n00bz CTF Challenge #2: Practical Website Hacking
In the second edition of our n00bs CTF Labs, we've created 13 small challenges to test your web app hacking skills. The challenges are based on common vulnerabilities (XXS, code injection, inadequate redirect functions ect.) as well as older and less frequently seen vulnerabilities such as Data Validation; Parameter Delimiter. Each level has a bounty of $100, you just need to find the flag and post your solutions online to to be entered in the contest. There are no limits to the number of entries you can submit, but entrants are only eligible to win the bounty for up to 3 levels.
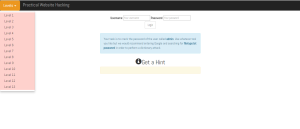
As you can see in the screenshot below, switching levels is as easy as clicking the orange levels button in the top left hand corner of the screen.

What should you learn next?
If you find yourself stuck on a level you can always click the Get a Hint button for additional information and the type of vulnerability you will be solving for is located in the bottom left corner of the page.
Vulnerabilities that are in a green font are on the OWASP's top 10 list while those in red are not.
You can access the second edition of our CTF Challenge by CLICKING HERE and additional information regarding the bounty submission requirements can be found here.
Happy Hunting!
Resources

What should you learn next?
There are many articles in our library that can help with the challenges, here are 8 particularly useful ones:
- /website-hacking-101/: Shows how to carry out dictionary and brute-force attacks using Hydra.
- /website-hacking-101-part-ii/: Gives necessary knowledge and examples for some of the challenges involving path traversal and delimiters.
- /website-hacking-101-part-iii/: Gives examples and information helpful for the code injection and file inclusion challenges.
- /website-hacking-part-iv-tips-better-website-security/: Reading the section on XSS can get you a long way through the exercises.
- /website-hacking-part-vii-common-web-vulnerabilities-brief-solutions/: Gives examples and helpful info about redirects, file handling and CSRF.
- /html5-security-local-storage/: Information about HTML5’s local storage which you can find useful for one of the challenges.
- /deadly-consequences-xss/: Knowing more about XSS can do no harm and you may find the information deep enough to solve a challenge or two.
- /file-inclusion-attacks/: File inclusion is something that you should be aware of – to complete the challenges and beyond.