Anti-Phishing: Threat Modeling and Impact Analysis
Introduction
Phishing is an efficient and cost-effective cyberattack. It has prevailed in cyberspace for over two decades. Phishing is commonly considered a low-level cyberattack against careless individuals and institutions. Generic emails containing malicious links or malware can easily be detected by antivirus software and the embedded security of web browsers. It is unlikely to fall prey to such a low technique. Nonetheless, the statistics reveal a shocking reality in which phishing severely affects thousands of institutions. The impact of phishing includes data and identity theft, confidential information exposure, and costly reputation and monetary damages. The FBI estimates over 2.3 billion USD was lost as a result of a specialized type of phishing attack, whaling, between early 2013 and 2016. Whaling is a phishing attack targeting C-level executives. One notable example is the case of Mattel in April 2015. The company was scammed by Chinese phishers and nearly lost three million USD. Another major event involving the central bank of Bangladesh in February 2016 also reveals the effectiveness of phishing. It is believed that the computer networks of the central bank of Bangladesh were previously compromised by multiple spear-phishing attacks. This enabled the attack operators to carry out actions aiming at the transfer of 951 million USD from the accounts of the central bank of Bangladesh. As a result, 101 million USD was successfully withdrawn and transferred to foreign bank accounts located in Sri Lanka and the Philippines.
Low-level phishing messages easily arouse the suspicion of the recipients. However, the aforementioned cases demonstrate the effectiveness of context-aware phishing schemes—whaling and spear-phishing. Encapsulating victims in an appropriate context so as to make them believe the authenticity of the message is a powerful strategy. As one security researcher, Markus Jakobsson, puts it, “phishing is the marriage of technology and social engineering.” Phishing is always the first step to compromise the entire computer networks of the targeted victim. It is imperative to stop believing that phishing is a mere simple trick.
Phishing simulations & training
Institutions should implement a holistic evaluation and threat modeling of the risks their staff, collaborators, and digital assets face vis-à-vis phishing. Through this approach, the threat model can further be used to analyze the impact and thus to identify the appropriate solutions.
Threat Modeling for Phishing
It is a misconception that a mere antivirus program could stop phishing from breaching the internal network of an institution. By default, antivirus filters only know malicious IP addresses, websites, and senders. Therefore, novel phishing tactics and attack origins that are not previously recorded can slip through detection. A group of Brazilian cybersecurity researchers suggests that it normally takes more than 60 minutes for the security product vendor to identify a phishing campaign and thus update the database to block it (Olivo et al., 2013). Using antivirus software is a first step, but it is inadequate to tackle increasingly sophisticated phishing schemes. Institutions should approach the issue via upstream threat modeling.
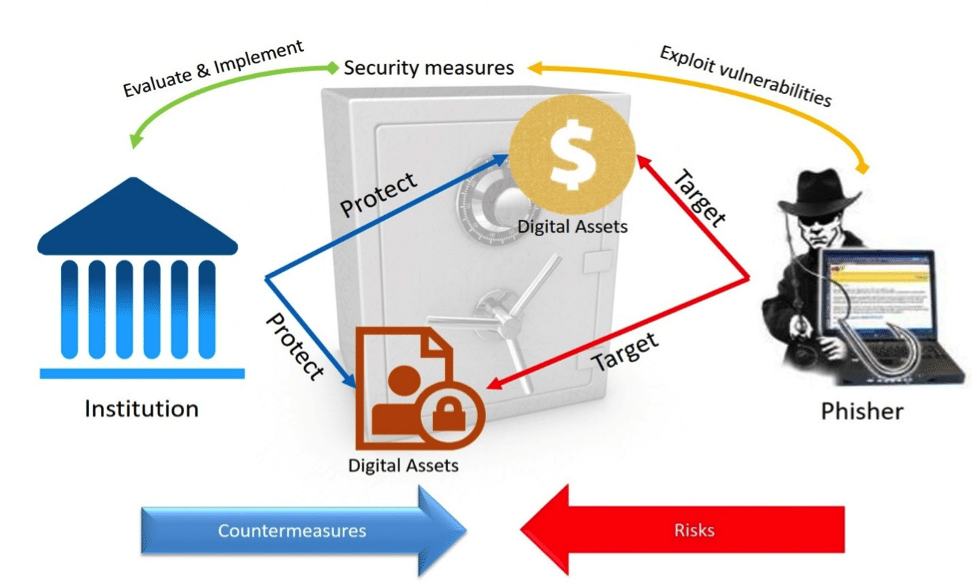
Indeed, three perspectives can be adopted in establishing an effective threat model for phishing. They are attack-centric, system design-centric, and asset-centric. The attack-centric approach takes the attacker’s perspective to overview the weaknesses of the institution. The system design-centric approach focuses on operations to enhance the global security performance. The asset-centric approach takes an in-depth assessment to prioritize and protect the key digital properties. In the case of phishing, the asset-centric approach would be most useful because the other two methodologies emphasize the constantly changing and diversified external security factors. Focusing on the internal digital assets of the institution improves global security awareness and also tackles two successive internal security aspects of the institution: technical vulnerabilities and personnel training. The asset-centric threat modeling outlines the three Ws: What digital assets are at stake? What attacker profiles would be interested in such assets? Which security compliance and product should be adopted to protect the assets? The following diagram demonstrates the dynamics of the asset-centric threat modeling approach:
Figure 1. Security Relationship Model of Phishing
There are four attributes, the three Is and one M, to recognize in threat modeling: identification of assets, threats, and vulnerabilities, plus threat mitigation. The three Is are interrelated, as the digital assets provide considerable clues for the institution to anticipate the threats, motivations, attack patterns, and objectives of the phisher. This eventually contributes to recognizing the vulnerabilities of the internal systems and thus mitigating the risk.
One crucial aspect in threat modeling for phishing, different from other threat scenarios, is the human aspect. Regular system checks can significantly deal with technical vulnerabilities and weaknesses. Meanwhile, the security awareness of personnel has to evolve, depending on the growth of digital assets and external attack strategies. Social engineering attacks are commonly launched against the personnel as the initial step of a context-aware phishing scheme. Personnel also hold the key role of managing various digital assets of the institution. Naturally, gaining the trust of a staff is equivalent to compromising the digital assets that he manages. The personnel are equally important asset to the institution and should be protected.
In addition, the asset-centric perspective can integrate certain attributes of the attack-centric methodology. Stepping into the shoes of the attacker is as important as learning the internal security landscape of the institution. For example, if the digital assets are part of the critical infrastructure of a state, they will likely attract high-level attackers ranging from hacktivists having political goals to achieve, cyber-criminals seeking financial gains, to advanced persistent threat (APT) eavesdropping on confidential and sensitive information. Knowing the background of the attacker and what they are after provides useful information for the institution to foresee the potential phishing messages and defend themselves. More important, the attacker may be inside the institution. The insider threat comprises both careless and unintentional staff and malicious ones who work for the competitor of the institution or who seek revenge against their employer. Identifying these actors helps prevent the institution from getting phished inside.
In a nutshell, the asset-centric threat modeling can be established mostly based on the digital assets of the institutions. Understanding the value of its belongings and the nature of its activities can determine a great of scenarios for organizational readiness training. The institution can develop action plans accordingly.
Phishing Impact Analysis
The impact of phishing is substantial, particularly the reputational damage following a phishing attack. A Return Path report (2016) studies the impact of phishing for email marketers. It discovered that customers would be less likely to trust brands that had been victims of phishing. The read rates of these email advertisements by subscribers dropped 18% on Gmail and 11% on Yahoo. In the same study, large institutions on average spent 3.7 million USD to recover from the direct loss of phishing. Combining the figures of immediate operational and financial loss as well as consequent reputational damage can be costly to the victim of phishing. Indeed, if the phisher can usurp the authenticity of the real brand/institution, it will disrupt the legitimate message exchange between the real sender and recipient. It is difficult to regain customer confidence and the costs of rebuilding the trust will be higher than the initial customer acquisition costs. The impact of phishing is highly quantifiable in business as customers and users are aware of their service quality.
In addition, from the political aspect, the loss caused or initiated by phishing is both quantifiable and qualifiable. Chinese and Russian APTs are known for their cyberespionage and geopolitical interests. Luring victim institutions to activate malware via spear-phishing can paralyze a government website or retrieve military secrets. The 2015 Ukrainian power plant cyberattack is a vivid example of how powerful initial spear-phishing attacks can lead to consecutive lateral attacks, resulting in cutting the power supply to over 80,000 people. Moreover, the University of Cambridge and Lloyds published a study in 2015 anticipating the scenario of a cyberattack against the U.S. power grid. The global impact on the U.S. economy in this scenario would be estimated from $243 million to over $1 trillion, leaving 93 million people across 15 states without electricity for approximately 24 hours. These studies and real case scenarios provide an outline for both governmental and major private institutions to take into account when it comes to establishing their threat model for phishing.
The ROI of Implementing Phishing Controls
Phishing causes both qualifiable and quantifiable loss for institutions. It is unwise to continue to underestimate its damages. The number and sophistication of phishing attacks increase every year. Anti-phishing mechanisms ranging from anti-spam software and security landscape evaluation to employee awareness training are essential to counter and mitigate the risk posed by phishers. As a matter of fact, security can be costly but ineffective, or vice versa. Moreover, every institution should have its particular concerns in adopting security measures according to their digital assets. Phishlabs provides a good example of the costs and return on investment (ROI) of establishing phishing incident response for an institution of 5000 personnel. This sample institution will spend an average of 225,844 USD annually based on a susceptibility rate of 30%, meaning three out of ten fraudulent messages are likely to be opened by internal staff and cause various degree of damages. Thus, if a phishing awareness training program can lower this susceptibility rate from 30% to 5%, the institution will be able to save 188,203 USD per year. The ROI formula will look like this:
ROI= (Gain from investment – cost of investment)/ Cost of investment.
Following the same example, suppose the awareness training program costs 100,000 per year, the ROI will be (188,203 – 100,000)/ 100,000 = 88%. This ROI of adopting an anti-phishing training or mechanism is convincing for institutions to rethink their security landscape and start outlining its threat model. If we change these numbers with real monetary loss from a phishing incident and the cost of security awareness training, for example, the central bank of Bangladesh, the ROI will look more promising than the scenario of Phishlabs.

Get six free posters
Reinforce cybersecurity best practices with six eye-catching posters found in our free poster kit from our award-winning series, Work Bytes.
Conclusion
The condescending view of phishing as a low-level trick reveals inadequate understanding of the damages that phishing can cause for an institution. The reputational and monetary loss as a result of phishing affects the victim both internally and externally. Such damages can continue for a period of time, adding additional loss to the institution. Hence, establishing an effective threat model is necessary for institutions to defend themselves against phishing. It helps them understand the risks and threats they deal with. Furthermore, it justifies the ROI of investing in anti-phishing measures, awareness training programs, and other antimalware products.