Non Technical Countermeasures
Non-Technical Anti-Phishing
Countermeasures articles:
[clist id="1470331352967" post="35744"]
Phishing simulations & training
Overview
Today’s cyber scammers are quite savvy in their attempts to bypass security measures and collect information and data that should not normally be publicly exposed. Phishing, in particular, is a widely used social engineering technique that targets users by means of a bait to solicit personal information or deceive victims into performing certain actions, such as opening malicious links or attachments.
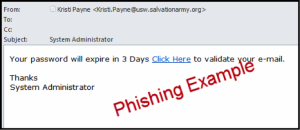
Security Awareness Training to improve phishing resilience
Recent statistics give a good measure of the growth in the number of phishing scams and how effective they really are. Today, many malicious attempts affect online financial organizations (banks, payment systems and retail stores) accounting for more than one out of three, 34.33%, of the total, according to Kaspersky Lab ‘year in figures’ 2015. The Verizon 2015 Data Breach Investigations Report, which provides insight on the cybersecurity landscape and offers an analysis of almost 80,000 incidents, including more than 2,100 confirmed data breaches, reports that 23% of recipients still opens phishing messages and 11% actually clicks on attachments; “On average, it’s just 82 seconds before a phishing campaign gets its first click.” Furthermore, analyzing the security incidents, the Verizon team found that even a small phishing campaign (10 e-mails) can have a 90% success rate and lure at least one victim.

Helping employees identify and avoid threats can be achieved with training sessions that not only introduce security best practices, pitfalls recognition and applicable policies, but also include mock phishing scenarios or exercises with pre-and post-training phishing tests; a Phishing Simulation Program, like the Infosec’s Infosec IQ campaign, for example, is designed for such a purpose. This type of program has a high return on investment, as it allows security managers to sensitize employees continuously throughout the weeks and gauge their ability to detect phishing emails. By easily crafting and sending simulated phishing messages, they can actually not only test the level of readiness the company workforce has with regards to IT security, but they can also identify topics that need to be addressed more in detail in future formal cybersecurity awareness sessions.
As anyone can be a target within an organization, it is essential to include every level and department in these campaigns. It would be ideal to craft phishing messages that are tailored to the different departments so as to test employees’ resilience to phishing by providing realistic baits they could really fall for. One of the most effective forms of phishing attacks, in fact, is spear-phishing, as it targets a particular person or a relatively small group; it uses an invasive approach and usually includes the use of e-mails that contain details that make the bait more credible to the recipient who is then more likely to comply with the message. As for regular phishing, which is less sophisticated and less specific, communicating the technical aspects of how this scam works is the best way to avoid most attacks; the purpose is to have users think twice before mindlessly responding to emails. Modifying the automatic behaviors of users is one of the main objectives of security awareness to prevent spear-phishing.
By adopting an IT Security Awareness Program, particularly against phishing and social engineering in general, it is possible to help users become ‘human firewalls’ and drive a behavior change in them that could reduce the impact of scams specifically targeting their habits. Users can learn how to avoid becoming victims of phishing attempts by employing best practices and safe behaviors like not clicking on links in an unsolicited email message. They can also learn that legitimate entities will not solicit an immediate response or ask to provide or verify sensitive information, such as login ID, password and PIN, through non-secure means. They will learn to look for signs of "spoofed" emails that can direct users to enter details at a fake website (spoof sites that look identical to legitimate sites) containing deceptive, malicious links.
Policies and Procedures for protection
Tools like InfoSec Institute’s Infosec IQ's phishing simulator “PhishSim" used to run training phishing campaigns can help businesses in their efforts to combat phishing. Sending users simulated phishing tests plays an important role in enhancing their knowledge in a practical, beyond-the-theory way and, ultimately, help diminish the likelihood of falling prey to an attack, while addressing email security awareness and the compliance requirements needed by any company. This tool can be an excellent complement to training modules offered by programs like Infosec IQ AwareEd; engaging, interactive education modules coupled with hands-on practice are essential elements in an articulated, multi-faceted security awareness approach.
Another important part of awareness training is making employees aware of internal policies; policies and procedures serve as effective non-technical countermeasures for phishing attempts by providing users with rules and regulations that dictate proper response behaviors and correct use of systems and software. It’s imperative that an overall security plan consists of such documentation to guard against phishing scams and reduce the number of incidents. Thanks to clear policies, all staff members can be held accountable for their actions but can also be properly armed with precise guidelines in order to avoid at least the easiest scams. By abiding by the standards set forth and designed to reduce these risks, employees will likely be able to effectively prevent "hacks," "threats," or "attacks" from happening.
[cta id="1461775666362" post="35256"]
The majority of organizations have rules in place to prevent the clicking of links directly into e-mails or prohibit the downloading of certain types of files. Some prevent the forwarding of chain e-mails or the re-directing of e-mails toward private accounts. Other companies restrict the use of e-mails or instant messaging for PII or any kind of sensitive information; others don’t allow the use of instant messages or chat software if not the internal, company-provided version. Security policies also dictate rules for password expiration and complexity. These and many more restrictions give users a safe framework in which to operate. The existence of policies and procedures also show the company’s stance towards the safeguard of systems and data and shows employees how much importance is placed by its management and executives on the issue. Stressing the value of awareness and safe behaviors through company official directives empowers employees to enforce protective measures even when receiving messages that seem legitimate and sent by supervisors.
Anti-Phishing Legislation
Aside from company-policies, laws can also be effective non-technical countermeasures. The U.S. Department of Homeland Security and the FBI, to name a few, take cybercrime-related phishing and malware incidents seriously and will effectively respond to and investigate the most severe or high-profile cases on offenders that come to violate the integrity of data and privacy of others. Many illegal internet-mediated activities are prosecuted by the Computer Crime and Intellectual Property Section (CCIPS) of the DOJ. Today, there is no lack of cybercrime and cybersecurity Anti-Phishing State Laws or regulatory measures. After the Anti-Phishing Act of 2005 was enacted in California (it was never passed by Congress at the federal level though), many other computer crime laws have followed, including the cybersecurity legislation (S. 3414), that have been enacted at the state and federal levels. Victims of online phishing scams can report attacks to the proper authorities who will in turn look into the ‘phishy’ email and attempt a resolution.
The first lawsuit against a suspected phisher, a Californian teenager who had created a webpage similar to the America Online official page and allegedly used it to steal credit card information, was filed in January of 2004 by the U.S. Federal Trade Commission. AOL took further legal action to protect its members in 2006 by filing three lawsuits and making headway to make the Internet a better, safer place for all consumers by protecting the integrity of the email experience of web users, affirmed Curtis Lu, Senior Vice President and Deputy General Counsel for America Online, Inc. from 2002-2006. The ‘AOL Anti-Phishing Lawsuits Against Three Major Phishing Gangs,’ filed in Alexandria, Virginia's U.S. Court system, addressed the phishing emails transmitted to unaware internet users in the attempt to commit identity theft. A similar case happened in 2005 when Microsoft filed 117 lawsuits against unidentified scam artists who sent out spam e-mail targeting its consumers via Microsoft services such as MSN and Hotmail, mentioned Grant Gross, senior editor at IDG News Service, in Computerworld. The email phishing schemes were filed in the U.S. District Court for the Western District of Washington, said Aaron Kornblum, Microsoft's Internet safety attorney who also mentioned how, through the lawsuits, Microsoft attempted to uncover the names of the phishers to identify who was behind large-scale scam operations. Kornblum called “phishing legislation ‘critical’ to helping law enforcement agencies go after scam artists.”
[cta id="1461775666362" post="35256"]
These early phishing court cases contributed to identify the need of a legislative approach to the problem. Laws can’t help companies eliminate the risk of social engineering attacks and, of course, can’t help identify perpetrators and eradicate the issue; they can, however, provide a clear definition of what is to be considered a crime and what are the avenues businesses and customers can use to denounce attacks and seek help and relief. A recent example of a phishing case that hit a courtroom is the infamous iCloud hack that eventually caused the stealing of hundreds of personal information and pictures of users including world renowned celebrities. The U.S. Attorney for the Central District of California accused Ryan Collins of devising a phishing scheme from November 2012 until the beginning of September 2014 that allowed him to obtain usernames and passwords for the iCloud and Gmail accounts of his victims. In March of 2016, he agreed to plead guilty to a felony violation of the Computer Fraud and Abuse Act and will face a sentence of up to 5 years in federal prison (the recommendation was for 18 months).
Conclusion
The rise in email phishing scams is apparent today. These threats can affect anyone, so raising security awareness about it can help computer users be more discerning and savvy against attempts to compromise their systems and personal data. As phishing has a very non-technical component and targets users and their online behaviors, in order to reduce the likelihood of falling victim to this type of threat, companies shall complement technical protection tools with 'non-technical' countermeasures including specific, almost around-the-clock sensitizing campaigns and specific policies and procedures that can help employees be less vulnerable to skillful attacks. The role of education in the company regulatory effort and states’ legislation (as well as law enforcement) is paramount in the fight against this elusive scam scheme.
References
America Online. (2006, February 28). AOL Takes Fight Against Identity Theft To Court, Files Lawsuits Against Three Major Phishing Gangs. Retrieved from https://web.archive.org/web/20070131204118/http:/media.aoltimewarner.com/media/newmedia/cb_press_view.cfm?release_num=55254535
Ferrara, J. (2014, September 3). Phishing Scams at All-Time High, Employee Training Not Keeping Pace. Retrieved from http://www.wallstreetandtech.com/security/phishing-scams-at-all-time-high-employee-training-not-keeping-pace/a/d-id/1306866
Grant, G. (2005, March 31). Microsoft files 117 phishing lawsuits. Retrieved from http://www.computerworld.com/article/2556692/cybercrime-hacking/microsoft-files-117-phishing-lawsuits.html
HG.org. (n.d.). Computer Crime Law. Retrieved from http://www.hg.org/computer-crime.html
Orlando Scott-Cowley. (2014, August 19). The 'human firewall': a more proactive approach to infosec. Retrieved from http://www.scmagazine.com/the-human-firewall-a-more-proactive-approach-to-infosec/article/367038/
Phishing.org. (n.d.). 10 Ways to Avoid Phishing Scams. Retrieved from http://www.phishing.org/scams/avoid-phishing/
Rubens, P. (2012, November 26). How to Prevent Spear Phishing Attacks. Retrieved from http://www.esecurityplanet.com/network-security/how-to-prevent-spear-phishing-attacks.html
StaySafeOnline.org. (n.d.). Spam & Phishing. Retrieved from https://staysafeonline.org/stay-safe-online/keep-a-clean-machine/spam-and-phishing
The Federal Trade Commission. (n.d.). Consumer Information – Phishing. Retrieved from https://www.consumer.ftc.gov/articles/0003-phishing
Phishing simulations & training
US Department of Justice. (2016, March 15). Pennsylvania Man Charged with Hacking Apple and Google E-Mail Accounts Belonging to More Than 100 People, Mostly Celebrities. Retrieved from https://www.justice.gov/usao-cdca/pr/pennsylvania-man-charged-hacking-apple-and-google-e-mail-accounts-belonging-more-100










