Python for active defense: Decoys
The MITRE ATT&CK framework is probably the best-known of the MITRE Corporation’s cybersecurity resources; however, it is focused on the offensive side of cybersecurity. The MITRE Shield framework is a recent project focused on active defense.
Like the MITRE ATT&CK framework, MITRE Shield is organized into tactics (operational objectives) and techniques (methods for achieving these objectives). The difference is instead of describing how cyberattacks are performed, Shield describes ways in which defenders can act against cyberthreats.
One aspect of active defense is the use of deception. MITRE Shield describes various means by which decoys can be used to mislead and trick an attacker.

What should you learn next?
Decoy processes for active defense
Processes are running applications on a computer. The processes running on a system are of extreme interest to both an attacker and a defender. One might be looking for antivirus or other security solutions, while the other is checking for suspicious and potentially malicious programs on a computer.
Decoy processes
In MITRE Shield, decoy processes can be used for a couple of different purposes. They’re explicitly mentioned as part of the channel and legitimize tactics within the framework.
These processes can be used to trick an attacker into taking certain actions, such as trying to kill or hide from an antivirus running on a system. Alternatively, they can be used to make a honeypot look more realistic.
Decoy processes with Python
Python can be used to implement either of these types of decoy processes.
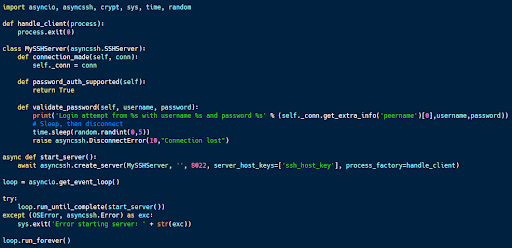
The code sample above (available on Github) is designed to impersonate an antivirus or other endpoint security solution. It then monitors and reports if a program on the system tries to kill it.
By using the signal library, the program can catch certain exceptions, allowing it to control how they are handled. In this case, the Python script catches SIGTERM and SIGINT, two signals designed to terminate a process. When a SIGTERM or SIGINT signal is caught, the program collects and writes information about the process that sent the signal to a file and then terminates (to make the signal seem successful).
This decoy process can be used to impersonate antivirus and similar solutions that malware may try to terminate (as part of MITRE ATT&CK’s Evade Defenses Tactic). By watching for attempted interference with defenses, it can help with detecting malware on a system.
Decoy content for active defense
Another way to use decoys for active defense is through fake content. Discovery of the content stored on a system is a common stage of cyberattacks, and misleading content may trick an attacker into wasting time or going down the wrong path in the next stage of their attack.
Decoy content
Decoy content is a type of deception that can be used to achieve almost all of the tactics of MITRE Shield (all except contain). The reason for this is that decisions based on false and misleading data can completely derail an attack.
Differentiating legitimate and malicious use is difficult for most content in an organization’s network. For decoy content, no legitimate use exists. This means that it can also be used as a detective control since any access attempts to the decoy content are suspicious by default.
Decoy content with Python
Python can be used to either generate and monitor decoy content.
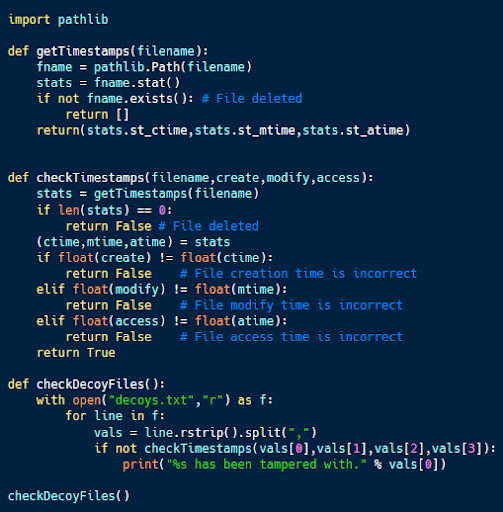
The code sample above (from here) is designed to detect if someone accesses or modifies certain files on the system. These files are listed in decoys.txt alongside their official creation, modification and access dates.
When run, this script will grab these values for the decoy files and compare them to the stored values. If there are any mismatches, then the script will alert that the file has been tampered with. This tampering could include an access attempt, modification of the file or an attempted timestamp to a time other than the true creation, access and modification times.
Decoy credentials for active defense
User credentials are a common target of cyberattackers. With the right credentials, an attacker can gain access to new systems or elevate their privileges to ones that they already have access to.
Decoy credentials
The MITRE Shield framework discusses the use of decoy credentials to help trick attackers into focusing their efforts on the systems and services that the defender wants them to. Decoy credentials could be used to drive an attacker toward a honeypot or to interact with a fake service or one that is serving fake data to a visitor.
Decoy credentials with Python
Python can be used to implement fake services that use decoy credentials.
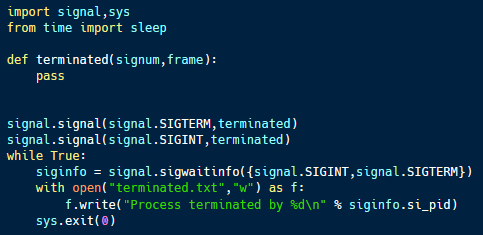
The code sample above (available here) implements an SSH server that is designed to accept connection attempts. After accepting the connection, it sleeps for a random amount of time, then throws an error, emulating a lost connection.
Such a server could be used to track an attacker’s access throughout an organization’s systems. Decoy SSH credentials could be planted on different systems. If an attacker used these credentials to attempt to connect to the service, it can reveal the systems that they have access to based on the source IP address(es) and the credentials used (if different credentials are planted on each system).
Using Python for active defense
Deception is a crucial part of active defense because it allows the defender to trick and guide an attacker into doing what the defender wants.
Python can be used with many different types of decoys, including processes, content and credentials.

What should you learn next?
Sources
- MITRE ATT&CK, MITRE
- MITRE Shield, MITRE
- Python for Cybersecurity, GitHub