Python for active defense: Monitoring
The MITRE ATT&CK framework is likely the MITRE Corporation’s most famous cybersecurity tool, but it is not the only one. To complement the offensively-focused ATT&CK framework, MITRE recently released the Shield framework. MITRE Shield focuses on active defense or how defenders can proactively protect against cyberattacks.
The MITRE Shield framework is organized similarly to MITRE ATT&CK with tactics defining operational objectives and techniques describing specific ways to accomplish these goals.
Across multiple different tactics, MITRE Shield discusses monitoring, which provides visibility that is essential for effective active defense.

FREE role-guided training plans
Network monitoring for active defense
Monitoring can be performed at multiple different levels within an organization’s environment. Since most cyberattacks come over the network and the network is used for lateral movement within an organization’s environment, monitoring at the network level is a logical component of an active defense strategy.
Network monitoring
At the network level, monitoring is focused on traffic collection and analysis. Traffic collection is relatively simple if an organization controls the infrastructure that the traffic flows over.
Analysis can be more complex due to the vast amount of network traffic in the average enterprise and the complexity of this traffic. Starting with high-level statistics and expanding to more in-depth information can be a good way to get started.
Network monitoring with Python
Python can be used to monitor network traffic and collect a wide range of data about it.
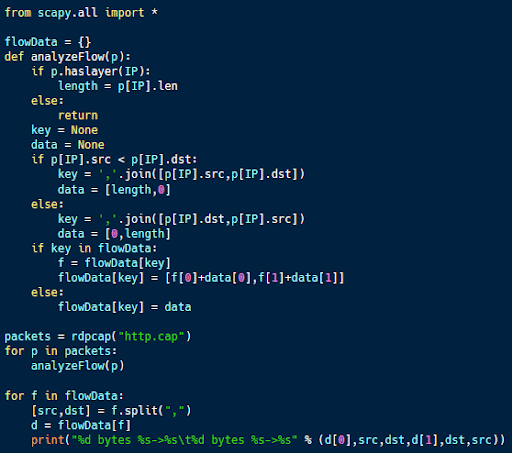
The code sample above (available on Github) uses scapy and Python to perform high-level statistical collection for network traffic. For each pair of communicating computers, it determines the number of bytes flowing from one to the other and vice versa.
This sort of statistical information, while high-level, can be useful for detecting anomalous traffic flows like data breaches. For example, most user workstations ingest more data than they send out. If this imbalance changes, then it could be a sign of an attack.
System activity monitoring for active defense
In addition to monitoring the network, it is also important to achieve visibility into an organization’s endpoints. While some threats can be detected based on their network activity, others are only visible on the infected system.
System activity monitoring
Operating systems collect a vast amount of information about the operation of the system. This includes system logs, application logs and other information sources.
This means that, when monitoring the system, it’s not necessary to collect the usage and security data yourself. Instead, it’s possible to just monitor and analyze the data contained within these built-in logs.
System activity monitoring with Python
On Windows, Python can access system log files using the win32evtlog library.
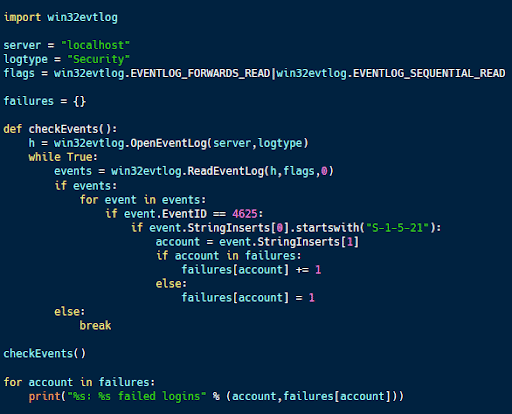
The code sample above (available here) is designed to monitor for failed login attempts on a Windows system. These failed logins can be indicative of a credential stuffing or other password guessing attack.
The code above looks at the security log for event 4625, which is a failed login request. It then filters to look for failed logins by users and records the number associated with each account. This way, large numbers of failed logins can be used to identify brute force password attacks (as opposed to a user mistyping a password once or twice).
Behavioral analytics for active defense
Behavioral analytics can be an invaluable tool for monitoring and active defense. By definition, the actions taken by a cyberattacker as part of an attack are anomalous. If a defender can identify these anomalies quickly enough and correctly interpret them, they can gain valuable insights into the attacker’s activities and potential end goals.
Behavioral analytics
Behavioral analytics can be applied to many different components of a computer. One option is to attempt to monitor the behavior of a particular user. Looking at the files accessed and other activities can potentially help to differentiate between legitimate use and a compromised account.
Another option is to look at the behavior of the applications running on a system. Malware can hide from detection in several different ways, but, in the end, the malware needs to take certain actions to achieve its operational objectives. Detecting these activities can help with identifying malware on the system and determining the scope and effects of a malware infection.
Behavioral analytics with Python
Python can be used for a variety of different types of behavioral analytics, including analyzing the activities of processes running on a particular system.
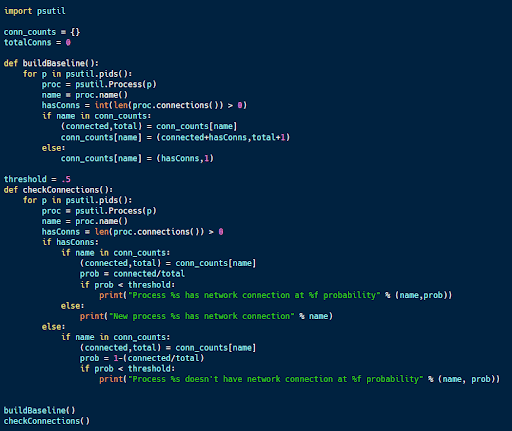
The code sample above (available here) looks at the network connections of various processes running on a computer. It’s designed to build a baseline profile of how processes connect to the network, then later run the same analysis and compare the results to identify any anomalies.
The code works by using the psutil library in Python. This package allows the code to iterate over processes and determine whether or not they have network connections. This result is stored for each process, providing a ratio of the instances of a particular process (like Firefox) that have network connections.
After building a baseline, the same process can be repeated later for comparison against the baseline. For each process with/without network connections identified, the probability that that process does/doesn’t have a network connection is calculated using the baseline and printed.
This code, while simple, can help with identifying malware masquerading as a legitimate process. For example, an instance of notepad.exe with network connections is suspicious, while firefox.exe without network connectivity may be worthy of investigation.
Using Python for active defense monitoring
Data is essential to effective active defense. Python can be used to monitor a variety of different data sources to identify activities or anomalies that may point to an active attack, enabling an active defender to take action against the intruder.

What should you learn next?
Sources
- MITRE ATT&CK, MITRE
- MITRE Shield, MITRE
- Python for Cybersecurity, GitHub