SpyderSec Challenge
Here is another interesting challenge we are going to solve. The vulnerable machine's name is SpyderSec. We hosted the machine in VirtualBox and fired nmap on it. After running nmap, we found only one open port, which was port 80. We opened the IP and we found a webpage there.

What should you learn next?
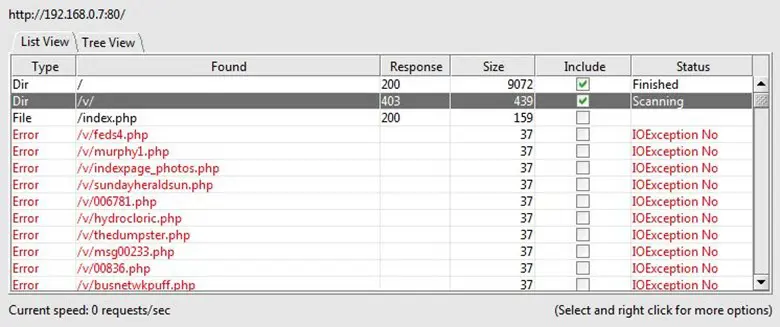
We ran DirBuster on the target but didn't found anything interesting. There was only one "V" directory, which was forbidden for access.
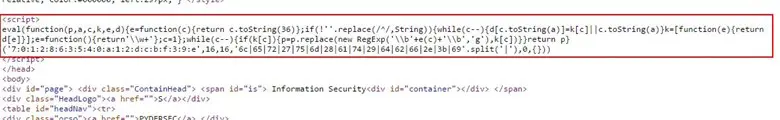
Then we went back to that webpage and started to check its source view and we found one obfuscated JavaScript.
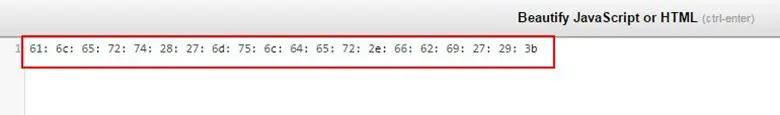
We put this JavaScript in JS beautifier for de-obfuscating the script and we found hex code.
We decode this ASCII Hex and we found a JS alert message.
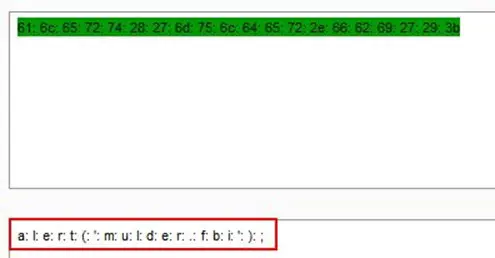
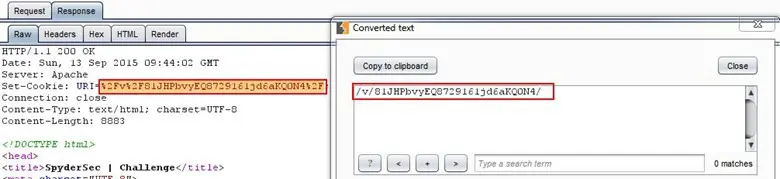
We found it is printing mulder.fbi, and it looks like some kind of file. After that, we configured the browser with Burp Suite for intercepting the application traffic. We found that web page was setting a cookie named URL and there was directory path.
We opened the directory and it showed access forbidden, again we added that file name, which we found from JavaScript mulder.fbi, and the file was there.
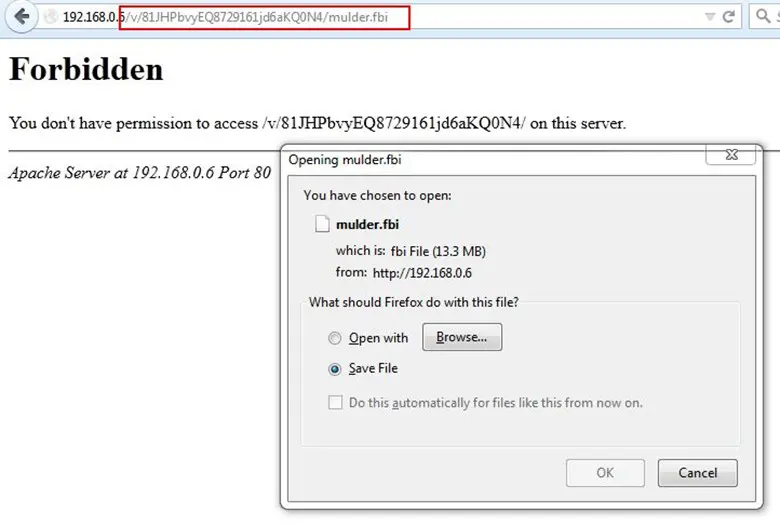
We googled for the FBI file format and we found that it is a video file. We tried to play the file but found nothing there. Therefore, we moved on for digging more clues from the webpage. We saved the whole html page and started to look every file there was an image called challenge.png
We tried to check the image's Meta data file for finding any more clues. We uploaded the image on online ExifTool.
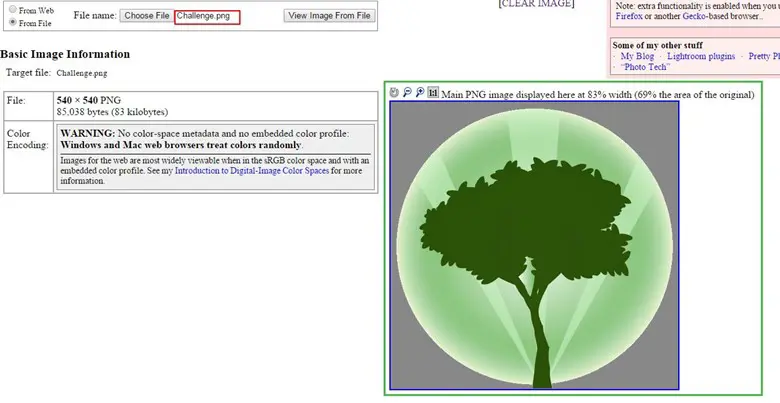
We found all Meta data from the image and we found in comment section there was hex code.

We decoded the hex two times and found a base64 string, and after decoding the base64 string, we found something in plain text, which was looks like password.
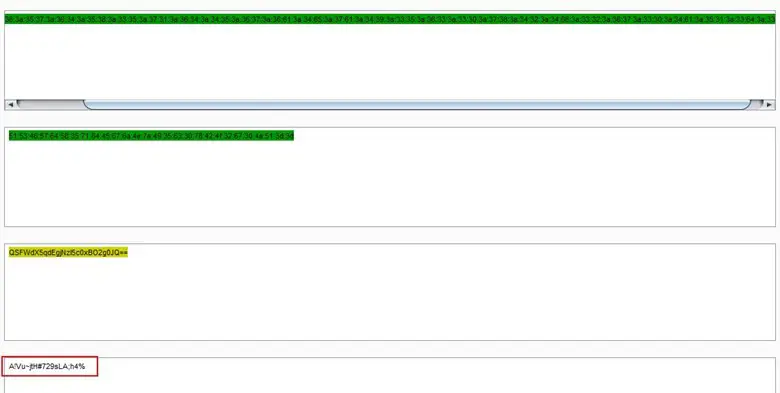
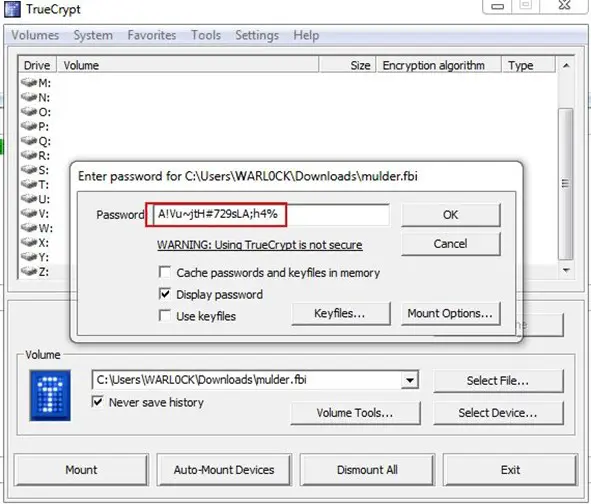
Now we have two things mulder.fbi file and a password type string. After googling about video lock, we found article about hiding message in a video by using TrueCrypt. We launched TrueCrypt, mounted a drive, and it asked for the password. We used that string value and it created a disk in my computer.
As we can see, a mounted drive is showing in my computer.
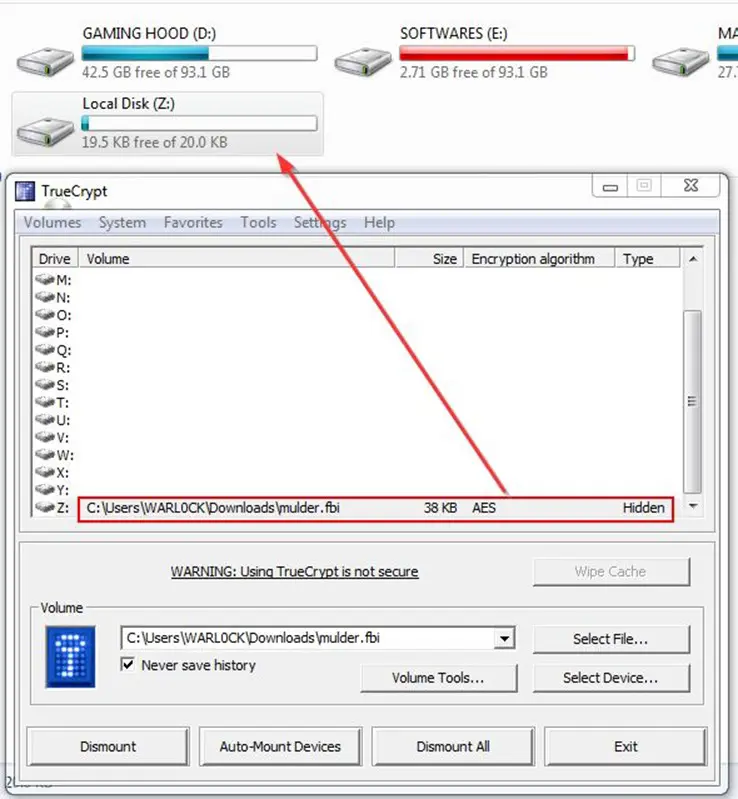
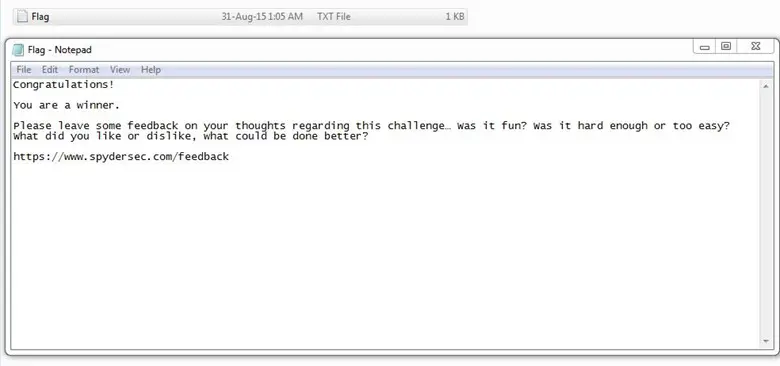
We opened the hard drive and we found the flag.txt file.
References:
https://www.vulnhub.com/series/spydersec,66/

What should you learn next?
http://oskarhane.com/hide-encrypted-files-inside-videos/





