Top tools for mobile android assessments
We are living in an era where digital transformation has a vital role in our lives. With this expansion, some objects have become indispensable in our life, including mobile devices.
Security assessments are composed of techniques and approaches that ensure systems, infrastructures, and applications' security and resilience. The spectrum of an IT environment is huge, and it was enlarged in the last few years with the Internet of Things (IoT), which brought new devices into this field. In this sense, today, we are observing another part as a critical segment to secure: mobile application security.
Mobile security is seen as a critical component in any security plan, and so we now present the most popular tools to use when conducting a mobile Android assessment.

What should you learn next?
Top tools for Android assessments
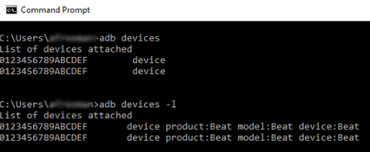
Android debug bridge (ADB)
ADB is part of the Android SDK, a command-line tool used to communicate with physical or virtual devices. This tool provides many features, such as installing and removing applications, debugging capabilities and backing and pulling data from the target device.
Some of the popular ADB commands are:
adb push <local> <remote> - pushes the file <local> to <remote>
adb pull <remote> [<local>] - pulls the file <remote> to <local>
adb logcat - allows you to view the device log in real-time
adb install <file> - installs the given .apk file to your deviceURL: https://developer.android.com/studio/command-line/adb
Mobile security framework (MobSF)
Mobile security framework, the extension form to MobSF is an automated framework to conduct static and dynamic mobile assessments. This tool is capable of performing tests under Android and iOS applications and also malware analysis.
The framework provides a REST API for integration with continuous integration or test environments on DevSecOps pipelines. With the help of a dynamic analyzer, MobSF can perform runtime security assessments and interactive instrumented testing.
URL: https://github.com/MobSF/Mobile-Security-Framework-MobSF
Dex to Java
During the Android assessment, it's necessary to revert the Dex code into Java class code. For this, some tools can be used, including:
- d2j-dex2jar: tools to work with android .dex and java .class files.
- bytecode-viewer: a Java 8+ Jar & Android APK Reverse Engineering Suite (Decompiler, Editor, Debugger & More).
- JD-GUI: it is a standalone graphical utility that displays Java source codes of ".class" files.
- Online platform: https://www.decompiler.com.
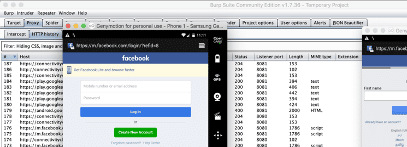
Burpsuite
Burpsuite is a popular tool typically used during web-pentests for intercepting and tampering data. Nonetheless, this tool can also check mobile application security by intercepting the HTTP requests performed by the target application in runtime.
More details on how to use Burpsuite during mobile assessments 1, 2.
URL: https://portswigger.net/burp
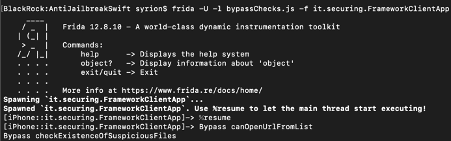
Frida instrumentation
Frida is a powerful toolkit designed to allow dynamic code instrumentation. It can be used to inject custom JavaScript code into black-box processes and modify them in runtime.
With Frida, it's possible to inject code to bypass execution restrictions and techniques that developers use to secure mobile applications, such as SSL pinning.
Frida is also provided with a set of standalone tools from its toolkit, including:
- frida-ps: command-line tool for listing processes
- frida-trace : a tool for dynamically tracing calls and methods
- frida-discover: a tool for discovering internal functions
- frida-ls-devices: command-line tool for listing attached devices
- frida-kill: command-line tool for killing processes
URL: https://frida.re/docs/home/
Objection
Objection is a tool powered by Frida and built to help experts execute their mobile assessments without needing a jailbroken or rooted mobile device.
This tool is composed of a group of features, including:
- Root detection bypass
- SSL pinning bypass
- Dump Keystore
- Dump Android Heap
- Monitors Android copy/paste buffer cache
- Hook a method(s) of a class in runtime
- Execute custom Frida scripts; and
- Work with the Android intents
URL: https://github.com/sensepost/objection
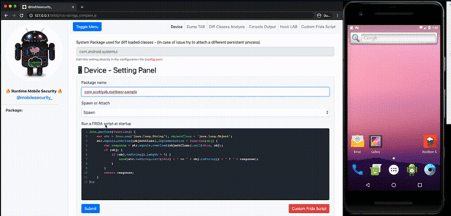
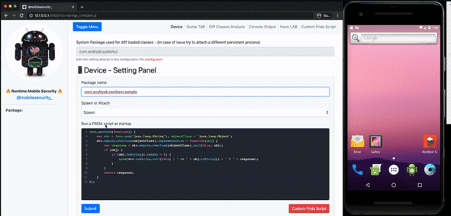
Runtime Mobile Security (RMS)
RMS is powered by Frida and is seen as the web interface to interact with Frida easily. This tool helps to manipulate Android java classes and their methods in runtime.
This tool can be used to dump all the loaded classes and methods, hook specific calls on the fly, trace methods, their arguments and return values, load custom scripts and so on.
URL: https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Red teaming assessments
This article presents important considerations about red teaming assessments within the mobile landscape. Every application and environment has its particularity, so the approach and tools used during the test should be planned and chosen depending on the priority and features to secure. More information about the presented tools and quick guides can be found in the official sources.
Sources
- Mobile pentest cheatsheet, GitHub
- Android reversing, GitBook Segurança-Informática
- Android tools, Mobexler