its turn saves not only the organization’s time and money, but keeps it safe from phishing dangers.
Put into practice what your employees are now aware of
In addition to AwareEd, and for optimal results, InfoSec puts at your disposal PhishSim, which is the second component integrated to SecurityIQ. With PhishSim, you can test your employees in real life situations, measure to which extent they can figure out what are potential phishing emails and complete their learning by making them practice. Indeed, this tool allows you to create real-looking phishing email templates and campaigns and send them to your employees. These emails can be exactly similar to what has been sent in the “Nile Phish” and Cozy Bear campaigns described above; they can come from an actual donor to the organization asking for an explanation on the high debit on his bank card by the non-profit, a disappointed president who wants to see more volunteers involved in the non-profit activities, or a message from the IT department asking for a security check. But in this case, if the employees open the email and click on the theoretically compromised link, they are redirected to a video that explains to them how they were mistaken.
AwareEd and PhishSim are complementary. You can start by using one or the other, for instance, you can run first the PhishSim campaign, then ask lured employees to enroll for AwareEd. However, it is important to keep in mind that for a better use of PhishSim, it is preferred to surprise your employees and not make any communication about the tool and its purpose, nor announce the dates of the “fake” phishing campaign.
Follow a minimum of security measures
In addition to making your employees aware, there are other preventive and curative phishing measures that you are recommended to take. Make sure to put security as a top priority in your organization by implementing documented security procedures and policy as a “steps to follow” guidance. This might include a breach internal reporting procedure, for instance. Furthermore, do not neglect your trademarks, and protect them beforehand by registering them in countries where your organization is active. This way, you can play the card of property rights violation. Depending on the severity of the case, you can also consider reporting to authorities through law enforcement, as phishing may be a crime. This can be done in different ways depending on your location. At the federal level, it is possible to report the case online to the U.S. Federal Trade Commission or by alerting the Internet Crime Complaint Center of the Federal Bureau of Investigation. It is also important to report to the Applicable Domain Name Registrar, after which the fake domain used to scam individuals can be shut down.
Conclusion
In the game of phishing, hackers double their imagination to find tricks to get what they want from the malicious emails they spread, and the Non-Profit sector stays a target, especially when it comes to spear phishing, where emails are highly personalized and directed to specific individuals. This is even more dangerous when it involves the lives of concerned people, as we saw in some cases. Training stays the pillar to prevent collecting sensitive data through phishing, as this kind of cyber-attacks primarily involves the individuals clicking on the infected links.
References
https://blog.watchpointdata.com/spear-phishing-examples
https://www.statista.com/statistics/266161/websites-most-affected-by-phishing/
http://www.thenonprofittimes.com/news-articles/nonprofits-also-hooked-phishing-trips/
http://securityaffairs.co/wordpress/53318/intelligence/cozy-bear-post-election.html
https://www.schgroup.com/w-2-phishing-email-scam-spreads-not-profit-organizations/
https://citizenlab.ca/2017/02/nilephish-report/
See Infosec IQ in action