Android penetration tools walkthrough series: Frida
Frida is a powerful and extensible instrumentation toolkit – among its many strengths, it is ideally suited to testing and evaluating native Android apps. Frida allows you to intercept data received and sent by apps and inject your own code into the process. If you've had any experience with Dex2Jar, JD-GUI or Baksmali, you'll soon appreciate Frida's versatility. (if you haven't, check out our article here [link to Dex2Jar article]
We'll be running through a quick walkthrough to decompile an apk and inject some arbitrary code into the process.

FREE role-guided training plans
Requirements:
- Frida (pip install frida / npm install frida)
- Frida Server (available at https://github.com/frida/frida/releases)
- Make sure Frida-Server is the same version as your Frida install. To check this, simply execute 'frida --version'
- Dex2Jar
- JD-GUI
- adb (Available from the official Google repository – just google "platform-tools adb"
- A rooted android phone or emulator running at least Android 4.4 (We used Nox Player 6 for this walkthrough)
- A downloaded APK file (we're using Sieve [com.mwr.example.sieve]) available from https://github.com/as0ler/Android-Examples/blob/master/sieve.apk
Let's dive right in – ensure your Android device is plugged in and rooted with Developer options and USB Debugging enabled.
- Open a command window and find your connected Android device:
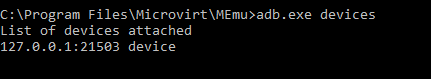
- Push Frida-server to your device using "adb push frida-server /data/local/tmp" – we're placing the Frida-server in a temp directory for ease of use. Note: In the image below, I'm specifically sending to my MEmu emulator – if you're using a normal phone, just the command above will be fine.

- Open a shell session to your device by executing 'adb.exe shell,' chmod your Frida-server so that it's executable and run it!
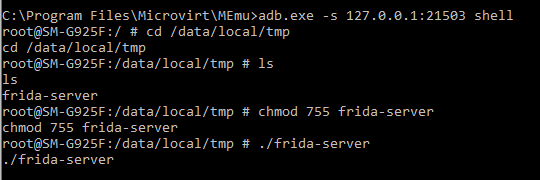
As you can see above, there's no output from running Frida-server but rest assured that it's listening in the background. We're ready to start exploring our Android device!
- Let's do a quick test and use our first Frida tool: frida-ps (which lists processes running on your device). Open a new command window and execute 'frida-ps –Ua'

- As you can see, we're running Sieve [com.mwr.example.sieve], and it will be the target of our testing. First, we decompress the apk using an unzipping program (In our case, 7zip). The file we're interested in is classes.dex

- Just as with baksmali, we're going to convert the classes.dex to a jar file and then open it with jd-gui for easy reading. Go ahead and copy classes.dex to your dex2jar folder now:

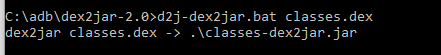
- Execute 'd2j-dex2jar.bat classes.dex' to convert into a valid .jar file
- Let's open our new .jar file in jd-gui and find an activity to inspect:

- If you look sieve, you'll see we're presented with a login screen. Let's bypass that.

- We need to look at our checkKeyResult function – it's looking for verification that the password was correct. So, we'll override it just to send back instead "true."
Because Frida allows us to inject arbitrary code, we can easily overwrite the return from the function with the following python code:

Let's look at what we're doing. The code we really care about is from line 10 onwards. We're overriding the checkKeyResult function to return true, no matter what we enter ourselves.
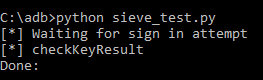
Save your code as sieve_test.py and launch the sieve app on your phone or emulator

Run your script as below and try it out – put in any password or, simply push sign in and you'll be taken straight through to the passwords screen.

FREE role-guided training plans
Excellent work – you've tested your first android app and had a brief taste of some of the amazing things you can do with Frida.








