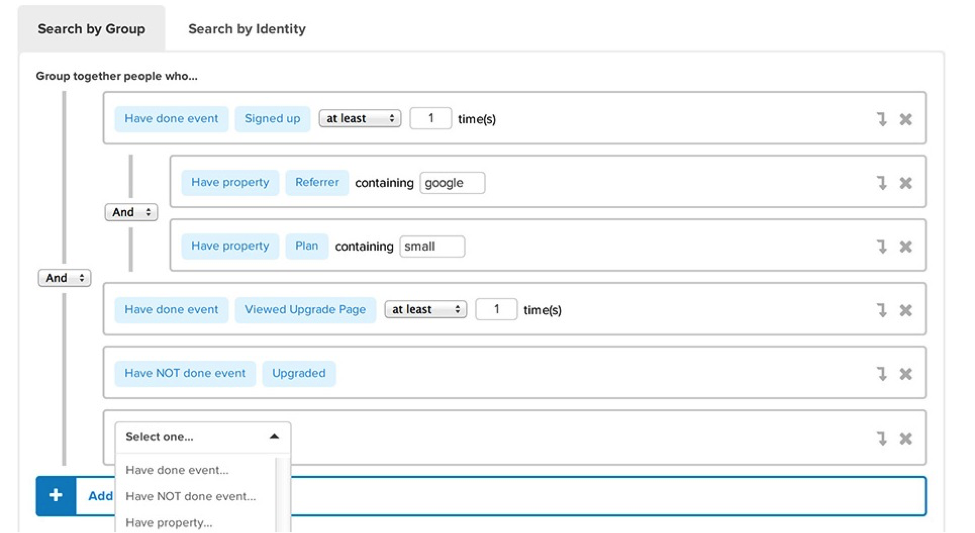
Phishing Variations: Watering Hole Attacks
Watering Hole Attacks
Related Phishing Variation Articles:
What is a Watering Hole Attack?
Now that phishing has become a widely understood and common phenomenon throughout the world, more users are getting smarter about responding to emails. Not only are cyber criminals adopting more advanced phishing mechanisms such as spear phishing, they are also looking for new ways to infiltrate into their target’s system. In a phishing email, a cyber-criminal intends to trick the receiver into providing his/her sensitive information or clicking a malicious link. In a variation of phishing called a watering hole attack, instead of attacking targets, cyber criminals set up a trap for the user and wait for the prey to come to them.
See Infosec IQ in action
The term “watering hole attack” refers to predators in nature that lurk near watering holes in the hope of attacking a prey nearby. In the cyber world, these predators stay on the prowl near websites which are frequently visited by their prey. They wait for an opportunity to infect these websites with malware to make their target vulnerable.
It won’t be wrong to compare watering hole attacks with spear phishing attacks, as in both cases, the prey is normally a group of employees of a large company or government office – and the aim is to gather their sensitive information. Though not as common as spear phishing, they pose a high risk as they cannot be easily detected and usually target connected vendors, business partners, or employees with low security systems.
How is a Watering Hole Attack Carried Out?
To understand it better, let us see how a watering hole attack is planned and carried out in general.
- Finding the Target: The attacker finds out a target organization, but cannot attack head-on because of its tightened security.
- Discovering frequently visited websites of the target: The attacker – with the help of internet tracking tools like KISSmetrics and AddThis – then discovers the websites frequented by the users of their target organization.
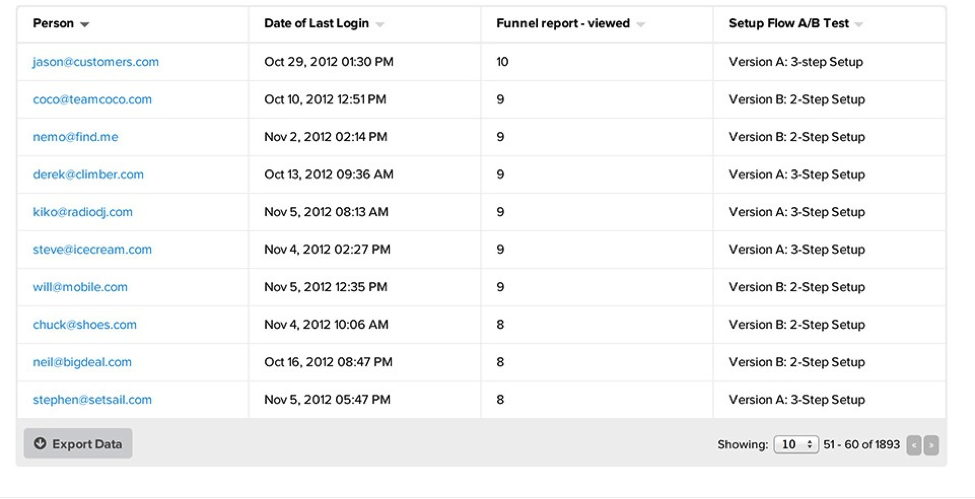
As an example, the screenshots below show a demo report of “People Searches” on KISSmetrics. It is one of the many reports that can be generated according to various demographics and market segments and shows groups of people having similar behaviors and characteristics. It also helps you find dedicated customers and those that need to be reengaged in order to make them repeat customers. This can also help find out which category of people regularly visit a website.
Why Do Watering Hole Attacks Work?
Just like spear phishing attacks, watering hole attacks also hold high success rates. The question is, why? The answer: because attackers can easily get information about which websites and links users click with the help of web analytics tools. Most of the time the attackers compromise legitimate websites which are not blacklisted and can be effectively used to deliver malware. They exploit zero-day vulnerabilities as they are unknown to the vendor at that point. It is difficult to avoid them altogether unless you completely stop using the web. It would certainly not be feasible if you ban your mobile developers from looking online for an important resource that they need to get their job done. Again, you cannot stop a government official from contributing to an online policy resource. Hackers understand this, and this is how they succeed in conducting successful watering hole attacks.
What is the Impact of Watering Hole Attacks?
Watering hole attacks are strategically planned, where instead of targeting random websites, the attackers carefully select legitimate and trustworthy ones to compromise. Relying on visiting trusted sites alone to avoid online threats can no longer be considered as a safe practice. In addition to financial loss and leakage of critical information, watering hole attacks can also impact the organization’s operations. If a watering hole attack is successful in dropping a Remote Access Trojan (RAT), the attacker can also get to carry out commands on the infected servers. This can include monitoring and spying the target organization’s activities. Once the attackers infiltrate the network, they can also modify or delete crucial files and initiate harmful attacks resulting in huge losses to the organization.
Real Life Examples
In the past few years, some high-profile incidents of watering hole attacks have been documented. Let us look at some of those.
In mid-2012, a campaign called VOHO was identified by the RSA. It was aimed at a specific group of organizations – particularly local government agencies and businesses in some specific geographical locations. Attackers selected the sites carefully and inserted malicious JavaScript, thus delivering a Gh0st RAT variant.
In December 2012, the website of Council of Foreign Relations (CFR) was compromised and made to host malicious content to its users. The attackers exploited a zero-day vulnerability in Internet Explorer, where visitors were dispensed with backdoor malware in their systems.
In November 2014, a group of Chinese attackers infected Forbes’ website and targeted visitors from US defense and financial service industries. The Advanced Persistent Threat (APT) exploited two zero-day vulnerabilities. One was in Microsoft Internet Explorer and the other in Adobe Flash Player. The campaign appeared to last only for a few days, but the possibility of it staying for a longer period of time could not be ruled out.
Watering Hole VS Spear Phishing
It’s been a while now that watering hole attacks have been proven to be a successful attack strategy by hackers. After analyzing some of the prominent examples of these attacks, many in the industry now consider them to be as good a technique as spear phishing. Like many other tools, both spear phishing and watering hole attacks have their own strengths that may work better than the other in specific situations. Watering hole attacks can, in fact, be seen as an additional technique at the disposal of cyber criminals.
These attacks do have an edge – their ability to work without employing exhaustive social engineering techniques. It involves lesser work on the part of the attacker and only requires compromising a website that is frequented by the target users. But then again, once a large number of users visiting the website are compromised, the flood of information gets difficult to be handled. The attackers then need to thoroughly scan huge data and break it down to find valuable information.
On the other hand, spear phishing allows attackers to focus on specific targets and gather precise information. In case a spear phishing attack is successful, it grants immediate access to the target’s system. Though spear phishing can exploit zero-days to inject malware on hosts, it does not depend upon vulnerabilities to do that. However, a spear phishing attack requires careful social engineering techniques to identify targets and its success depends upon how well-crafted and seemingly genuine an email is, so as to compel the target to respond positively.
How to Prevent a Watering Hole Attack
Although not necessary, watering hole attacks usually make use of new tactics and exploits that are unknown to signature-based approaches, which rely on past knowledge of threats. To ensure advanced security levels, organizations need to put in additional layers of protection – like behavioral analysis – which has a higher probability to detect these zero-day threats.
Let us look at some prevention measures organizations can take to minimize the occurrence of watering hole attacks.
Updating Software Regularly
Although watering hole attacks are usually carried out with new exploits and vulnerabilities, keeping systems up to date with the latest software patches can reduce the probability of being hit by those employing old vulnerabilities for their attacks.
Shielding Vulnerabilities with Virtual Patching
Virtual patching is the act of shielding new vulnerabilities as they are discovered, before they can be exploited. Software vulnerabilities are discovered every month. It is often impossible or too expensive to develop timely patching solutions for them. Virtual patching makes use of intrusion detection and prevention systems to shield vulnerabilities before being exploited. This can help you in getting immediate protection of your endpoints and servers before patches can be set up.
Detecting Suspicious Network Traffic
Regardless of the exploits launched by the attackers, traffic generated by the malware during communication with command-and-control server remains steady. With the help of Network Traffic Analysis tools, such communications can be detected and security measures can be implemented by organizations to decelerate the attack.
Scanning Websites for Malware Detection
Large enterprises, on their behalf, should implement processes to ensure that their websites are malware-free and not used for conducting watering hole attacks. Some of the techniques that are used for securing Web 2.0 widgets can be used for malware detection as well. Other than that, services by Internet security providers – such as Comodo and GeoTrust – can be attained for daily scanning of websites for potential malware.
On the other hand, organizations that are wary of being a target of such attacks should monitor and inspect the top websites favored by their employees on a regular basis. If the monitoring system detects malicious links, block the traffic and warn the user. More preferably, block the site if it continues to host malware, and contact their administrator.
Phishing simulations & training
Some Useful Tips to Follow:
- Identify and block all the analytics trackers that monitor your user activity, e.g. KISSmetrics, AddThis, Chartbeat, etc.
- Block http redirect by using browser plugins.
- Allow “auto-updates” of web browsers.
- Maintain the visibility of all tracking services being used to identify and block any new services.
- Use Web Application Firewalls from trusted vendors with cross-site scripting, SQL injection and command injection rules in the deny mode.
- Restrict access to your Content Management System to specific geographical areas.
- Create a plan to disable third-party content such as advertisements, etc., in case its provider gets compromised.
- Secure your name servers and DNS registration to prevent attackers from redirecting your domain to arbitrary locations.